In the realm of computing, seamless remote access to Linux environments has become a cornerstone of modern productivity and collaboration. Windows Subsystem for Linux (WSL) has revolutionized this landscape by enabling Linux distributions to run natively on Windows, opening up a world of possibilities for developers, system administrators, and enthusiasts alike.
Among its many features, the WSL SSH server stands out as a pivotal tool for establishing secure remote connections to these Linux environments, empowering users with unparalleled flexibility and control.
WSL SSH server acts as a gateway, bridging the gap between remote systems and the WSL-hosted Linux distributions. It allows users to securely connect to their Linux environments from virtually any operating system, transforming their local machines into powerful command centers for remote administration, file transfers, and application execution.
This guide delves into the intricacies of WSL SSH server, providing a comprehensive exploration of its setup, configuration, usage, and troubleshooting, empowering users to harness its full potential.
Understanding WSL SSH Server
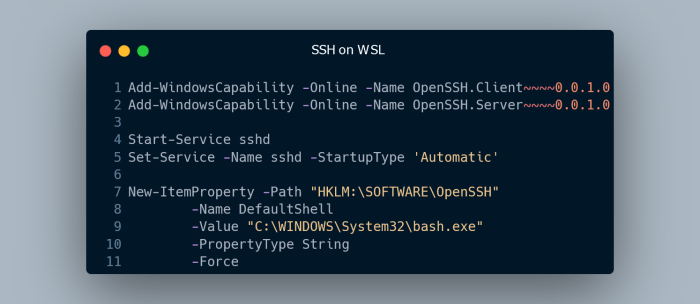
Windows Subsystem for Linux (WSL) has revolutionized the way developers and system administrators interact with Linux distributions on Windows. WSL allows users to run a Linux environment directly on their Windows machines, enabling seamless integration and interoperability between the two operating systems.
At the core of WSL’s functionality lies the WSL SSH server, a crucial component that facilitates secure remote access to Linux distributions running within WSL. This enables users to connect to their WSL environments from remote locations, providing a convenient and efficient way to manage and interact with their Linux systems.
WSL SSH Server: A Gateway to Remote Linux Access
The WSL SSH server operates on the principle of secure shell (SSH), a network protocol that allows for encrypted communication between two computers over an insecure network. When enabled, the WSL SSH server listens for incoming SSH connections on a specified port, typically port 22. Upon receiving a connection request, the server authenticates the user’s credentials and establishes a secure tunnel between the remote client and the WSL environment.
Once authenticated, users can remotely access their WSL Linux distribution as if they were physically present at the console. This allows them to execute commands, manage files, and perform various administrative tasks, all from the comfort of their remote location.
Benefits of Using WSL SSH Server
- Enhanced Security: WSL SSH server utilizes SSH encryption to protect data transmitted between the remote client and the WSL environment, ensuring the confidentiality and integrity of sensitive information.
- Remote Access Convenience: With WSL SSH server, users can access their WSL Linux distributions from anywhere with an internet connection, enabling remote management and troubleshooting.
- Cross-Platform Compatibility: The WSL SSH server supports a wide range of SSH clients, including those available on Windows, macOS, and Linux, providing cross-platform compatibility and flexibility.
- Simplified Development and Testing: WSL SSH server streamlines the development and testing process for applications that require a Linux environment. Developers can remotely connect to their WSL Linux distributions to run tests, debug code, and perform other development tasks.
Setting Up WSL SSH Server
If you want to harness the power of WSL and enjoy the seamless remote access to your Windows machine, setting up a WSL SSH server is the key. With this guide, we’ll walk you through the step-by-step process, from enabling WSL to configuring your SSH server and firewall rules, ensuring a secure and reliable connection.
1. Enable WSL
Before diving into the SSH server setup, you need to ensure WSL is enabled on your Windows system. Head over to the Control Panel, navigate to “Programs and Features,” and select “Turn Windows features on or off.” Find “Windows Subsystem for Linux” and check the box next to it.
Click “OK” to complete the WSL installation.
2. Install an SSH Server
Now, it’s time to install an SSH server on your WSL distribution. Ubuntu users can simply run the command “sudo apt install openssh-server” in their terminal. For other distributions, refer to their respective package managers.
3. Configure SSH Server
Once the SSH server is installed, you need to configure it to allow remote access. Edit the SSH configuration file “/etc/ssh/sshd_config” using a text editor. Look for the line “PasswordAuthentication” and change it to “yes” to enable password-based authentication. Additionally, you can set up key-based authentication for enhanced security.
4. Configure Firewall Rules
To allow incoming SSH connections, you need to configure your firewall rules. In Windows Defender Firewall, create a new inbound rule. Select “Port” as the rule type and specify port 22, which is the default SSH port. Ensure the rule is enabled and applies to both public and private networks.
5. Test the Connection
With everything set up, it’s time to test the SSH connection. From another computer or device, open a terminal and type “ssh username@ip_address,” where “username” is your WSL username and “ip_address” is your Windows machine’s IP address. If you’ve set up password-based authentication, you’ll be prompted for your password.
If the connection is successful, you’ll be greeted with a command prompt.
Potential Challenges and Solutions
During the setup process, you might encounter a few challenges. If you face issues connecting to the SSH server, double-check your firewall rules and ensure port 22 is open. Additionally, verify that the SSH server is running by checking the status with the command “sudo systemctl status ssh.”
If you encounter permission issues, adjust the file permissions using the “chmod” command.
Connecting to WSL SSH Server
Establishing a connection to your WSL SSH server is a straightforward process. With the help of SSH clients, you can securely access your WSL environment from various operating systems.
Choosing an SSH Client
There are several SSH clients available, each with its unique features and capabilities. Some popular options include:
- PuTTY: A free and open-source SSH client for Windows, known for its simplicity and reliability.
- OpenSSH: A widely used SSH client available for Windows, macOS, and Linux, known for its robust security features.
- MobaXterm: A commercial SSH client for Windows that offers a comprehensive set of features, including a terminal emulator, file transfer, and X11 forwarding.
Select the SSH client that best suits your needs and preferences.
Connecting from Windows
To connect to your WSL SSH server from Windows, follow these steps:
- Launch your chosen SSH client (e.g., PuTTY or MobaXterm).
- In the hostname or IP address field, enter the IP address of your WSL distribution (you can find this by running “ipconfig” in your WSL terminal).
- Enter the SSH port number (by default, it’s 22).
- Provide your WSL username and password.
- Click “Connect” or “Login” to establish the SSH connection.
Connecting from macOS and Linux
The process of connecting to your WSL SSH server from macOS or Linux is similar to that of Windows.
- Open your terminal window (e.g., Terminal or Konsole).
- Run the following command, replacing with the IP address of your WSL distribution:
ssh -p 22 username@
- Enter your WSL password when prompted.
You should now be successfully connected to your WSL SSH server.
Using WSL SSH Server
WSL SSH server enables you to securely connect to your WSL environment from remote devices. This section demonstrates its capabilities and advantages compared to traditional SSH servers.
File Transfer
WSL SSH server supports seamless file transfer between your remote device and the WSL environment. Using the secure file transfer protocol (SFTP), you can easily copy, move, and edit files as needed.
Remote Command Execution
With WSL SSH server, you can execute commands on your WSL environment from the remote device. This allows you to manage and control your WSL system remotely, perform maintenance tasks, and run scripts or applications.
Remote Filesystem Management
WSL SSH server provides access to the WSL filesystem from remote devices. You can browse directories, create or delete files, and perform various filesystem operations as if you were directly connected to the WSL environment.
Advantages and Disadvantages
Advantages:
* Seamless integration with WSL environment – Secure file transfer and remote command execution – Easy setup and configuration – Lightweight and resource-efficient
Disadvantages:
* Limited to WSL-compatible systems – May require additional configuration for specific use cases – Potential security risks if not properly configured
Troubleshooting WSL SSH Server
Ensuring a smooth experience with WSL SSH server requires addressing potential issues and errors that may arise during its usage. Common problems include connection difficulties, authentication failures, and permission denied errors. This section provides detailed troubleshooting steps to effectively resolve these challenges.
Connection Problems
Establishing a successful SSH connection between a client and the WSL SSH server is crucial. If you encounter connection issues, consider the following troubleshooting steps:
- Verify Network Connectivity: Ensure that both the client and WSL SSH server have stable network connections. Check for any firewall or network restrictions that might be blocking the SSH connection.
- Confirm SSH Service Status: Verify that the SSH service on the WSL SSH server is running. You can use the command
systemctl status sshdto check the service status. - Check SSH Port Configuration: Ensure that the SSH service is listening on the correct port. The default SSH port is 22, but it can be modified. Verify the port configuration in the SSH configuration file (/etc/ssh/sshd_config) and adjust it if necessary.
- Disable Firewall: Temporarily disable the firewall on the WSL SSH server to eliminate it as a potential source of connection issues. Once the connection is established, re-enable the firewall and configure it to allow SSH traffic.
Authentication Failures
When encountering authentication failures while connecting to the WSL SSH server, consider the following troubleshooting steps:
- Verify SSH Credentials: Ensure that you are using the correct username and password or SSH key for authentication. Double-check the credentials and ensure they are entered accurately.
- Check SSH Key Permissions: If using SSH keys for authentication, verify that the SSH key file has the correct permissions. The key file should have read-only permissions for the owner and no permissions for others.
- Disable Password Authentication: As a security measure, consider disabling password authentication and relying solely on SSH key-based authentication. This can be done by editing the SSH configuration file (/etc/ssh/sshd_config) and setting
PasswordAuthenticationtono.
Permission Denied Errors
If you encounter permission denied errors when accessing files or directories on the WSL SSH server, consider the following troubleshooting steps:
- Check File and Directory Permissions: Verify the file and directory permissions on the WSL SSH server. Ensure that the user or group you are using has the appropriate permissions to access the resources.
- Change File and Directory Ownership: If necessary, change the ownership of the file or directory to the user or group that needs access. Use the
chowncommand to modify the ownership. - Adjust User and Group Permissions: Use the
chmodcommand to modify the permissions of the file or directory. Grant the necessary permissions (read, write, execute) to the user or group that requires access.
Advanced WSL SSH Server Techniques
Beyond the basics, WSL SSH server offers advanced techniques that expand its capabilities and enhance its versatility in various scenarios. These techniques include setting up SSH tunnels, configuring port knocking, and utilizing SSH key forwarding. Each technique unlocks unique benefits and applications, enabling users to customize and optimize their WSL SSH server setup for specific needs.
SSH Tunneling
SSH tunneling allows users to create a secure tunnel between two networks, encapsulating data transmission within an encrypted SSH connection. This technique is particularly useful for accessing remote resources that are otherwise inaccessible due to network restrictions or firewalls. SSH tunneling offers several advantages, including:
- Secure Data Transmission: By establishing an encrypted tunnel, data transmitted between the two networks remains protected from eavesdropping and interception.
- Bypassing Network Restrictions: SSH tunneling enables users to bypass firewalls and network restrictions that may block certain ports or protocols, allowing access to otherwise inaccessible resources.
- Remote Access to Services: SSH tunneling allows users to remotely access services running on a private network, such as a local web server or database, from a public network.
Port Knocking
Port knocking is a security technique that involves sending a specific sequence of port connections to a server before establishing an SSH connection. This technique enhances security by requiring authorized users to “knock” on specific ports in a predefined order, acting as a secret handshake.
Port knocking offers several benefits:
- Increased Security: By requiring a specific sequence of port connections, port knocking adds an extra layer of security, making it more difficult for unauthorized users to gain access to the SSH server.
- Stealth Mode: Port knocking allows users to keep SSH ports closed and only open them when authorized users knock on the correct ports. This stealth mode reduces the risk of port scanning attacks and unauthorized access attempts.
- Granular Access Control: Port knocking enables administrators to define different port knocking sequences for different users or groups, allowing granular control over access to the SSH server.
SSH Key Forwarding
SSH key forwarding allows users to securely access remote servers using their local SSH keys. This technique eliminates the need to manually enter passwords on each remote server, streamlining the authentication process and enhancing security. SSH key forwarding offers several advantages:
- Simplified Authentication: SSH key forwarding enables users to authenticate to remote servers using their local SSH keys, eliminating the need to remember multiple passwords.
- Improved Security: SSH key forwarding provides a more secure authentication method compared to passwords, as SSH keys are less susceptible to brute-force attacks and keyloggers.
- Automated Access: SSH key forwarding allows users to automate access to remote servers, enabling seamless integration with scripts and automation tools.
Securing WSL SSH Server
Safeguarding your WSL SSH server from unauthorized access and cyber threats is of utmost importance. By implementing robust security measures, you can protect sensitive data, prevent unauthorized access, and maintain the integrity of your system.
Hardening the SSH Server
Implementing effective security measures to harden your SSH server is crucial in preventing unauthorized access and ensuring the integrity of your system.
- Disable Root Login: Disable root login to prevent direct access to the root account, making it more difficult for attackers to gain administrative privileges.
- Use Strong Passwords: Enforce the use of strong passwords for all users, ensuring they are complex and unique to prevent brute-force attacks.
- Implement Two-Factor Authentication: Enable two-factor authentication (2FA) to add an extra layer of security by requiring a second form of authentication, such as a code sent to your mobile device.
- Restrict Access: Limit SSH access to authorized users and IP addresses by configuring firewall rules and access control lists (ACLs).
- Regularly Update Software: Keep your SSH server and operating system up to date with the latest security patches and updates to address known vulnerabilities.
Performance Considerations
When using WSL SSH server, it’s crucial to consider the potential performance implications to ensure smooth remote access and optimal resource utilization.
Several factors can influence the performance of WSL SSH server, including latency, bandwidth utilization, and resource usage. Understanding these factors and implementing appropriate optimizations can significantly improve the overall performance of the server.
Latency
Latency, also known as network delay, refers to the time it takes for data packets to travel between the client and the server. High latency can result in noticeable delays and decreased responsiveness during remote access sessions.
To minimize latency, consider the following:
- Network Infrastructure: Ensure that the network infrastructure between the client and the server is optimized for low latency. This includes using high-speed network connections, such as Gigabit Ethernet or fiber optic cables, and avoiding congested or unreliable network segments.
- Physical Distance: The physical distance between the client and the server can also impact latency. If the client and the server are located far apart, consider using a VPN or other techniques to reduce the effective distance.
Bandwidth Utilization
Bandwidth utilization refers to the amount of data transferred between the client and the server. High bandwidth utilization can lead to network congestion and slowdowns, especially if the available bandwidth is limited.
To optimize bandwidth utilization, consider the following:
- Data Compression: Use data compression techniques, such as SSH compression or zlib compression, to reduce the size of data packets transferred over the network. This can significantly improve bandwidth utilization, especially for large file transfers or high-volume traffic.
- Traffic Shaping: Implement traffic shaping mechanisms to prioritize SSH traffic and ensure that it receives a fair share of the available bandwidth. This can be achieved using QoS (Quality of Service) techniques or by configuring traffic shaping rules on the network devices.
Resource Usage
WSL SSH server utilizes system resources, such as CPU, memory, and disk space, to operate. Excessive resource usage can lead to performance degradation, especially on resource-constrained systems.
To optimize resource usage, consider the following:
- Resource Monitoring: Regularly monitor the resource usage of the WSL SSH server to identify any potential bottlenecks or resource contention issues. This can be done using system monitoring tools or by examining the server logs.
- Resource Allocation: If necessary, allocate additional resources to the WSL SSH server to improve its performance. This may involve increasing the amount of RAM or CPU cores allocated to the WSL instance or moving the server to a more powerful machine.
Alternatives to WSL SSH Server
While WSL SSH Server offers a convenient way to access Linux environments on Windows, it’s not the only option available. Here’s a comparison of some alternatives, each with its own advantages and disadvantages:
VirtualBox
- VirtualBox is a free and open-source virtualization software that allows you to run multiple operating systems simultaneously on a single host machine.
- It provides a dedicated virtual machine for each Linux distribution, ensuring complete isolation and resource allocation.
- However, VirtualBox requires a significant amount of system resources and can be slower than other options.
VMware
- VMware is a commercial virtualization software that offers a wider range of features and better performance than VirtualBox.
- It provides advanced networking and security options, making it suitable for enterprise environments.
- However, VMware is more expensive than VirtualBox and requires a paid subscription for some features.
Docker
- Docker is a containerization platform that allows you to package and run applications in isolated environments.
- It provides a lightweight and portable way to deploy Linux applications on Windows without the overhead of a full virtual machine.
- However, Docker may not be suitable for all use cases, especially those that require direct access to the underlying Linux kernel.
Final Thoughts
WSL SSH server has emerged as a game-changer in the realm of remote access, seamlessly integrating Linux environments into the Windows ecosystem. Its ability to provide secure and versatile connections, coupled with its ease of setup and configuration, makes it an indispensable tool for developers, system administrators, and enthusiasts seeking to unlock the full potential of Linux from within Windows.
As technology continues to evolve, WSL SSH server stands poised to play an increasingly pivotal role in shaping the future of remote computing.