In the realm of virtual private networks (VPNs), WireGuard stands tall as a formidable contender. With its lightning-fast speed, robust security, and modern design, it has revolutionized the way we protect and manage our online presence. One of WireGuard’s most compelling features is split tunneling, a game-changer that empowers users to route specific traffic through the VPN while allowing other traffic to flow directly over their local network.
Split tunneling offers a unique blend of security and convenience, allowing you to safeguard sensitive data while maintaining optimal performance for applications that require direct access to local resources. Whether you’re a seasoned network administrator or a home user seeking greater control over your online experience, WireGuard VPN split tunneling is an invaluable tool that can enhance your digital life.
Understanding WireGuard VPN Split Tunneling
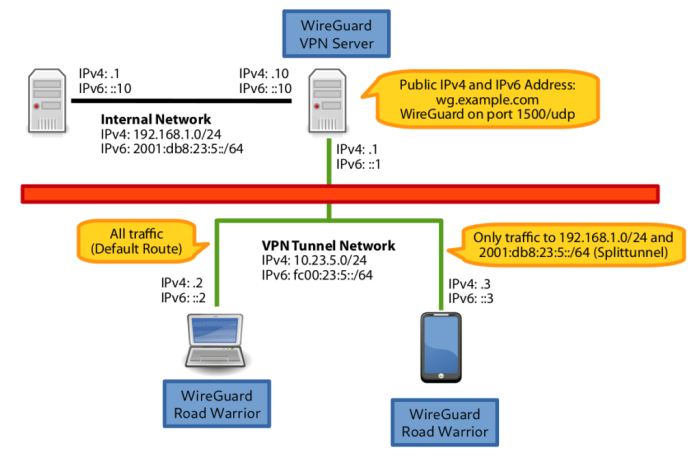
Split tunneling in VPNs allows users to route only specific traffic through the VPN, while other traffic is sent directly over the local network connection. This can be useful for tasks that require high bandwidth or low latency, such as gaming or video streaming.WireGuard
implements split tunneling by using a routing table to determine which traffic should be sent through the VPN. The routing table can be configured to allow all traffic to go through the VPN, or to only send specific types of traffic, such as traffic from a particular application or website.
Benefits of Using WireGuard VPN Split Tunneling
There are several benefits to using WireGuard VPN split tunneling, including:
- Improved performance for tasks that require high bandwidth or low latency.
- Reduced latency for traffic that does not need to go through the VPN.
- Increased security for traffic that is sent through the VPN.
Configuring WireGuard VPN Split Tunneling
WireGuard VPN split tunneling allows you to selectively route traffic through the VPN tunnel while excluding certain applications or destinations. Here’s how to configure it:
Step 1: Determine Excluded Destinations
Identify the applications or destinations you want to exclude from the VPN tunnel. This could include local network resources, streaming services, or websites that require direct access to your local IP address.
Step 2: Configure WireGuard Configuration File
Edit your WireGuard configuration file and add the following lines:“`[Interface]…ExcludedApplications = ExcludedDestinations = “`Replace ` ` with a comma-separated list of application names or process IDs. For example:“`ExcludedApplications = “Spotify,Discord”“`Replace ` ` with a comma-separated list of IP addresses, subnets, or domain names.
For example:“`ExcludedDestinations = “192.168.1.0/24,example.com”“`
Step 3: Restart WireGuard
Restart WireGuard to apply the new configuration. On Linux:“`sudo systemctl restart wg-quick@ “`On Windows:“`Restart-Service wg- “`
Step 4: Verify Split Tunneling
Check if split tunneling is working by accessing the excluded destinations. They should now be reachable without going through the VPN tunnel.
Best Practices for Split Tunneling Performance
* Minimize the number of excluded destinations to improve overall VPN performance.
- Use wildcards (*) to match a range of IP addresses or subnets.
- Regularly review and update your excluded destinations to ensure optimal performance.
Using WireGuard VPN Split Tunneling in Different Scenarios
WireGuard VPN split tunneling allows for more granular control over the traffic that goes through the VPN tunnel, offering several benefits in specific scenarios.
Performance Optimization
Split tunneling can enhance performance for applications that don’t require VPN protection. By excluding certain traffic from the tunnel, it reduces the amount of data that needs to be encrypted and decrypted, freeing up resources and minimizing latency. For instance, if you’re streaming a video on a local network while connected to a VPN, split tunneling allows the streaming traffic to bypass the VPN, resulting in a smoother and more responsive video experience.
Specific Use Cases
Split tunneling finds applications in various scenarios:
-
- -*Banking and Financial Transactions
Some banks require access to local networks for authentication or fraud prevention measures. Split tunneling allows users to connect to their bank’s website or app securely while still accessing local resources.
- -*Banking and Financial Transactions
-*Local Network Access
If you need to access resources on your local network, such as a printer or shared files, split tunneling ensures that this traffic remains on the local network, avoiding the VPN tunnel and potential performance issues.
-*Gaming and Streaming
Split tunneling can optimize gaming or streaming experiences by directing non-gaming traffic outside the VPN tunnel. This reduces latency and minimizes the impact of VPN overhead on the performance of these applications.
Balancing Security and Performance
When using split tunneling, it’s crucial to strike a balance between security and performance.
Consider the following guidelines:
- Only exclude traffic from the VPN tunnel that genuinely does not require VPN protection.
- Monitor traffic patterns to ensure that sensitive data is not inadvertently routed outside the VPN.
- Regularly review and update the split tunneling rules to maintain optimal security and performance.
Security Considerations for WireGuard VPN Split Tunneling
Implementing split tunneling with WireGuard VPN offers enhanced flexibility, but it also introduces potential security risks. Understanding these risks and implementing appropriate mitigation strategies is crucial for maintaining a secure network environment.
Split tunneling allows specific traffic to bypass the VPN tunnel, potentially exposing sensitive data or applications to external threats. To address these risks, consider the following mitigation strategies:
Firewall Configuration
- Configure firewalls to restrict access to sensitive applications and data from untrusted networks.
- Implement granular firewall rules to control traffic flow based on source and destination addresses, ports, and protocols.
Network Segmentation
- Create separate network segments for different types of traffic, isolating sensitive data and applications from untrusted traffic.
- Use VLANs or subnets to segregate traffic based on security requirements and minimize the impact of potential breaches.
Encryption and Authentication
- Ensure that all traffic, including split-tunneled traffic, is encrypted using strong encryption algorithms.
- Implement strong authentication mechanisms, such as two-factor authentication or certificate-based authentication, to prevent unauthorized access.
Monitoring and Logging
- Enable logging and monitoring to track VPN activity and identify any suspicious or unauthorized behavior.
- Configure alerts to notify administrators of potential security incidents or configuration changes.
Configuration Hardening
- Use the latest version of WireGuard VPN and keep it updated with security patches.
- Configure WireGuard VPN with strong encryption parameters and disable unnecessary features.
- Limit access to VPN configuration files and credentials to authorized personnel.
Troubleshooting WireGuard VPN Split Tunneling
Split tunneling can occasionally encounter issues, but they are typically easy to troubleshoot. Here are some typical issues and their remedies:
Incorrect configuration
Confirm that the split tunnel settings in your WireGuard configuration are correct. Check that the appropriate interfaces are listed in the “AllowedIPs” field and that the “Peer” address is configured correctly.
Firewall blocking
Firewalls can occasionally interfere with split tunneling. Verify that the WireGuard port (typically UDP 51820) is accessible from both the client and server machines.
Routing issues
Routing issues can occasionally prevent split tunneling from functioning properly. Check that the routing table on the client machine is configured to direct traffic to the appropriate interfaces.
Debug logs
WireGuard provides debug logs that can be helpful in troubleshooting split tunneling issues. Enable debug logging in the WireGuard configuration and examine the logs for any errors or warnings.
Additional tips
- Use a VPN client that supports split tunneling.
- Test split tunneling with a simple network configuration before implementing it in a production environment.
- Monitor the VPN connection to ensure it is stable and performing as expected.
Performance Comparison of WireGuard VPN Split Tunneling with Other VPNs
WireGuard VPN split tunneling offers impressive performance advantages compared to other VPN protocols. It utilizes modern encryption algorithms and a streamlined architecture, resulting in faster connection speeds and lower latency.
Factors affecting performance include the choice of encryption algorithm, network conditions, and hardware capabilities. WireGuard’s ChaCha20 encryption is highly efficient, providing strong security without sacrificing speed.
Encryption Algorithms
- WireGuard: ChaCha20 (fast and secure)
- OpenVPN: AES-256-CBC (slower, but widely supported)
- IPsec: AES-GCM (moderate speed and security)
Network Conditions
Network conditions such as bandwidth and latency can impact VPN performance. WireGuard’s efficient protocol design minimizes overhead, making it suitable for both high-speed and low-bandwidth connections.
Choosing the Best VPN Protocol
The optimal VPN protocol depends on specific requirements. WireGuard VPN split tunneling is ideal for users seeking high performance, while OpenVPN offers broader compatibility. IPsec is suitable for enterprise environments with stringent security needs.
Integration of WireGuard VPN Split Tunneling with Other Technologies
WireGuard VPN split tunneling can be integrated with other network technologies to enhance its functionality and security. This integration allows you to tailor the VPN connection to specific requirements and scenarios.
One way to integrate WireGuard VPN split tunneling is with firewalls. By configuring the firewall rules, you can control which traffic is routed through the VPN tunnel and which is sent directly to the internet. This provides granular control over network access and can help improve security by preventing unauthorized access to sensitive resources.
Integrating WireGuard VPN Split Tunneling with Routers
Another integration option is with routers. By configuring the router’s routing table, you can specify which devices or subnets use the VPN tunnel and which use the regular internet connection. This allows for more flexible network management and can optimize network performance by directing traffic through the most efficient path.
The integration of WireGuard VPN split tunneling with other technologies offers several benefits. It enhances network security by providing granular control over traffic flow. It also improves network performance by optimizing routing and reducing latency. Additionally, it simplifies network management by centralizing control over different network components.
Advanced Topics in WireGuard VPN Split Tunneling
WireGuard VPN split tunneling offers advanced features that enhance its flexibility and customization. These features include per-application routing and custom rules, allowing users to tailor the split tunneling behavior to specific requirements.
Per-Application Routing
Per-application routing enables users to selectively route specific applications through the VPN tunnel while excluding others. This is useful for scenarios where certain applications, such as online banking or sensitive data transfers, require the added security of the VPN, while others, such as streaming services or social media, can be routed directly over the local network for better performance.To
configure per-application routing, users can specify the applications to be routed through the VPN in the WireGuard configuration file. This is done by adding the “AllowedIPs” parameter to the interface section, followed by the IP addresses or subnets that should be routed through the VPN.
For example:“`[Interface]Address = 10.0.0.1/24AllowedIPs = 192.168.1.0/24, 10.10.10.0/24“`In this example, traffic from applications on the local network with IP addresses in the 192.168.1.0/24 and 10.10.10.0/24 subnets will be routed through the VPN tunnel, while traffic from other applications will be routed directly over the local network.
Custom Rules
Custom rules provide even greater flexibility by allowing users to define their own routing rules based on various criteria, such as source or destination IP addresses, ports, or protocols. This enables users to create complex split tunneling configurations that meet their specific requirements.To
create custom rules, users can add the “PostUp” and “PostDown” scripts to the WireGuard configuration file. These scripts are executed after the VPN interface is brought up or down, respectively. Within these scripts, users can use iptables or other networking commands to define the desired routing rules.For
example, the following PostUp script adds a rule to route all traffic from the 192.168.1.100 IP address through the VPN tunnel:“`#!/bin/shiptables
- t nat
- A POSTROUTING
- o wg0
- s 192.168.1.100
- j SNAT
- -to 10.0.0.2
“`In this example, the 10.0.0.2 IP address is the IP address of the VPN gateway.Advanced features like per-application routing and custom rules empower users with greater control over their WireGuard VPN split tunneling configurations. These features enable users to tailor the split tunneling behavior to meet their specific requirements, enhancing the flexibility and security of their VPN connections.
Future Developments in WireGuard VPN Split Tunneling
WireGuard VPN split tunneling is a rapidly evolving technology, and several exciting developments are expected in the future. These advancements aim to enhance security, improve performance, and expand the functionality of split tunneling.
Enhanced Security
- WireGuard’s developers are exploring new cryptographic algorithms and protocols to further strengthen the security of split tunneling.
- Implementing post-quantum cryptography will safeguard against emerging threats posed by quantum computers.
- Improved key management techniques will simplify key generation and distribution, enhancing overall security.
Performance Improvements
- Optimizing the WireGuard protocol and kernel implementation will lead to significant performance enhancements.
- Multi-threading and hardware acceleration will be leveraged to maximize throughput and reduce latency.
- Adaptive traffic shaping algorithms will dynamically adjust bandwidth allocation based on application requirements, ensuring optimal performance.
Expanded Functionality
- Integration with network management tools will enable centralized control and monitoring of split tunneling configurations.
- Support for IPv6 and multiple network interfaces will expand the applicability of split tunneling to more complex network environments.
- Integration with cloud platforms and container technologies will facilitate seamless deployment and management of split tunneling in cloud-native environments.
Role in Evolving VPN Landscape
- Split tunneling will become increasingly prevalent as businesses and individuals adopt zero-trust network architectures.
- It will play a crucial role in securing remote access and protecting sensitive data in hybrid work environments.
- The integration of split tunneling with other security technologies, such as firewalls and intrusion detection systems, will create a comprehensive security ecosystem.
Additional Resources for WireGuard VPN Split Tunneling
If you want to explore WireGuard VPN split tunneling further, here are some helpful resources:
-
- -*Official WireGuard documentation
The WireGuard website provides comprehensive documentation on split tunneling, including setup instructions and troubleshooting tips.
- -*Official WireGuard documentation
-*Tutorials and guides
Many online tutorials and guides can help you set up and configure split tunneling with WireGuard. Search for “WireGuard split tunneling tutorial” or “WireGuard split tunneling guide” to find these resources.
-*Community forums
The WireGuard community forum is a great place to ask questions and get help from other users. You can find the forum at https://forum.wireguard.com/.
To stay up-to-date with the latest developments in split tunneling technology, you can follow the WireGuard project on GitHub and subscribe to the WireGuard mailing list.
Outcome Summary

WireGuard VPN split tunneling empowers users with unprecedented flexibility and control over their network traffic. By selectively routing only essential traffic through the VPN, you can enjoy the benefits of enhanced security without compromising performance or sacrificing local network access.
As the future of VPN technology continues to evolve, WireGuard split tunneling will undoubtedly play a pivotal role, enabling us to navigate the complexities of modern networking with greater efficiency and peace of mind.