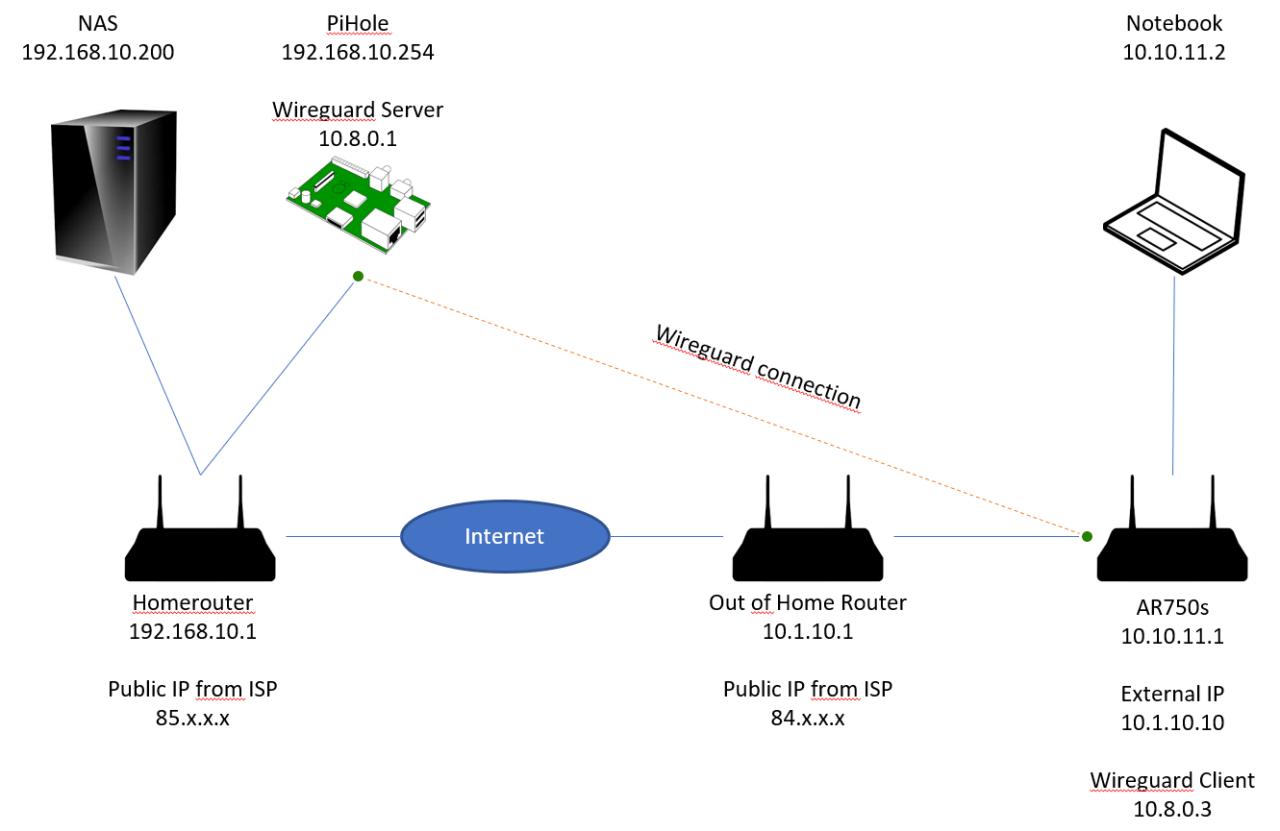
ssh.sshslowdns.com – In the realm of virtual private networks (VPNs), WireGuard has emerged as a formidable player, renowned for its speed, security, and user-friendliness. One of its most versatile features is split tunneling, which allows users to selectively route specific network traffic through the VPN while leaving other traffic unaffected.
This guide will delve into the intricacies of WireGuard split tunneling on Windows, empowering you with the knowledge to configure, troubleshoot, and optimize this powerful networking tool.
Split tunneling offers a unique blend of security and convenience. By directing only essential traffic through the VPN, you can maintain secure access to sensitive resources while enjoying unhindered access to local network devices and services. This approach not only enhances performance but also minimizes potential security risks associated with exposing your entire network traffic to the VPN.
WireGuard Split Tunneling Overview
WireGuard is a modern, open-source VPN protocol known for its speed, security, and simplicity. Split tunneling is a feature that allows you to selectively route specific traffic through the VPN tunnel while sending other traffic directly over your regular internet connection.
Split tunneling offers several benefits. It can improve performance by reducing latency and bandwidth usage for traffic that doesn’t require VPN protection. Additionally, it can enhance security by preventing sensitive data from being exposed to the VPN provider.
Limitations of Split Tunneling
While split tunneling provides advantages, it also has some limitations. One potential drawback is that it can increase complexity in network management. Additionally, it may not be suitable for all use cases, such as when strict security requirements dictate that all traffic must be routed through the VPN.
Configuring WireGuard Split Tunneling on Windows
To configure WireGuard split tunneling on Windows, follow these steps:
1. Open the WireGuard app and click on the “Settings” tab.
2. In the “General” section, enable the “Split Tunneling” option.
3. In the “Allowed Networks” section, click on the “Add” button.
4. Enter the IP address or subnet of the networks you want to exclude from the VPN tunnel.
5. Click on the “Save” button.
6. Connect to the VPN server.
7. Your traffic will now be routed through the VPN tunnel for all networks except those you have specified in the “Allowed Networks” section.
Here are some screenshots to illustrate the process:
- Enable Split Tunneling
- Add Allowed Networks
Troubleshooting WireGuard Split Tunneling Issues
Identifying and resolving issues with WireGuard split tunneling can ensure a seamless and efficient user experience. Here are some common problems you may encounter and potential solutions:
Unable to Connect to the VPN
-
- -*Check your network connection
Ensure your computer has a stable internet connection before attempting to connect to the VPN.
- -*Check your network connection
-*Verify the WireGuard configuration
Confirm that the WireGuard configuration on your device is correct, including the server address, port, and encryption keys.
-*Disable other VPNs
Close any other VPN software or services running on your device, as they may interfere with WireGuard.
Limited Access to Local Resources
-
- -*Configure the split tunneling rules
Review the split tunneling rules and ensure they are correctly configured to allow access to local resources.
- -*Configure the split tunneling rules
-*Check firewall settings
Make sure your firewall is not blocking access to local resources when connected to the VPN.
-*Exclude specific applications
If necessary, exclude specific applications from the VPN tunnel to ensure they have access to local resources.
Slow Internet Speed
-
- -*Optimize your network settings
Adjust your network settings to prioritize traffic over the VPN tunnel for better performance.
- -*Optimize your network settings
-*Check server load
Consider the load on the VPN server and connect to a less congested server if possible.
-*Upgrade your internet connection
If your internet speed is consistently slow, consider upgrading your broadband plan for a faster connection.
DNS Leaks
-
- -*Configure DNS settings
Ensure your DNS settings are configured to use the VPN’s DNS servers to prevent DNS leaks.
- -*Configure DNS settings
-*Use a VPN kill switch
Enable the VPN kill switch feature to automatically disconnect your internet connection if the VPN connection drops, preventing DNS leaks.
-*Check for DNS leaks
Use online tools to check for DNS leaks and identify any potential vulnerabilities.
Security Considerations for WireGuard Split Tunneling on Windows
Split tunneling with WireGuard offers convenience, but it also introduces potential security risks that must be carefully considered.
Understanding these risks and implementing appropriate mitigation strategies is crucial for maintaining a secure network environment.
The primary security concern with split tunneling is the potential for sensitive traffic to bypass the VPN tunnel and be exposed to external threats. This can occur if untrusted devices or networks are allowed to access the local network segment that is excluded from the VPN.
Best Practices for Mitigating Risks
- Limit Excluded Traffic: Carefully define the specific traffic that will be excluded from the VPN tunnel. Avoid excluding sensitive or critical traffic, such as financial transactions or confidential data.
- Implement Network Segmentation: Divide the local network into separate segments, with the VPN tunnel covering only the critical segments. This helps isolate sensitive traffic and minimizes the risk of exposure.
- Use Strong Authentication: Implement strong authentication mechanisms, such as two-factor authentication, to prevent unauthorized access to the local network and the VPN.
- Monitor Network Activity: Regularly monitor network activity to detect any suspicious or anomalous behavior that could indicate a security breach.
Performance Considerations for WireGuard Split Tunneling
Split tunneling can impact network performance due to the additional routing and processing involved. Here’s an analysis of the impact and tips for optimization:
Network Latency
- Split tunneling introduces an extra hop for traffic destined for the VPN tunnel, increasing latency.
- To mitigate latency, ensure the VPN server is geographically close to the client device.
Bandwidth Utilization
- Split tunneling can increase bandwidth utilization as traffic is duplicated over both the VPN tunnel and the local network.
- Monitor bandwidth usage and adjust split tunneling rules to exclude non-essential traffic from the VPN.
CPU Utilization
- Routing and processing split tunneling traffic can increase CPU utilization on the client device.
- Consider using a hardware-accelerated VPN client or offloading routing to a dedicated device to reduce CPU load.
Memory Consumption
- Split tunneling requires additional memory for routing tables and connection management.
- Ensure the client device has sufficient memory to handle the increased load.
Tips for Optimizing Performance
- Use a high-performance VPN client and server.
- Configure split tunneling rules carefully to minimize unnecessary traffic over the VPN.
- Consider using a dedicated VPN appliance or router to offload processing from the client device.
- Monitor network performance and adjust settings as needed.
Comparison of WireGuard Split Tunneling to Other VPN Protocols
WireGuard split tunneling offers several advantages and disadvantages compared to other VPN protocols. Here’s a comparison:
OpenVPN
- OpenVPN is a mature and widely-used VPN protocol known for its security and stability.
- It supports a wide range of encryption algorithms and authentication methods, providing a high level of customization.
- However, OpenVPN can be more complex to configure and may have a higher performance overhead compared to WireGuard.
IPsec
- IPsec is a suite of protocols used for secure communication at the IP layer.
- It offers strong encryption and authentication mechanisms, making it suitable for high-security applications.
- However, IPsec can be complex to configure and manage, and its performance may be lower than WireGuard.
IKEv2
- IKEv2 is a modern VPN protocol that provides strong security and mobility features.
- It supports fast rekeying and seamless roaming, making it suitable for mobile devices.
- However, IKEv2 may not be as widely supported as other protocols and may have a higher configuration overhead.
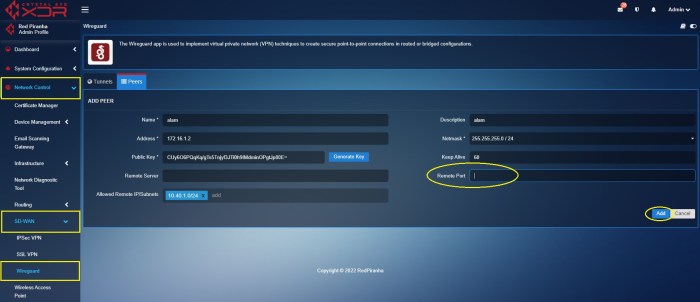
Advanced Configuration Options for WireGuard Split Tunneling

WireGuard split tunneling offers advanced configuration options that provide granular control over the behavior of split tunneling. These options allow administrators to customize the rules and exceptions that determine which traffic is routed through the VPN tunnel and which is sent directly to the internet.
Using AllowedIPs
The AllowedIPs option specifies a list of IP addresses or subnets that are allowed to bypass the VPN tunnel. This option is useful for excluding specific destinations from the VPN tunnel, such as local network resources or internal servers. For example, to exclude the local network from the VPN tunnel, you can use the following configuration:“`[Interface]AllowedIPs = 192.168.1.0/24“`
Using ExcludedIPs
The ExcludedIPs option is the opposite of AllowedIPs. It specifies a list of IP addresses or subnets that are forced to go through the VPN tunnel. This option is useful for ensuring that specific traffic, such as sensitive data or financial transactions, is always routed through the VPN for added security.
For example, to force all traffic to a specific website through the VPN tunnel, you can use the following configuration:“`[Interface]ExcludedIPs = 8.8.8.8“`
Using Table
The Table option allows administrators to create custom routing rules based on a table of IP addresses and subnets. This option provides the most flexibility for controlling split tunneling behavior. For example, to create a table that excludes all traffic from the local network except for a specific IP address, you can use the following configuration:“`[Interface]Table = mytable[Table]mytable = 192.168.1.0/24mytable
= 192.168.1.100“`
Real-World Applications of WireGuard Split Tunneling
WireGuard split tunneling offers a wide range of practical applications in various scenarios, enhancing both network security and performance.
Benefits for Businesses
- Improved Network Security: Split tunneling allows businesses to securely connect remote employees to specific resources within the corporate network while maintaining internet access through their local ISP. This reduces the risk of data breaches by limiting the exposure of sensitive information to the VPN tunnel.
- Enhanced Performance: By directing only necessary traffic through the VPN tunnel, split tunneling reduces network latency and improves overall performance for users accessing local resources and services.
- Simplified Network Management: Split tunneling simplifies network management by eliminating the need for complex routing configurations and firewall rules. It allows administrators to easily manage VPN access for remote users without compromising network security.
Benefits for Individuals
- Enhanced Privacy: Split tunneling enables individuals to access both local and remote resources securely without exposing their entire internet traffic to the VPN provider. This provides greater privacy and reduces the risk of online tracking.
- Improved Performance for Streaming and Gaming: By routing non-VPN traffic directly to the local ISP, split tunneling ensures optimal performance for activities such as streaming videos or playing online games, which require low latency and high bandwidth.
- Access to Geo-Restricted Content: Split tunneling allows individuals to access geo-restricted content from different regions while maintaining local internet access. This is useful for travelers or individuals who want to access content from other countries.
Future Trends in WireGuard Split Tunneling
WireGuard split tunneling is a rapidly evolving technology, with new developments and trends emerging all the time. Here are a few of the most important trends to watch for in the future:
- Increased adoption of WireGuard split tunneling: WireGuard split tunneling is becoming increasingly popular as more and more people become aware of its benefits. This trend is likely to continue in the future, as WireGuard split tunneling becomes more widely available and easier to use.
- Improved performance: The performance of WireGuard split tunneling is constantly improving. New developments, such as the use of hardware acceleration, are making WireGuard split tunneling faster and more efficient. This trend is likely to continue in the future, as WireGuard split tunneling becomes more mature and optimized.
- Increased security: The security of WireGuard split tunneling is also constantly improving. New developments, such as the use of strong encryption algorithms and the implementation of security best practices, are making WireGuard split tunneling more secure. This trend is likely to continue in the future, as WireGuard split tunneling becomes more widely adopted and more widely tested.
Emerging Technologies
In addition to these trends, there are a number of emerging technologies that have the potential to impact the future of WireGuard split tunneling. These technologies include:
- Blockchain technology: Blockchain technology has the potential to be used to create more secure and efficient WireGuard split tunneling solutions. For example, blockchain technology could be used to create a decentralized network of WireGuard servers, which would be more resistant to censorship and hacking.
- Artificial intelligence (AI): AI has the potential to be used to improve the performance and security of WireGuard split tunneling. For example, AI could be used to optimize the routing of traffic through a WireGuard tunnel, or to detect and block malicious traffic.
- Cloud computing: Cloud computing has the potential to make WireGuard split tunneling more accessible and easier to use. For example, cloud computing could be used to provide a managed WireGuard split tunneling service, which would be easier to set up and use than a self-hosted WireGuard split tunneling solution.
These are just a few of the trends and emerging technologies that have the potential to impact the future of WireGuard split tunneling. As these technologies continue to develop, we can expect to see even more innovation and progress in the field of WireGuard split tunneling.
Additional Resources for WireGuard Split Tunneling
For further exploration of WireGuard split tunneling, we recommend the following resources:
Documentation
WireGuard Split Tunneling Documentation
https://www.wireguard.com/split-tunneling/
Microsoft Documentation on WireGuard Split Tunneling
https://docs.microsoft.com/en-us/windows-server/networking/technologies/vpn/split-tunnel-wireguard
Tutorials
Setting Up WireGuard Split Tunneling on Windows
https://www.tecmint.com/setup-wireguard-split-tunneling-windows/
Configuring WireGuard Split Tunneling with AllowedIPs
https://www.linode.com/docs/guides/configure-wireguard-split-tunneling-allowed-ips/
Troubleshooting
Troubleshooting WireGuard Split Tunneling Issues
https://www.wireguard.com/troubleshooting/split-tunneling/
Resolving Common WireGuard Split Tunneling Problems
https://www.techrepublic.com/article/resolving-common-wireguard-split-tunneling-problems/
Best Practices
Best Practices for Implementing WireGuard Split Tunneling
https://www.networkworld.com/article/3656090/best-practices-for-implementing-wireguard-split-tunneling.html
Security Considerations for WireGuard Split Tunneling
https://www.wireguard.com/security-considerations/split-tunneling/