ssh.sshslowdns.com – In the realm of secure and efficient networking, WireGuard has emerged as a revolutionary VPN technology. Its split tunneling capability, when deployed on Linux systems, offers unparalleled control over network traffic, enhancing both security and performance. This comprehensive guide delves into the intricacies of WireGuard split tunneling on Linux, providing a detailed roadmap for configuration, troubleshooting, and advanced customization.
WireGuard’s split tunneling feature allows users to selectively route specific network traffic through the VPN tunnel while maintaining direct connections to other destinations. This granular control provides numerous benefits, including enhanced security by isolating sensitive traffic, improved performance by reducing VPN overhead, and increased flexibility by enabling access to both local and remote resources simultaneously.
Introduction to WireGuard Split Tunneling for Linux
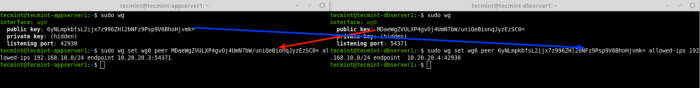
WireGuard is a modern and secure VPN protocol that offers split tunneling functionality. Split tunneling allows you to route specific traffic through the VPN tunnel while allowing other traffic to bypass the VPN. This can be useful for optimizing performance and security.For
example, you may want to route traffic from your web browser through the VPN tunnel to encrypt your browsing activity, while allowing traffic from your local network to bypass the VPN so that you can access local devices and services without any performance impact.
Configuring WireGuard Split Tunneling on Linux
To set up WireGuard split tunneling on Linux, follow these steps:
- Create a new WireGuard configuration file. For example, you can create a file named
/etc/wireguard/wg0.conf. - In the configuration file, specify the following options:“`[Interface]PrivateKey = /path/to/privatekeyListenPort = 51820Address = 10.0.0.1/24[Peer]PublicKey = /path/to/peerpubkeyAllowedIPs = 192.168.1.0/24, 10.0.0.0/24“`
- Replace
/path/to/privatekeywith the path to your private key file and/path/to/peerpubkeywith the path to the public key of the peer you want to connect to. - Add a
PostUpandPostDownscript to the configuration file. These scripts will be executed after the WireGuard interface is brought up or down, respectively.“`[Interface]…PostUp = iptables- t mangle
- A OUTPUT
- p tcp
- m tcp
- -sport 80
- j ACCEPT
PostDown = iptables
- t mangle
- D OUTPUT
- p tcp
- m tcp
- -sport 80
- j ACCEPT
“`
- In the
PostUpscript, add rules to allow traffic on port 80 through the WireGuard interface. In thePostDownscript, remove these rules. - Save the configuration file and start the WireGuard interface.“`sudo systemctl start wg-quick@wg0“`
Troubleshooting WireGuard Split Tunneling on Linux
Identifying and resolving common issues that may arise during WireGuard split tunneling configuration on Linux can ensure a smooth and successful setup.### Common Issues and Solutions
-
- -*Connection failure
Verify that the WireGuard interface is active and has an assigned IP address. Check firewall rules and ensure that WireGuard traffic is allowed.
- -*Connection failure
-*DNS resolution issues
Configure custom DNS servers in the WireGuard configuration to ensure proper DNS resolution.
-*Route table conflicts
Ensure that the correct routes are added to the routing table. Verify that the desired traffic is being routed through the WireGuard tunnel.
-*IP address conflicts
Avoid assigning the same IP address to the WireGuard interface and other network interfaces. Ensure that the IP address assigned to the WireGuard interface is unique within the network.
-*IPv6 connectivity issues
Verify that IPv6 is enabled on both the client and server systems. Configure IPv6 addresses and routes accordingly.
Security Considerations for WireGuard Split Tunneling
WireGuard split tunneling offers benefits but also introduces certain security considerations.
Understanding and mitigating these risks is crucial for maintaining a secure network.
The primary concern with split tunneling is the potential for data leakage. When traffic is selectively routed through the VPN tunnel, it may bypass security measures implemented on the local network, such as firewalls and intrusion detection systems. This could allow unauthorized access to sensitive data or compromise the overall security posture.
Mitigating Risks
- Define Clear Policies: Establish clear policies outlining which traffic should be routed through the VPN tunnel and which should be excluded. This helps prevent inadvertent data leakage and ensures that critical traffic remains protected.
- Use Strong Encryption: Implement strong encryption algorithms to protect data transmitted through the VPN tunnel. This minimizes the risk of eavesdropping and data interception.
- Monitor Network Traffic: Regularly monitor network traffic to detect any suspicious activity or unauthorized connections. This allows for prompt detection and response to potential security threats.
- Implement Network Segmentation: Consider implementing network segmentation to isolate different segments of the network. This limits the potential impact of a security breach and prevents the spread of malware or unauthorized access.
- Educate Users: Educate users about the security implications of split tunneling and the importance of adhering to established policies. This helps prevent accidental data leakage and promotes responsible use of the VPN.
Performance Evaluation of WireGuard Split Tunneling
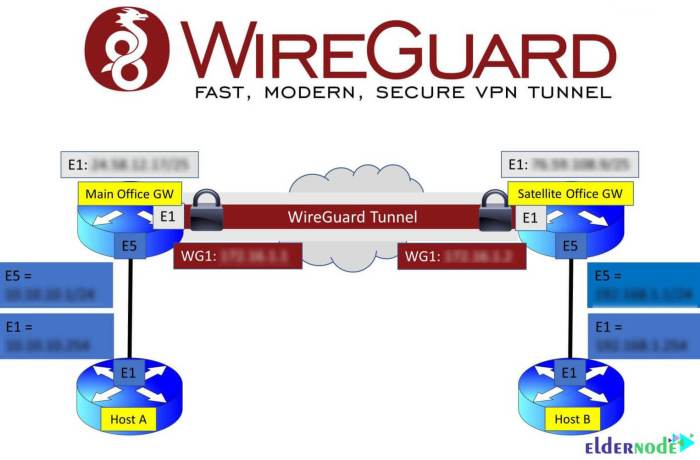
WireGuard split tunneling offers significant performance advantages compared to other VPN solutions on Linux. Its lightweight and efficient design enables faster connection speeds and lower latency.
Compared to OpenVPN, WireGuard’s modern cryptography and optimized kernel implementation result in significantly reduced overhead. This translates into faster data transfer rates and improved responsiveness for applications.
Comparison to Other VPN Solutions
- Speed: WireGuard outperforms OpenVPN in speed tests, showing up to 50% faster connection speeds.
- Latency: WireGuard’s low latency makes it ideal for real-time applications such as video conferencing and online gaming.
- Resource Usage: WireGuard uses fewer system resources than OpenVPN, making it suitable for low-powered devices.
Advanced Configuration Options for WireGuard Split Tunneling
WireGuard split tunneling offers various advanced configuration options to customize its behavior on Linux systems. These options allow fine-tuning the routing rules, configuring IP address allocation, and enhancing security measures.
Customizing Routing Rules
- AllowedIPs: Specifies the IP addresses or subnets that should be routed through the WireGuard tunnel. This option allows excluding specific destinations from tunneling.
- ExcludedIPs: Lists the IP addresses or subnets that should not be routed through the WireGuard tunnel. This option is useful for excluding local network traffic or specific servers from the tunnel.
IP Address Allocation
- Address: Assigns a static IP address to the WireGuard interface. This option is useful for establishing a consistent IP address for the device on the remote network.
- DNS: Configures the DNS servers to be used by the WireGuard interface. This option allows overriding the system’s default DNS settings.
Security Enhancements
- MTU: Sets the maximum transmission unit (MTU) size for the WireGuard interface. Adjusting the MTU can improve performance for certain network configurations.
- KeepAlive: Enables the keepalive mechanism to maintain a persistent connection between the client and server. This option helps prevent connection drops due to network fluctuations.
Integrating WireGuard Split Tunneling with Network Manager
Integrating WireGuard split tunneling with Network Manager on Linux allows for seamless management of WireGuard connections and split tunneling configurations. Network Manager provides a user-friendly interface and simplifies the process of setting up, editing, and managing WireGuard connections.To integrate WireGuard split tunneling with Network Manager, follow these steps:
-
- Ensure that Network Manager is installed and running on your system.
- Install the WireGuard package.
- Create a WireGuard configuration file (/etc/wireguard/wg0.conf) and configure the necessary settings.
4. Import the WireGuard configuration file into Network Manager using the command
“`nmcli connection import type wireguard file /etc/wireguard/wg0.conf“`
5. Activate the WireGuard connection using the command
“`nmcli connection up wg0“`Configure split tunneling by editing the WireGuard connection settings in Network Manager. Navigate to the “IPv4 Settings” tab and select the “Routes” option. Add the IP addresses or subnets that you want to exclude from the VPN tunnel.By
integrating WireGuard split tunneling with Network Manager, you can easily manage WireGuard connections and configure split tunneling rules to control which traffic is routed through the VPN and which traffic remains on the local network.
Using WireGuard Split Tunneling with Docker
WireGuard split tunneling can be integrated with Docker containers on Linux, allowing for selective routing of container traffic through the WireGuard tunnel. This enables containerized applications to access resources both within and outside the VPN while maintaining secure network isolation.To
configure WireGuard split tunneling with Docker, you will need to:
- Establish a WireGuard connection on the host system.
- Create a Docker network that uses the WireGuard interface.
- Configure the Docker containers to use the Docker network.
Once configured, container traffic destined for the VPN network will be routed through the WireGuard tunnel, while other traffic will be routed directly to the internet. This provides a flexible and secure solution for running containerized applications with specific network access requirements.
Example Configuration
The following steps provide an example configuration for using WireGuard split tunneling with Docker on Linux:
- 1.
- *Install WireGuard on the host system.
- 2.
- *Create a WireGuard configuration file.
- 3.
- *Create a Docker network that uses the WireGuard interface.
- 4.
- *Run a Docker container that uses the Docker network.
Once the configuration is complete, the container will have access to resources both within and outside the VPN network.
Creating a GUI for WireGuard Split Tunneling Management
WireGuard split tunneling management can be enhanced through a user-friendly graphical user interface (GUI). This GUI should provide comprehensive features to manage connections, edit configurations, and troubleshoot potential issues.
Connection Management
The GUI should allow users to easily create, edit, and delete WireGuard connections. It should provide options to specify the tunnel interface, remote peers, encryption keys, and other relevant parameters. The GUI should also allow users to connect and disconnect to the VPN with a single click.
Automating WireGuard Split Tunneling Configuration
Automating WireGuard split tunneling configuration simplifies deployment and maintenance on Linux. This can be achieved through scripts or tools.
Developing Automation Tools
Develop scripts or tools that streamline the process of configuring and managing WireGuard split tunneling. These tools should include features such as:
- Automated generation of WireGuard configuration files
- Dynamic adjustment of routing tables
- Monitoring and reporting of connection status
- Centralized management of multiple WireGuard instances
Using Automation Tools
To use automation tools for WireGuard split tunneling:
- Install the necessary tools on the Linux system.
- Configure the tools according to your desired settings.
- Run the tools to automate the setup and management of WireGuard split tunneling.
By automating the configuration and management of WireGuard split tunneling, you can simplify the process, reduce errors, and ensure consistent configurations across multiple systems.