ssh.sshslowdns.com – In the realm of virtual private networks (VPNs), WireGuard has emerged as a game-changer, offering unparalleled speed, security, and flexibility. One of its most compelling features is split tunneling, which allows you to selectively route specific traffic through the VPN while excluding others.
This guide will delve into the intricacies of WireGuard split tunneling on Linux, providing a comprehensive overview of its benefits, use cases, configuration techniques, and potential pitfalls. By the end of this discussion, you will be equipped with the knowledge and skills to implement split tunneling effectively and securely.
WireGuard Split Tunneling
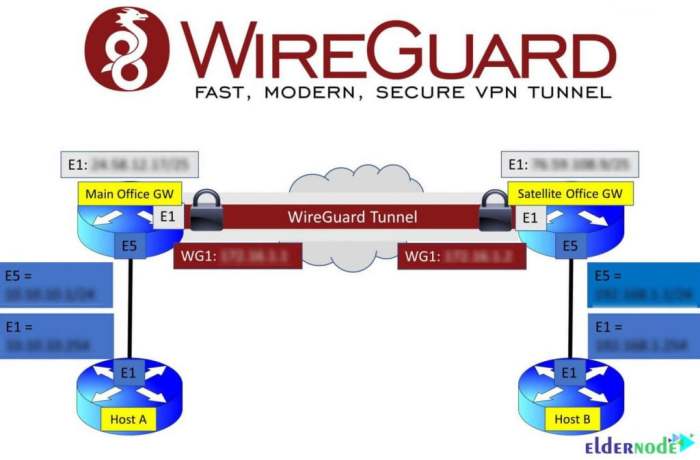
WireGuard split tunneling on Linux is a feature that allows you to selectively route traffic through the WireGuard VPN tunnel, while other traffic is sent directly over the regular network connection. This can be useful for performance reasons, as it can reduce the amount of traffic that is encrypted and decrypted by the VPN, or for security reasons, as it can prevent certain types of traffic from being exposed to the VPN.There
are a number of different ways to configure split tunneling with WireGuard on Linux. One common method is to use the `AllowedIPs` option in the WireGuard configuration file. This option specifies a list of IP addresses or subnets that will be routed through the VPN tunnel.
Any traffic destined for IP addresses outside of this list will be sent over the regular network connection.Another method of configuring split tunneling with WireGuard is to use the `Table` option in the WireGuard configuration file. This option specifies a routing table that will be used to determine which traffic is sent through the VPN tunnel.
You can create a custom routing table that includes specific IP addresses or subnets that you want to route through the VPN tunnel.Split tunneling can be a useful feature for improving the performance and security of your WireGuard VPN connection.
By selectively routing traffic through the VPN tunnel, you can reduce the amount of overhead associated with the VPN connection and protect sensitive traffic from exposure to the VPN.
Use Cases for Split Tunneling with WireGuard
There are a number of different use cases for split tunneling with WireGuard. Some common use cases include:
- Performance optimization: Split tunneling can be used to improve the performance of your WireGuard VPN connection by reducing the amount of traffic that is encrypted and decrypted by the VPN. This can be especially beneficial for applications that are sensitive to latency, such as online gaming or video streaming.
- Security enhancement: Split tunneling can be used to enhance the security of your WireGuard VPN connection by preventing certain types of traffic from being exposed to the VPN. This can be useful for protecting sensitive data, such as financial information or medical records, from being intercepted by attackers.
- Network segmentation: Split tunneling can be used to segment your network traffic into different zones. For example, you could use split tunneling to send work traffic through the VPN tunnel while sending personal traffic over the regular network connection.
Configuring WireGuard Split Tunneling
To configure WireGuard split tunneling on Linux, follow these steps:
- Create a WireGuard configuration file. For example:
“`[Interface]Address = 10.0.0.1/24ListenPort = 51820PrivateKey = /etc/wireguard/privatekeyPostUp = iptables
- t mangle
- A OUTPUT
- p udp
- m udp
- -dport 53
- j ACCEPT
PostDown = iptables
- t mangle
- D OUTPUT
- p udp
- m udp
- -dport 53
- j ACCEPT
- Add split tunneling rules to the configuration file. For example:
“`[Interface]…DNS = 8.8.8.8[Peer]…AllowedIPs = 10.0.0.2/32, 192.168.1.0/24“`
This allows traffic to 192.168.1.0/24 to bypass the VPN, while all other traffic is routed through the VPN.
- Activate the WireGuard interface:
“`sudo wg-quick up “`
Split tunneling is now configured for WireGuard on Linux.
Options for Configuring Split Tunneling Rules
There are several options for configuring split tunneling rules in WireGuard:
- AllowedIPs: Specifies the IP addresses or subnets that should bypass the VPN.
- DNS: Specifies the DNS servers that should be used for traffic bypassing the VPN.
- Table: Specifies the routing table that should be used for traffic bypassing the VPN.
Advanced Split Tunneling Techniques
Split tunneling can be further enhanced using advanced techniques that provide greater control over traffic routing. These techniques include excluding specific subnets from the tunnel and using multiple WireGuard interfaces.
Excluding Specific Subnets
In certain scenarios, you may want to exclude specific subnets from being routed through the WireGuard tunnel. This can be useful for accessing local network resources or optimizing performance for specific applications. To exclude a subnet, use the “AllowedIPs” directive in the WireGuard configuration file.
For example, to exclude the subnet 192.168.1.0/24, add the following line: AllowedIPs = 0.0.0.0/0, 192.168.1.0/24
Using Multiple WireGuard Interfaces
Another advanced technique is to use multiple WireGuard interfaces. This allows you to create separate tunnels for different purposes, such as routing traffic from specific applications or devices. To create multiple interfaces, use the “Interface” directive in the WireGuard configuration file.
For example, to create an interface named “wg0” and another named “wg1”, add the following lines: [Interface]Address = 10.0.0.1/24ListenPort = 51820[Interface]Address = 10.0.0.2/24ListenPort = 51821Name = wg1 Once you have created multiple interfaces, you can configure traffic routing rules to direct traffic through the appropriate interface.
This can be done using firewall rules or by configuring the routing table.
Troubleshooting Split Tunneling
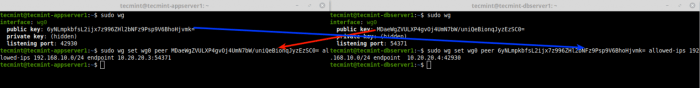
Split tunneling is a powerful feature that allows you to route specific traffic through a VPN tunnel while allowing other traffic to go directly to the internet. However, it can sometimes be challenging to set up and troubleshoot. In this section, we will identify some common troubleshooting scenarios and offer solutions and best practices for resolving these issues.
Identifying Common Troubleshooting Scenarios
- The VPN connection is not working at all.
- Some traffic is not going through the VPN tunnel.
- The VPN tunnel is dropping intermittently.
- The VPN connection is slow.
Resolving Split Tunneling Issues
There are a few things you can do to troubleshoot split tunneling issues:
- Check your firewall settings. Make sure that the VPN traffic is allowed through your firewall.
- Check your routing table. Make sure that the VPN traffic is being routed through the VPN tunnel.
- Check your DNS settings. Make sure that the VPN traffic is using the correct DNS servers.
- Restart your VPN client. Sometimes, a simple restart can fix split tunneling issues.
- Update your VPN client. Make sure that you are using the latest version of your VPN client.
- Contact your VPN provider. If you are still having trouble troubleshooting split tunneling issues, contact your VPN provider for help.
Performance Considerations
WireGuard split tunneling can impact network performance in various ways. Understanding these implications is crucial for optimizing performance based on specific use cases.
Routing Overhead
Split tunneling introduces additional routing overhead due to the need to maintain separate routing tables for local and tunnel traffic. This overhead can be minimal for small networks but can become significant in complex environments with multiple subnets and traffic flows.
Packet Processing Overhead
Each packet traversing the WireGuard tunnel incurs additional processing overhead due to encryption and decryption. This overhead is typically negligible for high-speed connections but can affect latency-sensitive applications or low-powered devices.
Network Latency
The latency introduced by WireGuard split tunneling depends on the distance between the client and the server, the network conditions, and the encryption algorithm used. Latency can be a concern for real-time applications such as gaming or video conferencing.
Optimizing Performance
Optimizing performance for split tunneling involves balancing security and performance requirements. Here are some guidelines:
- Choose an appropriate encryption algorithm: ChaCha20 is a good choice for low-latency applications, while AES-256 provides stronger security but with higher overhead.
- Use a dedicated WireGuard server: Running WireGuard on a separate server dedicated to tunneling can improve performance by reducing contention and latency.
- Optimize routing: Configure routing tables efficiently to minimize routing overhead. Consider using static routes or policy-based routing.
- Monitor performance: Regularly monitor network performance using tools like Wireshark or tcpdump to identify potential bottlenecks and optimize accordingly.
Security Implications
WireGuard split tunneling introduces several security considerations that need to be carefully evaluated before implementation.
Potential Risks
Increased Attack Surface
Split tunneling creates an additional attack vector by allowing specific traffic to bypass the VPN tunnel. This can potentially expose sensitive data or systems to malicious actors who exploit vulnerabilities in the unprotected network segments.
Data Leakage
Unprotected traffic can inadvertently leak sensitive information, such as user credentials, financial data, or confidential documents, to untrusted networks. This can lead to data breaches or identity theft.
Malware Propagation
Malware or viruses can spread more easily within the unprotected network segments, as they can bypass the VPN’s security controls. This can result in widespread infections and data loss.
Mitigation Strategies
Strong Authentication
Implement robust authentication mechanisms, such as multi-factor authentication or hardware tokens, to protect access to the VPN and the unprotected network segments.
Network Segmentation
Divide the network into separate segments based on sensitivity and assign appropriate security measures to each segment. This limits the potential impact of a security breach.
Firewall Rules
Configure firewall rules to restrict access to sensitive resources only from trusted IP addresses or within the VPN tunnel. This helps prevent unauthorized access and data leakage.
Regular Security Audits
Conduct regular security audits to identify vulnerabilities and ensure that security measures are effective. This helps maintain a strong security posture.
User Education
Educate users about the risks associated with split tunneling and provide guidance on how to protect their data and devices. This promotes responsible use and reduces the likelihood of security incidents.
Comparison with Other VPN Technologies
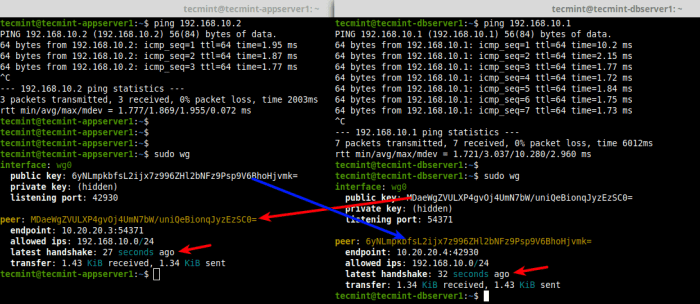
WireGuard split tunneling offers several advantages over other VPN technologies that provide similar functionality. One of the main advantages is its simplicity and ease of configuration. WireGuard is designed to be lightweight and efficient, with a minimal configuration process. This makes it an attractive option for users who want to quickly and easily set up split tunneling without having to deal with complex configuration settings.Another
advantage of WireGuard is its performance. WireGuard is known for its high speeds and low latency, which makes it a good choice for users who require fast and reliable VPN connections. Additionally, WireGuard’s modern encryption protocols provide strong security, ensuring that user data is protected from eavesdropping and other threats.However,
it’s important to note that WireGuard is still a relatively new technology, and it may not be as widely supported as some other VPN technologies. This means that users may encounter compatibility issues with certain devices or operating systems. Additionally, WireGuard’s lack of advanced features, such as support for multiple VPN gateways or dynamic routing, may be a limitation for users who require more complex VPN configurations.Overall,
WireGuard split tunneling is a good choice for users who prioritize simplicity, performance, and security. However, users who require advanced features or wide compatibility may want to consider other VPN technologies that offer a broader range of capabilities.
OpenVPN
OpenVPN is a well-established VPN technology that offers a wide range of features and customization options. OpenVPN is known for its strong security and support for a variety of platforms and devices. However, OpenVPN can be more complex to configure than WireGuard, and it may not be as performant in some cases.
IPsec
IPsec is a standards-based VPN technology that is widely supported by a variety of devices and operating systems. IPsec offers a high level of security and flexibility, but it can be complex to configure and manage. Additionally, IPsec can be less performant than WireGuard, especially on mobile devices.
Comparison Table
The following table provides a comparison of WireGuard split tunneling with OpenVPN and IPsec:| Feature | WireGuard | OpenVPN | IPsec ||—|—|—|—|| Simplicity and ease of configuration | High | Medium | Low || Performance | High | Medium | Low || Security | High | High | High || Compatibility | Medium | High | High || Advanced features | Low | High | High |
Use Cases for Split Tunneling
WireGuard split tunneling offers several practical use cases where selective routing of network traffic can enhance privacy, security, and performance.
Accessing Local Network Resources
Split tunneling allows users to access local network resources, such as printers, file servers, and intranet applications, while simultaneously routing internet traffic through the VPN. This is particularly beneficial for remote workers or employees who need to access company resources from home or public Wi-Fi networks.
Improving Internet Performance
By selectively routing only specific traffic through the VPN, split tunneling can improve internet performance. For instance, users can exclude streaming services, gaming platforms, or large file downloads from the VPN tunnel, ensuring optimal bandwidth and reduced latency for these activities.
Enhancing Privacy
Split tunneling provides increased privacy by preventing sensitive local network traffic from being exposed through the VPN. This is particularly useful for individuals concerned about their privacy on public Wi-Fi networks or when using untrusted internet connections.
Compliance and Security
Organizations can use split tunneling to enforce compliance with security policies. By routing only work-related traffic through the VPN, they can prevent employees from accessing unauthorized websites or downloading potentially malicious content while connected to the company network.
Cost Optimization
Split tunneling can help reduce VPN costs by selectively routing traffic through the VPN. This is especially beneficial for organizations with limited bandwidth or when VPN usage is primarily for accessing specific resources or applications.
Best Practices for Implementing Split Tunneling
Split tunneling allows you to selectively route traffic through a VPN tunnel while allowing other traffic to bypass the tunnel. This can improve performance and security by reducing the amount of traffic that goes through the VPN tunnel.There are a few best practices to follow when implementing split tunneling:
- Only route traffic that needs to go through the VPN tunnel. This will help to improve performance and reduce the risk of security breaches.
- Use strong encryption and authentication methods to protect the traffic that goes through the VPN tunnel.
- Monitor the VPN tunnel to ensure that it is working properly and that there are no security breaches.
Rule Management
When configuring split tunneling, you need to create rules that specify which traffic should go through the VPN tunnel and which traffic should bypass the tunnel. The rules can be based on the source IP address, destination IP address, port number, or protocol.It
is important to carefully consider the rules that you create. If you create rules that are too broad, then too much traffic will go through the VPN tunnel, which can impact performance. If you create rules that are too narrow, then some traffic that should go through the VPN tunnel will bypass the tunnel, which can create a security risk.
Monitoring
It is important to monitor the VPN tunnel to ensure that it is working properly and that there are no security breaches. You can use tools such as ping and traceroute to test the connectivity of the VPN tunnel. You can also use tools such as Wireshark to analyze the traffic that is going through the VPN tunnel.
Future Developments in Split Tunneling
As the technology landscape continues to evolve, split tunneling is expected to witness significant advancements in the years to come. These developments will likely revolve around enhancing security, improving performance, and expanding the range of applications where split tunneling can be effectively deployed.
One potential area of development is the integration of advanced encryption algorithms and security protocols into split tunneling solutions. This will further strengthen the protection of sensitive data and communications, making it even more difficult for unauthorized individuals to access private information.
Enhanced Performance
Another area of focus is the optimization of split tunneling performance. Future developments may include the implementation of new traffic routing algorithms and network optimization techniques. These advancements will enable split tunneling solutions to handle increased traffic loads more efficiently, resulting in faster and more reliable connections.
Expanded Applications
The future of split tunneling also holds the promise of expanding its applications to new and emerging technologies. For instance, split tunneling could be integrated into cloud computing environments, allowing users to securely access cloud resources while maintaining local network connectivity.
Additionally, split tunneling could play a crucial role in the development of next-generation IoT devices, enabling secure communication between IoT devices and both local and remote networks.