ssh.sshslowdns.com – In the realm of virtual private networks (VPNs), WireGuard has emerged as a game-changer, offering lightning-fast speeds, robust security, and an innovative feature known as split tunneling. This feature empowers you to route specific traffic through the VPN while allowing other traffic to bypass it, providing a unique blend of security and flexibility.
WireGuard split tunneling grants you granular control over your network traffic, enabling you to safeguard sensitive data while maintaining seamless access to local resources. In this comprehensive guide, we will delve into the intricacies of WireGuard split tunneling, exploring its benefits, drawbacks, configuration methods, and use cases.
Introduction
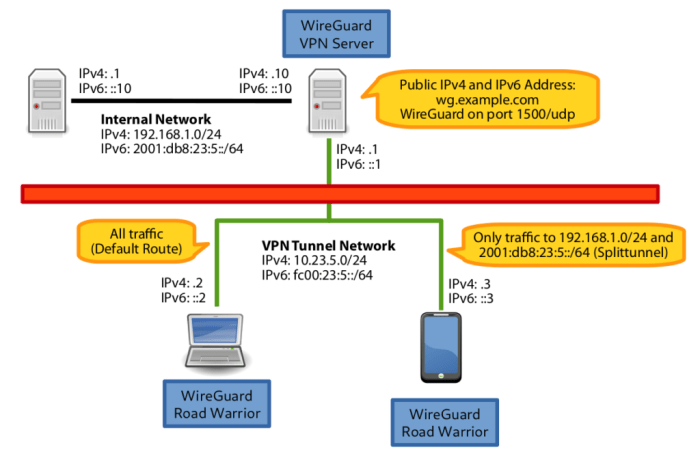
WireGuard split tunneling is a networking technique that allows you to route specific traffic through a virtual private network (VPN) while allowing other traffic to bypass the VPN and connect directly to the internet. This can be useful for situations where you want to protect sensitive traffic, such as banking or financial data, while still allowing other traffic, such as streaming or gaming, to connect directly to the internet for better performance.
There are several benefits to using WireGuard split tunneling. First, it can improve performance for traffic that does not need to be protected by the VPN. This is because traffic that bypasses the VPN does not have to be encrypted and decrypted, which can save time and resources.
Second, split tunneling can help to reduce the risk of data leaks. By only routing specific traffic through the VPN, you can reduce the risk of sensitive data being exposed if the VPN connection is compromised.
However, there are also some drawbacks to using WireGuard split tunneling. First, it can be more difficult to configure than a traditional VPN connection. Second, split tunneling can create security risks if it is not configured properly. For example, if you allow all traffic to bypass the VPN, then all of your traffic will be exposed to the internet, even if you only intended for specific traffic to bypass the VPN.
Configuring WireGuard Split Tunneling
WireGuard split tunneling allows you to selectively route specific traffic through the VPN tunnel while allowing other traffic to bypass the VPN. This can be useful for optimizing performance and security.To configure WireGuard split tunneling, you will need to edit the WireGuard configuration file on your device.
The specific steps will vary depending on your operating system.
Windows
To configure WireGuard split tunneling on Windows, open the WireGuard configuration file (usually located at C:\Program Files\WireGuard\wg0.conf ) in a text editor. Add the following lines to the file:“`[Interface]DNS = 8.8.8.8DNS = 8.8.4.4AllowedIPs = 0.0.0.0/0“`Replace
0.0.0.0/0 with the IP address range that you want to bypass the VPN.
Linux
To configure WireGuard split tunneling on Linux, open the WireGuard configuration file (usually located at /etc/wireguard/wg0.conf ) in a text editor. Add the following lines to the file:“`[Interface]DNS = 8.8.8.8DNS = 8.8.4.4AllowedIPs = 0.0.0.0/0“`Replace
0.0.0.0/0 with the IP address range that you want to bypass the VPN.
macOS
To configure WireGuard split tunneling on macOS, open the WireGuard configuration file (usually located at /Library/Application Support/WireGuard/wg0.conf ) in a text editor. Add the following lines to the file:“`[Interface]DNS = 8.8.8.8DNS = 8.8.4.4AllowedIPs = 0.0.0.0/0“`Replace
0.0.0.0/0 with the IP address range that you want to bypass the VPN.
Use Cases for WireGuard Split Tunneling
WireGuard split tunneling offers versatility in network configurations, enabling tailored routing of traffic based on specific criteria. Let’s explore some practical use cases that demonstrate its advantages.
Enhancing Security and Privacy
Split tunneling allows selective routing of traffic through the VPN tunnel, enhancing security and privacy by limiting the exposure of sensitive data to untrusted networks. For instance, you can configure your VPN to route only work-related traffic through the tunnel while excluding personal browsing or online banking activities.
Accessing Local Resources
Split tunneling provides seamless access to local resources within a private network while connected to a VPN. This feature is particularly useful for accessing intranet sites, printers, or shared drives without compromising the security of the VPN connection.
Optimizing Network Performance
By selectively routing only necessary traffic through the VPN tunnel, split tunneling can optimize network performance by reducing bandwidth consumption and minimizing latency. This is beneficial for applications that require high bandwidth, such as video streaming or large file transfers.
Complying with Regulations
Split tunneling can assist in compliance with data protection regulations by ensuring that specific types of traffic, such as financial transactions or sensitive data, are routed through a secure VPN connection.
Flexible Network Management
Split tunneling empowers administrators with granular control over network traffic, allowing them to implement customized routing rules based on source/destination IP addresses, protocols, or application-specific criteria.
Performance Considerations
WireGuard split tunneling may impact network performance due to additional routing and processing overhead.
Optimizing Performance
To mitigate potential performance issues:
- Use efficient encryption algorithms: Choose algorithms like ChaCha20 or BLAKE2s, which offer good performance while maintaining security.
- Configure MTU (Maximum Transmission Unit): Adjust the MTU to match the network interface’s MTU to avoid fragmentation and performance degradation.
- Use hardware acceleration: If available, utilize hardware acceleration features on the device to offload encryption and routing tasks, improving performance.
Troubleshooting WireGuard Split Tunneling
WireGuard split tunneling is a powerful tool, but it can also be complex to configure and troubleshoot. Here are some common issues that may arise when using WireGuard split tunneling, along with solutions for resolving them:
Incorrect network configuration
- Ensure that the WireGuard interface is configured correctly and has the appropriate IP address and subnet mask.
- Verify that the routing table is configured to route traffic through the WireGuard interface for the desired networks.
Firewall rules blocking traffic
- Check the firewall rules on the device to ensure that traffic is allowed through the WireGuard interface.
- If necessary, create firewall rules to allow traffic from the desired networks through the WireGuard interface.
DNS issues
- Ensure that the DNS settings are configured correctly on the device.
- If necessary, configure the WireGuard interface to use a specific DNS server.
MTU issues
- The MTU (Maximum Transmission Unit) of the WireGuard interface may need to be adjusted to match the MTU of the underlying network.
- To adjust the MTU, edit the WireGuard configuration file and set the “MTU” parameter to the desired value.
Comparison with Other VPN Tunneling Protocols
WireGuard split tunneling stands out from other VPN tunneling protocols like OpenVPN and IPsec in several ways. It offers a unique combination of performance, security, and ease of use that makes it an attractive option for various use cases.
OpenVPN
- Advantages: OpenVPN is an established and widely used protocol known for its robust security features and support for a wide range of platforms and devices.
- Disadvantages: OpenVPN can be more complex to configure and manage compared to WireGuard, and its performance may be lower in certain scenarios.
IPsec
- Advantages: IPsec is a mature and well-supported protocol that provides strong security and is widely deployed in enterprise networks.
- Disadvantages: IPsec is more complex to configure and manage than WireGuard, and its performance may be lower due to its reliance on encryption and decryption overhead.
Security Considerations
WireGuard split tunneling offers security advantages over traditional VPN tunneling, but it also introduces unique security implications that need to be considered.
One potential risk is that split tunneling can expose your local network to untrusted traffic. If a malicious actor gains access to your device while split tunneling is enabled, they could potentially exploit vulnerabilities in your local network to launch attacks on other devices or steal sensitive data.
Best Practices for Securing WireGuard Split Tunneling Connections
- Use strong encryption: WireGuard uses robust encryption algorithms by default, but it’s important to ensure that you’re using strong encryption settings for both the VPN connection and your local network.
- Implement firewall rules: Configure firewall rules on your device to restrict access to your local network from untrusted sources. This will help prevent malicious actors from exploiting vulnerabilities in your local network.
- Monitor your network traffic: Regularly monitor your network traffic for suspicious activity. This will help you identify and mitigate any potential security threats.
- Use a reputable VPN provider: Choose a VPN provider that has a proven track record of security and privacy. This will help ensure that your VPN connection is secure and reliable.
Advanced Configuration
WireGuard split tunneling offers a range of advanced configuration options to customize its behavior and meet specific networking requirements. These options allow administrators to fine-tune the split tunneling functionality, enabling granular control over traffic routing.
One of the key advanced configuration options is the ability to specify custom DNS servers. By default, WireGuard uses the DNS servers provided by the VPN server, but administrators can override these settings to use custom DNS servers for specific domains or applications.
This can be useful for optimizing DNS resolution performance or accessing region-specific content.
Another advanced configuration option is the ability to define custom firewall rules. These rules allow administrators to control which traffic is allowed to pass through the VPN tunnel and which traffic is routed directly over the local network connection. This provides a high level of flexibility in managing network access and security.
Customizing Interface Binding
WireGuard split tunneling allows administrators to specify the network interface to which the VPN tunnel is bound. By default, WireGuard binds to the default network interface, but administrators can manually specify a different interface to use. This can be useful for scenarios where multiple network interfaces are available, such as in multi-homed systems or virtual machines with multiple virtual network interfaces.
Fine-tuning Routing Behavior
WireGuard split tunneling provides granular control over routing behavior. Administrators can configure specific routes to be excluded from the VPN tunnel, ensuring that certain traffic always uses the local network connection. This can be useful for optimizing performance for latency-sensitive applications or accessing local resources that should not be routed through the VPN.
Additional Advanced Options
In addition to the aforementioned advanced configuration options, WireGuard split tunneling also supports a range of other advanced features, including:
- Port forwarding: Allows administrators to forward specific ports from the VPN tunnel to the local network, enabling remote access to services running on the local network.
- IPv6 support: Provides support for IPv6 traffic, allowing administrators to configure WireGuard split tunneling for both IPv4 and IPv6 networks.
- MTU (Maximum Transmission Unit) adjustment: Allows administrators to adjust the MTU size for the VPN tunnel, optimizing performance for specific network configurations.
Integration with Other Tools
WireGuard split tunneling can be integrated with other security tools to enhance network security. By selectively routing traffic through the VPN tunnel, organizations can implement a layered security approach that combines the benefits of both local and remote security measures.
Integrating WireGuard split tunneling with firewalls allows for granular control over network traffic. Firewalls can be configured to block or allow specific types of traffic, while WireGuard split tunneling can route traffic from specific applications or subnets through the VPN tunnel, providing an additional layer of protection for sensitive data.
Intrusion Detection Systems (IDS)
WireGuard split tunneling can also be integrated with intrusion detection systems (IDS) to enhance threat detection and response. By monitoring traffic passing through the VPN tunnel, IDS can identify suspicious activity and trigger alerts, allowing security teams to respond quickly to potential threats.
Future Developments
WireGuard split tunneling technology is still in its early stages of development, but it has the potential to revolutionize the way we use VPNs. As the technology matures, we can expect to see new features and use cases emerge.
One potential future development is the integration of split tunneling with other network technologies, such as SD-WAN and cloud networking. This would allow businesses to create more complex and flexible network configurations that can meet the specific needs of their applications.
New Use Cases
As split tunneling becomes more widely adopted, we can expect to see new use cases emerge. For example, split tunneling could be used to: