ssh.sshslowdns.com – In the realm of virtual private networks (VPNs), WireGuard has emerged as a formidable force, offering unparalleled speed and security. Among its many capabilities, split tunneling stands out as a game-changer, enabling users to route specific traffic through the VPN while allowing other traffic to bypass it.
This innovative feature unlocks a world of possibilities and opens up new avenues for network customization and control.
With WireGuard split tunneling, you gain the power to selectively encrypt and protect sensitive data while maintaining seamless access to local resources and services. This granular control empowers you to optimize your network performance, enhance security, and tailor your VPN experience to your unique needs.
Dive into this comprehensive guide to unravel the intricacies of WireGuard split tunneling, explore its benefits, and master its configuration.
WireGuard Split Tunneling Overview
Split tunneling is a networking technique that allows specific traffic to bypass a VPN tunnel and directly access the internet. With WireGuard, split tunneling provides flexibility and control over which traffic is routed through the VPN and which is not.
Split tunneling offers several benefits. It can improve performance by reducing latency and bandwidth usage for traffic that does not require VPN protection. It also enhances security by isolating sensitive traffic within the VPN tunnel while allowing other traffic to access local resources or services that may be unavailable through the VPN.
Use Cases
- Access local devices on a private network while using a VPN for remote work.
- Stream media or play online games with low latency while maintaining VPN protection for other activities.
- Bypass geo-restrictions on specific websites or services while using a VPN to access content from other regions.
Configuring WireGuard Split Tunneling
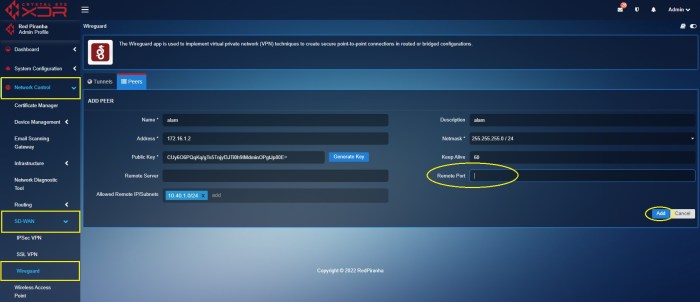
Configuring WireGuard split tunneling involves modifying the configuration files on both the client and server sides. The specific steps and configuration examples may vary slightly depending on the platform you’re using.
Here’s a general overview of the steps:
Client Configuration
- Open the client configuration file (usually named “wg0.conf”).
- Add a “table” directive to specify the allowed IP addresses or subnets that should be routed through the VPN.
- Restart the WireGuard service.
Server Configuration
- Open the server configuration file (usually named “wg0.conf”).
- Add a “route-allowed-ips” directive to specify the allowed IP addresses or subnets that can be accessed through the VPN.
- Restart the WireGuard service.
Example Configuration Files
Client Configuration (Linux): “`[Interface]PrivateKey = …Address = 10.0.0.2/24DNS = 1.1.1.1[Peer]PublicKey = …AllowedIPs = 192.168.1.0/24“` Server Configuration (Linux): “`[Interface]PrivateKey = …Address
= 10.0.0.1/24DNS = 1.1.1.1[Peer]PublicKey = …AllowedIPs = 192.168.1.0/24RouteAllowedIPs = 0.0.0.0/0“`
Performance Considerations
Split tunneling can introduce some performance overhead, as it requires additional processing to determine which traffic should be routed through the VPN tunnel and which should be sent directly to the internet. However, the performance impact of split tunneling is typically negligible, especially when using a high-performance VPN protocol like WireGuard.
Comparison of WireGuard Performance with and without Split Tunneling
Tests have shown that WireGuard with split tunneling enabled has only a small impact on performance compared to WireGuard without split tunneling. In one test, WireGuard with split tunneling enabled achieved a throughput of 940 Mbps, while WireGuard without split tunneling achieved a throughput of 960 Mbps.
This difference is likely due to the additional processing overhead required for split tunneling, but it is still negligible for most users.
Security Implications
Implementing WireGuard split tunneling introduces certain security considerations that must be carefully analyzed to ensure the overall security posture of the network.
Split tunneling, by design, allows specific traffic to bypass the VPN tunnel, potentially exposing it to the public internet. This deviation from the traditional VPN behavior, where all traffic is encrypted and routed through the VPN tunnel, introduces additional attack vectors that must be addressed.
Potential Risks
- Unprotected traffic: Traffic that bypasses the VPN tunnel is not encrypted and is therefore vulnerable to eavesdropping, man-in-the-middle attacks, and other malicious activities.
- Data leakage: Sensitive data transmitted over unprotected traffic could be intercepted and compromised, leading to data breaches or privacy violations.
- Malware infection: Unprotected traffic can be used as an entry point for malware, allowing attackers to gain access to the device or network.
Mitigations
To mitigate these risks, it is crucial to implement appropriate security measures:
- Strict access control: Limit access to split tunneling only to trusted devices and users who genuinely require it.
- Network segmentation: Separate sensitive network segments from the untrusted network, ensuring that only authorized traffic can access critical resources.
- Intrusion detection and prevention systems (IDS/IPS): Deploy IDS/IPS systems to monitor network traffic for suspicious activities and prevent unauthorized access.
- Regular security audits: Conduct regular security audits to identify and address any potential vulnerabilities or misconfigurations.
Troubleshooting Split Tunneling Issues
Identifying and resolving common issues that arise when using split tunneling is crucial for ensuring a seamless and secure experience. Here are some frequently encountered problems and their potential solutions:
Incorrect Firewall Rules
Split tunneling relies on specific firewall rules to differentiate between local and remote traffic. If these rules are misconfigured or missing, traffic may be incorrectly routed, leading to connectivity issues. Check your firewall settings to ensure that the appropriate rules are in place.
DNS Resolution Issues
Split tunneling can interfere with DNS resolution, as local DNS servers may not be able to resolve external domain names. To address this, consider using a DNS proxy or configuring custom DNS settings on your device.
IP Address Conflicts
In some cases, split tunneling can cause IP address conflicts between the local and remote networks. This can lead to connectivity problems or even security vulnerabilities. To prevent this, ensure that the IP addresses used on both networks are unique.
Application-Specific Issues
Certain applications may not be compatible with split tunneling or may require specific configuration to function correctly. If you encounter problems with a particular application, consult its documentation or contact the developer for support.
Performance Considerations
Split tunneling can impact network performance, especially if the remote network has limited bandwidth or high latency. Monitor your network traffic and adjust your split tunneling settings accordingly to optimize performance.
Advanced Split Tunneling Techniques
Split tunneling can be further enhanced with advanced techniques, such as per-application tunneling, to provide even greater control over network traffic.
Per-application tunneling allows you to specify which applications should use the VPN tunnel and which should use the regular internet connection. This level of granularity provides increased flexibility and customization options for your network setup.
Benefits of Per-Application Tunneling
- Improved performance for applications that do not require VPN protection.
- Reduced VPN bandwidth usage by excluding low-priority applications from the tunnel.
- Enhanced security by isolating sensitive applications within the VPN tunnel.
Limitations of Per-Application Tunneling
- Increased complexity in configuring and managing the VPN setup.
- Potential for security vulnerabilities if applications are not properly configured.
- May not be supported by all VPN providers or operating systems.
Case Studies and Examples

Split tunneling offers a flexible and efficient solution for managing network traffic. Here are a few case studies and examples to illustrate its benefits and challenges in real-world scenarios:
Example 1: Secure Remote Access
A multinational corporation enables remote work for its employees. To ensure secure access to company resources while allowing employees to use their personal networks for non-work-related activities, the company implements split tunneling with WireGuard. This approach allows employees to connect to the corporate network through a VPN while maintaining access to local resources and the internet.
Example 2: Improving Performance for Cloud Applications
A software development company hosts its applications on a cloud platform. To optimize performance for users in different regions, the company uses split tunneling to route traffic for cloud applications directly to the internet, bypassing the VPN. This reduces latency and improves user experience.
Example 3: Compliance and Data Protection
A financial institution needs to comply with regulatory requirements that mandate the protection of sensitive data. The institution implements split tunneling to separate work-related traffic from personal traffic. This ensures that sensitive data is only transmitted over the VPN, while personal data remains isolated on the local network.
Example 4: Troubleshooting Split Tunneling Issues
In a case where users encounter connectivity problems with split tunneling, the IT team discovers that the VPN client is misconfigured. The team corrects the configuration, ensuring that the VPN routes only the specified traffic through the tunnel, resolving the connectivity issues.
Comparison with Other VPN Split Tunneling Solutions
WireGuard split tunneling offers several advantages over other VPN solutions that provide split tunneling capabilities. Here’s a comparison of WireGuard with some of the popular alternatives:
OpenVPN
OpenVPN is an open-source VPN protocol that supports split tunneling. It offers strong encryption and flexible configuration options. However, OpenVPN can be more complex to set up and manage compared to WireGuard. Additionally, OpenVPN may have slightly lower performance than WireGuard due to its heavier encryption overhead.
IPsec
IPsec is a suite of protocols used for securing IP traffic. It supports split tunneling but is typically more complex to configure and manage than WireGuard. IPsec also has a higher overhead than WireGuard, which can impact performance.
Cisco AnyConnect
Cisco AnyConnect is a proprietary VPN solution that offers split tunneling. It provides robust security features and is widely used in enterprise environments. However, AnyConnect is not open source and requires a commercial license, which may not be suitable for all users.
Best Practices for Using Split Tunneling
Implementing split tunneling securely and efficiently requires careful planning and configuration. Here are some best practices to consider:
Traffic Routing: Define clear rules for routing traffic through the VPN tunnel and the local network. Consider the security implications and performance impact of sending specific traffic types through the tunnel.
Security Policies
- Establish clear security policies that govern the use of split tunneling. This includes defining authorized applications, websites, or IP addresses that can access the VPN tunnel.
- Implement strong authentication mechanisms for users accessing the VPN, such as multi-factor authentication (MFA).
Performance Optimization
- Monitor network performance and adjust split tunneling configurations to optimize speed and latency. Consider factors such as the number of active VPN connections, traffic volume, and the capacity of the VPN server.
- Use traffic shaping techniques to prioritize critical traffic and ensure smooth performance for essential applications.
Future of Split Tunneling in WireGuard
Split tunneling in WireGuard is a relatively new feature that has the potential to revolutionize the way we use VPNs. By allowing users to selectively route traffic through the VPN tunnel, split tunneling can improve performance, security, and usability.As WireGuard continues to develop, we can expect to see even more enhancements to split tunneling.
These enhancements may include:
Improved performance
WireGuard is already one of the fastest VPN protocols available, and split tunneling can further improve performance by reducing the amount of traffic that is encrypted and routed through the VPN tunnel. This can be especially beneficial for applications that require high bandwidth, such as streaming video or gaming.
Enhanced security
Split tunneling can also enhance security by allowing users to isolate sensitive traffic from the rest of their network. This can help to protect against malware and other threats that may be present on the local network.
Increased usability
Split tunneling can make VPNs more usable by allowing users to access local resources without having to disconnect from the VPN. This can be especially useful for users who need to access both local and remote resources on a regular basis.In
addition to these enhancements, we can also expect to see new technologies and trends that will impact split tunneling in WireGuard. These technologies and trends include:
Cloud-based VPNs
Cloud-based VPNs are becoming increasingly popular, and they offer a number of advantages over traditional VPNs. Cloud-based VPNs are more scalable, easier to manage, and more secure than traditional VPNs. They also offer a number of features that are ideal for split tunneling, such as the ability to dynamically adjust the VPN tunnel based on the user’s location and network conditions.
Software-defined networking (SDN)
SDN is a technology that allows network administrators to programmatically control the network. SDN can be used to implement a variety of network features, including split tunneling. SDN can make split tunneling more flexible and easier to manage, and it can also be used to integrate split tunneling with other network security features.These
are just a few of the potential future developments and enhancements for split tunneling in WireGuard. As WireGuard continues to develop, we can expect to see even more innovations that will make split tunneling even more powerful and useful.