ssh.sshslowdns.com – Welcome to the realm of WireGuard split tunneling, where the boundaries between local and remote networks blur, empowering you with unparalleled control over your online presence.
This innovative VPN technique allows you to selectively route specific traffic through an encrypted tunnel while maintaining direct access to your local network.
Join us as we delve into the intricacies of WireGuard split tunnel MAC address management, unlocking a world of possibilities for enhanced privacy, security, and network optimization.
WireGuard, renowned for its lightning-fast speeds and robust encryption, now empowers you to tailor your VPN experience to your unique needs.
Split tunneling grants you the flexibility to channel sensitive traffic through the secure VPN tunnel while allowing other traffic to flow freely over your local network.
This granular control opens up a plethora of benefits, ranging from improved performance to enhanced security and privacy.
WireGuard Split Tunnel Configuration
Split tunneling is a feature in WireGuard that allows you to route specific traffic through the VPN tunnel while allowing other traffic to go directly to the internet. This can be useful for improving performance and reducing latency for applications that don’t need to be routed through the VPN.To
configure split tunneling in WireGuard, you need to add the following lines to your WireGuard configuration file:“`[Interface]Address = 10.0.0.1/24DNS = 1.1.1.1MTU = 1420[Peer]PublicKey = AllowedIPs = 0.0.0.0/0 “`
The `Address` line specifies the IP address of the WireGuard interface. The `DNS` line specifies the DNS server to use for the WireGuard interface. The `MTU` line specifies the maximum transmission unit for the WireGuard interface. The `PublicKey` line specifies the public key of the peer that you want to connect to.
The `AllowedIPs` line specifies the IP addresses that are allowed to access the WireGuard interface.
Once you have added these lines to your WireGuard configuration file, you can start the WireGuard interface by running the following command:
“` sudo wg-quick up “`
You can now use the `wg` command to check the status of the WireGuard interface and to add or remove peers.
Here are some examples of how to implement split tunneling with WireGuard:
* -*Route all traffic through the VPN tunnel:
“` [Interface] Address = 10.0.0.1/24 DNS = 1.1.1.1 MTU = 1420
[Peer] PublicKey = AllowedIPs = 0.0.0.0/0 “`* -*Route only specific traffic through the VPN tunnel:
“` [Interface] Address = 10.0.0.1/24 DNS = 1.1.1.1 MTU = 1420
[Peer] PublicKey = AllowedIPs = 192.168.1.0/24, 10.0.0.0/24 “`* -*Exclude specific traffic from the VPN tunnel:
“` [Interface] Address = 10.0.0.1/24 DNS = 1.1.1.1 MTU = 1420
[Peer] PublicKey = AllowedIPs = 0.0.0.0/0 ExcludeIPs = 192.168.1.0/24, 10.0.0.0/24 “`Advantages and Disadvantages of Split Tunneling
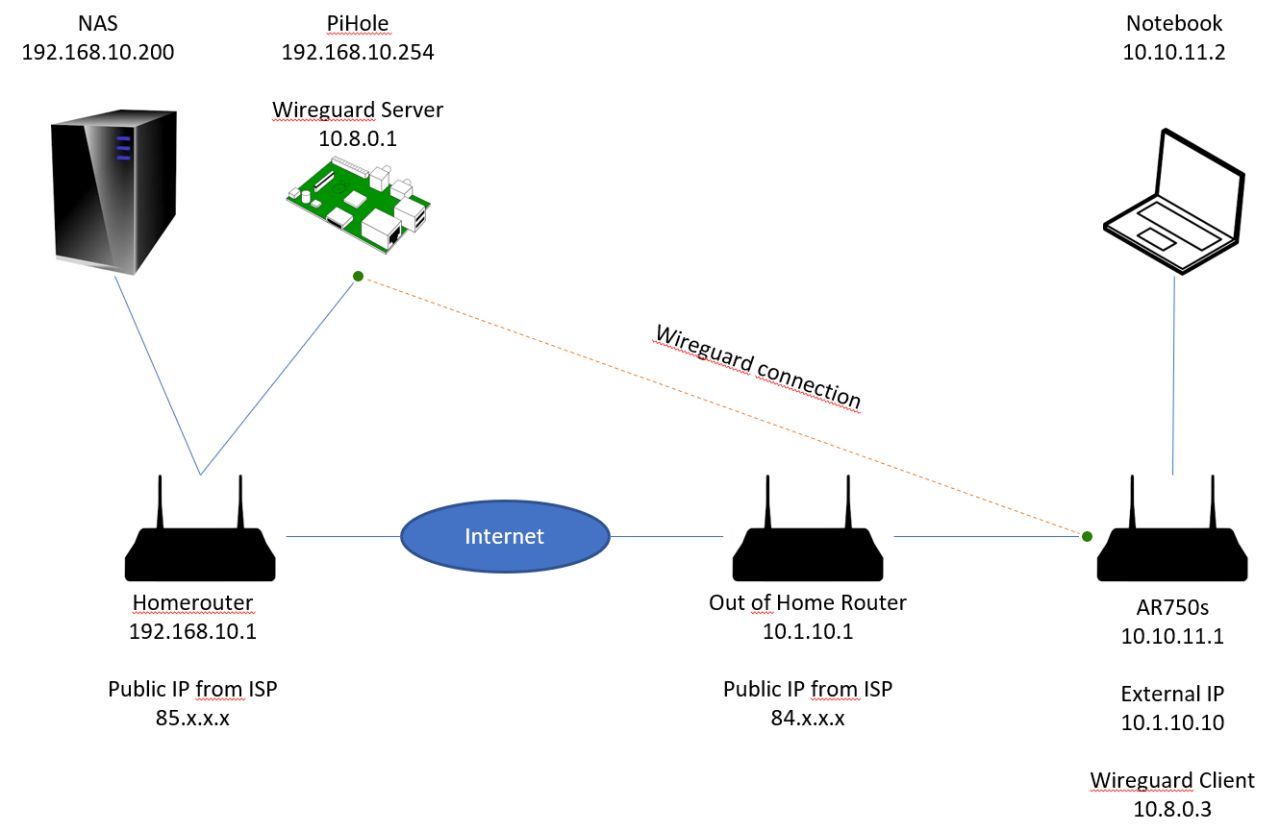
Split tunneling, a feature of VPNs, offers advantages and disadvantages compared to other VPN tunneling methods.
Advantages of Split Tunneling
- Selective routing: Allows users to specify which traffic goes through the VPN and which goes through their regular internet connection.
- Improved performance: By directing only essential traffic through the VPN, split tunneling can reduce latency and improve speeds for local network activities.
- Enhanced security: Can provide an additional layer of security by encrypting only the traffic that needs protection.
Disadvantages of Split Tunneling
- Potential security risks: If the VPN connection drops, traffic that is not routed through the VPN may become exposed.
- Increased complexity: Configuring split tunneling can be more complex than using a traditional VPN connection.
- May not be suitable for all applications: Some applications may require all traffic to go through the VPN for proper functionality.
Comparison to Other VPN Tunneling Methods
Compared to other VPN tunneling methods, split tunneling offers greater flexibility and control over traffic routing, while full tunneling provides more comprehensive protection.
Security Considerations for Split Tunneling
Split tunneling introduces certain security implications that need to be carefully considered. By allowing specific traffic to bypass the VPN tunnel, it creates potential entry points for malicious actors to access the internal network.
Best Practices for Securing Split Tunneling Configurations
To mitigate these risks, it is crucial to implement best practices for securing split tunneling configurations:
- Define clear policies: Establish well-defined policies that specify which traffic should be routed through the VPN tunnel and which should bypass it.
- Use trusted endpoints: Ensure that only authorized endpoints are allowed to access the internal network through the split tunnel.
- Implement strong authentication: Use robust authentication mechanisms to prevent unauthorized access to the VPN tunnel.
- Monitor and audit traffic: Regularly monitor and audit traffic passing through the split tunnel to detect any suspicious activity.
Troubleshooting Split Tunneling Issues
Split tunneling can occasionally encounter issues, which may disrupt your network connectivity or prevent it from functioning as intended. Identifying and resolving these problems can ensure a smooth and effective split tunneling experience.
Common Problems and Solutions
- No internet access for local devices: Ensure the split tunneling configuration is correct and that the local network is properly excluded from the VPN tunnel. Check firewall rules and network settings to rule out any conflicts.
- VPN tunnel not established: Verify that the VPN client is properly configured, the VPN server is reachable, and there are no network connectivity issues. Check for any error messages in the VPN logs.
- Slow or unreliable VPN connection: Optimize the VPN connection by adjusting the VPN protocol, encryption algorithm, and server location. Check for any network congestion or bandwidth limitations that may affect the VPN performance.
Troubleshooting Table
| Error Message | Recommended Action |
|---|---|
| “Failed to establish VPN tunnel” | Check VPN client configuration, server availability, and network connectivity. |
| “Local devices cannot access the internet” | Verify split tunneling configuration, firewall rules, and network settings. |
| “VPN connection is slow or unstable” | Optimize VPN protocol, encryption, and server location. Check for network congestion or bandwidth limitations. |
Advanced Split Tunneling Techniques
Advanced split tunneling techniques allow for more granular control over which traffic is routed through the VPN and which traffic is not. These techniques include:
Policy-Based Routing
Policy-based routing allows you to create rules that specify which traffic should be routed through the VPN based on factors such as source IP address, destination IP address, or port number. This allows you to create more complex split tunneling configurations, such as:
- Only routing traffic from specific applications or websites through the VPN.
- Routing all traffic from a specific subnet through the VPN.
- Routing all traffic to a specific destination IP address through the VPN.
Split Tunneling in Different Operating Systems
Split tunneling configuration varies across different operating systems. Here’s how to set it up on Windows, Linux, and macOS:
Windows
- Install WireGuard client and create a tunnel interface.
- Open Network & Internet settings and go to “Change adapter options”.
- Right-click on the WireGuard interface and select “Properties”.
- Go to “Networking” tab and uncheck “Internet Protocol Version 6 (TCP/IPv6)”.
- Click “OK” to save changes.
Linux
- Install WireGuard and create a tunnel interface.
- Edit the interface configuration file (/etc/wireguard/wg0.conf).
- Add “AllowedIPs = 0.0.0.0/1” to the file.
- Save the file and restart the WireGuard service.
macOS
- Install WireGuard and create a tunnel interface.
- Open System Preferences and go to “Network”.
- Click on the “Advanced” button and select the “TCP/IP” tab.
- Uncheck “Configure IPv6” and click “OK”.
- Click on “Apply” to save changes.
Comparison of Split Tunneling Features
| Feature | Windows | Linux | macOS ||—|—|—|—|| IPv6 Support | No | Yes | No || Multiple Interfaces | Yes | Yes | Yes || Per-Application Routing | Yes | Yes | No || Exclude Specific Domains | Yes | Yes | No |
Use Cases for Split Tunneling
Split tunneling offers several practical applications in various scenarios. It allows users to selectively route specific traffic through the VPN while maintaining a direct connection to the local network for other traffic. This approach provides flexibility and enhances both security and performance.
Specific Applications and Scenarios
- Access to Internal Resources: Split tunneling enables remote employees to access internal company resources, such as file servers and intranet applications, through the VPN while simultaneously accessing external websites and services with their local internet connection.
- Enhanced Security for Sensitive Data: Organizations can implement split tunneling to protect sensitive data by routing only business-critical traffic through the VPN. This approach minimizes the exposure of confidential information to the public internet, reducing the risk of data breaches.
- Improved Performance for Non-VPN Traffic: By excluding non-essential traffic from the VPN, split tunneling optimizes internet speed and reduces latency for applications that do not require the VPN’s security measures. This improves the user experience and enhances productivity.
Performance Implications of Split Tunneling
Split tunneling can have varying effects on network performance, depending on factors such as network configuration, traffic patterns, and the specific implementation of the split tunneling solution.
Factors Influencing Performance
- Network Latency: Split tunneling can introduce additional latency for traffic that is routed through the VPN tunnel, as it needs to traverse an additional network hop.
- Bandwidth Limitations: If the VPN connection has a lower bandwidth than the direct connection, split tunneling can limit the speed of traffic that is routed through the VPN.
- Traffic Patterns: The impact of split tunneling on performance will vary depending on the distribution of traffic between the VPN and direct connections. If a large proportion of traffic is routed through the VPN, it can lead to significant performance degradation.
Optimizing Performance
To optimize the performance of split tunneling, consider the following:
- Use a high-performance VPN solution: Choose a VPN solution that provides high bandwidth and low latency.
- Configure the VPN tunnel carefully: Ensure that the VPN tunnel is configured with appropriate settings for the network environment and traffic patterns.
- Monitor traffic patterns: Regularly monitor traffic patterns to identify any bottlenecks or areas where split tunneling may be impacting performance.
- Consider using a proxy server: A proxy server can help to reduce latency and improve performance for traffic that is routed through the VPN.
MAC Address Management in Split Tunneling

In split tunneling configurations, the management of MAC addresses becomes crucial. When a device is connected to a network using split tunneling, its MAC address is exposed to both the local network and the remote network. This can have implications for security and privacy.
Impact on Security and Privacy
If an attacker gains access to the local network, they could potentially spoof the MAC address of the device and gain access to the remote network. This could allow them to intercept sensitive data or launch attacks on the remote network.
Additionally, if the device is connected to a public Wi-Fi network, the MAC address could be exposed to other devices on the network, potentially compromising the privacy of the user.
Best Practices
To mitigate these risks, it is important to implement best practices for managing MAC addresses in split tunneling configurations:
- Use strong MAC address filtering on the local network to prevent unauthorized devices from accessing the network.
- Use MAC address randomization on the device to make it more difficult for attackers to spoof the MAC address.
- Avoid connecting to public Wi-Fi networks when using split tunneling.
- Use a VPN service that supports MAC address spoofing to protect the privacy of the device.
Ethical Considerations for Split Tunneling
Split tunneling, while offering flexibility and convenience, raises ethical concerns regarding privacy and data security. It is essential to use split tunneling responsibly to mitigate these concerns.
Privacy Concerns
Split tunneling can compromise privacy by exposing sensitive data on the untunneled network. For instance, unencrypted traffic can be intercepted by third parties, revealing personal information, financial details, or sensitive business data.
Responsible Use
To use split tunneling responsibly, consider the following guidelines:*
-*Limit Untunneled Traffic
Only exclude traffic that is not sensitive or confidential from the VPN tunnel.
-
- -*Use a Trusted VPN Provider
Choose a VPN provider with a strong privacy policy and proven security measures.
- -*Use a Trusted VPN Provider
-*Educate Users
Inform users about the risks associated with split tunneling and encourage them to use it only when necessary.