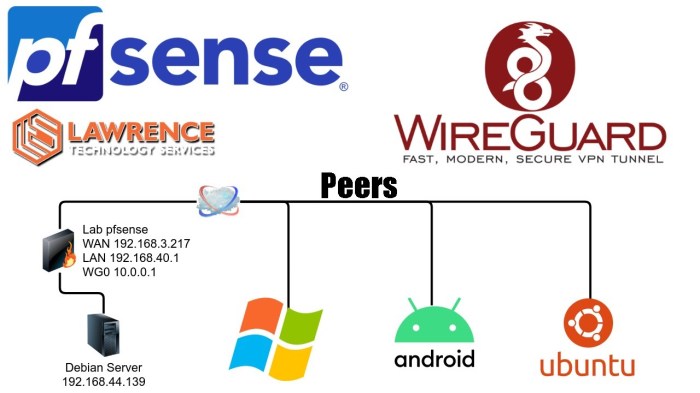
WireGuard is a modern and highly secure VPN protocol that has gained popularity due to its simplicity, speed, and versatility. One of its key features is split tunneling, which allows you to selectively route specific traffic through the VPN tunnel while leaving other traffic untouched.
In this comprehensive guide, we will delve into the concept of WireGuard split tunneling, explore its benefits and use cases, and provide step-by-step instructions on how to configure it. We will also discuss potential security risks and best practices, troubleshoot common issues, and explore advanced techniques for using split tunneling with WireGuard.
Whether you’re a network administrator, a remote worker, or simply someone who wants to enhance their online privacy and security, this guide will provide you with all the information you need to master WireGuard split tunneling and harness its full potential.
Overview of WireGuard Split Tunneling
WireGuard split tunneling is a networking technique that allows you to selectively route certain traffic through a virtual private network (VPN) while allowing other traffic to bypass the VPN and connect directly to the internet.
This provides several benefits, including improved performance for local network resources, reduced latency for non-VPN traffic, and increased privacy for sensitive data that should not be routed through the VPN.
Use Cases
- Accessing local network resources, such as printers or file servers, without having to connect the entire device to the VPN.
- Improving performance for online gaming or streaming services by bypassing the VPN for non-essential traffic.
- Protecting sensitive data, such as financial information or medical records, by only routing it through the VPN while allowing other traffic to bypass the VPN.
Configuring WireGuard Split Tunneling
Configuring WireGuard split tunneling allows you to route specific traffic through the VPN tunnel while excluding other traffic. This provides increased security and privacy for sensitive data while maintaining internet access for non-critical applications.
There are two primary methods for configuring split tunneling in WireGuard:
- Using rules
- Using IP ranges
Using Rules
Rules allow you to specify which traffic should be routed through the VPN tunnel based on source and destination IP addresses, ports, and protocols. For example, you could create a rule to send all traffic from your web browser through the VPN while excluding all other traffic.
- In the WireGuard configuration file, add the following line under the
[Peer]section: AllowedIPs = 192.168.1.0/24, 8.8.8.8/32- The first IP range (192.168.1.0/24) represents the local network that you want to route through the VPN. The second IP address (8.8.8.8/32) represents a specific IP address that you want to exclude from the VPN tunnel.
Using IP Ranges
IP ranges allow you to specify which traffic should be routed through the VPN tunnel based on source and destination IP address ranges. This is a simpler method than using rules, but it is less flexible.
- In the WireGuard configuration file, add the following line under the
[Peer]section: AllowedIPs = 192.168.1.0/24- This line specifies that all traffic from the local network (192.168.1.0/24) will be routed through the VPN tunnel.
Testing and Verifying Split Tunneling
Once you have configured split tunneling, you can test it by connecting to the VPN and checking if the desired traffic is being routed through the tunnel. You can use tools like traceroute or curl to verify the traffic flow.
Security Considerations
While WireGuard split tunneling offers flexibility and performance benefits, it also introduces certain security considerations. It’s crucial to be aware of potential risks and implement best practices to mitigate them.
One potential risk is the exposure of sensitive data on the untunneled interface. By default, split tunneling allows all traffic except specified subnets to bypass the VPN tunnel. This means that untrusted networks or public Wi-Fi connections could potentially intercept and access sensitive data transmitted over the untunneled interface.
Best Practices
To mitigate these risks, several best practices should be followed:
- Use strong encryption algorithms: WireGuard supports robust encryption algorithms like ChaCha20 and AES-256. Ensure that strong encryption is used to protect data transmitted over the VPN tunnel.
- Implement proper firewall rules: Configure firewall rules on the device to restrict access to sensitive data on the untunneled interface. This can prevent unauthorized access from untrusted networks.
- Monitor VPN connections: Regularly monitor VPN connections to detect any suspicious activity or unauthorized access attempts. This can help identify and address security breaches promptly.
- Educate users: Educate users about the potential risks associated with split tunneling and provide guidelines for secure usage. This can help prevent accidental data exposure or security breaches.
Security Enhancement
In certain scenarios, split tunneling can actually enhance security. For example, it allows users to access local network resources while still protecting sensitive data transmitted over the VPN tunnel. This can be beneficial in environments where both local and remote access is required.
By carefully considering the security implications and implementing appropriate best practices, organizations can effectively leverage WireGuard split tunneling to improve network flexibility and performance while maintaining a robust security posture.
Troubleshooting Split Tunneling Issues
WireGuard split tunneling can occasionally encounter issues. Common problems include:
- Traffic not being routed correctly
- Connectivity problems
- DNS resolution issues
To troubleshoot, check the following:
Network Configuration
Ensure that your network configuration is correct. Verify that the WireGuard interface is active and that the correct routes are in place. Check that the firewall rules allow traffic to and from the WireGuard interface.
DNS Settings
Configure DNS settings correctly. Split tunneling may not work properly if DNS is not set up correctly. Ensure that the DNS servers are accessible and that the correct DNS settings are applied to the WireGuard interface.
Routing Rules
Verify that the routing rules are configured correctly. Split tunneling relies on routing rules to direct traffic through the WireGuard tunnel. Check that the routing rules are in place and that they are configured correctly.
Firewall Rules
Ensure that the firewall rules are not blocking traffic to and from the WireGuard interface. Check that the firewall rules allow traffic on the WireGuard interface and that they are not blocking the traffic you want to tunnel.
Debug Logs
Enable debug logs in WireGuard to help identify the root cause of the problem. The debug logs can provide valuable information about the operation of WireGuard and can help pinpoint the source of the issue.
Additional Tips
- Restart the WireGuard service.
- Update to the latest version of WireGuard.
- Check for any updates to the documentation or support forums.
- Contact your network administrator or ISP for assistance.
Performance Considerations
Split tunneling can impact network performance, depending on factors such as the number of rules, the size of the split tunnel, and the hardware used.
A large number of rules can slow down the processing of packets, as the firewall needs to check each rule to determine if a packet should be routed through the tunnel or not. Similarly, a large split tunnel can also slow down performance, as more packets need to be processed.
Optimizing Performance
- Use a dedicated hardware firewall: A dedicated hardware firewall can offload the processing of packets from the host computer, which can improve performance.
- Limit the number of rules: Only create rules for the applications and services that need to be routed through the tunnel. Avoid creating unnecessary rules.
- Use a smaller split tunnel: Only include the necessary subnets in the split tunnel. Avoid including unnecessary subnets.
- Tune the firewall settings: Some firewalls allow you to tune the performance settings. Experiment with different settings to find the optimal balance between performance and security.
Advanced Split Tunneling Techniques
Advanced split tunneling techniques with WireGuard allow for greater customization and flexibility in network traffic routing. These techniques enable the creation of multiple split tunnels, the implementation of custom rules, and the use of load balancing to optimize network performance.
Creating Multiple Split Tunnels
Creating multiple split tunnels allows for the routing of different types of traffic through separate tunnels. For example, one tunnel could be used for general internet access, while another tunnel could be used specifically for accessing a private network. This level of granularity provides enhanced security and control over network traffic.
Custom Rules
Custom rules enable the definition of specific criteria for routing traffic through a split tunnel. These rules can be based on factors such as IP address, port number, or application type. Custom rules provide a high level of customization, allowing for the creation of complex and tailored split tunneling configurations.
Load Balancing
Load balancing can be implemented in split tunneling to distribute network traffic across multiple tunnels. This technique helps to improve network performance and reliability by ensuring that traffic is not concentrated on a single tunnel. Load balancing can be configured based on various parameters, such as bandwidth or latency.
Split Tunneling for Specific Applications or Services
Split tunneling can be used to route traffic for specific applications or services through a dedicated tunnel. This approach is particularly useful for applications that require a high level of security or performance. By isolating the traffic for these applications, it is possible to enhance their functionality and protect them from potential security risks.
Comparison with Other VPN Split Tunneling Solutions
WireGuard split tunneling compares favorably to other VPN solutions that offer similar capabilities. It offers several advantages, including:
- Simplicity: WireGuard’s configuration is straightforward, making it easy to set up and manage.
- Speed: WireGuard is known for its exceptional performance, offering high speeds and low latency.
- Security: WireGuard utilizes state-of-the-art cryptography, ensuring the privacy and integrity of your data.
However, it’s important to note that other VPN solutions may offer additional features or capabilities that WireGuard does not, such as:
- Multi-hop connections: Some VPNs allow you to route your traffic through multiple servers for added security.
- Ad blocking: Certain VPNs include ad-blocking features to enhance your browsing experience.
- Dedicated IP addresses: A few VPNs provide dedicated IP addresses for users who require a static IP address for specific applications.
Choosing the Right Solution
The best VPN split tunneling solution for you will depend on your specific needs and preferences. If you prioritize simplicity, speed, and security, WireGuard is an excellent choice. However, if you require additional features such as multi-hop connections or ad blocking, you may want to consider other VPN solutions.
Examples of Split Tunneling Use Cases
WireGuard split tunneling offers numerous practical applications in various scenarios. Let’s explore some real-world examples:
Business Use Cases
- Access to internal resources while on the road: Employees can securely connect to company intranets, file servers, and other internal resources while traveling or working remotely.
- Secure remote access to cloud applications: Split tunneling allows businesses to grant access to cloud-based applications while maintaining a secure connection to the corporate network.
- Protection of sensitive data: By routing specific traffic through the VPN tunnel, businesses can ensure that confidential data is protected from external threats.
Remote Worker Use Cases
- Access to home network resources: Remote workers can securely access their home network devices, such as printers, cameras, and media servers, while connected to a public Wi-Fi network.
- Bypass geo-restrictions: Split tunneling enables remote workers to access geo-blocked websites and streaming services by routing specific traffic through the VPN tunnel.
- Enhance privacy: Remote workers can protect their online activities from prying eyes by routing sensitive traffic through the VPN tunnel while maintaining regular internet access for other activities.
Home User Use Cases
- Secure online banking: Home users can protect their financial transactions by routing banking-related traffic through the VPN tunnel while accessing other websites and services without VPN protection.
- Access to region-locked content: Split tunneling allows home users to bypass geo-restrictions and access streaming services or websites that are only available in specific regions.
- Enhance privacy and security: Home users can protect their online activities from snooping by routing specific traffic through the VPN tunnel, ensuring that their data remains private.
When designing and implementing split tunneling solutions, it’s crucial to consider the specific requirements of each scenario, such as the types of traffic to be routed through the VPN, the security level required, and the performance implications.
Integration with Other Technologies
WireGuard split tunneling can be integrated with other technologies to enhance its functionality and security. Here are some examples:
Firewalls: WireGuard can be integrated with firewalls to create a more comprehensive security solution. By configuring the firewall to allow only specific traffic through the VPN tunnel, administrators can control which applications and services have access to the remote network while blocking all other traffic.
This helps to prevent unauthorized access to the local network and protect against potential security breaches.
Network Management Systems: WireGuard can be integrated with network management systems (NMS) to provide visibility and control over the VPN tunnel. NMS can be used to monitor the status of the VPN tunnel, troubleshoot issues, and generate reports on VPN usage.
This information can help administrators to optimize the performance of the VPN tunnel and ensure that it is meeting the needs of the organization.
Example of Integrated Solution
One example of an integrated solution is using WireGuard with a firewall to create a secure remote access solution. In this scenario, the firewall would be configured to allow only traffic from the VPN tunnel to access the internal network.
This would prevent unauthorized users from accessing the internal network, even if they were able to compromise the VPN client.
Future Developments in WireGuard Split Tunneling
WireGuard split tunneling is a relatively new feature, and there is considerable scope for future development and improvements. Some potential developments that could enhance the functionality and usability of split tunneling include:
Expanded Platform Support
WireGuard split tunneling is currently available on a limited number of platforms. In the future, it is likely that support will be expanded to include more operating systems and devices. This will make split tunneling more accessible to a wider range of users.
Improved User Interface
The current user interface for WireGuard split tunneling is relatively basic. In the future, it is likely that the interface will be improved to make it easier for users to configure and manage split tunneling. This could include the addition of graphical tools and wizards.
Additional Features
There are a number of additional features that could be added to WireGuard split tunneling to enhance its functionality. These features could include:
- Support for multiple tunnels
- The ability to specify which applications use the tunnel
- The ability to create custom rules for split tunneling
These features would give users more control over how split tunneling is used.
Impact on Adoption and Use
The future developments of WireGuard split tunneling are likely to have a significant impact on its adoption and use. As the feature becomes more accessible, easier to use, and more feature-rich, it is likely that more users will adopt it.
This could lead to a wider range of applications for split tunneling, including:
- Improved security for remote workers
- Enhanced privacy for online activities
- Reduced bandwidth usage for specific applications
WireGuard split tunneling is a powerful feature that has the potential to revolutionize the way that VPNs are used. The future developments of this feature are likely to make it even more useful and accessible to a wider range of users.
Final Summary
WireGuard split tunneling is a powerful tool that can greatly enhance the functionality and security of your VPN setup. By selectively routing traffic through the VPN tunnel, you can protect sensitive data while maintaining access to local resources and services.
As the technology continues to evolve, we can expect even more innovative and versatile applications of split tunneling in the future. Whether you’re a seasoned network professional or a home user looking to improve your online experience, WireGuard split tunneling is definitely worth exploring.