In the realm of virtual private networks (VPNs), WireGuard has emerged as a formidable contender due to its exceptional speed, security, and privacy features. One of its most versatile capabilities is split tunneling, which allows you to route specific network traffic through the VPN while maintaining a direct connection for other traffic.
This comprehensive guide will delve into the concept of WireGuard split tunneling on macOS, exploring its benefits, configuration steps, and advanced options. We will also discuss potential security implications and provide a comparison with other VPN protocols to help you make an informed decision.
WireGuard Split Tunneling on macOS
WireGuard is a modern, fast, and secure VPN tunnel that can be configured for split tunneling on macOS. Split tunneling allows you to route specific traffic through the VPN tunnel while allowing other traffic to bypass the tunnel and go directly to the internet.
This can be useful for improving performance and reducing latency for applications that don’t require VPN protection, such as local network resources or streaming services.
Configuring WireGuard for Split Tunneling on macOS
To configure WireGuard for split tunneling on macOS, you will need to add a custom DNS server to your WireGuard configuration file. This DNS server will be used to resolve DNS queries for traffic that should bypass the VPN tunnel.
-
- Open the WireGuard configuration file in a text editor.
- Add the following line to the file:
DNS = 8.8.8.8
- Save the file and restart WireGuard.
Once you have added the custom DNS server to your WireGuard configuration file, you will need to configure your applications to use the WireGuard interface for DNS resolution.
-
- For Chrome and Firefox, you can add the following line to your browser’s about:config page:
network.proxy.socks_remote_dns = true
- For Safari, you can enable the “Use proxy server for DNS lookups” option in the Network preferences.
Once you have configured your applications to use the WireGuard interface for DNS resolution, traffic from those applications will bypass the VPN tunnel and go directly to the internet.
Benefits of Using Split Tunneling with WireGuard
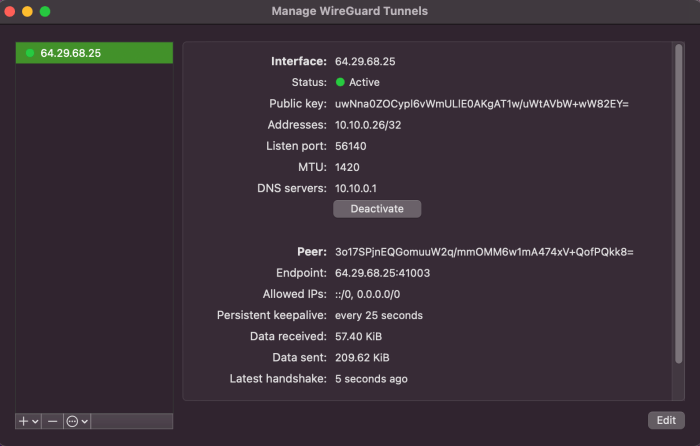
Split tunneling with WireGuard provides several advantages that enhance security, performance, and control over network traffic:
-
Improved security and privacy
Split tunneling allows you to route only specific traffic through the VPN, while excluding other traffic. This provides an additional layer of security and privacy by preventing sensitive data from being exposed to the public internet.
-
Enhanced network performance
By excluding certain traffic from the VPN, split tunneling can improve network performance.
Non-sensitive traffic can be routed directly through the local network, reducing latency and increasing bandwidth for VPN-bound traffic.
-
Flexible control over network traffic
Split tunneling provides granular control over which applications or websites are routed through the VPN.
This flexibility allows you to optimize network traffic based on security requirements and performance needs.
Configuring WireGuard for Split Tunneling on macOS
Configuring WireGuard for split tunneling on macOS involves a few simple steps:
Step 1: Install WireGuard
- Visit the WireGuard website and download the latest version of the WireGuard application for macOS.
- Open the downloaded DMG file and drag the WireGuard application to your Applications folder.
- Open the WireGuard application and click on the “Create New Tunnel” button.
Step 2: Configure Split Tunneling
- In the “Name” field, enter a name for your WireGuard tunnel.
- In the “Private Key” field, paste your private key.
- In the “Public Key” field, paste the public key of the server you want to connect to.
- In the “Addresses” field, enter the IP addresses or subnets that you want to route through the WireGuard tunnel.
- In the “Allowed IPs” field, enter the IP addresses or subnets that you want to allow traffic from.
- Click on the “Save” button.
Step 3: Activate the Tunnel
- Click on the “Activate” button to activate the WireGuard tunnel.
- You will see a green “Active” status next to the tunnel name.
- Your traffic will now be routed through the WireGuard tunnel for the specified IP addresses or subnets.
Troubleshooting Common Issues and Errors
If you encounter any issues or errors while configuring WireGuard for split tunneling on macOS, here are some common problems and their solutions:
- Error: “Invalid private key”
– Ensure that you have pasted the correct private key into the “Private Key” field. - Error: “Invalid public key”
– Ensure that you have pasted the correct public key of the server you want to connect to into the “Public Key” field. - Error: “Tunnel not activating”
– Ensure that you have allowed the WireGuard application through your firewall. - No internet access
– Ensure that you have entered the correct IP addresses or subnets into the “Addresses” field.
Advanced Split Tunneling Options
Configure advanced split tunneling options in WireGuard to customize the list of excluded routes and implement granular firewall rules.
Customizing the List of Excluded Routes
By default, WireGuard excludes all local routes from the tunnel. To customize this list, edit the AllowedIPs key in the WireGuard configuration file. Specify a comma-separated list of IP addresses or subnets to exclude from the tunnel.
Using the “allowedips” and “excludedips” Settings
The allowedips and excludedips settings provide finer control over split tunneling. allowedips specifies a list of IP addresses or subnets that should be routed through the tunnel, while excludedips excludes specific IP addresses or subnets from the tunnel.
Implementing Advanced Firewall Rules
WireGuard supports advanced firewall rules to further control network traffic. Use the iptables command to create custom firewall rules. For example, the following rule blocks all traffic to a specific IP address:
iptables
- I FORWARD
- d 192.168.1.100
- j DROP
Performance Considerations
Split tunneling can impact network speed by introducing additional processing overhead. However, the extent of the impact depends on various factors, including the number of rules configured, the complexity of the rules, and the hardware capabilities of the device.To optimize performance for specific use cases, it’s important to carefully consider the rules configured and the traffic that will be routed through the tunnel.
For example, if only a few specific applications or websites need to be routed through the tunnel, it’s best to create rules that are as specific as possible. This will minimize the amount of traffic that is processed by the VPN, improving overall performance.Additionally,
monitoring network traffic can help identify potential bottlenecks and areas for optimization. By observing the traffic patterns and identifying any delays or performance issues, administrators can make adjustments to the rules or configuration to improve performance.
Security Implications of Split Tunneling
Split tunneling introduces potential security risks due to the exposure of untunneled traffic. This can provide an entry point for malicious actors to access the device and internal network.
Comparing WireGuard with Other VPN Protocols

WireGuard’s split tunneling feature offers advantages and disadvantages compared to other VPN protocols. It’s essential to consider these factors when selecting a protocol for your specific needs.
Factors to Consider
- Speed and Performance: WireGuard is known for its high speed and low latency, making it suitable for bandwidth-intensive applications.
- Security: WireGuard utilizes modern cryptography algorithms, providing robust security.
- Ease of Use: WireGuard is relatively easy to configure and manage compared to other protocols.
- Cross-Platform Compatibility: WireGuard is supported on various platforms, including macOS, Windows, Linux, and mobile devices.
- Device Support: WireGuard has limited device support compared to protocols like OpenVPN.
- Maturity: WireGuard is a relatively new protocol compared to OpenVPN or IPsec, so it may have fewer established features and support.
Use Cases for WireGuard Split Tunneling
WireGuard split tunneling offers a versatile solution for various networking scenarios. Its ability to route specific traffic through the VPN tunnel while allowing other traffic to bypass it provides numerous benefits and use cases.
Some of the most common use cases for WireGuard split tunneling include:
Remote access to corporate resources
WireGuard split tunneling enables secure remote access to corporate networks and resources. By routing only work-related traffic through the VPN tunnel, users can access internal applications and data while maintaining regular internet connectivity for personal browsing and activities.
Secure browsing and online banking
Split tunneling can enhance online security and privacy by routing sensitive traffic, such as banking transactions or online shopping, through the VPN tunnel. This protects personal and financial information from potential threats on public Wi-Fi networks or unsecured connections.
Gaming and streaming media
WireGuard split tunneling allows users to enjoy low-latency gaming and streaming experiences while maintaining regular internet access for other activities. By routing gaming traffic through the VPN tunnel, users can bypass ISP throttling and optimize their gaming performance.
Troubleshooting Split Tunneling Issues
Using split tunneling may occasionally lead to issues. Understanding the common problems and solutions can help resolve them efficiently.
Diagnostic Techniques
To diagnose split tunneling issues, follow these steps:
- Verify that WireGuard is configured correctly for split tunneling.
- Check the firewall settings to ensure WireGuard traffic is allowed.
- Examine the routing table to confirm that traffic is being routed as expected.
- Use network monitoring tools to observe traffic patterns and identify any anomalies.
Solutions
Common solutions for split tunneling issues include:
- Reinstalling WireGuard and reconfiguring it for split tunneling.
- Adjusting firewall rules to allow WireGuard traffic.
- Modifying the routing table to direct traffic correctly.
- Updating network drivers or firmware.
Contacting Support
If the above solutions do not resolve the issue, consider contacting the WireGuard support team. Provide detailed information about the problem, including the error messages, configuration settings, and any diagnostic steps taken.
Advanced Topics in WireGuard Split Tunneling
Integrating Split Tunneling with Other Network Services
Split tunneling can be integrated with other network services to enhance its functionality. For instance, you can use split tunneling with a firewall to control network access and route specific traffic through the VPN tunnel.
Automating Split Tunneling Configurations
To simplify the management of split tunneling configurations, you can automate the process using tools like scripts or configuration management systems. This allows you to dynamically adjust split tunneling rules based on predefined criteria or user actions.
Developing Custom Scripts for Advanced Use Cases
For complex or specific use cases, you can develop custom scripts to tailor split tunneling configurations to your needs. These scripts can perform advanced tasks, such as modifying routing tables, managing network interfaces, or integrating with other services.
Final Thoughts
WireGuard split tunneling on macOS offers a compelling solution for users seeking enhanced security, network performance, and flexibility. By carefully configuring the split tunneling settings and implementing appropriate security measures, you can harness the full potential of WireGuard to protect your sensitive data and optimize your online experience.