In the realm of cybersecurity, WireGuard split tunneling has emerged as a game-changer, empowering Linux users with unprecedented control over their network traffic. This cutting-edge technology allows you to selectively route specific applications or traffic through a VPN tunnel while maintaining direct access to your local network for other connections.
Join us as we delve into the fascinating world of WireGuard split tunneling on Linux, exploring its benefits, configurations, and advanced techniques.
As we navigate this comprehensive guide, you’ll gain a thorough understanding of WireGuard split tunneling, from its fundamental concepts to practical implementation. Whether you’re a seasoned network administrator or a curious enthusiast, this guide will equip you with the knowledge and skills to harness the power of split tunneling for enhanced privacy, security, and network optimization.
WireGuard Split Tunneling on Linux: Overview
WireGuard split tunneling is a feature that allows you to selectively route specific network traffic through a VPN tunnel while leaving other traffic on your local network. This can be useful for accessing resources on your local network while still maintaining the security and privacy benefits of a VPN connection.WireGuard
split tunneling is configured by creating a separate interface for the VPN traffic. This interface is then added to a routing table, which specifies which traffic should be routed through the VPN interface and which traffic should be routed through the local network interface.WireGuard
split tunneling has several advantages over traditional VPN configurations. First, it allows you to access resources on your local network without having to disconnect from the VPN. This can be useful for accessing files on a shared network drive or printing to a local printer.
Second, split tunneling can improve performance by reducing the amount of traffic that is routed through the VPN tunnel. This can be especially beneficial for applications that require a lot of bandwidth, such as video streaming or gaming.Here are some use cases for WireGuard split tunneling:* Accessing resources on a local network while connected to a VPN
- Improving performance for applications that require a lot of bandwidth
- Bypassing geo-restrictions on certain websites or services
- Split tunneling can also be used to improve security by isolating specific traffic from the rest of your network. For example, you could route all traffic from your web browser through the VPN tunnel while leaving all other traffic on your local network. This would help to protect your web browsing activity from eavesdropping and other attacks.
Configuring WireGuard Split Tunneling on Linux
To set up WireGuard split tunneling on Linux, follow these steps:
Creating the WireGuard Interface
-
- Install WireGuard on your Linux system.
- Create a new WireGuard interface using the following command:
wg-quick up wg0
Configuring the WireGuard Interface
-
- Set the IP address and netmask for the WireGuard interface:
wg set wg0 address 10.0.0.1/24
-
- Add the allowed IP addresses to the WireGuard interface:
wg set wg0 allowed-ips 192.168.1.0/24
Adding Routes to the WireGuard Interface
-
- Add a route to the WireGuard interface for the traffic you want to tunnel:
ip route add 192.168.2.0/24 via 10.0.0.1
Enabling IP Forwarding
-
- Enable IP forwarding on your Linux system:
sysctl -w net.ipv4.ip_forward=1
Testing the WireGuard Split Tunnel
-
- Check if the WireGuard interface is up and running:
wg-quick status wg0
-
- Test the split tunnel by sending traffic through the WireGuard interface:
ping 192.168.2.1
Troubleshooting WireGuard Split Tunneling on Linux
Identifying Common Problems and Errors
During the setup of WireGuard split tunneling on Linux, various issues may arise.
These include problems connecting to the VPN, DNS resolution errors, and IP address conflicts. Identifying the specific error is crucial for effective troubleshooting.
Solutions and Workarounds
Once the error is identified, appropriate solutions can be implemented. For instance, if the VPN connection fails, check the WireGuard configuration files for errors. DNS resolution errors can be resolved by modifying the DNS settings on the Linux system. IP address conflicts can be addressed by assigning unique IP addresses to the VPN interface and the physical network interface.
Advanced Troubleshooting Techniques
In some cases, more advanced troubleshooting techniques may be required. These include using network monitoring tools like Wireshark to analyze network traffic, checking firewall settings to ensure VPN traffic is allowed, and examining system logs for error messages. Additionally, seeking support from the WireGuard community or consulting with a network administrator can provide valuable insights.
Advanced WireGuard Split Tunneling Techniques
WireGuard split tunneling can be further enhanced using advanced techniques that optimize performance and granular control over traffic routing. These techniques involve using specific rules and policies to manage split tunneling behavior, allowing for more flexibility and customization.
Routing Specific Applications or Traffic through the Tunnel
To route specific applications or traffic through the WireGuard tunnel, you can use the “AllowedIPs” and “ExcludeIPs” settings in the WireGuard configuration file. The “AllowedIPs” setting specifies the IP addresses or subnets that should be routed through the tunnel, while the “ExcludeIPs” setting specifies the IP addresses or subnets that should be excluded from the tunnel.
This allows for fine-grained control over which traffic is routed through the tunnel and which traffic is not.
Using Rules and Policies to Control Split Tunneling Behavior
In addition to the “AllowedIPs” and “ExcludeIPs” settings, you can also use rules and policies to control split tunneling behavior. These rules and policies can be based on factors such as source IP address, destination IP address, port number, or application protocol.
By using rules and policies, you can create more complex and flexible split tunneling configurations that meet your specific requirements.
Performance Comparison: WireGuard Split Tunneling vs. Other VPNs
WireGuard split tunneling offers significant performance advantages over other VPN protocols, particularly in terms of latency, throughput, and overhead. This section analyzes these aspects and explores their implications for different use cases.
Latency, measured in milliseconds, refers to the delay in data transmission between two points. WireGuard’s lightweight and efficient design results in exceptionally low latency, making it ideal for real-time applications like gaming, video conferencing, and online trading.
Throughput, measured in megabits per second (Mbps), indicates the maximum data transfer rate. WireGuard’s advanced encryption algorithms and optimized protocol design enable high throughput, ensuring smooth streaming, fast file downloads, and seamless browsing.
Overhead refers to the additional data added to the original packet during encryption and decryption. WireGuard’s minimal overhead reduces bandwidth consumption and improves overall network efficiency, particularly for resource-constrained devices.
Implications for Different Use Cases
- Gaming: WireGuard’s low latency and high throughput minimize lag and improve gaming performance, providing a seamless and immersive experience.
- Video Conferencing: WireGuard ensures stable and high-quality video and audio transmissions, reducing interruptions and enhancing collaboration.
- Online Trading: WireGuard’s fast and reliable connection is crucial for real-time market data analysis and quick trade executions.
- Remote Access: WireGuard’s efficient split tunneling allows secure and fast access to specific resources within a corporate network, while maintaining internet access for other activities.
Security Considerations for WireGuard Split Tunneling
Split tunneling using WireGuard introduces certain security considerations that must be carefully evaluated before implementation.
By selectively routing only a portion of the network traffic through the VPN tunnel, split tunneling potentially exposes the remaining traffic to security vulnerabilities and threats.
Potential Vulnerabilities
- Data Leakage: Unprotected traffic outside the VPN tunnel can be intercepted and compromised, potentially exposing sensitive data or credentials.
- Malware Infection: Unencrypted traffic can be vulnerable to malware infections, which can spread through the network and compromise the entire system.
- Network Reconnaissance: Attackers can use unencrypted traffic to gather information about the network topology and identify potential targets for further attacks.
Mitigation Recommendations
- Implement Strict Access Control: Define clear rules and policies to determine which traffic is allowed to bypass the VPN tunnel. Limit access to only essential resources.
- Use a Firewall: Configure a firewall to block all untrusted traffic from entering the network. This helps protect the system from external threats.
- Monitor Network Activity: Regularly monitor network traffic for suspicious activity or unauthorized access attempts. Use intrusion detection systems to identify and respond to potential security incidents.
- Keep Software Up-to-Date: Ensure that all software and operating systems are regularly updated with the latest security patches. This helps close any potential security vulnerabilities.
- Educate Users: Inform users about the potential risks of split tunneling and provide guidance on best practices for secure usage.
Use Cases for WireGuard Split Tunneling on Linux
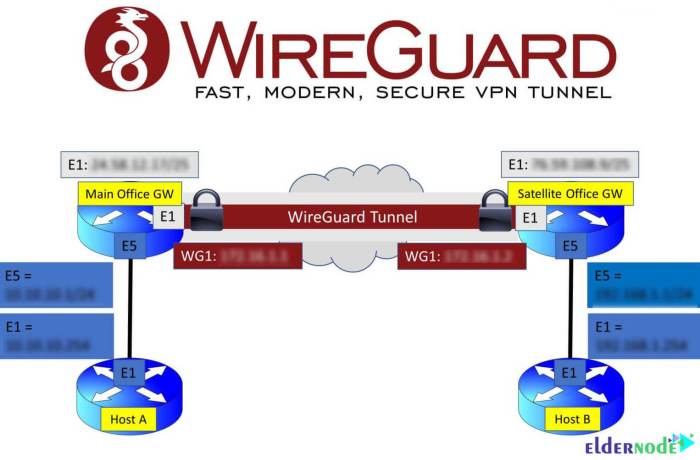
WireGuard split tunneling on Linux offers versatility in managing network traffic, making it suitable for various use cases.
Enhancing Privacy and Security
Split tunneling allows users to selectively route specific traffic through the VPN, while excluding others from the encrypted tunnel. This enhances privacy by limiting the exposure of sensitive data to the VPN provider and ensures that non-critical traffic remains unencrypted, improving performance.
Access Geo-restricted Content
By routing specific applications or services through the VPN, users can bypass geo-restrictions and access content unavailable in their region. For example, accessing streaming platforms or online services with country-specific content becomes possible.
Improving Network Performance
Split tunneling can optimize network performance by directing non-essential traffic directly to the internet, bypassing the VPN. This reduces latency and improves speed for activities such as gaming, video streaming, or large file downloads.
Secure Remote Access
For employees working remotely, split tunneling enables secure access to corporate resources while allowing personal internet traffic to remain unencrypted. This provides a balance between security and convenience.
Protecting Specific Devices
Split tunneling allows users to protect specific devices or applications from network threats. By routing traffic from those devices through the VPN, users can enhance their security without impacting the overall network performance.
Design Considerations for WireGuard Split Tunneling Deployments
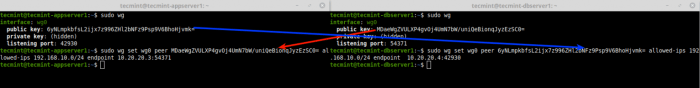
WireGuard split tunneling deployments require careful consideration to ensure optimal performance and security. Factors such as network topology, traffic patterns, and security requirements play a crucial role in determining the most appropriate configuration.
Network Topology
The network topology should be taken into account when deploying WireGuard split tunneling. For example, if the network has multiple subnets, it may be necessary to configure WireGuard to route traffic from specific subnets through the VPN tunnel, while allowing traffic from other subnets to bypass the tunnel.
Traffic Patterns
Traffic patterns should also be considered when configuring WireGuard split tunneling. For example, if most of the traffic is destined for internal resources, it may be beneficial to configure WireGuard to route all traffic through the VPN tunnel. However, if most of the traffic is destined for external resources, it may be more efficient to configure WireGuard to bypass the VPN tunnel for non-sensitive traffic.
Security Requirements
Security requirements should also be taken into account when configuring WireGuard split tunneling. For example, if the network is subject to strict security regulations, it may be necessary to configure WireGuard to use strong encryption and authentication mechanisms. Additionally, it may be necessary to configure WireGuard to block traffic from untrusted sources.
Best Practices for WireGuard Split Tunneling on Linux
WireGuard split tunneling offers increased flexibility and security in VPN deployments. Here are best practices for its effective implementation on Linux:
Configuration Optimization
– Configure the allowed IP ranges for the split tunnel carefully, only including necessary destinations to minimize potential security risks. – Use the “exclude” directive to exclude specific IP ranges or domains from the tunnel, ensuring local access to critical resources.
– Employ DNS leak prevention techniques to prevent DNS queries from leaking outside the tunnel, maintaining privacy and security.
Security Hardening
– Enable strong encryption algorithms, such as ChaCha20-Poly1305 or AES-256-GCM, to protect data transmitted through the tunnel. – Regularly update WireGuard and the Linux kernel to patch any vulnerabilities and enhance security. – Implement firewall rules to restrict access to the WireGuard interface, limiting exposure to potential attacks.
Performance Monitoring
– Monitor the performance of the split tunnel using tools like “wg” or “iftop” to identify any bottlenecks or performance issues. – Adjust the MTU (Maximum Transmission Unit) size to optimize network performance and reduce packet fragmentation.
– Consider using a WireGuard server with sufficient bandwidth and processing power to handle the split tunnel traffic.
Future Developments in WireGuard Split Tunneling on Linux
WireGuard split tunneling on Linux is a rapidly evolving field, with ongoing developments and future trends shaping its trajectory. Several potential enhancements and new features are on the horizon, promising to further improve the capabilities and usability of WireGuard split tunneling.
Kernel Integration
One significant development is the potential for deeper integration of WireGuard into the Linux kernel. This could lead to improved performance, reduced overhead, and enhanced security. Kernel integration would allow WireGuard to take advantage of the Linux kernel’s networking stack, potentially resulting in faster and more efficient VPN connections.
Improved Routing and Firewalling
Another area of focus is improving routing and firewalling capabilities for WireGuard split tunneling. This could involve the development of more granular controls for routing traffic through the VPN tunnel, as well as enhanced firewall rules to manage access to specific applications and services.
These improvements would provide greater flexibility and control over how traffic is managed through the VPN connection.
Simplified Configuration and Management
Simplifying the configuration and management of WireGuard split tunneling is another important area of development. This could include the development of user-friendly graphical user interfaces (GUIs) and automated tools to streamline the setup and management process. By making WireGuard split tunneling easier to configure and manage, it becomes more accessible to a wider range of users.
Enhanced Security Features
Ongoing developments are also focused on enhancing the security features of WireGuard split tunneling. This could involve the integration of additional encryption protocols, improved key management, and the development of new security protocols specifically tailored for split tunneling scenarios. These enhancements would further strengthen the security of WireGuard split tunneling, providing users with greater peace of mind when using the VPN connection.
Support for New Platforms
In addition to the ongoing developments for Linux, there is also growing interest in supporting WireGuard split tunneling on other platforms. This could include support for Windows, macOS, and mobile operating systems. By expanding the availability of WireGuard split tunneling to a wider range of platforms, it becomes more accessible and versatile for users.
Last Word
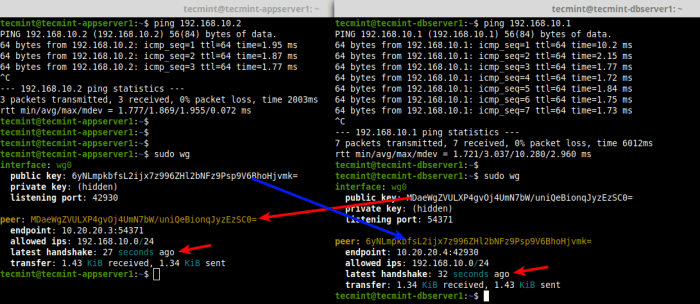
Through this comprehensive journey, we’ve explored the multifaceted world of WireGuard split tunneling on Linux. From its inception to advanced techniques, we’ve covered the essential aspects of this powerful technology. By embracing the concepts and implementing the strategies Artikeld in this guide, you’ll be well-equipped to leverage WireGuard split tunneling to enhance your network security, optimize performance, and enjoy a seamless online experience.
As the future of networking evolves, WireGuard split tunneling will undoubtedly play a pivotal role, and we encourage you to stay abreast of its ongoing developments to stay ahead of the curve.