ssh.sshslowdns.com – WireGuard Split Tunnel Configuration, In the realm of virtual private networks (VPNs), WireGuard has emerged as a frontrunner, renowned for its unparalleled speed, security, and versatility. Among its many capabilities, WireGuard’s split tunneling feature stands out as a game-changer, offering granular control over which traffic traverses the VPN tunnel and which remains on the local network.
This comprehensive guide will delve into the intricacies of WireGuard split tunnel configuration, empowering you to harness its full potential. We will explore the concept of split tunneling, its benefits, and how WireGuard implements this powerful feature. We will then provide step-by-step instructions for configuring WireGuard Split Tunnel Configuration, including examples for various operating systems.
Advanced split tunnel options will be discussed, such as excluding specific domains or IP addresses from the tunnel and routing specific traffic based on application or port.
WireGuard Split Tunnel Configuration Overview
Split tunneling is a network configuration that allows specific traffic to bypass a VPN connection and access the internet directly. This can be useful for improving performance for certain types of traffic, such as streaming media or gaming, while still maintaining the security benefits of a VPN for other traffic.WireGuard
implements split tunneling by using a feature called “allowed IPs”. Allowed IPs are a list of IP addresses or subnets that are allowed to bypass the VPN connection. When a packet matches an allowed IP, it is routed directly to the internet, instead of being sent through the VPN tunnel.
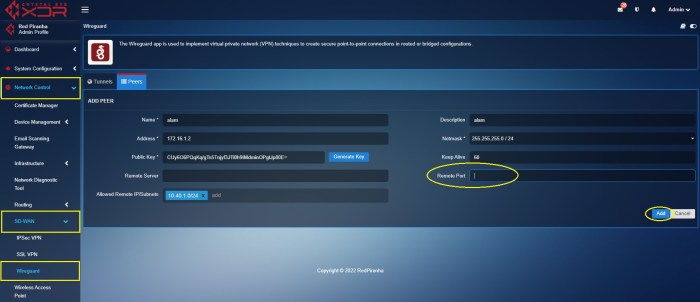
WireGuard Split Tunnel Configuration
Configure WireGuard Split Tunnel Configuration to route only specific traffic through the VPN, while allowing other traffic to use the local network connection.
This setup is useful for accessing local network resources while maintaining VPN protection for internet traffic.
Configuration Steps
- Create a WireGuard configuration file on the client device. Include the following settings:
- Interface: Specify the network interface to use for the VPN tunnel.
- Address: Assign an IP address to the client device within the VPN subnet.
- DNS: Specify the DNS servers to use for VPN traffic.
- AllowedIPs: Define the IP ranges that should be routed through the VPN tunnel. This can be specific IP addresses, subnets, or entire networks.
- Create a firewall rule on the client device to redirect traffic to the VPN interface. This ensures that traffic matching the AllowedIPs setting is routed through the VPN tunnel.
- Activate the WireGuard interface and apply the firewall rule. Verify the configuration by checking the VPN connection status and testing internet access.
Advanced Split Tunnel Options
In addition to the basic split tunneling options, WireGuard also provides advanced options for more granular control over traffic routing. These advanced options allow users to:
- Exclude specific domains or IP addresses from the tunnel.
- Route specific traffic through the tunnel based on application or port.
Excluding Specific Domains or IP Addresses from the Tunnel
To exclude specific domains or IP addresses from the tunnel, use the `AllowedIPs` parameter. This parameter specifies a list of IP addresses or domain names that will be allowed to bypass the tunnel. For example, to exclude the domain “example.com”
from the tunnel, you would use the following configuration:“`[Interface]AllowedIPs = 0.0.0.0/0, ::/0, example.com“`
Routing Specific Traffic Through the Tunnel Based on Application or Port
To route specific traffic through the tunnel based on application or port, use the `AllowedPorts` parameter. This parameter specifies a list of ports or applications that will be allowed to use the tunnel. For example, to allow only traffic from the port 443 to use the tunnel, you would use the following configuration:“`[Interface]AllowedPorts = 443“`
Troubleshooting Split Tunnel Issues
Split tunnel configuration may encounter various issues. Troubleshooting these issues involves identifying the root cause and applying appropriate solutions.Common issues include:
Incorrect Configuration
- Ensure that the WireGuard interface is properly configured and active.
- Verify that the allowedIPs setting in the WireGuard configuration file accurately specifies the traffic that should be routed through the tunnel.
- Check that the firewall rules are configured to allow traffic from the desired subnets.
Routing Problems
- Verify that the routing table is configured correctly to route traffic through the WireGuard interface.
- Check for any conflicting routing rules that may be interfering with the split tunnel configuration.
DNS Issues
- Ensure that the DNS settings are properly configured to resolve domain names correctly.
- Consider using a split-DNS configuration to separate DNS queries for internal and external traffic.
Other Issues
- Check for any hardware or software issues that may be affecting the WireGuard connection.
- Review the WireGuard logs for any error messages or warnings.
- Consider seeking support from the WireGuard community or the operating system vendor.
Performance Considerations
Implementing split tunneling can impact network performance, so it’s crucial to understand and mitigate potential performance implications.
Performance impact varies depending on factors like:
Traffic Volume and Distribution
Split tunneling directs a portion of traffic through the VPN tunnel, while the rest goes through the local network. If the volume of traffic directed through the VPN is significant, it can strain the VPN connection and slow down overall network performance.
VPN Server Location and Network Latency
The physical distance between the client and the VPN server can affect latency. High latency can introduce delays in VPN traffic, impacting the performance of applications and services.
VPN Encryption Overhead
VPN encryption adds computational overhead, which can impact performance, especially for bandwidth-intensive applications like video conferencing or large file transfers.
Optimization Tips
- Minimize traffic volume through the VPN tunnel by excluding non-sensitive traffic.
- Choose a VPN server located close to the client to reduce latency.
- Use high-performance VPN hardware or cloud-based VPN services to handle increased traffic load.
- Consider using a less computationally intensive encryption protocol for non-critical applications.
Security Implications of Split Tunneling
Split tunneling introduces security considerations by allowing specific traffic to bypass the VPN tunnel. This creates a potential attack surface for malicious actors to exploit.
Mitigating Potential Risks
To mitigate potential risks, consider the following recommendations:
- Restrict Access: Limit access to split tunneling to authorized users and devices.
- Use Strong Encryption: Implement strong encryption algorithms to protect sensitive data transmitted over the split tunnel.
- Monitor Traffic: Regularly monitor network traffic to detect any suspicious activity or unauthorized access.
- Consider a Firewall: Implement a firewall to filter and block unauthorized traffic from accessing the internal network.
- Educate Users: Train users on the potential risks of split tunneling and provide guidelines for secure usage.
Comparison with Other VPN Split Tunneling Implementations
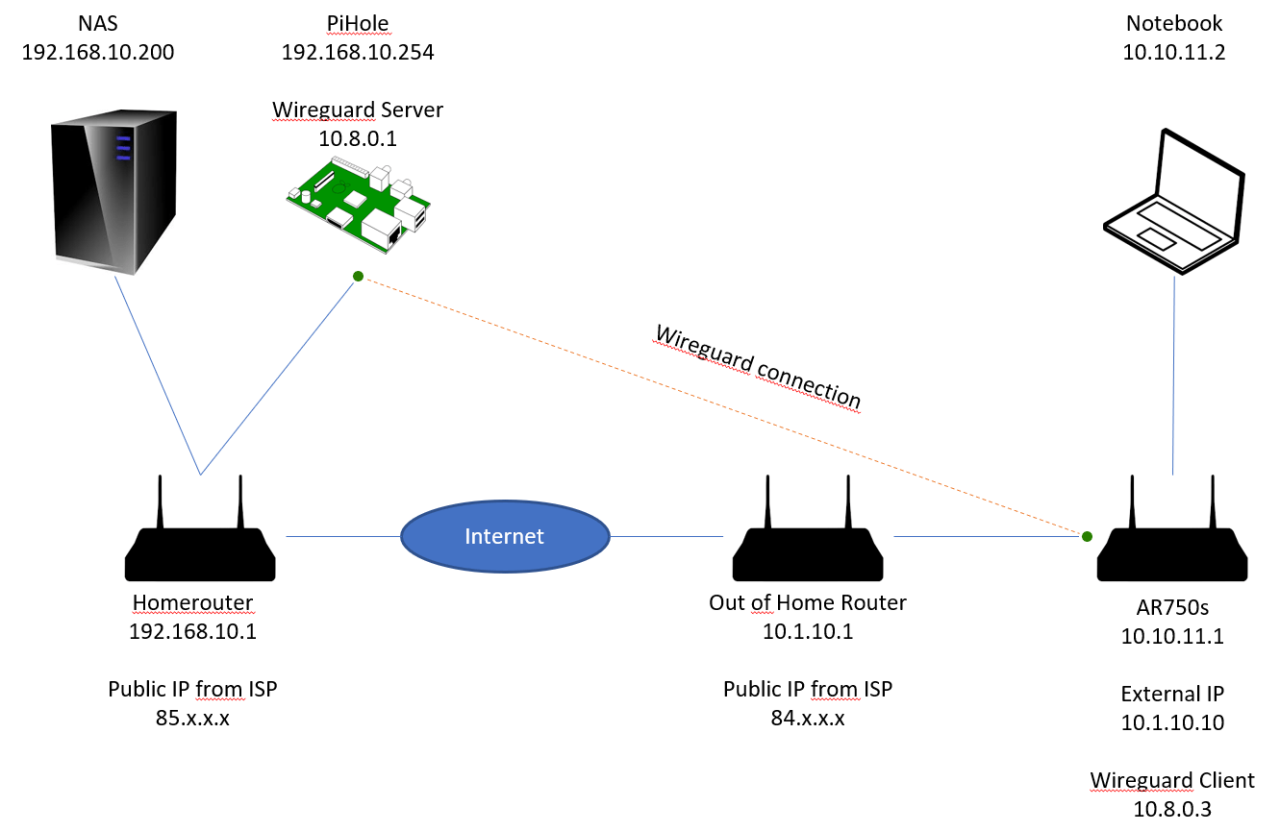
WireGuard’s split tunneling implementation offers several advantages over other VPN protocols. It is more efficient and lightweight than OpenVPN, and it provides better performance on low-powered devices. WireGuard also has a simpler configuration process than OpenVPN, making it easier to set up and manage.However,
other VPN protocols also have their own advantages. OpenVPN is more mature and widely supported than WireGuard, and it offers a wider range of features. OpenVPN also has a stronger track record of security and reliability.Ultimately, the best VPN split tunneling implementation for you will depend on your specific needs and requirements.
If you need a high-performance, lightweight VPN with a simple configuration process, WireGuard is a good option. If you need a more mature and widely supported VPN with a wider range of features, OpenVPN is a better choice.
Comparison of WireGuard and OpenVPN
WireGuard and OpenVPN are two of the most popular VPN protocols. Both protocols support split tunneling, but they have different advantages and disadvantages.WireGuard*
-*Advantages
High performance
Lightweight
-
- Simple configuration process
-*Disadvantages
Less mature than OpenVPN
Fewer features than OpenVPN
OpenVPN*
-*Advantages
Mature and widely supported
Wide range of features
-
- Strong track record of security and reliability
-*Disadvantages
Lower performance than WireGuard
More complex configuration process than WireGuard
Use Cases for Split Tunneling
Split tunneling offers various benefits in diverse network scenarios. It enhances network security and usability by allowing specific traffic to bypass the VPN while routing other traffic through the secure VPN connection.
Improved Network Performance
Split tunneling optimizes network performance by directing non-sensitive traffic directly to the local network, bypassing the VPN tunnel. This reduces latency and improves responsiveness for applications that require high bandwidth or low latency, such as video conferencing, online gaming, or file transfers.
Enhanced Security
Split tunneling provides granular control over network traffic, enabling organizations to protect sensitive data while allowing access to non-critical resources. By routing sensitive traffic through the VPN tunnel, organizations can mitigate security risks associated with unencrypted traffic.
Compliance and Data Governance
Split tunneling facilitates compliance with data protection regulations and internal security policies. By selectively routing specific traffic through the VPN, organizations can ensure that sensitive data remains within the secure VPN tunnel, meeting regulatory requirements and preventing data breaches.
Improved User Experience
Split tunneling enhances the user experience by allowing access to local resources without the need to connect to the VPN. This eliminates the need for constant VPN connections, simplifying network access and improving productivity.
Best Practices for Split Tunnel Configuration

To ensure optimal performance and security when configuring split tunnels, consider the following best practices:
Guidelines for Optimal Performance
- Select appropriate devices: Use devices that support hardware acceleration for WireGuard to maximize performance.
- Configure optimal MTU: Set the MTU (Maximum Transmission Unit) to match the underlying network’s MTU to avoid fragmentation and performance issues.
- Minimize hops: Design the split tunnel configuration to minimize the number of hops between the client and the VPN endpoint to reduce latency.
- Monitor performance: Regularly monitor network performance metrics such as latency, throughput, and packet loss to identify and address any potential bottlenecks.
Guidelines for Enhanced Security
- Implement strong encryption: Use strong encryption algorithms such as AES-256 or ChaCha20 to protect data in transit.
- Enable perfect forward secrecy: Utilize ephemeral keys to ensure that compromised keys do not compromise past or future sessions.
- Use trusted VPN providers: Choose reputable VPN providers with a proven track record of security and privacy.
- Regularly update software: Keep WireGuard software and firmware up to date to patch any vulnerabilities or security flaws.
Additional Considerations
- Consider split-horizon DNS: Implement split-horizon DNS to ensure that DNS requests for local resources are resolved through the local network, improving performance and security.
- Use access control lists: Define access control lists (ACLs) to restrict access to specific networks or resources through the VPN tunnel.
- Monitor and log activity: Establish a logging and monitoring system to track split tunnel activity and identify any suspicious or unauthorized access attempts.
Future Developments in Split Tunneling
As split tunneling continues to evolve, we can expect to see several advancements in the coming years. One potential development is the integration of more sophisticated traffic analysis and classification techniques. This will allow VPN providers to better identify and route specific types of traffic through the tunnel, providing more granular control over which applications and data are protected.
Emerging Trends
Another emerging trend is the use of machine learning and artificial intelligence (AI) to optimize split tunneling configurations. AI algorithms can analyze network traffic patterns and user preferences to automatically adjust split tunneling rules, ensuring optimal performance and security.Additionally, we can expect to see increased adoption of split tunneling in cloud computing environments.
As more businesses move their applications and data to the cloud, the need for secure and flexible VPN solutions will become increasingly important. Split tunneling can provide a cost-effective and scalable way to protect cloud-based resources while maintaining access to local networks.