In the realm of network security and privacy, WireGuard has emerged as a formidable contender, offering unparalleled speed, simplicity, and robust encryption. One of its most versatile features is split tunneling, a technique that allows you to selectively route traffic through the VPN tunnel while excluding specific destinations.
In this comprehensive guide, we will delve into the intricacies of WireGuard split tunnel configuration, exploring its benefits, use cases, and advanced options. We will also address troubleshooting tips, security considerations, performance implications, and best practices to ensure a seamless and secure split tunneling experience.
WireGuard Split Tunnel Configuration Overview
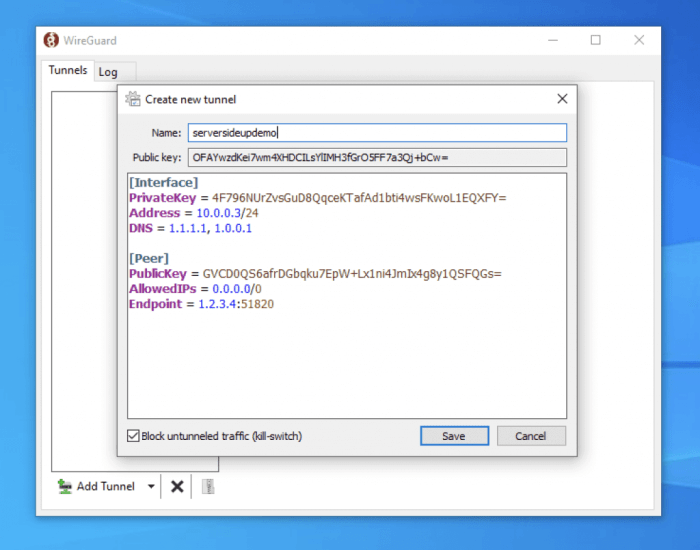
Split tunneling is a networking technique that allows you to route specific traffic through a VPN tunnel while allowing other traffic to bypass the tunnel and connect directly to the internet. This can be useful for improving performance and security.WireGuard
is a modern VPN protocol that supports split tunneling. To configure split tunneling in WireGuard, you need to add the `AllowedIPs` directive to your WireGuard configuration file. The `AllowedIPs` directive specifies which traffic should be routed through the VPN tunnel.
For example, the following configuration will allow all traffic from the 192.168.1.0/24 subnet to be routed through the VPN tunnel:“`[Interface]PrivateKey = 0123456789012345678901234567890123456789012345678901234567890123ListenPort = 51820AllowedIPs = 192.168.1.0/24“`Split tunneling can be useful for a variety of scenarios. For example, you can use split tunneling to:
- Improve performance by routing only traffic that needs to be encrypted through the VPN tunnel. This can reduce latency and improve bandwidth.
- Increase security by routing only sensitive traffic through the VPN tunnel. This can help to protect your privacy and data from eavesdropping and other attacks.
- Access geo-restricted content by routing traffic from specific countries or regions through the VPN tunnel. This can allow you to access content that is not available in your local area.
Configuring Split Tunneling in WireGuard
Split tunneling in WireGuard allows you to route specific traffic through the VPN tunnel while sending the rest directly to the internet. This is useful for accessing local resources or improving performance for certain applications.To configure split tunneling in WireGuard, you need to modify the configuration file for your WireGuard interface.
The configuration file is typically located at `/etc/wireguard/wg0.conf` on Linux and macOS, and at `%ProgramData%\WireGuard\wg0.conf` on Windows.
Linux and macOS
To enable split tunneling on Linux and macOS, add the following lines to your WireGuard configuration file:“`[Interface]AllowedIPs = 192.168.1.0/24, 192.168.2.0/24“`This will allow traffic from the subnets 192.168.1.0/24 and 192.168.2.0/24 to bypass the VPN tunnel. You can add additional subnets as needed.
Windows
To enable split tunneling on Windows, add the following lines to your WireGuard configuration file:“`[Interface]ExcludedIPs = 192.168.1.0/24, 192.168.2.0/24“`This will exclude traffic from the subnets 192.168.1.0/24 and 192.168.2.0/24 from being routed through the VPN tunnel. You can add additional subnets as needed.Once
you have made the necessary changes to your configuration file, save it and restart the WireGuard service. You can now test split tunneling by accessing local resources or running applications that require a direct internet connection.
Advanced Split Tunneling Options
WireGuard offers advanced split tunneling options that provide granular control over traffic routing. These options allow you to exclude specific domains or IP addresses from being routed through the VPN tunnel, ensuring that only essential traffic is encrypted.
Excluding Specific Domains or IP Addresses
To exclude specific domains or IP addresses from the VPN tunnel, use the following syntax in your WireGuard configuration file:“`[Interface]AllowedIPs = 0.0.0.0/0ExcludePrivateIPs = yesExcludeCIDRs = 192.168.0.0/24, 10.0.0.0/8“`In this example, all traffic will be routed through the VPN tunnel except for traffic destined for IP addresses within the 192.168.0.0/24 and 10.0.0.0/8 subnets.
Additional Advanced Options
WireGuard also provides additional advanced split tunneling options, including:
-
- -*RedirectRules
Allows you to redirect specific traffic through the VPN tunnel based on custom rules.
- -*RedirectRules
-*DNS
Allows you to specify custom DNS servers to use for traffic that is not routed through the VPN tunnel.
-*Proxy
Allows you to configure a proxy server to handle traffic that is not routed through the VPN tunnel.
Troubleshooting Split Tunneling Issues
Split tunneling in WireGuard is generally straightforward to configure, but various issues can arise.
Identifying and resolving these issues can ensure seamless and secure split tunneling functionality.
Common Issues and Solutions
Traffic not routed through the tunnel
Ensure that the appropriate firewall rules are in place to allow traffic to flow through the WireGuard interface. Verify that the split tunneling configuration is correct and that the desired traffic is being excluded from the tunnel.
DNS leaks
Configure DNS settings correctly to prevent DNS requests from leaking outside the tunnel. Consider using a DNS server within the tunnel or configuring a custom DNS configuration.
IPv6 leaks
If IPv6 is enabled on the device, ensure that the split tunneling configuration includes IPv6 addresses and that the firewall rules allow IPv6 traffic to flow through the tunnel.
Troubleshooting Tips
Use WireGuard logs
Enable logging in WireGuard to capture detailed information about the tunnel’s operation. Analyze the logs to identify any errors or configuration issues.
Check firewall rules
Verify that the firewall rules are correctly configured to allow traffic to flow through the WireGuard interface and to exclude the desired traffic from the tunnel.
Test with different devices
If encountering issues with a specific device, try connecting a different device to the same WireGuard configuration. This can help isolate the issue to a specific device or configuration.
Consult WireGuard documentation
Refer to the official WireGuard documentation for detailed information on split tunneling configuration and troubleshooting techniques.
Security Considerations for Split Tunneling
Split tunneling can introduce potential security risks and vulnerabilities. Understanding these risks and implementing appropriate mitigation strategies is crucial for secure split tunneling configurations.
Mitigating Risks and Vulnerabilities
To mitigate potential risks associated with split tunneling, consider the following measures:
- Restrict access to sensitive resources: Configure firewalls and access control lists (ACLs) to limit access to sensitive resources and applications to the VPN tunnel.
- Use strong encryption: Implement strong encryption algorithms, such as AES-256 or ChaCha20, to protect data transmitted over the VPN tunnel.
- Regularly update software: Ensure that all software, including the VPN client and server, is up to date with the latest security patches.
- Monitor network traffic: Monitor network traffic for suspicious activity or unauthorized access attempts.
Best Practices for Secure Configurations
For secure split tunneling configurations, follow these best practices:
-
- Define a clear split tunneling policy: Establish a clear policy outlining which traffic should be routed through the VPN tunnel and which should not.
- Use a reputable VPN provider: Choose a VPN provider with a strong security track record and transparent privacy policies.
- Educate users: Inform users about the risks and benefits of split tunneling and provide guidance on how to use it securely.
li> Regularly review and audit configurations: Periodically review and audit split tunneling configurations to ensure they remain secure and compliant.
Performance Implications of Split Tunneling
Split tunneling can introduce some performance overhead due to the additional processing and routing required.
The impact varies depending on several factors, including:
Hardware
The performance of the underlying hardware, such as the CPU and network interface, can affect the speed of split tunneling.
Software
The efficiency of the split tunneling software can also impact performance.
Network traffic
The amount and type of network traffic being split can affect the overhead.
Encryption
The encryption algorithms used for the VPN tunnel can also impact performance.To optimize performance, consider the following tips:
Use efficient hardware
Invest in a device with a powerful CPU and network interface to handle the additional processing.
Choose optimized software
Look for split tunneling software that is known for its efficiency and performance.
Limit split traffic
Only split the traffic that needs to go through the VPN tunnel to minimize overhead.
Use faster encryption
If performance is a critical concern, consider using faster encryption algorithms, such as AES-256-GCM.
Benchmarks and Comparisons
The performance impact of split tunneling can vary depending on the specific configuration and environment. However, general benchmarks and comparisons with other tunneling methods can provide some insights.
Split tunneling is generally less efficient than full tunneling
This is because split tunneling requires additional processing and routing, which can introduce some overhead.
The performance impact of split tunneling can be negligible in most cases
For typical use cases, the overhead introduced by split tunneling is minimal and does not significantly affect network performance.
Split tunneling can be more efficient than other tunneling methods in some cases
For example, if the VPN tunnel is used only for specific applications or services, split tunneling can reduce the overall network traffic and improve performance.
Comparison with Other Tunneling Methods
Split tunneling in WireGuard offers several advantages over other tunneling methods like OpenVPN and IPSec. WireGuard is known for its simplicity, performance, and modern cryptographic algorithms, making it a compelling choice for split tunneling implementations.
OpenVPN, while widely used, has a more complex configuration process and may exhibit lower performance compared to WireGuard. IPSec, on the other hand, is a more mature protocol but may lack the user-friendliness and performance of WireGuard.
Comparison Table
The following table summarizes the key differences between WireGuard split tunneling and other tunneling methods:
| Feature | WireGuard | OpenVPN | IPSec |
|---|---|---|---|
| Simplicity | High | Medium | Low |
| Performance | High | Medium | Medium |
| Modern Cryptography | Yes | Yes | No |
Use Cases for Split Tunneling
Split tunneling in WireGuard offers several practical benefits in various industries and applications. By selectively routing specific traffic through the VPN tunnel while allowing other traffic to bypass it, split tunneling enhances network security and flexibility.
Remote Access and Teleworking
- Allows remote employees to securely access company resources (e.g., internal applications, databases) while keeping personal internet traffic separate.
- Improves performance by directing work-related traffic through the VPN while excluding personal browsing or streaming, which can consume bandwidth.
Internet of Things (IoT) and Industrial Control Systems
- Enables secure remote management and monitoring of IoT devices and industrial control systems by allowing access to specific devices or subnets while excluding non-critical traffic.
- Protects sensitive data and operations from unauthorized access while maintaining connectivity for essential functions.
Cloud Computing and Hybrid Environments
- Facilitates seamless connectivity to cloud-based applications and services while maintaining access to on-premises resources.
- Allows selective routing of traffic to specific cloud providers or services, enhancing performance and security.
Financial Transactions and e-Commerce
- Provides secure and isolated channels for financial transactions, protecting sensitive data from eavesdropping and cyberattacks.
- Allows access to online banking, e-commerce platforms, and payment gateways while maintaining privacy for personal internet activities.
Best Practices for Implementing Split Tunneling
Implementing split tunneling in WireGuard effectively requires adhering to best practices that encompass network design, traffic management, and security controls. These practices aim to optimize performance, maintain security, and meet specific requirements for different scenarios.
Network Design
- Design the network architecture to segregate traffic based on the split tunneling rules.
- Utilize separate network interfaces or VLANs for traffic that will traverse the tunnel and traffic that will bypass it.
- Implement firewall rules to enforce the split tunneling policies.
Traffic Management
- Establish clear policies for determining which traffic should be routed through the tunnel and which should bypass it.
- Use traffic shaping or QoS mechanisms to prioritize and manage traffic flow.
- Monitor traffic patterns to ensure optimal performance and identify potential issues.
Security Controls
- Implement strong authentication mechanisms for WireGuard connections.
- Use IPsec or other encryption protocols to secure the tunnel traffic.
- Regularly update WireGuard software and monitor for security vulnerabilities.
Future Developments in Split Tunneling
Split tunneling technology is rapidly evolving, with new developments emerging to enhance its capabilities and security. WireGuard, as a leading VPN protocol, is expected to incorporate these advancements to provide a more robust and flexible split tunneling solution.One key trend in split tunneling is the integration of artificial intelligence (AI) and machine learning (ML) algorithms.
These technologies can automate the process of identifying and routing specific traffic through the tunnel, based on pre-defined rules or real-time analysis of network usage patterns. This can improve performance and reduce the need for manual configuration.Another area of development is the integration of zero-trust network access (ZTNA) principles into split tunneling.
ZTNA requires users and devices to be authenticated and authorized before accessing specific network resources. By combining ZTNA with split tunneling, organizations can implement more granular access controls and reduce the risk of unauthorized access to sensitive data.Furthermore, the future of split tunneling may involve the adoption of quantum-resistant encryption algorithms.
As quantum computers become more powerful, traditional encryption methods may become vulnerable to attack. Quantum-resistant algorithms can provide an additional layer of security for split tunneling connections, ensuring the confidentiality and integrity of data even in the face of future advancements in computing technology.
Closure

Mastering WireGuard split tunnel configuration empowers you with granular control over your network traffic, enhancing both security and flexibility. Whether you seek to protect sensitive data, access geo-restricted content, or optimize network performance, this guide will equip you with the knowledge and techniques to harness the full potential of split tunneling.