ssh.sshslowdns.com – In the realm of secure and flexible networking, WireGuard split tunneling has emerged as a game-changer. This innovative technique allows you to selectively route specific traffic through a VPN tunnel while maintaining direct access to your local network for other applications.
Discover the benefits, use cases, and implementation strategies of WireGuard split tunneling in this comprehensive guide.
WireGuard’s split tunneling capabilities provide unparalleled control over your network traffic, enabling you to enhance privacy and security while maintaining seamless access to local resources. Whether you’re a seasoned network engineer or a home user seeking greater control over your online presence, this guide will empower you with the knowledge to harness the power of WireGuard split tunneling.
WireGuard Split Tunneling Basics
Split tunneling in WireGuard allows you to selectively route specific traffic through the VPN tunnel while allowing other traffic to bypass the tunnel and directly access the internet.
This is useful in scenarios where you want to protect sensitive traffic (such as banking or work-related data) through the VPN tunnel while maintaining regular internet access for other activities (such as streaming or gaming).
Benefits of Split Tunneling
- Improved performance for non-VPN traffic
- Reduced VPN bandwidth usage
- Enhanced security for sensitive data
- Flexibility in network configurations
Use Cases of Split Tunneling
- Accessing local resources on a VPN-connected device
- Splitting work and personal traffic
- Improving performance for latency-sensitive applications
- Bypassing VPN restrictions on certain websites or services
Configuring WireGuard Split Tunneling
Configuring split tunneling in WireGuard involves modifying the configuration files on both the client and server sides. This allows you to specify which traffic should be routed through the WireGuard tunnel and which should remain on your local network.
Modifying the Server Configuration
To enable split tunneling on the server, add the following line to the server configuration file:“`AllowedIPs = 0.0.0.0/0, ::/0 except 192.168.0.0/24, fe80::/10“`This line specifies that all traffic from the client will be routed through the WireGuard tunnel, except for traffic destined for the local network (192.168.0.0/24) and link-local addresses (fe80::/10).
Modifying the Client Configuration
On the client side, add the following line to the client configuration file:“`AllowedIPs = 192.168.0.0/24“`This line specifies that only traffic destined for the local network (192.168.0.0/24) should be excluded from the WireGuard tunnel.
Example Configuration Files
Server Configuration (Linux):“`[Interface]Address = 10.0.0.1/24ListenPort = 51820PrivateKey = /etc/wireguard/server-private.key[Peer]PublicKey = /etc/wireguard/client-public.keyAllowedIPs = 0.0.0.0/0, ::/0 except 192.168.0.0/24, fe80::/10“`Client Configuration (Linux):“`[Interface]Address = 10.0.0.2/24PrivateKey = /etc/wireguard/client-private.key[Peer]PublicKey
= /etc/wireguard/server-public.keyAllowedIPs = 192.168.0.0/24“`
Routing Traffic through the Tunnel
When split tunneling is enabled, traffic destined for specific networks is routed through the WireGuard tunnel while other traffic continues to use the default gateway. This allows users to access both local and remote resources securely without compromising their privacy.
Routing Table
The routing table is responsible for determining the path that traffic takes through the network. When split tunneling is enabled, the routing table is modified to include a new route for the specific networks that should be routed through the tunnel.
This ensures that traffic destined for those networks is sent to the WireGuard interface instead of the default gateway.
Firewall Rules
In addition to the routing table, firewall rules are also used to control the flow of traffic through the tunnel. Firewall rules can be used to block or allow specific types of traffic from entering or leaving the tunnel. This allows users to fine-tune the security of their split tunneling setup.
Excluding Specific Applications from the Tunnel
In certain scenarios, you may want to exclude specific applications or traffic from being routed through the WireGuard tunnel. This allows you to maintain direct internet access for those applications while still using the tunnel for other traffic.
Using Rules
One way to exclude applications is by using firewall rules. For example, in the firewall configuration of your WireGuard interface, you could add a rule that blocks traffic from a specific application or port range. This rule would take precedence over the default routing rules and prevent the traffic from being sent through the tunnel.
Using Tags
Another approach is to use tags. You can assign tags to network interfaces and then use those tags in firewall rules to control traffic flow. By tagging the interface used by the excluded applications, you can create a firewall rule that matches the tag and bypasses the tunnel.
This method provides more flexibility and allows you to exclude multiple applications or traffic types with a single rule.
Advanced Split Tunneling Techniques
Advanced split tunneling techniques provide greater control over how traffic is routed through the VPN tunnel. These techniques can be useful for organizations that need to meet specific security or performance requirements.One advanced split tunneling technique is to use multiple tunnels.
This allows traffic to be routed through different tunnels based on its destination. For example, an organization could have one tunnel for traffic destined for the corporate network and another tunnel for traffic destined for the public internet. This can help to improve performance and security by isolating traffic from different sources.Another
advanced split tunneling technique is to use policy-based routing. This allows traffic to be routed through the VPN tunnel based on specific criteria, such as the source or destination IP address, the port number, or the application protocol. This can be useful for organizations that need to control access to specific resources or applications.
Benefits of Advanced Split Tunneling Techniques
* Improved performance: By isolating traffic from different sources, advanced split tunneling techniques can help to improve performance by reducing congestion on the VPN tunnel.
Increased security
By controlling which traffic is routed through the VPN tunnel, advanced split tunneling techniques can help to improve security by reducing the risk of data breaches.
Greater flexibility
Advanced split tunneling techniques provide greater flexibility for organizations to meet their specific security and performance requirements.
Drawbacks of Advanced Split Tunneling Techniques
* Increased complexity: Advanced split tunneling techniques can be more complex to configure and manage than basic split tunneling.
Potential performance issues
If multiple tunnels are used, there is the potential for performance issues if the tunnels are not properly configured.
Security risks
If policy-based routing is used, there is the potential for security risks if the policies are not properly configured.
Troubleshooting Split Tunneling Issues
Using WireGuard split tunneling can occasionally lead to unexpected behavior. This section will explore common issues and provide troubleshooting tips to resolve them.
Before delving into specific issues, it’s crucial to ensure that WireGuard is properly configured and functioning as intended. Verify that the WireGuard interface is up and running, and check the routing table to confirm that traffic is being routed through the tunnel as expected.
Identifying Common Issues
- No traffic is routed through the tunnel: This can occur if the firewall is blocking traffic to the WireGuard interface or if the routing rules are not set up correctly.
- Only some traffic is routed through the tunnel: This might indicate that the split tunneling rules are not configured properly or that specific applications are excluded from the tunnel.
- Unexpected traffic is routed through the tunnel: This can happen if the routing rules are too broad or if there are conflicting rules in the routing table.
Troubleshooting Tips
- Check the firewall: Ensure that the firewall is not blocking traffic to the WireGuard interface. If necessary, add rules to allow traffic on the appropriate ports (UDP 51820 by default).
- Review the routing rules: Verify that the routing rules are set up correctly to route traffic through the tunnel as intended. Check for any conflicting rules or incorrect gateway settings.
- Examine the split tunneling rules: Ensure that the split tunneling rules are configured properly to exclude the desired applications from the tunnel. Check for any typos or incorrect IP addresses.
- Test with a packet sniffer: Use a packet sniffer to monitor traffic and determine if it is being routed through the tunnel as expected. This can help identify any unexpected behavior or routing issues.
Performance Considerations

Split tunneling with WireGuard generally incurs minimal performance overhead compared to a full VPN tunnel. However, certain factors can influence the performance:
Tunnel Overhead
WireGuard introduces a small amount of overhead associated with encrypting and decrypting traffic. This overhead is typically negligible, especially for modern CPUs. However, it can become more noticeable with high-bandwidth connections or a large number of concurrent connections.
Routing
The routing configuration can also impact performance. Split tunneling requires careful routing rules to ensure that only specific traffic is routed through the tunnel. Complex routing rules or inefficient routing tables can introduce delays or performance issues.
Security Implications
WireGuard split tunneling offers convenience and flexibility in network configurations, but it also introduces security implications that require careful consideration.
Split tunneling divides network traffic, allowing certain applications or destinations to bypass the VPN tunnel while others are routed through it. This creates a potential security risk as unencrypted traffic outside the tunnel can be intercepted and compromised.
Potential Risks
- Data Leakage: Unencrypted traffic outside the VPN tunnel is vulnerable to interception, exposing sensitive data such as passwords, financial information, and personal communications.
- Malware Infections: Malicious actors can exploit unencrypted traffic to bypass security measures and infect devices with malware, leading to data breaches or system compromise.
- Network Reconnaissance: Attackers can analyze unencrypted traffic to gather information about network topology, IP addresses, and open ports, facilitating targeted attacks.
Mitigations
- Strong Encryption: Implement robust encryption algorithms and protocols for both the VPN tunnel and the underlying network to protect sensitive data from interception.
- Least Privilege: Configure split tunneling policies carefully, only allowing essential applications or destinations to bypass the VPN tunnel.
- Regular Monitoring: Monitor network traffic for suspicious activity and implement intrusion detection and prevention systems to identify and mitigate potential threats.
- User Education: Educate users about the security risks associated with split tunneling and provide guidance on best practices for secure usage.
Comparison with Other Split Tunneling Solutions
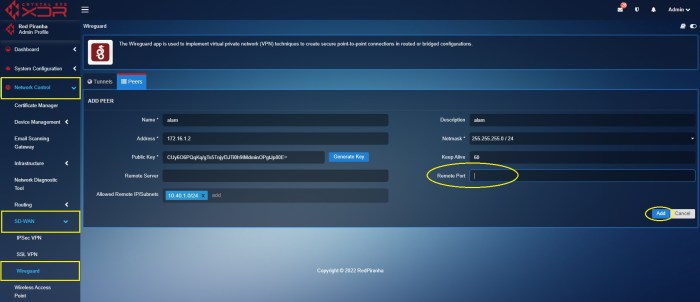
WireGuard split tunneling compares favorably to other split tunneling solutions, offering a combination of performance, security, and ease of use. Let’s compare it with two popular alternatives:
OpenVPN
- Advantages: Well-established, highly customizable, supports a wide range of platforms.
- Disadvantages: Slower performance compared to WireGuard, more complex to configure.
pfSense
- Advantages: Powerful firewall and routing capabilities, flexible configuration options.
- Disadvantages: Requires a dedicated hardware or virtual appliance, can be more complex to set up and manage than WireGuard.
Overall, WireGuard split tunneling stands out for its superior performance, simplicity, and open-source nature, making it a compelling choice for users seeking a secure and efficient split tunneling solution.
Real-World Applications
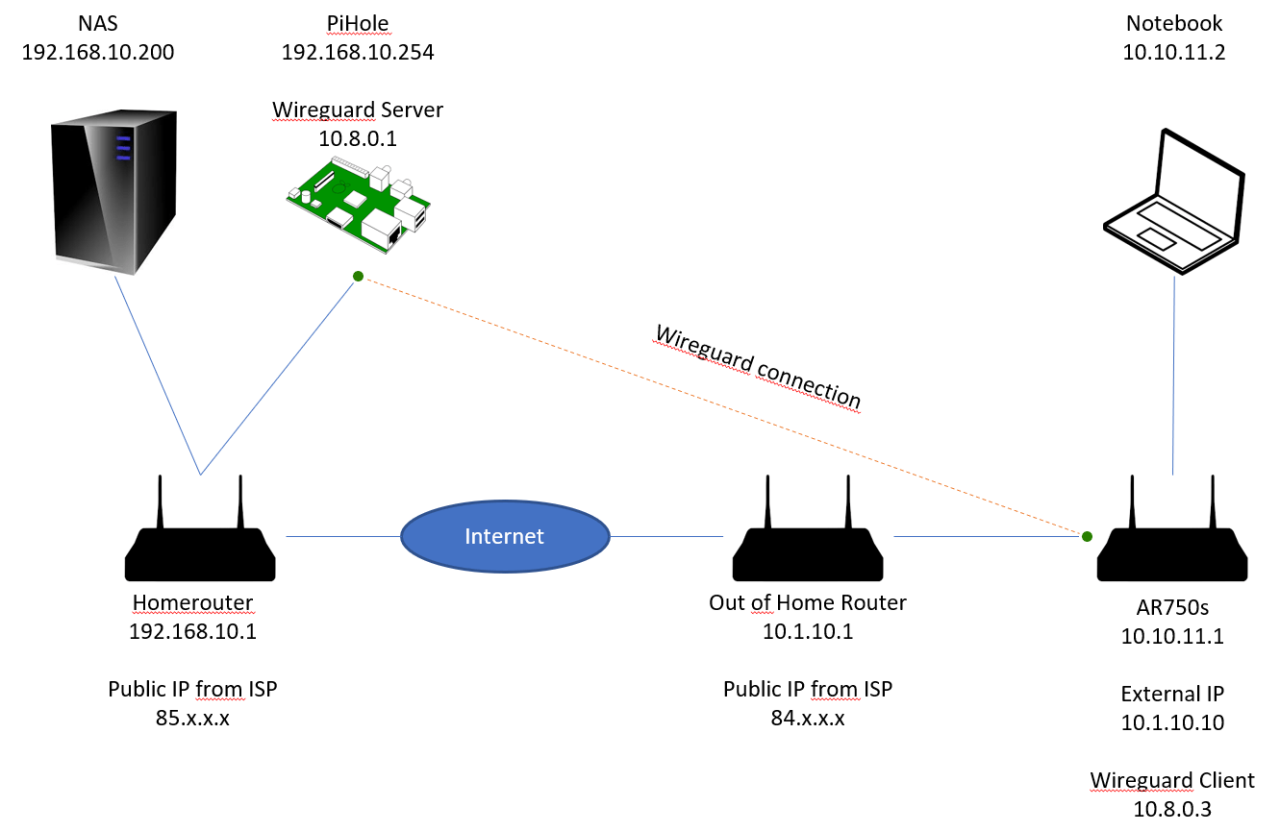
WireGuard split tunneling finds practical applications in various real-world scenarios, offering benefits and challenges that vary depending on the specific use case.
Secure Remote Access
Split tunneling enables secure remote access to corporate resources while allowing local internet traffic to bypass the VPN tunnel. This allows employees to access internal applications and data while still accessing local resources like printers and intranet sites. Benefits include improved security and convenience, but challenges include managing access policies and ensuring compliance.