In the realm of virtual private networks (VPNs), WireGuard stands out as a cutting-edge solution offering exceptional speed and security. Among its advanced features is split tunneling, a technique that empowers users with granular control over their network traffic, enabling them to route specific applications or services through the VPN while maintaining direct access to local network resources.
This comprehensive guide delves into the concept of WireGuard split tunneling, exploring its benefits, configuration process, use cases, and security considerations. We will also delve into advanced configuration options and integration with other network tools, providing a comprehensive understanding of this powerful networking feature.
Concept of WireGuard Split Tunneling
Split tunneling is a network configuration that allows specific traffic to bypass a VPN connection while other traffic is routed through the VPN. This can be useful for accessing local resources or devices that are not accessible through the VPN.
WireGuard implements split tunneling by allowing users to specify which IP addresses or subnets should be excluded from the VPN tunnel.
How WireGuard Implements Split Tunneling
WireGuard implements split tunneling by using the AllowedIPs and ExcludeIPs settings. The AllowedIPs setting specifies which IP addresses or subnets are allowed to bypass the VPN tunnel. The ExcludeIPs setting specifies which IP addresses or subnets are excluded from the VPN tunnel.For
example, to allow all traffic from the local subnet (192.168.1.0/24) to bypass the VPN tunnel, you would use the following AllowedIPs setting:“`AllowedIPs = 192.168.1.0/24“`To exclude all traffic from the 10.0.0.0/8 subnet from the VPN tunnel, you would use the following ExcludeIPs setting:“`ExcludeIPs = 10.0.0.0/8“`
Benefits of Using WireGuard Split Tunneling
WireGuard split tunneling offers several advantages that enhance network functionality and user experience.
Improved Performance for Local Network Resources
By selectively routing specific traffic through the local network, split tunneling improves the performance of local network resources. This is particularly beneficial for applications and services that require low latency and high bandwidth, such as streaming media, gaming, and file sharing.
Configuration of WireGuard Split Tunneling
Setting up split tunneling with WireGuard involves configuring your WireGuard interface and routing table to direct specific traffic through the VPN tunnel while allowing other traffic to bypass it.
The configuration process may vary slightly depending on your operating system and network setup, but the general steps are as follows:
Interface Configuration
First, you need to create a WireGuard interface on your device. This can be done using the “wg” command in the terminal. You will need to specify the interface name, public key, and private key for the interface.
- For example, on Linux, you can use the following command:
wg set wg0 private-key privatekey
wg set wg0 listen-port 51820
wg set wg0 public-key publickey
wg-genkey | tee privatekey | wg pubkey | tee publickey Peer Configuration
Next, you need to configure a peer for the WireGuard interface.
This involves specifying the IP address or hostname of the remote WireGuard server, as well as the public key of the server.
- For example, you can use the following command to add a peer:
wg set wg0 peer 192.168.1.1 public-key serverpublickey
allowed-ips 192.168.1.0/24 Routing Configuration
Finally, you need to configure your routing table to direct specific traffic through the WireGuard tunnel. This can be done using the “ip route” command in the terminal.
- For example, on Linux, you can use the following command to add a route:
ip route add 192.168.2.0/24 via 192.168.1.1 dev wg0 This command will route all traffic destined for the 192.168.2.0/24 network through the WireGuard tunnel.
Use Cases for WireGuard Split Tunneling
WireGuard split tunneling offers versatile applications, catering to specific networking needs. Here are a few notable use cases:
Streaming Media from Local Sources while Connected to a VPN
When connected to a VPN, accessing local media content can be challenging due to IP address conflicts. WireGuard split tunneling solves this by excluding local traffic from the VPN tunnel, allowing seamless streaming from local sources while maintaining VPN protection for internet traffic.
Accessing Local Network Devices Remotely without Compromising Privacy
Remotely accessing local network devices, such as printers or file servers, can be risky without proper security measures. WireGuard split tunneling allows remote access to these devices while maintaining privacy by only routing essential traffic through the VPN.
Managing Multiple Network Connections Simultaneously
In scenarios where multiple network connections are necessary, WireGuard split tunneling simplifies management. By separating local traffic from VPN traffic, users can effortlessly switch between networks without interrupting local connectivity or VPN protection.
Comparison to Other VPN Split Tunneling Solutions
WireGuard’s split tunneling compares favorably to other popular VPN solutions, such as OpenVPN and IPsec, offering distinct advantages and drawbacks.
Performance
WireGuard outperforms OpenVPN and IPsec in terms of speed and latency, making it ideal for bandwidth-intensive applications. Its streamlined protocol and modern cryptography contribute to its superior performance.
Security
WireGuard employs modern cryptography algorithms, including ChaCha20 and Poly1305, which are considered more secure than those used by OpenVPN and IPsec. Additionally, WireGuard’s codebase is smaller and simpler, reducing the potential for vulnerabilities.
Configuration
WireGuard is known for its simplicity and ease of configuration. Its straightforward syntax and well-documented interface make it accessible to users of varying technical backgrounds. In contrast, OpenVPN and IPsec require more complex configurations and specialized knowledge.
Specific Scenarios
WireGuard excels in scenarios where performance and security are paramount, such as gaming, video conferencing, and online streaming. OpenVPN remains a strong choice for environments with complex routing requirements or legacy compatibility concerns. IPsec is often preferred for enterprise networks with stringent security standards.
Security Considerations for WireGuard Split Tunneling
Split tunneling introduces unique security considerations that require careful attention to mitigate potential risks.
To ensure a secure implementation, consider the following recommendations:
Security Measures
- Restrict access to sensitive applications and data: Configure WireGuard to exclude critical applications and data from being routed through the VPN tunnel. This limits the exposure of sensitive information in case of a VPN compromise.
- Use strong encryption: Implement robust encryption algorithms, such as AES-256 or ChaCha20, to protect data transmitted through the VPN tunnel.
- Enable two-factor authentication (2FA): Require users to provide an additional authentication factor, such as a one-time password (OTP) or hardware token, when connecting to the VPN. This adds an extra layer of security to prevent unauthorized access.
- Regularly update WireGuard: Keep WireGuard up-to-date with the latest security patches and fixes to address potential vulnerabilities.
- Monitor VPN logs: Regularly review VPN logs for suspicious activity or unauthorized access attempts. This helps identify potential security breaches early on.
Troubleshooting WireGuard Split Tunneling Issues
Implementing WireGuard split tunneling may encounter occasional difficulties. To ensure seamless operation, it’s crucial to be aware of potential problems and have troubleshooting strategies in place.
Common issues that may arise include:
- Leakage of local traffic through the VPN: Verify that the firewall rules are configured correctly to prevent local traffic from being routed through the VPN interface.
- Inability to access local resources while connected to the VPN: Ensure that the WireGuard configuration includes a rule to allow traffic to the local subnet.
- DNS resolution issues: Check that the WireGuard configuration includes DNS settings and that the DNS servers are reachable.
- Performance degradation: Split tunneling can introduce additional overhead, potentially impacting network performance. Monitor network usage and adjust the WireGuard configuration if necessary.
Performance Optimization for WireGuard Split Tunneling
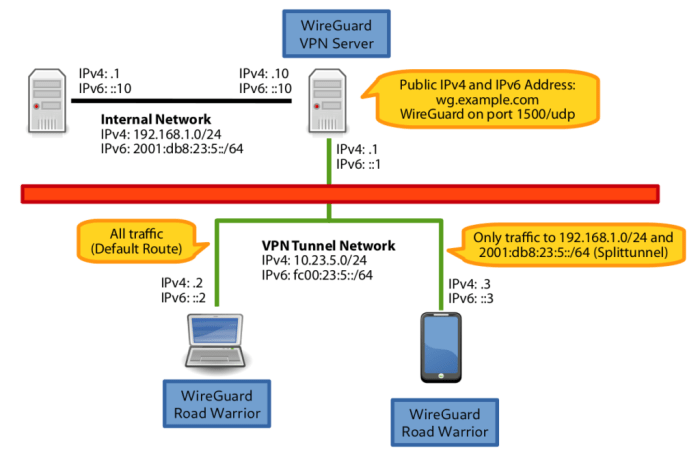
Optimizing performance in a WireGuard split tunneling setup is crucial to ensure seamless connectivity and prevent network latency. By implementing specific techniques and balancing security with speed, users can maximize the benefits of split tunneling without compromising network performance.
Balancing Security and Speed
Balancing security and speed in WireGuard split tunneling involves carefully configuring the VPN settings. Stronger encryption protocols, such as AES-256, provide enhanced security but may impact speed. Users should select an encryption level that aligns with their security requirements while considering the performance capabilities of their devices and network.
Additionally, optimizing MTU (Maximum Transmission Unit) settings can improve throughput and reduce latency.
Advanced Configuration Options for WireGuard Split Tunneling
WireGuard offers advanced configuration options for split tunneling, allowing users to customize their network routing and security policies. These options provide granular control over which traffic is routed through the VPN tunnel and which is excluded.
Custom Routing Tables
WireGuard allows users to define custom routing tables to specify how different types of traffic are handled. This enables fine-grained control over which traffic is routed through the VPN tunnel and which is sent directly to the internet. For example, a user could create a routing table that routes all work-related traffic through the VPN while allowing personal traffic to bypass the tunnel.
Network Rules
Network rules provide an additional layer of control over traffic flow. These rules can be used to filter traffic based on source and destination IP addresses, ports, and protocols. For example, a user could create a network rule to block all incoming traffic on a specific port or to allow only certain types of traffic through the VPN tunnel.
Integration of WireGuard Split Tunneling with Other Network Tools
WireGuard split tunneling can be seamlessly integrated with various network tools to enhance its functionality and meet specific network requirements. By combining WireGuard with firewalls, routers, and other network appliances, you can implement granular control over network traffic and optimize network performance.
Integration with Firewalls
Integrating WireGuard split tunneling with firewalls allows you to define specific firewall rules for traffic routed through the VPN tunnel. For instance, you can create rules to block certain types of traffic from accessing the VPN, while allowing other traffic to pass through.
This fine-grained control enhances network security by preventing unauthorized access to sensitive resources.
Integration with Routers
Integrating WireGuard split tunneling with routers enables you to configure advanced routing policies that optimize network performance. For example, you can configure routers to prioritize VPN traffic over other network traffic, ensuring a smooth and reliable VPN connection. Additionally, you can set up rules to route specific traffic through the VPN tunnel while allowing other traffic to bypass the VPN, optimizing bandwidth utilization.
Integration with Other Network Appliances
WireGuard split tunneling can also be integrated with various other network appliances, such as load balancers and intrusion detection systems (IDS). By integrating WireGuard with load balancers, you can distribute VPN traffic across multiple servers, enhancing scalability and improving performance.
Additionally, integrating WireGuard with IDS allows you to monitor and detect suspicious network activity, providing an additional layer of security.
Real-World Use Cases
Integrating WireGuard split tunneling with other network tools offers numerous benefits in real-world scenarios:
-
- -*Enhanced Security By integrating WireGuard with firewalls, you can implement strict firewall rules to protect sensitive data and prevent unauthorized access.
-*Optimized Network Performance
Integrating WireGuard with routers allows you to optimize routing policies, ensuring smooth and reliable VPN connections while maximizing bandwidth utilization.
-*Granular Control
Integrating WireGuard with other network appliances provides granular control over network traffic, allowing you to tailor your network configuration to meet specific requirements.
Closing Summary

WireGuard split tunneling empowers users with unprecedented control over their network traffic, enhancing privacy, improving performance, and simplifying network management. Its ease of configuration, coupled with its robust security features, makes it an ideal solution for a wide range of use cases.
As the adoption of WireGuard continues to grow, split tunneling will undoubtedly play a pivotal role in shaping the future of secure and flexible networking.