In the realm of network security, Wireguard has emerged as a formidable contender, renowned for its robust encryption and lightning-fast performance. However, harnessing the full potential of Wireguard requires a deep understanding of its intricate logging capabilities. This comprehensive guide will delve into the structure, configuration, analysis, and security considerations of Wireguard logs, empowering you to maximize your network’s resilience and compliance.
From deciphering the log’s structure to leveraging visualization tools for enhanced analysis, this guide will equip you with the knowledge and techniques to effectively manage and troubleshoot Wireguard. Whether you’re a seasoned network administrator or a novice seeking to enhance your cybersecurity posture, this guide will serve as an invaluable resource for unlocking the full potential of Wireguard logs.
WireGuard Log Structure
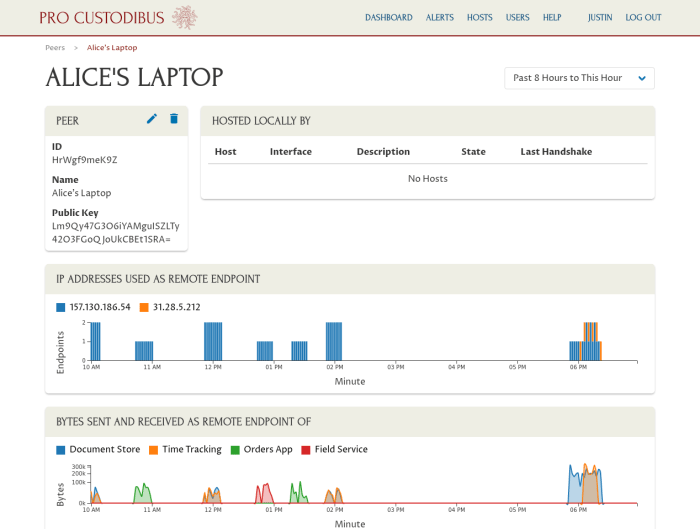
WireGuard logs provide a comprehensive record of events and activities within the VPN tunnel. They offer valuable insights for troubleshooting, performance analysis, and security monitoring.
WireGuard logs are structured in a chronological order, with each entry timestamped and categorized by severity level (debug, info, warning, error, fatal).
Types of Information Logged
- Connection Events: Log entries related to the establishment and termination of WireGuard connections, including peer IP addresses, timestamps, and status messages.
- Tunnel Establishment: Logs detailing the negotiation and establishment of WireGuard tunnels, including key exchange, endpoint configurations, and tunnel parameters.
- Packet Flow: Detailed records of packet transmission and reception, including source and destination IP addresses, port numbers, and packet sizes.
- Debug Messages: Extensive logging of internal WireGuard operations, providing insights into the behavior and performance of the VPN tunnel.
Configuring WireGuard Logging
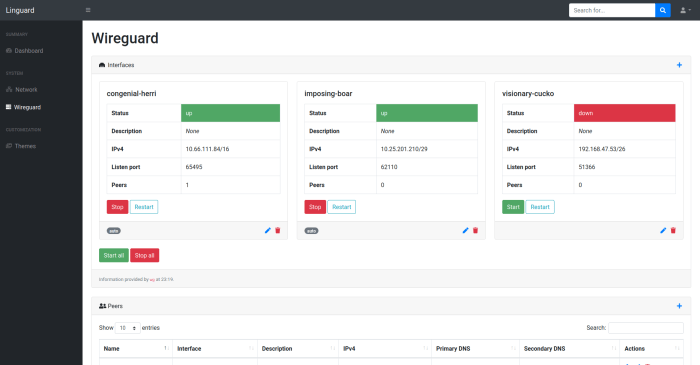
WireGuard provides robust logging capabilities to help users monitor and troubleshoot their VPN connections. Configuring logging levels allows users to control the amount and type of information recorded in the log files.Understanding the impact of different logging levels is crucial.
Higher logging levels capture more detailed information, which can be useful for debugging and analysis. However, it can also increase system overhead and potentially impact performance. Therefore, it’s essential to strike a balance between logging verbosity and system efficiency.
Analyzing WireGuard Logs
WireGuard logs provide valuable insights into the health and performance of your VPN connection. By analyzing these logs, you can identify potential issues, troubleshoot connectivity problems, and ensure the security of your network.To analyze WireGuard logs, follow these steps:
-
- 1.
- *Locate the log file. The WireGuard log file is typically located at `/var/log/wireguard/wg0.log` on Linux systems.
- 2.
- *Open the log file. You can use any text editor to open the log file.
- 3.
-*Filter the logs. Use the `grep` command to filter the logs for specific s or patterns. For example, to filter for errors, you can use the following command
`grep “error” wg0.log`.
-
- 4.
-*Analyze the results. Once you have filtered the logs, you can analyze the results to identify potential issues. Common errors and issues that can be detected through log analysis include
Connection failures
Routing problems
Security breaches
Performance issues
By analyzing WireGuard logs, you can proactively identify and resolve potential issues, ensuring the reliability and security of your VPN connection.
WireGuard Log Rotation
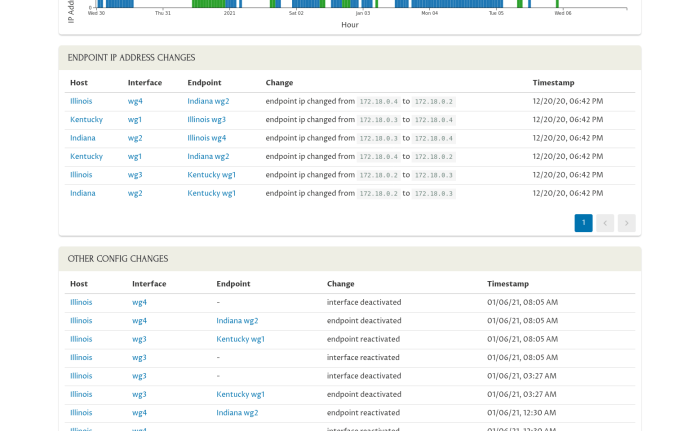
Log rotation is an essential practice in maintaining WireGuard logs. It ensures that log files do not grow indefinitely, potentially consuming excessive disk space and making it difficult to manage and analyze logs.
To set up log rotation for WireGuard, you can use the following steps:
Log File Configuration
-
- Edit the WireGuard configuration file (usually located at /etc/wireguard/wg0.conf).
- Add the following line to the file:
Log /var/log/wireguard/wg0.log
- Replace “wg0” with the name of your WireGuard interface.
- Save and close the configuration file.
Logrotate Configuration
-
- Create a new logrotate configuration file (e.g., /etc/logrotate.d/wireguard) with the following content:
/var/log/wireguard/*.log rotate 7 daily compress delaycompress missingok notifempty
- Replace “/var/log/wireguard/*.log” with the path to your WireGuard log files.
- Save and close the file.
Enable Logrotate
-
- Run the following command to enable logrotate:
logrotate /etc/logrotate.conf
WireGuard Log Security
WireGuard logs contain sensitive information, including IP addresses, connection timestamps, and traffic details. Exposing these logs to unauthorized parties could lead to various security risks, such as:
– -*Unauthorized access to the network: Attackers could use the logs to identify and target specific devices or hosts within the network. – -*Data breaches: The logs may contain sensitive data, such as passwords or encryption keys, which could be compromised and used to access confidential information.
– -*Network mapping: Attackers could use the logs to map out the network topology, identifying potential vulnerabilities and attack vectors.
Best Practices for WireGuard Log Security
To mitigate these risks, it is essential to implement robust log security measures, including:
– -*Restricting access to logs: Only authorized personnel should have access to WireGuard logs. This can be achieved through access control lists (ACLs) or role-based access control (RBAC). – -*Encrypting logs: WireGuard logs should be encrypted at rest and in transit to prevent unauthorized access.
This can be done using strong encryption algorithms, such as AES-256. – -*Regularly reviewing logs: Logs should be regularly reviewed for suspicious activity or unauthorized access attempts. This can help identify and mitigate potential security threats.
– -*Storing logs securely: WireGuard logs should be stored in a secure location, such as a dedicated log server or a cloud-based logging service. This ensures that the logs are protected from unauthorized access and potential data breaches.
By implementing these best practices, organizations can enhance the security of their WireGuard logs and protect their networks from potential threats.
WireGuard Log Visualization
Visualizing WireGuard logs provides an intuitive and comprehensive method to analyze and troubleshoot network issues. By transforming raw log data into graphical representations, it enhances the understanding of network activity and simplifies the identification of anomalies.
Interactive Log Viewers
Interactive log viewers, such as Kibana or Grafana, enable real-time monitoring and visualization of WireGuard logs. These tools allow users to create custom dashboards and visualizations, facilitating the correlation of events and the identification of patterns.
Graphical Network Maps
Graphical network maps provide a visual representation of the network topology, including WireGuard peers, tunnels, and traffic flow. By overlaying log data onto these maps, administrators can gain insights into the connectivity status, performance, and security of their networks.
Timeline Analysis
Timeline analysis tools enable the visualization of WireGuard logs over time. This helps identify trends, patterns, and anomalies in network activity. By correlating events with timestamps, administrators can quickly pinpoint the root cause of issues.
WireGuard Log Management Best Practices
Effective WireGuard log management involves implementing strategies to optimize storage, retention, and security. Here are some best practices to consider:
Log Storage Optimization
- Configure log rotation to prevent excessive disk space consumption.
- Use compression or archiving techniques to reduce log file sizes.
- Consider storing logs in a dedicated log management system or cloud service.
Log Retention Policies
Establish clear log retention policies based on regulatory compliance, security requirements, and operational needs. Consider factors such as:
- Data sensitivity and legal obligations
- Operational troubleshooting requirements
- Available storage capacity
Log Security
- Implement access controls to restrict unauthorized access to logs.
- Encrypt logs at rest and in transit to prevent unauthorized disclosure.
- Monitor logs for suspicious activity or security incidents.
Troubleshooting WireGuard Using Logs
WireGuard logs provide valuable insights into the behavior and health of your WireGuard setup. By analyzing logs, you can identify and resolve common issues, ensuring a stable and secure VPN connection.
Identifying and Resolving Common Issues
WireGuard logs can help you identify a wide range of issues, including:
- Connection problems (e.g., timeouts, failed handshakes)
- Configuration errors (e.g., incorrect IP addresses, missing keys)
- Security breaches (e.g., unauthorized access attempts)
To troubleshoot these issues, start by examining the log files for error messages and warnings. These messages will provide specific information about the problem, such as the time it occurred, the source of the error, and the action that triggered it.Once
you have identified the issue, refer to the WireGuard documentation or online forums for guidance on resolving it. Common solutions include:
- Verifying IP addresses and port numbers
- Ensuring that keys are correctly configured
- Checking for firewall or NAT issues
- Updating WireGuard to the latest version
Advanced Log Analysis Techniques
For more complex troubleshooting scenarios, you may need to use advanced log analysis techniques. These techniques involve using tools such as grep, sed, and awk to filter and analyze log data.For example, to find all log entries related to a specific IP address, you could use the following command:“`grep 192.168.1.1 /var/log/wireguard/wireguard.log“`By
combining these techniques with your understanding of WireGuard, you can effectively troubleshoot and resolve any issues that may arise with your VPN setup.
WireGuard Log Monitoring
WireGuard log monitoring involves tracking and analyzing log files generated by WireGuard to detect anomalies, security threats, and performance issues. Log monitoring tools can be used to automate this process and provide real-time alerts.
Centralized Logging
Centralized logging involves collecting logs from multiple WireGuard instances into a single location. This allows for easier analysis and management of logs. Log aggregation tools such as Fluentd or Logstash can be used for this purpose.
Real-Time Monitoring
Real-time monitoring involves using tools that continuously monitor WireGuard logs for suspicious activities or errors. These tools can send alerts via email, SMS, or other channels to notify administrators of potential issues.
Log Analysis Tools
Log analysis tools such as Splunk or ELK (Elasticsearch, Logstash, Kibana) can be used to analyze WireGuard logs. These tools provide advanced search and filtering capabilities, allowing administrators to quickly identify patterns and trends in the logs.
Security Monitoring
WireGuard logs can be monitored for security threats such as unauthorized access attempts, malware infections, or DDoS attacks. Security monitoring tools such as Suricata or Zeek can be used to detect and alert on suspicious activities.
Performance Monitoring
WireGuard logs can also be monitored for performance issues such as slow connection speeds, high latency, or packet loss. Performance monitoring tools such as Nagios or Prometheus can be used to track key performance metrics and alert on any deviations from normal behavior.
WireGuard Log Analysis for Compliance
WireGuard logs can provide valuable evidence for demonstrating compliance with regulatory requirements. By analyzing these logs, organizations can extract and interpret relevant data to prove their adherence to specific regulations.
Extracting Relevant Log Data
To extract relevant log data for compliance purposes, organizations should focus on identifying specific log entries that pertain to:
-
- User access and authentication
- Network configuration changes
- Security events (e.g., attempted breaches, failed logins)
- Compliance-specific actions (e.g., audits, system updates)
Last Word
Mastering Wireguard logs is not merely an exercise in technical proficiency; it’s an investment in the security and integrity of your network. By embracing the principles Artikeld in this guide, you can transform Wireguard logs from a passive record into a dynamic tool that empowers you to identify threats, troubleshoot issues, and demonstrate compliance with regulatory mandates.
Embrace the power of Wireguard logs and elevate your network’s security posture to new heights.