ssh.sshslowdns.com – In the realm of network security, WireGuard emerges as a game-changer with its unparalleled speed, security, and versatility. Among its many capabilities, split tunneling stands out as a powerful technique for optimizing network traffic and enhancing privacy. This guide delves into the intricacies of WireGuard Linux split tunneling, providing a comprehensive understanding of its benefits, configuration, and advanced techniques.
Split tunneling allows you to selectively route traffic through a VPN tunnel while maintaining direct connections for specific destinations. This granular control empowers you to protect sensitive data while maintaining optimal performance for applications that require low latency or local access.
WireGuard’s advanced features, such as policy-based routing, further enhance this capability, enabling you to tailor traffic handling based on specific criteria.
WireGuard Overview
WireGuard is a modern and secure VPN protocol that has gained popularity in recent years. It was designed with simplicity, speed, and security in mind, making it an attractive option for both personal and business use.WireGuard utilizes state-of-the-art cryptography and modern networking techniques to provide a highly secure and efficient VPN connection.
Unlike traditional VPN protocols, WireGuard does not rely on complex and legacy algorithms, resulting in significantly faster speeds and lower latency.
Key Features and Benefits
WireGuard offers several key features and benefits that make it stand out from other VPN protocols:
- Simplicity: WireGuard’s codebase is incredibly concise and easy to understand, making it more secure and less prone to vulnerabilities.
- Speed: WireGuard is designed for high performance and can achieve speeds that are comparable to a direct internet connection.
- Security: WireGuard employs robust encryption algorithms and modern cryptographic techniques to ensure the confidentiality and integrity of data transmitted over the VPN connection.
- Cross-platform compatibility: WireGuard is available for a wide range of platforms, including Linux, Windows, macOS, iOS, and Android.
- Open source: WireGuard is open source, allowing users to inspect the code and verify its security and functionality.
Advantages over Traditional VPN Protocols
Compared to traditional VPN protocols, WireGuard offers several advantages:
- Faster speeds: WireGuard’s modern design and efficient algorithms result in significantly faster connection speeds than legacy VPN protocols.
- Lower latency: WireGuard’s optimized networking techniques minimize latency, making it suitable for applications that require real-time responsiveness.
- Enhanced security: WireGuard’s use of state-of-the-art cryptography and modern security protocols provides a higher level of protection against cyber threats.
- Simplified configuration: WireGuard’s simple configuration process makes it easy to set up and manage, even for users with limited technical knowledge.
Overall, WireGuard’s combination of simplicity, speed, security, and cross-platform compatibility makes it an ideal choice for users seeking a reliable and high-performance VPN solution.
Split Tunneling with WireGuard
Split tunneling is a technique that allows you to route specific traffic through a VPN tunnel while allowing other traffic to go directly to the internet. This can be useful for a variety of reasons, such as:
- Protecting sensitive traffic, such as financial transactions or medical information, by sending it through the VPN tunnel.
- Accessing region-locked content by sending traffic for that specific website or service through the VPN tunnel.
- Improving performance for certain types of traffic, such as gaming or video streaming, by sending it directly to the internet.
How WireGuard Implements Split Tunneling
WireGuard implements split tunneling by allowing you to specify which traffic should go through the VPN tunnel and which traffic should go directly to the internet. This is done using the AllowedIPs setting in the WireGuard configuration file.
The AllowedIPs setting takes a list of IP addresses or subnets that are allowed to go through the VPN tunnel. Any traffic that is not destined for an IP address or subnet in the AllowedIPs list will go directly to the internet.
Use Cases for Split Tunneling
Split tunneling can be used in a variety of situations, such as:
- Protecting sensitive traffic from public Wi-Fi networks.
- Accessing region-locked content from abroad.
- Improving performance for online gaming or video streaming.
- Protecting your privacy by preventing your ISP from tracking your online activity.
Configuring WireGuard for Split Tunneling
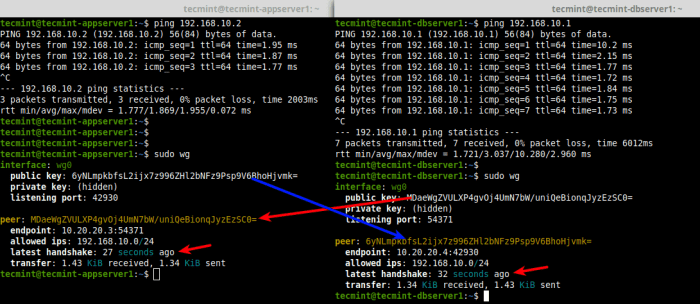
Split tunneling allows you to selectively route specific traffic through the WireGuard tunnel while excluding other traffic. This is useful for scenarios where you want to protect sensitive data while maintaining access to local resources.To configure WireGuard for split tunneling, follow these steps:
Exclude Specific Traffic from the Tunnel
- In the WireGuard configuration file, add the following line under the [Peer] section:
AllowedIPs = 0.0.0.0/0, ::/0 except 192.168.0.0/24
- This will exclude traffic from the 192.168.0.0/24 subnet from being routed through the tunnel.
Include Specific Traffic in the Tunnel
- Alternatively, you can specify specific IP addresses or subnets to be included in the tunnel:
AllowedIPs = 192.168.0.0/24, 2001:db8::/32
- This will only route traffic from the 192.168.0.0/24 and 2001:db8::/32 subnets through the tunnel.
Advanced Split Tunneling Techniques
WireGuard offers advanced split tunneling techniques beyond basic exclusion lists. One notable technique is policy-based routing, which allows you to define custom rules for handling specific types of traffic.
Policy-Based Routing
Policy-based routing enables you to create granular rules that determine how different traffic is routed through WireGuard. You can define rules based on various criteria, such as source IP address, destination IP address, port, or protocol. By defining specific rules, you can control which traffic goes through the VPN tunnel and which traffic remains on the local network.For
example, you can create a rule that sends all web traffic (port 80 and 443) through the VPN tunnel, while allowing all other traffic to bypass the tunnel and access the local network. This allows you to protect sensitive web traffic while maintaining access to local resources without sacrificing performance.Implementing
policy-based routing involves creating a set of iptables rules that match the desired traffic criteria and redirect it to the WireGuard interface. The specific rules will vary depending on your requirements and network configuration.
Troubleshooting Split Tunneling with WireGuard
Identifying and resolving issues with WireGuard split tunneling requires a systematic approach. Common errors may include connection failures, incorrect routing, or DNS resolution problems.
Identifying Common Issues and Error Messages
*
-*Connection failures
Check firewall settings, interface configurations, and WireGuard configuration files for errors.
-
- -*Incorrect routing
Verify routing tables and ensure traffic is being routed correctly through the tunnel.
- -*Incorrect routing
-*DNS resolution problems
Check DNS settings and ensure the DNS server is accessible and configured correctly.
Troubleshooting Tips and Solutions
*
-*Restart the WireGuard interface
This can resolve temporary connection issues or routing problems.
-
- -*Check firewall rules
Ensure that incoming and outgoing traffic is allowed on the appropriate ports and interfaces.
- -*Check firewall rules
-*Review WireGuard configuration files
Check for errors in syntax, IP addresses, and port numbers.
-*Test connectivity
Use ping or traceroute commands to verify connectivity to both internal and external networks.
-*Check DNS settings
Ensure that the DNS server is reachable and that DNS settings are correct in both the WireGuard configuration and system settings.
Diagnosing and Resolving Connection Problems
*
-*Check the WireGuard logs
They can provide detailed information about connection attempts, errors, and routing issues.
-
- -*Use network monitoring tools
Wireshark or tcpdump can be used to capture and analyze network traffic, helping identify connection problems.
- -*Use network monitoring tools
-*Consult the WireGuard documentation
It provides comprehensive troubleshooting resources and guidance.
Performance and Security Considerations
Split tunneling can have both performance and security implications that need to be considered when implementing it.
Performance Implications
Split tunneling can improve performance for traffic that is not routed through the VPN by reducing the load on the VPN connection. This can be especially beneficial for applications that require high bandwidth, such as video streaming or gaming.
Security Implications
Split tunneling can also affect security and privacy. By allowing some traffic to bypass the VPN, it creates a potential attack surface for attackers to exploit. For example, an attacker could exploit a vulnerability in an application that is not routed through the VPN to gain access to the user’s network.
Recommendations
To optimize performance and security when using split tunneling, consider the following recommendations:
- Only allow traffic that is necessary to bypass the VPN.
- Use a reputable VPN provider that offers strong security features.
- Keep your VPN software up to date.
- Monitor your VPN connection for suspicious activity.
Comparing WireGuard to Other Split Tunneling Solutions
WireGuard is a relatively new VPN protocol that has quickly gained popularity due to its simplicity, speed, and security. However, it is not the only split tunneling solution available. Other popular options include OpenVPN and IPsec.
Each of these solutions has its own advantages and disadvantages. WireGuard is generally considered to be the fastest and most secure option, but it is also the most complex to configure. OpenVPN is a more mature solution that is easier to configure, but it is not as fast or secure as WireGuard.
IPsec is a widely used protocol that is supported by a wide range of devices, but it is not as easy to configure as WireGuard or OpenVPN.
Choosing the Best Solution
The best split tunneling solution for you will depend on your specific needs. If you need the fastest and most secure solution, WireGuard is the best choice. If you need a solution that is easy to configure, OpenVPN is a good option.
If you need a solution that is supported by a wide range of devices, IPsec is a good choice.
Creating a Comprehensive Guide to WireGuard Split Tunneling
Creating a comprehensive guide to WireGuard split tunneling requires meticulous organization and a logical structure. The guide should be structured to facilitate easy understanding and navigation, with clear sections and subsections. It should include clear and concise explanations, examples, and a table summarizing key configuration parameters for quick reference.
The guide should cover the following topics in a logical order:
- Introduction to WireGuard and its benefits
- Explanation of split tunneling and its advantages
- Step-by-step instructions on configuring WireGuard for split tunneling
- Advanced split tunneling techniques, such as using multiple WireGuard interfaces
- Troubleshooting common issues with split tunneling
- Performance and security considerations
- Comparison of WireGuard to other split tunneling solutions
HTML Table for Key Configuration Parameters
To provide a quick reference for users, the guide should include an HTML table summarizing the key configuration parameters for WireGuard split tunneling. This table should include the following information:
- Parameter name
- Description
- Default value
- Example
Using WireGuard Split Tunneling for Specific Applications
WireGuard split tunneling offers flexibility in controlling which applications use the VPN tunnel and which access the internet directly. This selective routing capability enhances privacy, security, and performance for specific applications.To configure WireGuard split tunneling for specific applications, you need to create a firewall rule that routes traffic from the desired applications through the VPN interface.
Here’s an example using iptables for Linux:“`iptables
- t mangle
- A OUTPUT
- p tcp
- d 10.0.0.1
- -dport 443
- j MARK
- -set-mark 1
iptables
- t mangle
- A OUTPUT
- j ACCEPT
iptables
- t mangle
- A OUTPUT
- m mark
- -mark 1
- j ACCEPT
“`This rule marks traffic destined for a specific IP address (10.0.0.1) and port (443) and then routes it through the VPN interface. You can modify the IP address and port to match your specific application.
Popular Applications for WireGuard Split Tunneling
WireGuard split tunneling is particularly beneficial for applications that require both privacy and direct internet access, such as:
- Web browsing: Access sensitive websites through the VPN while browsing general websites directly for faster speeds.
- Online banking: Protect financial transactions while accessing other online services without the VPN.
- Gaming: Enjoy low-latency gaming without compromising security for other online activities.
- Streaming: Stream geo-restricted content through the VPN while maintaining fast speeds for other online tasks.
- Cloud services: Access cloud-based applications through the VPN while using other internet services directly.
Illustrating WireGuard Split Tunneling with Network Diagrams
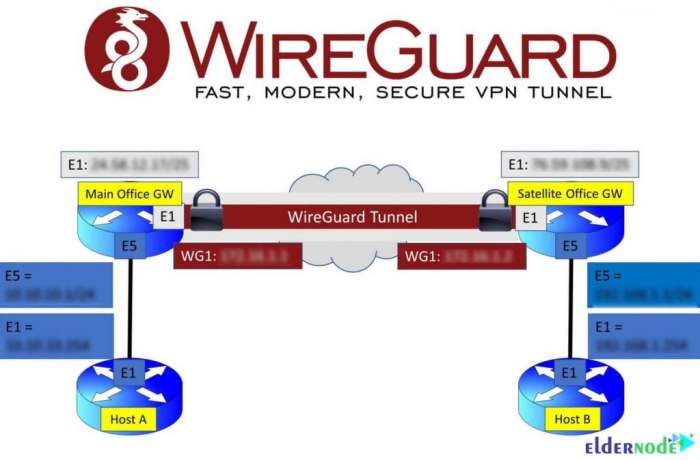
Network diagrams play a crucial role in understanding the concepts and implementation of WireGuard split tunneling. They visually depict the network topology, routing mechanisms, and traffic flow through the tunnel.
The diagrams illustrate how traffic is selectively routed through the tunnel based on destination IP addresses or application ports. This allows specific traffic to be encrypted and transmitted securely while other traffic remains on the local network.
Network Diagram of Basic Split Tunneling
This diagram shows a basic split tunneling configuration. The client device is connected to both a local network and a WireGuard tunnel.
- Traffic destined for specific IP addresses or application ports is routed through the tunnel.
- Other traffic remains on the local network, providing access to local resources and the internet without encryption.
Network Diagram of Advanced Split Tunneling
This diagram demonstrates advanced split tunneling techniques, such as source-based routing and multiple tunnels.
- Source-based routing allows traffic from specific devices or applications to be routed through the tunnel.
- Multiple tunnels can be used to provide separate encryption for different types of traffic or to connect to multiple remote networks.
Network Diagram of Troubleshooting Split Tunneling
This diagram illustrates potential issues that can arise with split tunneling, such as routing conflicts or incorrect firewall rules.