In the realm of virtual private networks (VPNs), WireGuard has emerged as a game-changer. Its lightning-fast speeds, robust security, and cross-platform compatibility have made it a favorite among privacy-conscious users. One of WireGuard’s most compelling features is its support for split tunneling on iOS devices, allowing you to selectively route specific traffic through the VPN while excluding others.
This guide will delve into the intricacies of WireGuard iOS split tunneling, empowering you to harness its potential and enhance your online privacy and security.
Understanding WireGuard
WireGuard is a modern, open-source VPN protocol designed to provide secure and efficient virtual private networks. It is a next-generation VPN protocol that aims to overcome the limitations and complexities of traditional VPN protocols.
One of the key benefits of WireGuard is its simplicity. The WireGuard codebase is significantly smaller than that of other VPN protocols, making it easier to audit and maintain. This simplicity also contributes to WireGuard’s high performance and low resource usage.
Advantages of WireGuard over Other VPN Protocols
- Simplicity: WireGuard’s codebase is significantly smaller and simpler than that of other VPN protocols, making it easier to audit and maintain.
- Performance: WireGuard is known for its high performance and low resource usage, making it suitable for use on even low-powered devices.
- Security: WireGuard uses state-of-the-art cryptography and modern algorithms to ensure the security of your data.
- Cross-platform support: WireGuard is available for a wide range of platforms, including Windows, macOS, Linux, iOS, and Android.
iOS Split Tunneling with WireGuard
Split tunneling is a networking feature that allows you to selectively route specific traffic through a VPN tunnel while allowing other traffic to bypass the tunnel and connect directly to the internet.
WireGuard supports split tunneling on iOS devices by allowing you to create multiple WireGuard tunnels and assign specific apps or traffic types to each tunnel. This gives you the flexibility to protect sensitive traffic with a VPN while allowing other traffic, such as streaming or gaming, to bypass the VPN and maintain optimal performance.
Configuring Split Tunneling with WireGuard on iOS
- Install the WireGuard app from the App Store.
- Create a new WireGuard tunnel and configure it with the desired settings.
- Tap on the “Allowed Apps” section and select the apps or traffic types that you want to route through the VPN tunnel.
- Toggle the “Split Tunneling” switch to enable split tunneling.
Once you have configured split tunneling, only the traffic from the selected apps or traffic types will be routed through the VPN tunnel. All other traffic will bypass the VPN and connect directly to the internet.
Configuring WireGuard Split Tunnel on iOS
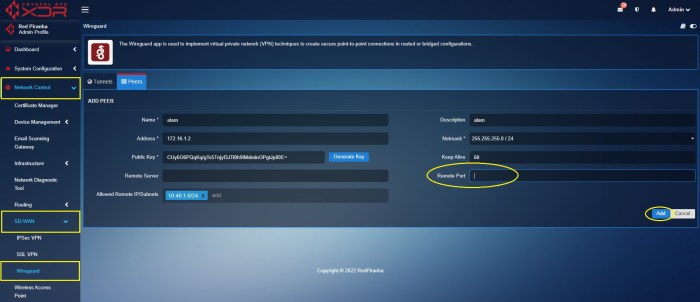
To configure WireGuard split tunneling on your iOS device, follow these steps:
- Ensure you have a WireGuard configuration file (.conf) and a valid VPN profile.
- Download and install the WireGuard app from the App Store.
- Open the WireGuard app and tap the “+” icon to add a new tunnel.
- Tap “Import from file” and select the WireGuard configuration file you downloaded.
- Review the tunnel settings and make any necessary changes.
- Enable the “Split Tunneling” option.
- Tap “Save” to create the tunnel.
- Connect to the VPN by tapping the toggle switch next to the tunnel name.
Customizing Split Tunnel Rules
WireGuard allows you to customize split tunnel rules to specify which traffic should be tunneled and which should bypass the VPN connection. This provides granular control over your network traffic and allows you to optimize your VPN usage.
To create a custom split tunnel rule, you can use the AllowedIPs and ExcludedIPs directives in the WireGuard configuration file.
AllowedIPs
The AllowedIPs directive specifies the IP addresses or subnets that should be tunneled through the VPN connection. Traffic destined for any other IP address will bypass the VPN.
- To allow all traffic to be tunneled, use
AllowedIPs = 0.0.0.0/0. - To allow traffic to a specific IP address, use
AllowedIPs = 192.168.1.100. - To allow traffic to a specific subnet, use
AllowedIPs = 192.168.1.0/24.
ExcludedIPs
The ExcludedIPs directive specifies the IP addresses or subnets that should bypass the VPN connection. Traffic destined for any of these IP addresses will not be tunneled.
- To exclude all traffic from being tunneled, use
ExcludedIPs = 0.0.0.0/0. - To exclude traffic to a specific IP address, use
ExcludedIPs = 192.168.1.100. - To exclude traffic to a specific subnet, use
ExcludedIPs = 192.168.1.0/24.
You can use both AllowedIPs and ExcludedIPs directives to create complex split tunnel rules. For example, you could allow all traffic to be tunneled except for traffic to a specific website or IP address.
Performance Considerations
Split tunneling can potentially impact network performance by introducing additional processing overhead on the device. This is because the device needs to determine which traffic should be routed through the VPN tunnel and which traffic should be sent over the regular internet connection.
To optimize performance while using split tunneling, consider the following tips:
Choose the Right VPN Protocol
The choice of VPN protocol can impact the performance of split tunneling. Some protocols, such as OpenVPN, have higher overhead than others, such as WireGuard. If performance is a concern, consider using a protocol with lower overhead.
Limit the Number of Split Tunnel Rules
The more split tunnel rules you create, the more processing overhead the device will need to perform. If you only need to route a few specific applications through the VPN tunnel, create only the necessary rules.
Use a Fast VPN Server
The speed of your VPN server can also impact the performance of split tunneling. If you are experiencing slow speeds, try connecting to a different server.
Disable Unnecessary Features
Some VPN clients offer additional features, such as ad blocking or malware protection. These features can add to the processing overhead of split tunneling. If you do not need these features, disable them to improve performance.
Security Implications
Split tunneling introduces security considerations that require careful evaluation and mitigation strategies.
One potential risk is the exposure of sensitive traffic to untrusted networks. When only specific traffic is routed through the VPN tunnel, other traffic remains exposed to potential eavesdropping or interception on insecure public networks.
Mitigating Risks
- Implement strong authentication and encryption: Use robust authentication methods (e.g., multi-factor authentication) and encryption algorithms to protect VPN connections and sensitive data.
- Restrict access to VPN: Limit VPN access to authorized users and devices to prevent unauthorized access to sensitive networks.
- Monitor VPN connections: Regularly monitor VPN connections for suspicious activity or unauthorized access attempts.
- Educate users: Inform users about the security risks associated with split tunneling and provide guidance on safe usage practices.
Troubleshooting Split Tunnel Issues
When implementing split tunneling with WireGuard on iOS, you may encounter various issues. Here are some common problems and troubleshooting steps:
Connection Issues
- No Internet access: Ensure your WireGuard configuration is correct and that your device is connected to a stable network. Check if your firewall or antivirus software is blocking WireGuard traffic.
- DNS resolution issues: Configure custom DNS settings in WireGuard’s iOS app or use a DNS resolver that supports split tunneling.
Split Tunneling Behavior
- Apps not using the VPN: Check your split tunneling rules and ensure the apps you want to route through the VPN are included. Verify that the apps are not bypassing the VPN due to network configuration or app-specific settings.
- Traffic not following split tunneling rules: Review your WireGuard configuration and ensure the rules are correctly defined. Check if the traffic is being intercepted by other network services or applications.
Performance Issues
- Slow speeds: Optimize your WireGuard configuration by selecting the appropriate encryption algorithm and MTU size. Consider upgrading to a faster VPN server or adjusting your network settings.
- Packet loss or high latency: Check your network connection and ensure it is stable. Adjust the WireGuard MTU size or try using a different VPN server location.
Security Concerns
- DNS leaks: Configure custom DNS settings or use a DNS resolver that supports split tunneling to prevent DNS leaks.
- IP address leaks: Ensure your WireGuard configuration is secure and that you are using a reputable VPN provider. Consider using a kill switch to prevent traffic from leaking outside the VPN.
Advanced Features
WireGuard offers a range of advanced features that can further enhance split tunneling capabilities. These features provide additional flexibility and control over how traffic is routed.
To configure these features, modify the WireGuard configuration file ( wg0.conf ) located in /etc/wireguard and restart the WireGuard service.
Peer Exclusion
Peer exclusion allows you to specify specific peers that should not use the split tunnel. This is useful for excluding devices or services that require direct access to the local network.
To exclude a peer, add the ExcludePeers directive to the peer configuration:
[Peer] PublicKey = ... AllowedIPs = ... ExcludePeers = 192.168.1.100, 192.168.1.101
Allowed IPs
The AllowedIPs directive specifies the IP addresses or subnets that are allowed to be routed through the WireGuard tunnel. By default, all traffic is allowed, but you can restrict access to specific destinations as needed.
To specify allowed IP addresses, use the following syntax:
[Peer] PublicKey = ... AllowedIPs = 192.168.1.0/24, 10.0.0.0/16
DNS Servers
WireGuard allows you to specify custom DNS servers for the VPN connection. This can be useful for bypassing local DNS settings or improving privacy.
To configure DNS servers, add the DNS directive to the peer configuration:
[Peer] PublicKey = ... AllowedIPs = ... DNS = 8.8.8.8, 8.8.4.4
Comparison with Other VPN Solutions
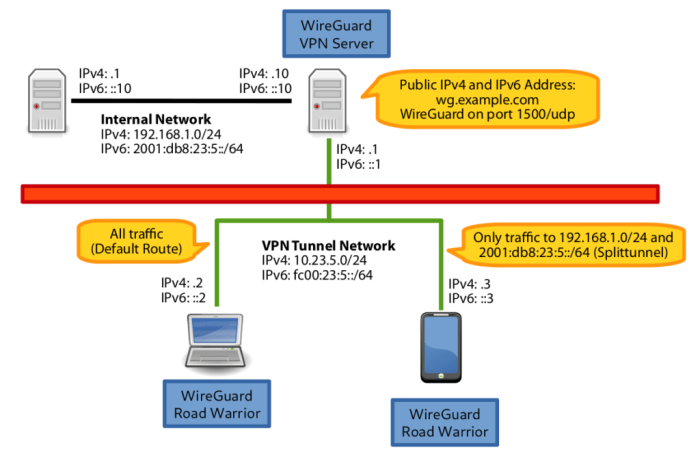
WireGuard’s split tunneling capabilities stand out in comparison to other popular VPN solutions. Let’s explore the strengths and weaknesses of each:
OpenVPN
OpenVPN is a widely used open-source VPN protocol known for its security and reliability. However, its split tunneling implementation is more complex and requires manual configuration, which can be challenging for non-technical users.
IPsec
IPsec is another widely adopted VPN protocol that supports split tunneling. It offers a stable and secure connection but can be more resource-intensive and may have compatibility issues with certain devices.
IKEv2
IKEv2 is a newer VPN protocol that provides fast and reliable connections. It supports split tunneling, but its implementation may vary depending on the VPN provider and device.
Strengths of WireGuard Split Tunneling:
– Ease of use: WireGuard’s split tunneling feature is simple to configure and use, making it accessible to users of all technical backgrounds. – Performance: WireGuard’s efficient protocol design results in faster and more reliable connections compared to other VPN protocols.
– Open source: WireGuard’s open-source nature allows for transparency, community support, and ongoing development.
Weaknesses of WireGuard Split Tunneling:
– Limited platform support: WireGuard is relatively new, and its split tunneling feature may not be supported on all platforms or devices. – Potential security concerns: While WireGuard is considered secure, it’s important to note that any VPN solution can introduce potential security risks, especially if not configured properly.
Case Studies
Split tunneling with WireGuard has been employed in various scenarios to address real-world networking challenges.
Benefits of Split Tunneling
Split tunneling offers several advantages, including:
– -*Improved performance: By directing only specific traffic through the VPN, split tunneling can reduce latency and improve overall network speed. – -*Enhanced security: It isolates sensitive traffic from the public internet, reducing the risk of data breaches or malware infections.
– -*Flexibility: Split tunneling allows users to customize their VPN connections, ensuring that only the desired traffic is encrypted and routed through the VPN.
Challenges of Split Tunneling
Despite its benefits, split tunneling also poses certain challenges:
– -*Configuration complexity: Implementing split tunneling can be technically complex, especially for non-technical users. – -*Potential for misconfiguration: Incorrectly configured split tunneling rules can lead to security vulnerabilities or performance issues. – -*Compatibility issues: Split tunneling may not be compatible with all devices or applications, which can limit its usefulness in certain environments.
Examples of Split Tunneling Use Cases
– -*Corporate networks: Businesses can use split tunneling to allow employees to access internal resources securely while maintaining internet access for personal use. – -*Public Wi-Fi security: Users can configure split tunneling to encrypt sensitive traffic while using public Wi-Fi networks, protecting their data from eavesdropping.
– -*Mobile device management: MDM solutions can utilize split tunneling to control and secure traffic from mobile devices, ensuring compliance with corporate policies. – -*Cloud access: Users can access cloud-based applications securely through a VPN while excluding local traffic from the tunnel, optimizing performance and reducing latency.
Summary
WireGuard iOS split tunneling offers a powerful and flexible solution for managing your network traffic. By carefully configuring split tunnel rules, you can optimize performance, enhance security, and tailor your VPN experience to your specific needs. Whether you’re a seasoned VPN user or just starting your journey, this guide has provided you with the knowledge and tools to leverage WireGuard’s capabilities and unlock the full potential of split tunneling.