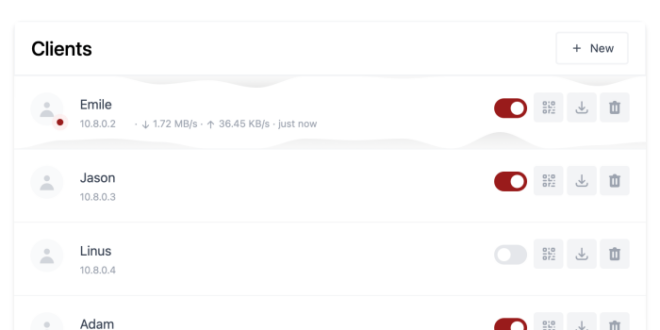
In the realm of virtual private networks (VPNs), WireGuard stands out as a game-changer, offering unparalleled speed, security, and ease of use. By leveraging the power of Docker, you can effortlessly deploy and manage WireGuard within isolated containers, unlocking a world of possibilities for secure and flexible networking.
This comprehensive guide will equip you with the knowledge and practical steps to set up, configure, and optimize WireGuard in Docker. From network configuration to client connectivity, security considerations to performance optimization, we’ll delve into every aspect to empower you with a robust and secure VPN solution.
Docker Image Setup
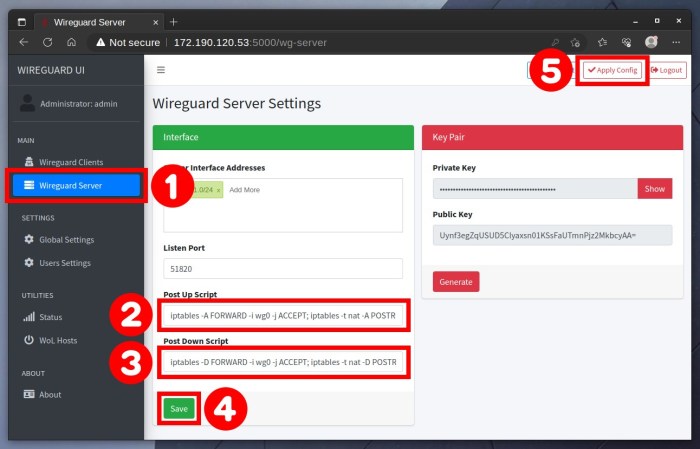
Setting up a WireGuard Docker image involves pulling the official image from Docker Hub and running it with specific configuration options. The image provides a pre-configured WireGuard server, making it easy to deploy and manage WireGuard VPNs.
Pulling the Image
To pull the WireGuard Docker image, run the following command:
docker pull wireguard/wireguard
Running the Image
To run the WireGuard Docker image, use the following command:
docker run
-d
--name wireguard
--cap-add=NET_ADMIN wireguard/wireguard
Configuration Options
The WireGuard Docker image supports several configuration options that allow you to customize the behavior of the WireGuard server. These options include:
- WG_PRIVATE_KEY: The private key for the WireGuard server.
- WG_LISTEN_PORT: The port on which the WireGuard server listens for connections.
- WG_PEER_ADDRESSES: A comma-separated list of IP addresses for the WireGuard peers.
Network Configuration
To configure the WireGuard network within the Docker container, you’ll need to modify the configuration files generated during the container creation.
These configuration files define the network settings, including the IP addresses, ports, and encryption keys used by the WireGuard interface.
Configuration Files
The main configuration file is located at /etc/wireguard/wg0.conf . It contains the following settings:
- [Interface]: Defines the WireGuard interface name, IP address, and port.
- [Peer]: Defines the public key and IP address of each peer that can connect to the WireGuard network.
- [ListenPort]: Specifies the port on which the WireGuard interface listens for incoming connections.
Advanced Network Settings
In addition to the basic configuration, you can also configure advanced network settings, such as port forwarding and firewall rules.
Port Forwarding
Port forwarding allows you to map a port on the Docker host to a port on the WireGuard container. This can be useful for accessing services running inside the container from outside the host.
To configure port forwarding, add the following line to the docker-compose.yml file:
ports: - "80:80/tcp"
This will map port 80 on the host to port 80 on the container.
Firewall Rules
Firewall rules can be used to restrict access to the WireGuard network. You can add firewall rules to the wg0.conf file using the AllowedIPs and DeniedIPs directives.
For example, the following rule allows access to the WireGuard network from the IP address 192.168.1.100 :
[Peer] AllowedIPs = 192.168.1.100/32
Client Connectivity
To establish secure connections between client devices and the WireGuard server, specific configuration steps are required. This section provides a comprehensive guide on connecting clients, distributing configuration files, and troubleshooting potential connection issues.
Before proceeding, ensure that the WireGuard server is up and running, and the necessary ports are forwarded on the firewall.
Generating Client Configuration Files
To connect to the WireGuard network, each client device requires a unique configuration file. This file contains essential information, including the public key of the client, the IP address and port of the server, and the shared secret key. To generate client configuration files:
- Run the following command on the server:
wg genkey | tee client-private.key | wg pubkey > client-public.key- Copy the generated
client-private.keyandclient-public.keyfiles to the client device. - On the client device, create a configuration file (e.g.,
client.conf) with the following content: [Interface]PrivateKey = client-private.keyAddress = 10.0.0.2/24DNS = 8.8.8.8[Peer]PublicKey = server-public-keyAllowedIPs = 0.0.0.0/0Endpoint = server-ip:port- Replace
server-public-keywith the public key of the server. - Replace
server-ipandportwith the IP address and port of the WireGuard server.
Distributing Client Configuration Files
Once the client configuration files are generated, they need to be distributed to the client devices. This can be done manually by copying the files to each device or by using automated methods such as:
- Creating a shared network folder or cloud storage location where clients can download the files.
- Using a configuration management tool to deploy the files to the client devices.
Troubleshooting Connection Issues
If a client device is unable to connect to the WireGuard network, the following steps can help troubleshoot the issue:
- Check that the WireGuard interface is enabled on both the client and server.
- Verify that the client configuration file contains the correct public key of the server and the IP address and port of the server.
- Ensure that the firewall on the client device is not blocking the WireGuard traffic.
- Check the logs on the server and client for any error messages.
Security Considerations
WireGuard offers robust security features, but using it within Docker containers introduces additional considerations.
Potential Security Risks
-
-*Exposed Docker Interface
The Docker interface, if not properly secured, can provide an entry point for attackers to gain access to the host system.
-*Privilege Escalation
If the Docker container has elevated privileges, attackers could exploit vulnerabilities in WireGuard or the container itself to gain access to the host.
-*Network Sniffing
WireGuard traffic passing through the Docker network can be vulnerable to sniffing attacks if the network is not properly isolated.
Mitigation Recommendations
-
-*Secure Docker Interface
Use strong passwords, disable unused ports, and restrict access to the Docker interface only to authorized users.
-*Limit Container Privileges
Run WireGuard containers with the minimum necessary privileges to reduce the risk of privilege escalation.
-*Isolate Docker Network
Create a dedicated network for WireGuard traffic and configure firewall rules to prevent unauthorized access.
-*Use Strong Cryptography
WireGuard provides strong encryption by default, but ensure to use strong key exchange algorithms and cipher suites.
-*Monitor Network Traffic
Implement network monitoring tools to detect suspicious activity and identify potential threats.
Performance Optimization
To optimize WireGuard’s performance within Docker, consider resource allocation, container isolation, and configuration adjustments.
Resource Allocation
Ensure sufficient memory and CPU resources are allocated to the WireGuard container. Monitor resource usage and adjust allocations as needed.
Container Isolation
Use Docker namespaces and cgroups to isolate WireGuard from other containers and the host system, reducing resource contention.
Configuration Adjustments
- Tune MTU (Maximum Transmission Unit) for optimal packet size.
- Enable IP forwarding in the Docker host.
- Use WireGuard’s Fast Socket API (FSA) for improved performance.
Advanced Use Cases
WireGuard’s versatility extends to advanced use cases within Docker environments.
Inter-Container Communication
WireGuard facilitates secure and efficient communication between containers within a Docker network. By creating a dedicated WireGuard interface for each container, you can establish secure tunnels for direct data exchange. This eliminates the need for complex network configurations and simplifies inter-container communication.
Integration with Networking Tools and Services
WireGuard seamlessly integrates with other networking tools and services to enhance its capabilities. For instance, you can use WireGuard with network monitoring tools like Prometheus and Grafana to gain insights into network performance and troubleshoot issues. Additionally, you can integrate WireGuard with load balancers to distribute traffic across multiple containers and ensure high availability.
Troubleshooting and Maintenance
Troubleshooting WireGuard in Docker involves identifying common issues, such as connection failures, performance degradation, or security concerns. Regular updates and maintenance of the Docker image and configuration files are essential to ensure optimal functionality and security. Additionally, monitoring and logging WireGuard activity can provide valuable insights for troubleshooting and maintaining the system.
Troubleshooting Common Issues
*
-*Connection failures
Check network connectivity, firewall settings, and IP address configurations. Ensure that the WireGuard interface is active and has a valid IP address.
-
-*Performance degradation
Optimize network settings, such as MTU size, and consider using a faster VPN server or upgrading to a more powerful Docker host.
-*Security concerns
Review security configurations, such as encryption algorithms and key management, and ensure that the WireGuard interface is properly isolated from other network interfaces.
Updating and Maintaining
*
-*Docker image updates
Regularly pull the latest version of the WireGuard Docker image to benefit from bug fixes and security enhancements.
-*Configuration file updates
Monitor changes in the WireGuard configuration file, such as IP addresses or encryption keys, and update the Docker container accordingly.
Monitoring and Logging
*
-*Monitoring
Use tools like “wg” or “docker logs” to monitor WireGuard activity, such as connection status, traffic statistics, and error messages.
-*Logging
Enable logging in the WireGuard configuration file to capture detailed information about events, such as connection attempts, data transfer, and errors.
Example Configurations
Sample Docker Compose Files
Docker Compose files provide an easy way to define and manage multiple Docker containers. Here’s an example for a simple WireGuard server and client setup:“`version: “3.7”services: server: image: linuxserver/wireguard container_name: wireguard-server volumes:
/etc/wireguard
/etc/wireguard ports:
51820
51820/udp environment:
TZ=America/Los_Angeles
SERVER_PRIVATE_KEY=/etc/wireguard/privatekey
SERVER_ADDRESS=10.6.0.1
SERVER_PORT=51820
PEER_PUBLIC_KEY=/etc/wireguard/peerpublickey
client: image: linuxserver/wireguard container_name: wireguard-client volumes:
/etc/wireguard
/etc/wireguard environment:
TZ=America/Los_Angeles
CLIENT_PRIVATE_KEY=/etc/wireguard/privatekey
CLIENT_ADDRESS=10.6.0.2
SERVER_PUBLIC_KEY=/etc/wireguard/serverpublickey
SERVER_ADDRESS=10.6.0.1
SERVER_PORT=51820
“`
Sample WireGuard Configuration Files
WireGuard configuration files define the network settings and peers for each device. Here’s an example server configuration:“`[Interface]PrivateKey =
And an example client configuration:
“` [Interface] PrivateKey =
Benefits and Limitations
Using Docker Compose files and pre-defined WireGuard configurations simplifies setup and maintenance. However, it’s important to consider the limitations:
– -*Customization: While these examples provide a good starting point, they may not meet specific customization requirements. – -*Security: Ensure proper key management and firewall rules to prevent unauthorized access. – -*Performance: Consider the resources available to the host system and adjust the configurations accordingly.
Comparison with Other VPN Solutions
WireGuard stands out among Docker VPN solutions due to its exceptional performance and security. Compared to other options like OpenVPN and IPsec, WireGuard offers several advantages and disadvantages.
OpenVPN
OpenVPN is a widely adopted VPN protocol known for its versatility and support for a wide range of platforms.
- Advantages:
- Mature and stable protocol with extensive support
- High level of customization and configuration options
- Disadvantages:
- Can be more complex to set up and manage
- Lower performance compared to WireGuard
IPsec
IPsec is a suite of protocols that provides secure communication at the network layer.
- Advantages:
- Supports a wide range of encryption algorithms and authentication methods
- Can be used to secure both IPv4 and IPv6 traffic
- Disadvantages:
- Can be complex to configure and manage
- Lower performance compared to WireGuard
Choosing the Right Solution
The choice between WireGuard, OpenVPN, and IPsec depends on specific use cases and requirements:
- WireGuard: Ideal for applications requiring high performance, low latency, and ease of use.
- OpenVPN: Suitable for complex setups requiring extensive customization and support for legacy devices.
- IPsec: Best suited for environments with stringent security requirements and compatibility with a wide range of devices.
Integration with Other Services
Integrating WireGuard in Docker with other services offers numerous benefits, including secure communication between containers and external systems. One popular integration is with Kubernetes, where WireGuard can provide a secure overlay network for container communication within a cluster. This enables secure communication between pods across different nodes, even when they reside on different physical hosts.
Another valuable integration is with cloud platforms like AWS and Azure. By utilizing WireGuard’s cloud-native features, you can establish secure tunnels between on-premises infrastructure and cloud resources. This allows for secure access to cloud services and data, as well as seamless communication between containers running in different environments.
Integrating WireGuard with other services can enhance security, streamline communication, and improve overall system efficiency. However, it’s crucial to consider the potential challenges, such as managing multiple network configurations and ensuring compatibility between different systems.
Kubernetes Integration
Integrating WireGuard with Kubernetes involves deploying a WireGuard container into the cluster and configuring it as a CNI plugin. This enables the creation of secure overlay networks that connect pods across different nodes. The WireGuard container acts as a network interface, encrypting and decrypting traffic between pods.
Cloud Platform Integration
To integrate WireGuard with cloud platforms, you can use the platform’s native WireGuard support or deploy a WireGuard container on a virtual machine instance. By establishing tunnels between on-premises infrastructure and cloud resources, you can securely connect to cloud services and access data stored in the cloud.
Closing Summary
Whether you’re a seasoned network engineer or a novice venturing into the world of VPNs, this guide will provide you with the tools and insights to harness the full potential of WireGuard in Docker. By following the detailed instructions and implementing the best practices Artikeld in this guide, you’ll be well-equipped to create secure, efficient, and scalable VPN solutions that meet the demands of modern networking.