In the realm of networking, security and scalability are paramount. Enter WireGuard, a modern VPN protocol renowned for its blazing speed and robust encryption. When combined with Docker, a leading containerization platform, WireGuard empowers you to establish secure and scalable network infrastructures with unprecedented ease.
This comprehensive guide will delve into the intricacies of deploying a WireGuard Docker server, unraveling its benefits, installation process, network topology, security features, performance considerations, use cases, advanced configuration options, monitoring and troubleshooting techniques, and integration with container orchestration platforms.
Join us on this enlightening journey as we unlock the full potential of WireGuard Docker servers.
WireGuard Docker Server Overview

WireGuard is a cutting-edge VPN technology that combines high performance and modern cryptography to provide secure and reliable virtual private networks. When integrated with Docker, a popular containerization platform, WireGuard offers a compelling solution for securing and managing network connectivity within Docker environments.
Deploying WireGuard as a Docker container offers several advantages. It enables easy deployment and management of WireGuard on any Docker-compatible system, including cloud platforms, virtual machines, and physical servers. Additionally, it simplifies configuration and maintenance, as the Docker image provides a pre-configured and optimized WireGuard setup.
Benefits of Using WireGuard with Docker
- Enhanced Security: WireGuard provides robust encryption and authentication mechanisms, ensuring the confidentiality and integrity of data transmitted over the network.
- Improved Performance: WireGuard’s optimized protocol and kernel integration result in exceptional performance, enabling fast and reliable network connectivity.
- Simplified Management: The Docker containerization approach simplifies the deployment, configuration, and management of WireGuard, making it accessible to users of all skill levels.
- Portability: Docker containers can be easily moved between different systems and platforms, ensuring consistent WireGuard functionality across various environments.
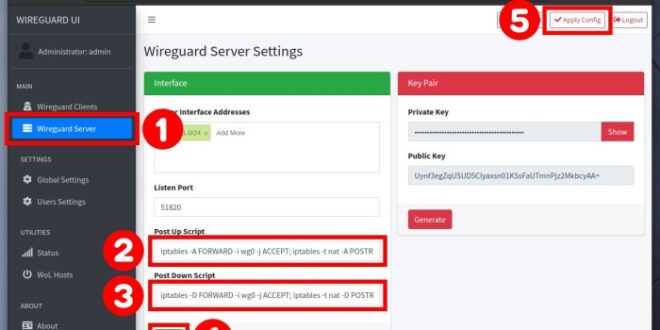
Installation and Configuration
Installing and configuring WireGuard on a Docker server is a straightforward process. This guide will provide step-by-step instructions to help you set up a secure and reliable WireGuard server using Docker.
Prerequisites
Before you begin, ensure you have the following prerequisites:
- A Docker host with Docker Engine installed and running
- A valid WireGuard configuration file
Installation
To install WireGuard on your Docker server, run the following command:“`docker run
- d
- -name wireguard-server
- -cap-add=NET_ADMIN
-p 51820
51820/udp
-v /path/to/wireguard-config.conf
/etc/wireguard/wg0.conf linuxserver/wireguard
“`Replace `/path/to/wireguard-config.conf` with the path to your WireGuard configuration file.
Configuration
After the container is running, you can configure WireGuard by editing the configuration file. You can do this by running the following command:“`docker exec
it wireguard-server nano /etc/wireguard/wg0.conf
“`Make the necessary changes to the configuration file and save the changes.
Network Topology
WireGuard Docker server connects to clients, peers, and other networks through a virtual private network (VPN) interface. The VPN interface creates a secure tunnel between the server and the remote endpoint, encrypting all traffic passing through it.
The server can be configured to connect to multiple clients, peers, and networks, allowing for flexible and secure network connectivity.
Server-Client Connection
When a client connects to the WireGuard Docker server, the server assigns the client an IP address from the VPN subnet. The client’s traffic is then encrypted and routed through the VPN tunnel to the server.
The server forwards the client’s traffic to the appropriate destination network, either on the local network or the internet.
Server-Peer Connection
WireGuard Docker server can also connect to other WireGuard peers. This allows for the creation of a mesh network, where each peer can communicate with each other securely.
Peer connections are established by exchanging public keys. Once the keys are exchanged, the peers can establish a secure VPN tunnel and exchange traffic.
Server-Other Network Connection
WireGuard Docker server can also connect to other networks, such as local networks or the internet. This allows the server to act as a gateway between the VPN network and other networks.
The server can be configured to route traffic between the VPN network and the other networks, allowing clients to access resources on both networks securely.
Security Features

WireGuard incorporates robust security features to protect connections, utilizing advanced encryption protocols, sophisticated authentication methods, and fine-grained access control.
The Docker environment further enhances security by providing isolation and resource constraints, ensuring that WireGuard containers operate securely within the host system.
Encryption Protocols
- WireGuard employs the latest and most secure encryption protocols, including ChaCha20, Curve25519, and BLAKE2s, to ensure data confidentiality and integrity.
- These protocols provide strong encryption and are resistant to known attacks, making it extremely difficult for unauthorized parties to intercept or decrypt communications.
Authentication Methods
- WireGuard utilizes modern authentication methods, such as pre-shared keys and public key cryptography, to verify the identity of peers.
- Pre-shared keys are securely generated and shared between peers, providing a simple and efficient way to establish trust.
- Public key cryptography allows peers to authenticate each other using digital certificates, ensuring that only authorized devices can connect to the VPN.
Access Control
- WireGuard offers granular access control, allowing administrators to specify which devices and users are permitted to connect to the VPN.
- Access control rules can be configured based on IP addresses, MAC addresses, or other criteria, ensuring that only authorized parties have access to the network.
Performance Considerations
Running WireGuard as a Docker container incurs minimal performance overhead compared to running it natively. The container’s isolation mechanisms, such as namespaces and cgroups, add a negligible amount of latency and resource consumption.To optimize performance for different workloads, consider the following tips:
Hardware Resources
Provision adequate CPU and memory resources to the WireGuard container. This ensures smooth operation, especially during peak traffic or encryption/decryption operations.
Network Interface
Configure the container’s network interface to match the capabilities of the host system’s network interface. This optimizes data transfer rates and minimizes latency.
Tuning Parameters
Adjust WireGuard’s configuration parameters to suit the specific workload. For example, increasing the MTU (Maximum Transmission Unit) can improve throughput for large data transfers.
Monitoring and Profiling
Use monitoring tools to track WireGuard’s performance metrics, such as CPU utilization, memory consumption, and network throughput. Profiling tools can help identify bottlenecks and optimize performance.
Optimizing for Specific Workloads
Tailor the WireGuard configuration and resource allocation to match the requirements of specific workloads. For example, latency-sensitive applications may benefit from prioritizing CPU resources, while throughput-intensive workloads may require more memory and a higher MTU.
Use Cases
WireGuard Docker server offers a versatile platform for deploying secure and scalable virtual private networks (VPNs). Its lightweight and efficient nature makes it suitable for various use cases, ranging from remote access and secure communication to network segmentation and cloud-based connectivity.
Below are some common applications where WireGuard Docker server can be leveraged:
Remote Access
- Enable secure remote access to corporate networks for employees working from home or on the move.
- Provide remote desktop access to servers and workstations, allowing administrators to manage systems remotely.
- Facilitate remote collaboration and file sharing among team members located in different geographic locations.
Secure Communication
- Establish encrypted communication channels between devices and servers, ensuring data privacy and confidentiality.
- Protect sensitive data transmissions from eavesdropping and interception over public networks.
- Secure communication between IoT devices, cloud services, and enterprise applications.
Network Segmentation
- Create isolated network segments within a larger network, improving security and reducing the risk of lateral movement in case of a breach.
- Segment different departments or business units into separate networks, enforcing access control and preventing unauthorized access.
- Isolate critical infrastructure and resources from untrusted networks, enhancing overall security posture.
Advanced Configuration
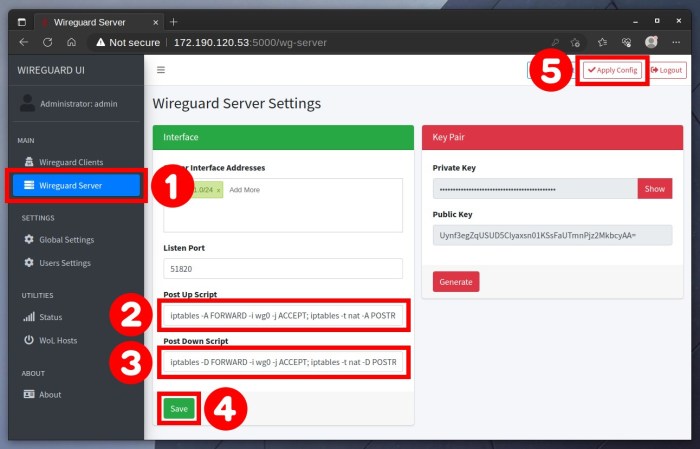
WireGuard Docker servers offer advanced configuration options for customizing and optimizing network performance and security.
Beyond the basic setup, you can configure:
Customizing Tunnels
- Define specific IP addresses for peers.
- Set custom MTU (Maximum Transmission Unit) sizes.
- Enable/disable forwarding of traffic between peers.
Setting Up Peering
- Establish connections between multiple WireGuard servers (peering).
- Configure allowed IP (Internet Protocol) ranges for peer communication.
- Implement routing policies to control traffic flow.
Integrating with Other Services
- Connect WireGuard to existing network infrastructure (e.g., firewalls, intrusion detection systems).
- Integrate with DNS (Domain Name System) services for name resolution.
- Use external authentication mechanisms (e.g., LDAP, RADIUS).
Monitoring and Troubleshooting
Effective monitoring and troubleshooting are crucial for maintaining the health and performance of WireGuard Docker servers. Here are some best practices to follow:
Use a combination of logs, metrics, and diagnostic tools to gain insights into the server’s operation. Logs provide detailed information about events and errors, while metrics offer real-time performance data. Diagnostic tools can be used to identify specific issues.
Logs
- Enable logging by setting the ‘log’ option to ‘true’ in the Docker container configuration.
- Configure log rotation to prevent logs from becoming too large and unwieldy.
- Use a log aggregation tool like Fluentd or ELK Stack to centralize and analyze logs from multiple servers.
Metrics
- Enable metrics collection by setting the ‘metrics’ option to ‘true’ in the Docker container configuration.
- Use a metrics monitoring tool like Prometheus or Grafana to visualize and analyze metrics.
- Monitor key metrics such as CPU usage, memory usage, and network traffic to identify potential issues.
Diagnostic Tools
- Use the ‘wg’ command-line tool to diagnose WireGuard-specific issues.
- Use the ‘docker inspect’ command to inspect the Docker container’s configuration and status.
- Use the ‘docker logs’ command to view the container’s logs.
Container Orchestration
Container orchestration platforms simplify the management of multiple WireGuard Docker servers by automating tasks like deployment, scaling, and monitoring.Kubernetes and Docker Swarm are popular container orchestration tools that can be used to deploy and manage WireGuard. Kubernetes provides advanced features like auto-scaling, self-healing, and load balancing, while Docker Swarm is a lightweight and easy-to-use platform.
Deploying WireGuard using Kubernetes
To deploy WireGuard using Kubernetes, you can create a YAML file that defines the deployment configuration. The file should include the WireGuard image, network configuration, and any other necessary parameters. Once the YAML file is created, you can apply it to your Kubernetes cluster using the `kubectl` command.
Kubernetes will then automatically create the WireGuard pods and configure the network.
Deploying WireGuard using Docker Swarm
To deploy WireGuard using Docker Swarm, you can create a Docker Compose file that defines the deployment configuration. The file should include the WireGuard image, network configuration, and any other necessary parameters. Once the Docker Compose file is created, you can run the `docker-compose up` command to deploy the WireGuard service.
Docker Swarm will then automatically create the WireGuard containers and configure the network.
Community and Resources
The WireGuard community is an active and supportive group of users, developers, and enthusiasts. They provide a wealth of resources to help you get started with WireGuard and troubleshoot any issues you may encounter.The official WireGuard website is a great place to start.
It contains documentation, tutorials, and a support forum where you can ask questions and get help from the community.There are also a number of other resources available online, including:
- The WireGuard subreddit
- The WireGuard Discord server
- The WireGuard mailing list
These resources can be a valuable source of information and support, especially if you are new to WireGuard.
Outcome Summary
WireGuard Docker servers offer a compelling solution for securing and scaling network infrastructures. Their ease of deployment, robust security features, and impressive performance make them an ideal choice for a wide range of applications. Whether you seek to establish secure remote access, protect sensitive communications, or segment your network for enhanced security, WireGuard Docker servers provide a powerful and versatile tool.
Embrace the future of networking with this cutting-edge technology and elevate your network infrastructure to new heights of security and scalability.