ssh.sshslowdns.com – In the realm of virtual private networks (VPNs), WireGuard stands out as a cutting-edge solution renowned for its exceptional speed, security, and ease of configuration. One of its most compelling features is split tunneling, which empowers users to selectively route specific traffic through the VPN while allowing other traffic to bypass it.
This guide will delve into the intricacies of WireGuard split tunnel configuration, providing a comprehensive understanding of its benefits, implementation methods, and best practices.
Split tunneling offers a myriad of advantages, including enhanced security, optimized performance, and flexible network management. By directing only essential traffic through the VPN, users can minimize latency and bandwidth consumption while maintaining robust protection for sensitive data. Furthermore, split tunneling enables seamless access to local network resources, such as printers and file shares, without compromising the security of the VPN connection.
WireGuard Configuration Overview

WireGuard is a modern and advanced VPN technology that provides secure, fast, and easy-to-use virtual private networks. Compared to traditional VPN protocols like OpenVPN and IPsec, WireGuard offers several advantages:
- Simplified configuration: WireGuard’s configuration is straightforward and user-friendly, with a concise and well-structured configuration file that makes it easy to set up and manage VPN connections.
- Enhanced performance: WireGuard utilizes state-of-the-art cryptography and optimized network protocols to deliver exceptional performance, resulting in faster and more reliable VPN connections.
- Improved security: WireGuard employs robust encryption algorithms and modern cryptographic techniques to ensure the confidentiality and integrity of data transmitted over the VPN connection, safeguarding user privacy and protecting against potential security breaches.
The WireGuard configuration process typically involves the following steps:
- Generate keys: Unique public and private keys are generated for each device that will participate in the VPN connection.
- Create configuration files: Configuration files containing the generated keys and network settings are created for each device.
- Establish the VPN connection: The devices exchange their configuration files and establish a secure VPN tunnel, allowing them to communicate privately and securely over the public network.
By implementing WireGuard, users can enjoy the benefits of secure, high-performance, and user-friendly VPN connections, making it an ideal solution for remote access, privacy protection, and secure network connectivity.
Split Tunneling with WireGuard
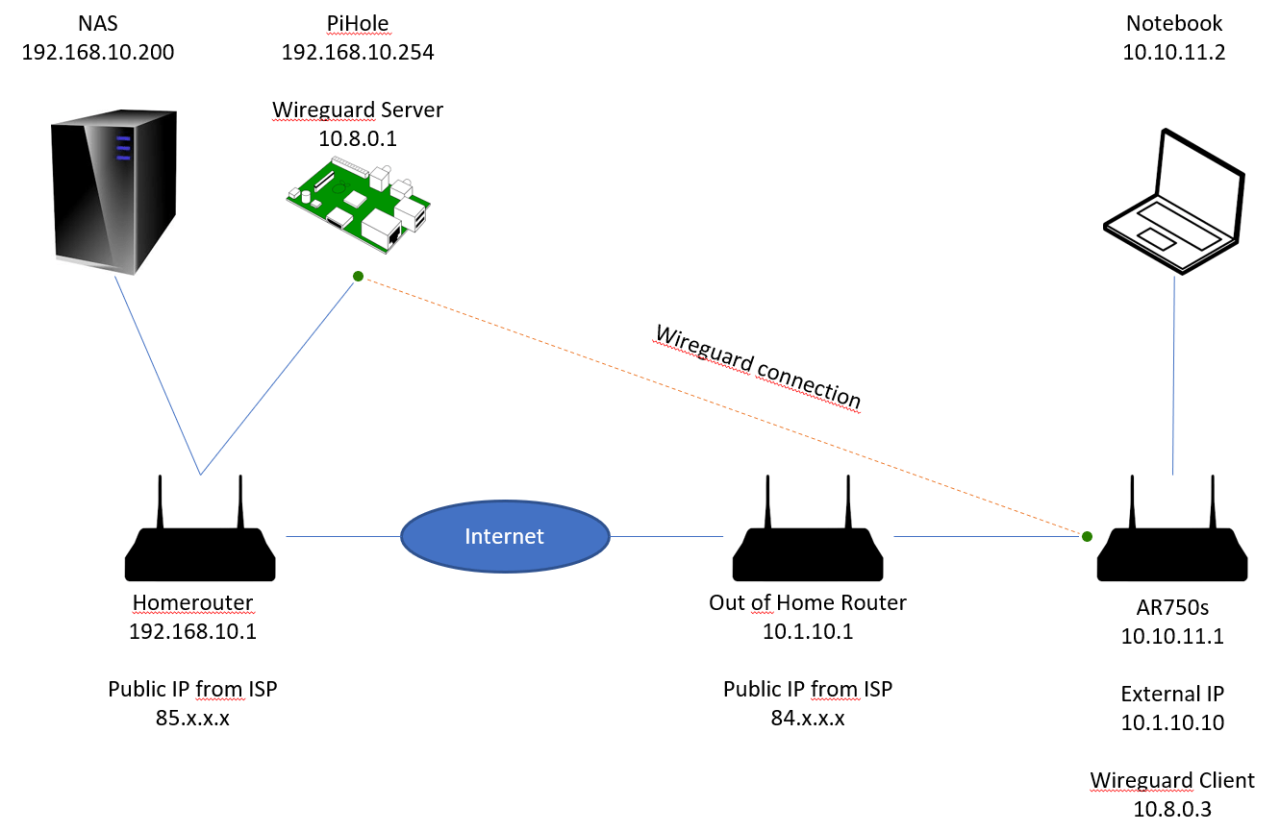
Split tunneling is a technique that allows a device to use a VPN connection for specific traffic while routing the rest of the traffic through the local network connection. This can be useful for situations where you want to protect sensitive traffic, such as work-related data, while still being able to access local resources, such as printers or shared files.
There are two main methods of implementing split tunneling with WireGuard:
Using the AllowedIPs Option
The AllowedIPs option in WireGuard’s configuration file specifies which IP addresses or subnets are allowed to be routed through the VPN tunnel. Any traffic destined for other IP addresses or subnets will be routed through the local network connection.
Using the ExcludedIPs Option
The ExcludedIPs option in WireGuard’s configuration file specifies which IP addresses or subnets are excluded from being routed through the VPN tunnel. All other traffic will be routed through the VPN tunnel.
Configuring Split Tunneling
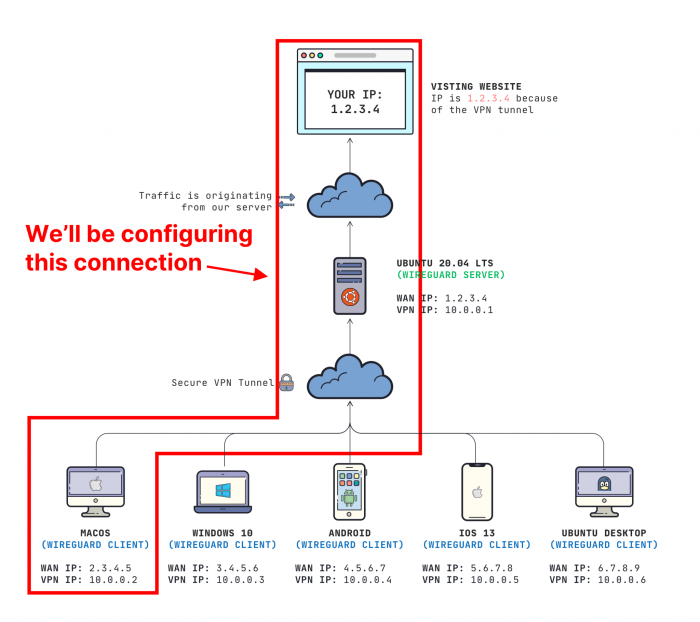
Split tunneling allows you to route specific traffic through the VPN tunnel while allowing other traffic to bypass the tunnel. This can be useful for accessing local network resources while still maintaining privacy and security for internet traffic.
Step-by-Step Instructions
To configure split tunneling with WireGuard, follow these steps:
-
- Add the following line to the client configuration file:
AllowedIPs = 0.0.0.0/0, ::/0
-
- Replace the 0.0.0.0/0 and ::/0 values with the IP ranges you want to route through the tunnel.
- Add the following line to the server configuration file:
AllowedIPs = 0.0.0.0/0, ::/0
- Replace the 0.0.0.0/0 and ::/0 values with the IP ranges you want to allow through the tunnel.
- Restart the WireGuard service on both the client and server.
Firewall Rules for Split Tunneling
Firewall rules are essential for implementing split tunneling with WireGuard. They allow you to control which traffic is routed through the VPN tunnel and which traffic bypasses the VPN.
To configure firewall rules for split tunneling, you need to create two sets of rules: one set to allow traffic through the VPN and one set to bypass the VPN.
Allowing Traffic through the VPN
The firewall rules to allow traffic through the VPN should be configured on the device that is connecting to the VPN server. These rules should allow traffic from the device’s IP address to the VPN server’s IP address on the VPN port.
- For example, if the device’s IP address is 192.168.1.10 and the VPN server’s IP address is 10.0.0.1, you would create a firewall rule that allows traffic from 192.168.1.10 to 10.0.0.1 on port 51820 (the default WireGuard port).
Bypassing the VPN
The firewall rules to bypass the VPN should be configured on the device that is connecting to the VPN server. These rules should allow traffic from the device’s IP address to any other IP address on the local network.
- For example, if the device’s IP address is 192.168.1.10, you would create a firewall rule that allows traffic from 192.168.1.10 to any IP address in the 192.168.1.0/24 subnet.
Troubleshooting Split Tunneling
Configuring split tunneling with WireGuard may encounter some common issues. This section provides solutions and troubleshooting tips to resolve these issues.
Debugging Connection Issues
- Check if the WireGuard interface is up and running:
ip link show wg0should show the interface as UP. - Verify that the firewall rules are correctly configured to allow traffic through the WireGuard interface.
- Ensure that the WireGuard configuration files on both the client and server are correct and match.
- Check if the client is able to establish a connection to the server:
wg showshould show the connection as established.
Troubleshooting Routing Issues
- Make sure that the client’s routing table is configured to send traffic through the WireGuard interface for the desired destinations.
- Verify that the server’s routing table is configured to forward traffic from the client to the desired destinations.
- Check if the client is using a default gateway that is not reachable through the WireGuard interface.
- Ensure that the WireGuard interface has a valid IP address and is not conflicting with any other interfaces.
Advanced Split Tunneling Techniques
Implementing split tunneling with multiple WireGuard interfaces offers advanced techniques for granular control over network traffic. By utilizing multiple interfaces, you can establish distinct tunnels for different subnets or applications, allowing for more flexible and customized network configurations.
For instance, you can create a dedicated tunnel for sensitive corporate traffic while routing all other internet traffic through a separate tunnel. This approach enhances security by isolating critical data from potential threats on the public internet.
Multiple WireGuard Interfaces
- Improved Security: Isolate sensitive traffic on a dedicated tunnel, minimizing exposure to potential security risks.
- Enhanced Performance: Optimize network performance by routing different traffic types through dedicated tunnels, reducing congestion and latency.
- Granular Control: Gain precise control over which subnets or applications are routed through specific tunnels, enabling tailored network configurations.
Use Cases
- Enterprise Networks: Implement split tunneling to protect sensitive corporate data while allowing employees to access the internet securely.
- Cloud-Based Applications: Route traffic to specific cloud services through a dedicated tunnel, ensuring optimal performance and security.
- IoT Devices: Establish separate tunnels for IoT devices, isolating them from other network traffic for enhanced security and reliability.
Split Tunneling Security Considerations
Split tunneling offers increased flexibility and control over network traffic, but it also introduces potential security implications. Understanding these risks and implementing appropriate mitigation strategies is crucial for maintaining a secure network environment.Split tunneling can create a scenario where certain traffic is routed through the VPN tunnel, while other traffic bypasses it.
This can create a security vulnerability if the untunneled traffic is exposed to threats on the public internet. For instance, if an attacker gains access to the device’s network, they could potentially intercept or manipulate untunneled traffic.To mitigate these risks, organizations should carefully consider the following recommendations:
Implement Strict Access Controls
Implement strong authentication mechanisms and access control policies to limit who can access the VPN and the resources it provides. This includes using multi-factor authentication, role-based access controls, and network segmentation to isolate critical systems and data.
Monitor Network Traffic
Monitor network traffic both inside and outside the VPN tunnel to detect any suspicious activity or unauthorized access attempts. Use intrusion detection systems (IDS) and intrusion prevention systems (IPS) to identify and block malicious traffic.
Use Trusted VPN Providers
Choose a reputable VPN provider with a proven track record of security and reliability. Ensure the provider uses strong encryption algorithms, follows industry best practices, and has a transparent privacy policy.
Educate Users
Educate users about the security risks associated with split tunneling and provide guidance on how to use it securely. Encourage users to be cautious when accessing untrusted websites or downloading files from the public internet.
Split Tunneling with Multiple Devices
Configuring split tunneling with WireGuard on multiple devices allows you to connect several devices to the same VPN while selectively routing specific traffic through the VPN tunnel. This provides enhanced flexibility and control over your network connections.
To set up split tunneling with WireGuard on multiple devices, you need to:
- Install WireGuard on all devices.
- Create a WireGuard configuration file on each device.
- Edit the configuration file to enable split tunneling.
- Configure firewall rules to route specific traffic through the VPN tunnel.
Configure Firewall Rules for Split Tunneling
After enabling split tunneling in the WireGuard configuration files, you need to configure firewall rules on each device to route specific traffic through the VPN tunnel. The firewall rules will determine which traffic is sent through the VPN and which traffic is sent directly over the local network.
The specific firewall rules will vary depending on your operating system and network configuration. Here are some general guidelines:
- Create a new firewall rule that allows traffic from the WireGuard interface to access the VPN subnet.
- Create a new firewall rule that blocks traffic from the local network to the VPN subnet.
- Create a new firewall rule that allows traffic from the local network to specific destinations through the VPN tunnel.
Split Tunneling with Different Operating Systems
Split tunneling configuration with WireGuard varies across different operating systems. Here are the specific configurations for Windows, macOS, and Linux:
Windows
- Create a WireGuard interface and configure the appropriate settings.
- Use the “AllowedIPs” directive to specify the IP addresses that will be routed through the VPN.
- Set the “ExcludePrivateIPs” directive to “false” to allow access to private IP addresses on the local network.
macOS
- Install WireGuard using Homebrew or MacPorts.
- Create a WireGuard interface and configure the necessary settings.
- Use the “AllowedIPs” directive to specify the IP addresses that will be routed through the VPN.
- Set the “ExcludePrivateIPs” directive to “false” to allow access to private IP addresses on the local network.
Linux
- Install WireGuard using the package manager or compile from source.
- Create a WireGuard interface and configure the required settings.
- Use the “AllowedIPs” directive to specify the IP addresses that will be routed through the VPN.
- Set the “ExcludePrivateIPs” directive to “false” to allow access to private IP addresses on the local network.
Performance Optimization for Split Tunneling
To optimize the performance of split tunneling with WireGuard, consider the following tips:
- Use a fast and reliable VPN server: The performance of split tunneling is directly affected by the speed and reliability of the VPN server. Choose a server that is located close to your physical location and has a good reputation for uptime and speed.
- Configure your firewall rules correctly: The firewall rules on your device can impact the performance of split tunneling. Make sure that the firewall rules are configured to allow traffic through the VPN tunnel for the applications that you want to use.
- Use a high-quality VPN client: The VPN client software that you use can also affect the performance of split tunneling. Choose a VPN client that is known for its performance and reliability.
- Test your performance: Once you have configured split tunneling, test its performance by running speed tests and checking the latency of your connection.
DNS Optimization
DNS optimization can also improve the performance of split tunneling. Here are some tips: