WireGuard is a state-of-the-art VPN protocol renowned for its speed, security, and user-friendliness. Among its many features, split tunneling stands out as a game-changer, enabling users to selectively route traffic through the VPN tunnel while allowing other traffic to bypass it.
In this comprehensive guide, we will delve into the intricacies of WireGuard split tunnel configuration, exploring its benefits, limitations, and advanced options. We will provide step-by-step instructions for configuring split tunneling using both the WireGuard GUI and command-line methods. Additionally, we will address common troubleshooting issues and discuss best practices for securing split tunnel configurations.
Whether you’re a seasoned network engineer or a novice user, this guide will empower you to harness the full potential of WireGuard split tunneling.
Split tunneling offers a myriad of advantages, including enhanced privacy and security for sensitive data, improved performance for local network resources, and cost savings by reducing bandwidth consumption. However, it is essential to be aware of its limitations, such as potential compatibility issues with certain applications and the need for careful configuration to avoid security vulnerabilities.
By understanding these nuances, you can make informed decisions about whether split tunneling is the right solution for your specific needs.
WireGuard Split Tunnel Configuration
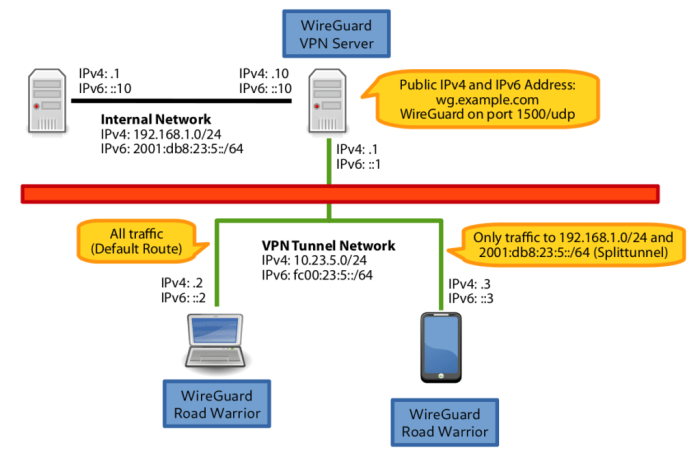
Split tunneling is a networking technique that allows you to route specific traffic through a VPN while allowing other traffic to go through your regular internet connection. This can be useful for situations where you want to protect sensitive traffic, such as banking or work-related data, while still being able to access local resources or browse the internet without the overhead of the VPN.
To configure split tunneling in WireGuard, you will need to add a few lines to your WireGuard configuration file. First, you will need to specify the IP addresses or subnets that you want to exclude from the VPN. You can do this by adding the following line to your configuration file:
- AllowedIPs = 192.168.0.0/24
This line will exclude all traffic from the 192.168.0.0/24 subnet from the VPN. You can add multiple AllowedIPs lines to exclude multiple subnets.
Once you have added the AllowedIPs lines to your configuration file, you will need to restart WireGuard for the changes to take effect. You can do this by running the following command:
- sudo systemctl restart wg-quick@tun_name
Once WireGuard has restarted, traffic from the excluded subnets will no longer be routed through the VPN.
Benefits of Split Tunneling
- Improved performance: By excluding certain traffic from the VPN, you can improve the overall performance of your internet connection. This is because the VPN will not have to encrypt and decrypt the excluded traffic, which can save bandwidth and reduce latency.
- Increased security: Split tunneling can help to increase the security of your network by protecting sensitive traffic from being intercepted by third parties. This is because the excluded traffic will not be routed through the VPN, which means that it will not be subject to the same security risks.
- Flexibility: Split tunneling gives you the flexibility to choose which traffic you want to route through the VPN and which traffic you want to send over your regular internet connection. This can be useful for situations where you need to access both local resources and the internet at the same time.
Limitations of Split Tunneling
- Complexity: Split tunneling can be more complex to configure than a regular VPN connection. This is because you need to specify which traffic you want to exclude from the VPN, which can be a challenge if you have a complex network.
- Security risks: If you are not careful when configuring split tunneling, you could create security risks. For example, if you exclude too much traffic from the VPN, you could expose your network to attack. It is important to carefully consider which traffic you want to exclude from the VPN before making any changes to your configuration.
Configuration Methods
Configuring WireGuard split tunneling can be achieved through two primary methods: the WireGuard GUI and the command line.
Using the WireGuard GUI
To set up split tunneling using the WireGuard GUI, follow these steps:
- Open the WireGuard GUI.
- Select the interface you want to use for split tunneling.
- Click on the “Edit” button.
- In the “Advanced” tab, enable the “Split Tunneling” option.
- Enter the IP addresses or subnets that you want to exclude from the tunnel.
- Click on the “Save” button.
Using the Command Line
To configure split tunneling using the command line, use the following syntax:
wg set allowed-ips /
For example, to exclude the 192.168.1.0/24 subnet from the tunnel, you would use the following command:
wg set wg0 allowed-ips 192.168.1.0/24
Advanced Options
WireGuard offers advanced options for fine-tuning the split tunnel configuration.
One of the key features is the ability to use rules to specify which traffic should be routed through the tunnel. These rules are based on IP addresses, ports, and protocols, allowing for granular control over the traffic flow.
Exclude Specific Destinations
Additionally, it is possible to exclude specific destinations from the tunnel. This can be useful for accessing local resources or specific websites without going through the VPN connection.
Troubleshooting
Troubleshooting split tunnel configuration involves identifying common issues and implementing appropriate solutions or workarounds. By addressing these challenges effectively, you can ensure a seamless and secure split tunnel setup.
Here are some common issues and their solutions:
Connection Problems
- Problem: Unable to establish a VPN connection.
- Solution: Verify that the WireGuard interface is active and that the correct network settings are configured. Check firewall rules to ensure that WireGuard traffic is allowed.
Split Tunneling Not Working
- Problem: Traffic is not being routed as expected through the VPN tunnel.
- Solution: Ensure that the split tunnel configuration is correctly set up, including the appropriate AllowedIPs and excluded destinations. Verify that the WireGuard interface is assigned a higher metric than the default gateway.
DNS Resolution Issues
- Problem: DNS queries are not being resolved properly through the VPN tunnel.
- Solution: Configure the WireGuard interface to use the VPN DNS server or set up a custom DNS configuration on the client devices.
Performance Problems
- Problem: Slow or unstable VPN performance.
- Solution: Optimize the WireGuard configuration by adjusting parameters such as MTU, cipher, and key exchange algorithm. Consider upgrading to a faster VPN server or improving network connectivity.
Security Concerns
- Problem: Concerns about potential security vulnerabilities.
- Solution: Implement strong encryption protocols, such as AES-256 or ChaCha20, and regularly update the WireGuard software to patch any security issues. Use a reputable VPN provider and adhere to best security practices.
Security Considerations
Split tunneling introduces security implications that must be carefully considered. Understanding these implications and implementing best practices are crucial for maintaining a secure network configuration.
Split tunneling allows specific traffic to bypass the VPN tunnel, potentially exposing sensitive data to untrusted networks. Therefore, it’s essential to analyze the security risks associated with each application or service that is exempted from the VPN.
Best Practices for Securing Split Tunnel Configurations
- Limit exempted traffic: Restrict split tunneling to only essential applications or services that require direct access to local resources.
- Use strong encryption: Ensure that the VPN connection is protected with robust encryption algorithms, such as AES-256 or ChaCha20, to prevent eavesdropping.
- Monitor VPN logs: Regularly review VPN logs to detect any suspicious activity or unauthorized access attempts.
- Implement network segmentation: Divide the network into separate segments to isolate sensitive data and applications from untrusted traffic.
- Use a reputable VPN provider: Choose a VPN provider with a proven track record of security and privacy protection.
Performance Impact
Evaluating the impact of split tunneling on network performance is crucial for optimizing connectivity and user experience. Factors such as the number of tunnels, encryption algorithms, and network latency can influence performance.
To minimize performance impact, consider the following optimization tips:
Encryption Algorithm Selection
- Choose encryption algorithms that balance security and performance. AES-256 offers strong security but may be more computationally intensive than other options like ChaCha20.
- Use hardware acceleration if available to offload encryption and decryption tasks from the CPU, improving performance.
Network Optimization
- Configure multiple tunnels for load balancing and redundancy, ensuring optimal performance even under heavy traffic.
- Monitor network latency and adjust tunnel configurations accordingly to minimize delays.
- Prioritize traffic on the VPN tunnel to ensure critical applications receive the necessary bandwidth.
Use Cases
Split tunneling offers significant advantages in various scenarios, enabling businesses and individuals to enhance their network security and flexibility.
For businesses, split tunneling allows them to:
Remote Access with Enhanced Security
- Provide secure remote access to internal resources for employees working from home or on the go.
- Restrict access to sensitive data and applications only through the VPN tunnel, while allowing general internet traffic to bypass the VPN.
Compliance and Regulatory Adherence
- Meet compliance requirements that mandate the separation of business and personal traffic.
- Control access to specific websites or services based on corporate policies or industry regulations.
Improved Network Performance
- Reduce network congestion by directing only necessary traffic through the VPN, improving overall performance.
- Optimize internet speeds for non-business-related activities, such as streaming or gaming.
For individuals, split tunneling provides:
Privacy and Security
- Protect personal data and online activities by encrypting sensitive traffic through the VPN tunnel.
- Bypass geo-restrictions and access websites or services that are blocked in certain regions.
Cost Savings
- Reduce VPN subscription costs by limiting VPN usage to essential tasks, saving on bandwidth and data consumption.
- Avoid additional charges for accessing premium content or services that are not covered by the VPN provider.
Convenience and Flexibility
- Seamlessly switch between VPN and non-VPN connections without disrupting internet access.
- Customize split tunneling rules to meet specific needs and preferences, such as excluding specific websites or applications from the VPN.
Comparison with Other VPN Protocols
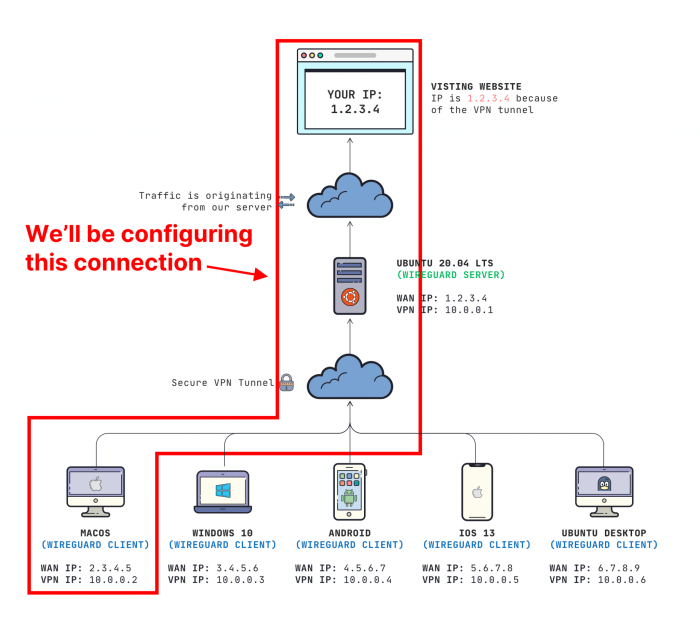
WireGuard’s split tunneling capabilities compare favorably to other popular VPN protocols, such as OpenVPN and IPSec. Each protocol offers unique advantages and disadvantages:
OpenVPN
- Mature and widely used protocol with a large community.
- Supports a wide range of encryption algorithms and authentication methods.
- Complex to configure and may require additional software.
IPSec
- Industry-standard protocol widely used in corporate environments.
- Provides strong security and supports a variety of encryption algorithms.
- Can be complex to configure and manage.
Future Developments

Split tunneling in WireGuard is an evolving feature with the potential for significant enhancements and improvements in the future.
Emerging trends and technologies, such as the increasing adoption of cloud-based applications and the growing popularity of IoT devices, are expected to drive the demand for more flexible and granular control over network traffic.
Potential Enhancements
- Improved User Interface: Simplifying the configuration and management of split tunneling rules through a user-friendly interface.
- Fine-Grained Control: Providing users with the ability to define more granular rules, such as specifying specific IP addresses or ports to be excluded from the VPN tunnel.
- Automatic Rule Generation: Developing algorithms that can automatically generate split tunneling rules based on user preferences and network usage patterns.
Emerging Trends
- Integration with Cloud Services: Enhancing split tunneling capabilities by integrating with cloud-based services, such as Azure and AWS, to enable seamless access to cloud resources.
- IoT Device Support: Optimizing split tunneling for IoT devices with limited resources, ensuring secure and efficient network connectivity.
- Network Virtualization: Leveraging network virtualization technologies to create multiple virtual networks and apply split tunneling rules to specific virtual networks.
Create a Comprehensive Guide
To make the most of WireGuard’s split tunneling capabilities, it’s essential to have a comprehensive guide that covers all the important aspects. This guide will provide you with a step-by-step approach to configuring split tunneling, troubleshooting tips, and best practices to ensure a secure and efficient setup.
The guide will be structured into clear sections, each covering a specific aspect of split tunneling configuration. We’ll start with an overview of split tunneling and its benefits, then dive into the configuration methods for different operating systems and devices.
We’ll also explore advanced options for customizing your split tunneling setup and provide troubleshooting tips to help you resolve any issues that may arise.
Configuration Methods
Configuring split tunneling with WireGuard can vary depending on your operating system and device. We’ll provide detailed instructions for the most popular platforms, including Windows, macOS, Linux, iOS, and Android. Each set of instructions will include clear steps, code snippets, and screenshots to guide you through the process.
Advanced Options
Once you have a basic split tunneling setup, you can explore advanced options to customize your configuration. We’ll cover topics such as creating custom rules for specific applications, using different network interfaces for split tunneling, and optimizing performance for your specific needs.
Troubleshooting Tips
Troubleshooting split tunneling issues can be challenging, but our guide will provide you with a comprehensive set of tips and tricks to help you resolve common problems. We’ll cover issues such as connectivity problems, DNS leaks, and performance issues, and provide solutions to help you get your split tunneling setup working smoothly.
Last Word
In conclusion, WireGuard split tunnel configuration is a powerful tool that can significantly enhance the security and efficiency of your network. By carefully considering the benefits and limitations, selecting the appropriate configuration method, and implementing advanced options to fine-tune your setup, you can harness the full potential of WireGuard split tunneling.
Remember to prioritize security by implementing strong encryption and access control measures, and regularly monitor your configuration for any suspicious activity. As WireGuard continues to evolve, we can expect further enhancements and improvements to split tunneling capabilities, making it an even more indispensable tool for network administrators and users alike.