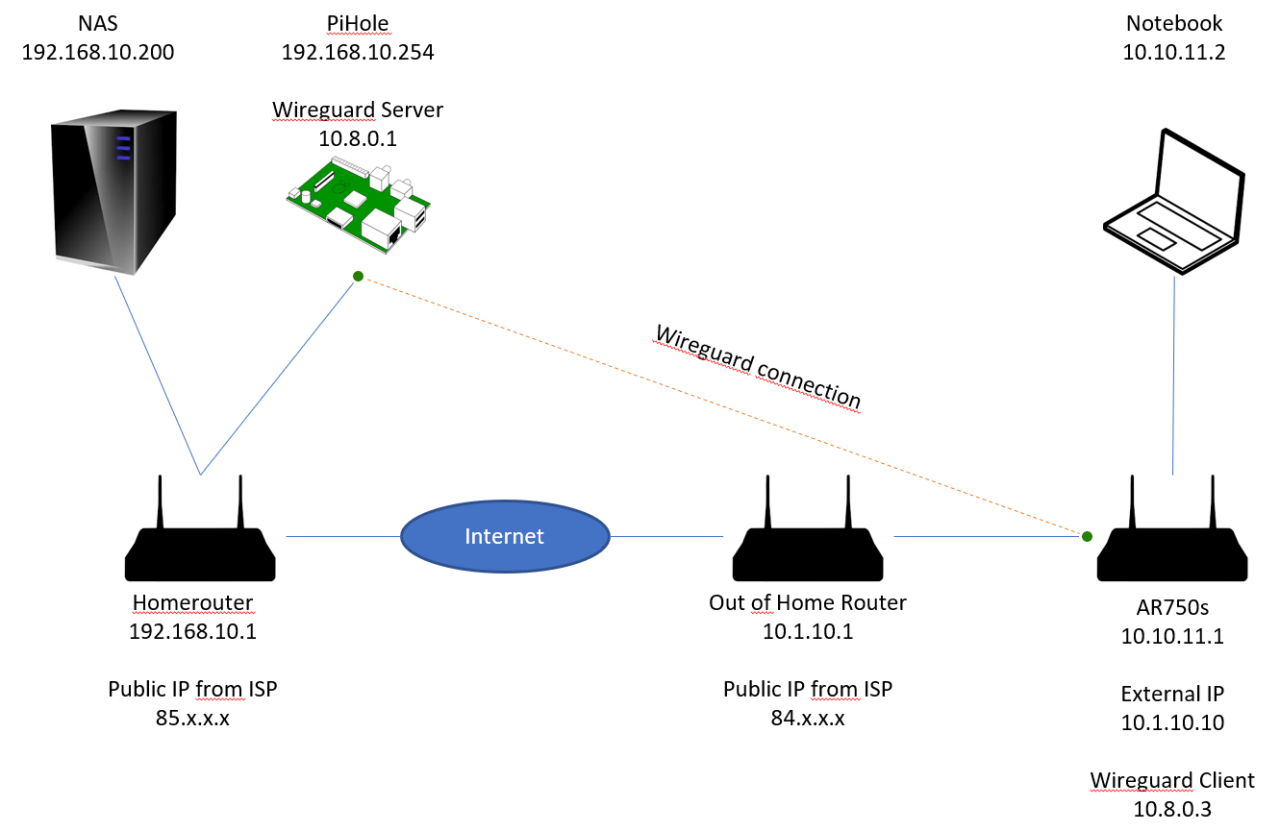
ssh.sshslowdns.com – In the ever-evolving world of cybersecurity, the need for secure and flexible network access has become paramount. WireGuard, a cutting-edge VPN protocol, has emerged as a game-changer in this arena, offering robust encryption and lightning-fast speeds. One of its most powerful features is client split tunneling, which allows users to selectively route traffic through the VPN tunnel while excluding specific applications or destinations.
In this comprehensive guide, we will delve into the intricacies of WireGuard client split tunneling, exploring its benefits, use cases, and step-by-step configuration instructions. We will also discuss advanced configuration options, troubleshooting techniques, and best practices to ensure optimal performance and security.
WireGuard Client Split Tunneling Overview
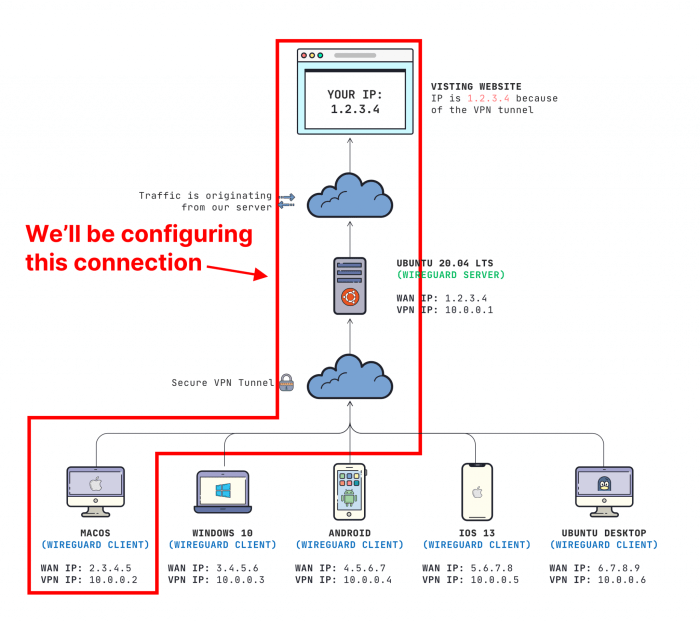
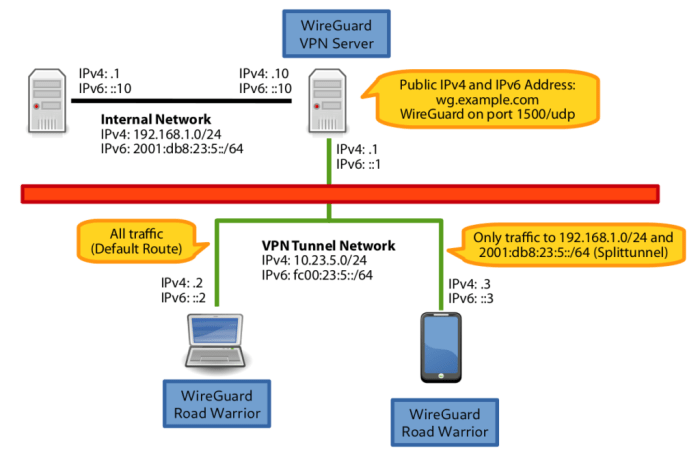
WireGuard client split tunneling is a technique that allows a WireGuard client to selectively route only specific traffic through the VPN tunnel, while other traffic is routed directly over the local network connection. This can be useful for performance reasons, to improve privacy, or to bypass certain network restrictions.
One of the main benefits of split tunneling is that it can improve performance by reducing the amount of traffic that is encrypted and routed through the VPN tunnel. This can be especially beneficial for applications that are sensitive to latency, such as gaming or video streaming.
Split tunneling can also be used to improve privacy by preventing certain traffic from being routed through the VPN tunnel. For example, you could configure your WireGuard client to only route traffic from your web browser through the VPN tunnel, while all other traffic is routed directly over your local network connection.
This would prevent your ISP from seeing what websites you are visiting.
Configuring WireGuard Client Split Tunneling
Configure WireGuard client split tunneling to route specific traffic through the VPN tunnel while excluding other traffic.
Windows
Edit the WireGuard configuration file (.conf) and add the following lines:
“`[Interface]Table = 255“`
macOS
Edit the WireGuard configuration file (.conf) and add the following lines:
“`[Interface]Table = off“`
Linux
Edit the WireGuard configuration file (.conf) and add the following lines:
“`[Interface]Table = off“`
Add the following firewall rules:
“`iptables
- t mangle
- I OUTPUT
- m owner
- -uid-owner
- j MARK
- -set-mark 255
iptables
- t mangle
- I OUTPUT !
- d
- j MARK
- -set-mark 1
iptables
- t mangle
- I OUTPUT
- j ACCEPT
“`
Replace with the user ID of the WireGuard client and with the IP address of the VPN server.
Routing Traffic Through the Tunnel
To selectively route specific traffic through the WireGuard tunnel while excluding others, you can utilize a combination of routing tables and firewall rules.
Routing Tables
Routing tables are used to determine the path that network traffic takes. By modifying the routing table, you can specify which traffic should be directed through the WireGuard tunnel.
- Add a route: To route traffic through the tunnel, add a route to the routing table that specifies the destination IP address or network and the gateway (WireGuard interface).
- Set metric: Assign a metric to the route to prioritize it over other routes. A lower metric indicates a higher priority.
Firewall Rules
Firewall rules can be used to control which traffic is allowed to pass through the WireGuard interface. By configuring specific rules, you can block or allow traffic based on source, destination, or port.
- Allow traffic: Create a firewall rule that allows traffic from the specified source IP address or network to pass through the WireGuard interface.
- Block traffic: Create a firewall rule that blocks traffic from specific source or destination IP addresses or networks from accessing the WireGuard interface.
Bypassing the Tunnel for Specific Applications
In some cases, you may want to exclude certain applications from the WireGuard tunnel. This allows them to bypass the VPN connection and access the internet directly.There are two main methods for achieving this:
Troubleshooting WireGuard Client Split Tunneling
Identifying and resolving issues with WireGuard client split tunneling is crucial for maintaining a stable and secure network connection. Common problems may arise due to connectivity issues, routing configurations, or application compatibility.
Troubleshooting these issues involves examining the WireGuard configuration, network settings, and application behavior to pinpoint the source of the problem. By understanding potential issues and their solutions, you can effectively troubleshoot and resolve any split tunneling challenges.
Connectivity Issues
- Check WireGuard Interface Status: Ensure that the WireGuard interface is active and has a valid IP address assigned. Use the command
ip addr showto verify the interface status. - Verify Firewall Rules: Confirm that the firewall is allowing traffic through the WireGuard interface. Check the firewall rules and ensure that the necessary ports and protocols are open.
- Test Network Connectivity: Perform a network connectivity test using a tool like
pingortracerouteto verify if packets are reaching their destination.
Routing Issues
- Examine Routing Table: Check the routing table (
route) to ensure that traffic is being routed through the WireGuard interface as intended.
-n - Disable Default Gateway: If the default gateway is set to the WireGuard interface, it may interfere with split tunneling. Try disabling the default gateway on the WireGuard interface.
- Use Policy-Based Routing: Implement policy-based routing to selectively route specific traffic through the WireGuard tunnel.
Application Compatibility Issues
- Check Application Network Settings: Verify that the application is configured to use the correct network interface. Some applications may have their own network settings that need to be adjusted.
- Bypass Tunnel for Specific Applications: Exclude certain applications from using the WireGuard tunnel by configuring the
AllowedIPsorExcludedIPssettings. - Use Split Tunneling-Compatible Applications: Ensure that the applications you are using are compatible with split tunneling. Some applications may not support split tunneling and may need to be excluded.
Security Considerations
WireGuard client split tunneling introduces some security considerations that must be taken into account.Split tunneling allows certain traffic to bypass the VPN tunnel, potentially exposing it to external threats. This can be mitigated by carefully defining the rules for which traffic is allowed to bypass the tunnel, ensuring that only trusted applications and destinations are permitted.
Mitigating Potential Security Risks
To mitigate potential security risks associated with WireGuard client split tunneling, consider the following measures:
- Define clear and restrictive bypass rules: Specify precisely which applications or destinations are allowed to bypass the VPN tunnel. Avoid using broad or ambiguous rules that could allow unauthorized traffic to bypass the tunnel.
- Use strong encryption: Ensure that the VPN tunnel uses strong encryption algorithms, such as AES-256 or ChaCha20, to protect data transmitted through the tunnel.
- Monitor VPN activity: Regularly monitor VPN activity to detect any suspicious behavior or unauthorized access attempts. Use tools like firewalls and intrusion detection systems to identify and block malicious activity.
- Educate users: Inform users about the potential security implications of using split tunneling and provide guidance on how to use it securely.
Advanced Configuration Options
WireGuard client split tunneling offers advanced configuration options to enhance its functionality and tailor it to specific network requirements. These options include the ability to establish multiple tunnels, implement load balancing, and configure traffic shaping rules.
Multiple Tunnels
Setting up multiple WireGuard tunnels allows for increased redundancy and flexibility. By creating multiple tunnels with different endpoints, you can distribute traffic across multiple paths, reducing the impact of outages or performance issues on a single tunnel.
Load Balancing
Load balancing in WireGuard client split tunneling distributes network traffic across multiple tunnels based on predefined criteria. This helps optimize network performance by utilizing available bandwidth more efficiently. Load balancing algorithms can be configured to consider factors such as latency, bandwidth, and tunnel availability.
Traffic Shaping
Traffic shaping allows you to prioritize or limit the bandwidth allocated to specific types of traffic. By configuring traffic shaping rules, you can ensure that critical applications receive adequate bandwidth while limiting non-essential traffic to prevent network congestion. Traffic shaping can be implemented using advanced features like QoS (Quality of Service) or traffic shaping tools.
Performance Considerations
WireGuard client split tunneling can impact network performance, depending on several factors. One key factor is the computational overhead associated with encrypting and decrypting traffic. WireGuard uses modern cryptography algorithms that are highly efficient, but they still require some processing power.
This overhead can be noticeable on low-powered devices or when handling large amounts of traffic.Another factor that can affect performance is the network latency between the client and the VPN server. Higher latency can lead to slower transfer speeds and increased response times.
To mitigate this, it’s recommended to choose a VPN server that is geographically close to the client.
Optimization Tips
To optimize performance, consider the following tips:
- Use a high-speed internet connection.
- Choose a VPN server with low latency.
- Limit the number of applications that route traffic through the tunnel.
- Avoid encrypting large files or streaming high-bandwidth content over the VPN connection.
Alternative Split Tunneling Solutions
Split tunneling is a networking technique that allows users to route specific traffic through a VPN tunnel while allowing other traffic to bypass the tunnel. WireGuard is one of several solutions that can be used to implement split tunneling.
Other Split Tunneling Solutions
Besides WireGuard, other popular split tunneling solutions include:
- OpenVPN
- IPsec
- pfSense
OpenVPN
OpenVPN is an open-source VPN protocol that supports split tunneling. It is widely used and has a large community of users and developers. OpenVPN is known for its security and flexibility, but it can be more complex to configure than WireGuard.
IPsec
IPsec is a suite of protocols that can be used to implement VPNs. IPsec supports split tunneling and is widely used in enterprise environments. IPsec is more complex to configure than WireGuard, but it offers a high level of security.
pfSense
pfSense is a free and open-source firewall and router distribution that supports split tunneling. pfSense is easy to configure and manage, making it a good choice for small businesses and home users.
Advantages and Disadvantages of Different Split Tunneling Solutions
The choice of split tunneling solution depends on the specific requirements of the user. Here is a table summarizing the advantages and disadvantages of each solution:| Solution | Advantages | Disadvantages ||—|—|—|| WireGuard | Simple to configure, fast, and secure | Limited support for split tunneling || OpenVPN | Secure and flexible, large community support | Complex to configure || IPsec | High level of security, widely used in enterprise environments | Complex to configure || pfSense | Easy to configure and manage | Limited features compared to other solutions |
Best Practices for WireGuard Client Split Tunneling
Implementing WireGuard client split tunneling effectively requires careful consideration of security, performance, and user experience. Here are some best practices to guide you: