In the realm of cybersecurity, the concept of split tunneling has emerged as a game-changer. This technique allows users to route specific network traffic through a virtual private network (VPN) while simultaneously allowing other traffic to flow directly over the public internet.
By leveraging the powerful capabilities of WireGuard, a cutting-edge VPN protocol, organizations can implement split tunneling with unprecedented ease and efficiency. This comprehensive guide will delve into the intricacies of WireGuard application split tunneling, exploring its advantages, limitations, and practical applications.
Split tunneling with WireGuard offers a unique solution for organizations seeking to enhance their network security without compromising performance. By selectively routing sensitive traffic through the encrypted VPN tunnel while allowing non-critical traffic to bypass the VPN, organizations can maintain both data protection and network efficiency.
Furthermore, WireGuard’s advanced encryption algorithms and streamlined protocol design ensure lightning-fast VPN connections, making it an ideal choice for bandwidth-intensive applications.
WireGuard Application Split Tunneling Overview
Split tunneling is a networking technique that allows specific network traffic to bypass a virtual private network (VPN) while other traffic is routed through the VPN. This can be useful for accessing local network resources while still maintaining the security and privacy benefits of a VPN.
WireGuard is a modern VPN protocol that supports split tunneling. With WireGuard, you can configure which traffic is sent through the VPN and which traffic is excluded. This gives you more control over your network traffic and can help improve performance.
Use Cases for Split Tunneling
There are several use cases where split tunneling can be beneficial. For example, you might want to use split tunneling to:
- Access local network resources while connected to a VPN
- Improve performance by excluding certain types of traffic from the VPN
- Bypass geo-restrictions on certain websites or services
Advantages of Split Tunneling with WireGuard
There are several advantages to using split tunneling with WireGuard, including:
- Increased flexibility: Split tunneling gives you more control over your network traffic.
- Improved performance: Excluding certain types of traffic from the VPN can improve performance.
- Enhanced security: Split tunneling can help improve security by isolating certain types of traffic from the VPN.
Limitations of Split Tunneling with WireGuard
There are also some limitations to using split tunneling with WireGuard, including:
- Increased complexity: Split tunneling can be more complex to configure than a traditional VPN connection.
- Potential security risks: Split tunneling can introduce security risks if it is not configured properly.
Configuring WireGuard Split Tunneling
Configuring WireGuard for split tunneling involves modifying the configuration files to specify which traffic should be routed through the VPN tunnel and which should remain on the local network.
The following steps Artikel the general process for configuring WireGuard split tunneling:
Adding the Split Tunnel Configuration
In the WireGuard configuration file, add the following line under the [Interface] section:
AllowedIPs = 192.168.0.0/24
This line specifies that traffic destined for the 192.168.0.0/24 subnet will be routed through the VPN tunnel, while all other traffic will remain on the local network.
Modifying the Routing Table
After modifying the WireGuard configuration file, you need to update the routing table to reflect the new settings. This can be done using the following commands:
- Linux:
sudo ip route add 192.168.0.0/24 via $WG_INTERFACE - macOS:
sudo route add
-net 192.168.0.0/24
-interface $WG_INTERFACE - Windows:
netsh interface ipv4 add route 192.168.0.0/24 $WG_INTERFACE
Replace $WG_INTERFACE with the name of the WireGuard interface.
Potential Challenges and Troubleshooting
- Traffic not routing through the VPN tunnel: Verify that the AllowedIPs setting in the WireGuard configuration file matches the subnet you want to route through the VPN. Also, check the routing table to ensure that the correct route has been added.
- DNS leaks: Ensure that your DNS settings are configured correctly to prevent DNS requests from leaking outside the VPN tunnel.
Using WireGuard Split Tunneling with Different Applications
WireGuard split tunneling allows you to selectively route traffic from specific applications through the VPN tunnel, while other traffic remains on the local network. This can be useful for improving performance, security, or privacy.
To configure WireGuard split tunneling for specific applications, you need to add the following lines to your WireGuard configuration file:
“`[Interface]Address = 10.0.0.1/24DNS = 8.8.8.8AllowedIPs = 0.0.0.0/0# Add the IP addresses of the applications you want to route through the VPN tunnelAllowedIPs = 192.168.1.100/32“`
You can replace 192.168.1.100/32 with the IP addresses of the applications you want to route through the VPN tunnel.
Once you have added the necessary lines to your WireGuard configuration file, you can save the file and restart the WireGuard service. Traffic from the specified applications will now be routed through the VPN tunnel.
Examples of Applications that Can Benefit from Split Tunneling
- BitTorrent clients: Split tunneling can improve the performance of BitTorrent clients by routing torrent traffic through the VPN tunnel, while other traffic remains on the local network. This can help to reduce latency and improve download speeds.
- Gaming: Split tunneling can improve the performance of online games by routing gaming traffic through the VPN tunnel, while other traffic remains on the local network. This can help to reduce latency and improve ping times.
- Streaming services: Split tunneling can improve the performance of streaming services by routing streaming traffic through the VPN tunnel, while other traffic remains on the local network. This can help to reduce buffering and improve video quality.
Security Implications of Using Split Tunneling with Different Applications
Split tunneling can have some security implications. For example, if you route traffic from a sensitive application through the VPN tunnel, and the VPN connection is compromised, the attacker could access your sensitive data. Therefore, it is important to only route traffic from trusted applications through the VPN tunnel.
You should also be aware that split tunneling can bypass your firewall. If you have a firewall configured to block certain types of traffic, split tunneling can allow that traffic to bypass the firewall. Therefore, it is important to carefully consider the security implications of using split tunneling before enabling it.
Performance Considerations
Split tunneling with WireGuard can impact performance, but the extent depends on several factors.
Factors Affecting Performance
- Device capabilities: High-performance devices handle split tunneling better.
- Network conditions: Latency and bandwidth affect performance.
- Number of split tunnels: Multiple tunnels can increase overhead.
Optimization Tips
- Use a high-performance device.
- Ensure a stable and fast network connection.
- Limit the number of split tunnels created.
- Configure WireGuard efficiently (e.g., using modern encryption algorithms).
Comparison to Other VPN Solutions
WireGuard split tunneling generally offers better performance than other VPN solutions due to its efficient implementation and low overhead. However, performance may vary depending on the specific VPN solution used and the device configuration.
Security Implications
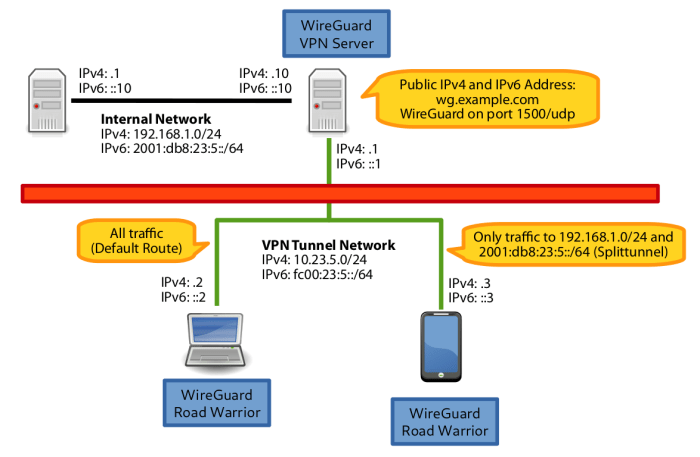
WireGuard split tunneling, like any network configuration, introduces potential security risks. However, by understanding these risks and implementing appropriate mitigation strategies, organizations can effectively secure their networks while enjoying the benefits of split tunneling.One potential risk is the exposure of sensitive data to untrusted networks.
When traffic from specific applications is excluded from the VPN tunnel, it may traverse untrusted networks, increasing the risk of interception or manipulation. To mitigate this risk, organizations should carefully consider which applications and traffic types should be excluded from the VPN tunnel and implement additional security measures, such as firewalls and intrusion detection systems, to protect these excluded resources.Another
potential risk is the introduction of a single point of failure. If the VPN connection fails, all traffic from excluded applications will be exposed to untrusted networks. To mitigate this risk, organizations should implement redundant VPN connections or consider using alternative network connectivity options, such as SD-WAN or MPLS, to ensure that critical applications remain accessible even in the event of a VPN failure.Overall,
the security of WireGuard split tunneling is comparable to that of traditional VPNs. However, organizations should carefully consider the specific risks associated with their network configuration and implement appropriate mitigation strategies to ensure a secure and effective network environment.
Troubleshooting WireGuard Split Tunneling
Resolving issues with WireGuard split tunneling requires a systematic approach to identify and address the root cause. Here are some common troubleshooting tips to assist you:
Error Messages
- “Failed to create tunnel: Permission denied”: Indicates that the user does not have sufficient privileges to create a tunnel. Ensure that the user has root or sudo privileges.
- “Failed to start tunnel: Interface not found”: The specified interface may not exist or may not be properly configured. Verify that the interface name is correct and that it is active.
- “Failed to add route: Destination unreachable”: The specified destination may not be reachable through the VPN tunnel. Check the network configuration and ensure that the destination is accessible.
Resources and Documentation
- WireGuard Documentation: https://www.wireguard.com/docs/
- WireGuard Forum: https://forum.wireguard.com/
- Linux Kernel Documentation: https://www.kernel.org/doc/html/latest/networking/index.html
Alternatives to WireGuard Split Tunneling
WireGuard split tunneling offers a flexible and efficient approach to network traffic management. However, alternative solutions exist that may suit specific use cases and requirements.
Proxy Servers
Proxy servers act as intermediaries between clients and remote servers, redirecting traffic based on defined rules. They provide split tunneling capabilities by selectively routing traffic through the proxy server or the regular network connection.Advantages:
- Supports a wide range of applications and protocols.
- Easy to set up and configure.
- Can provide additional security features, such as authentication and encryption.
Disadvantages:
- Can introduce performance overhead due to the additional hop in the traffic path.
- May require manual configuration for each application.
Virtual Private Networks (VPNs)
VPNs create encrypted tunnels between devices and remote networks, allowing secure access to resources. They can be configured to provide split tunneling by excluding specific traffic from the VPN connection.Advantages:
- Provides comprehensive network security and privacy.
- Supports a wide range of protocols and applications.
- Easy to set up and manage.
Disadvantages:
- Can be more complex to configure than split tunneling solutions.
- May require additional hardware or software.
Network Address Translation (NAT)
NAT allows multiple devices to share a single public IP address. It can be used to implement split tunneling by translating traffic destined for specific applications to a different IP address.Advantages:
- Simple and cost-effective solution.
- Requires minimal configuration.
Disadvantages:
- Limited to IPv4 networks.
- Can be less secure than other alternatives.
Recommendation
The best alternative to WireGuard split tunneling depends on the specific use case and requirements. For applications that require high performance and granular control, WireGuard remains a strong choice. Proxy servers offer flexibility and ease of use, while VPNs provide comprehensive security and privacy.
NAT is a simple and cost-effective option for limited use cases.
Best Practices for WireGuard Split Tunneling
Implementing WireGuard split tunneling effectively requires careful planning and configuration. Here are some best practices to consider:
- Understand Your Network and Applications: Assess the network topology, traffic patterns, and applications that will be using WireGuard. This will help you determine the appropriate configuration for split tunneling.
- Define Clear Policies: Establish clear policies for which applications and traffic will be routed through the VPN tunnel and which will bypass it. This will ensure consistent and secure operation.
- Use Trusted Endpoints: Configure WireGuard with trusted endpoints to prevent unauthorized access to your network. This includes using strong encryption and authentication mechanisms.
- Monitor and Manage Traffic: Regularly monitor VPN traffic and connections to identify any suspicious activity or performance issues. Implement tools for logging, traffic analysis, and intrusion detection.
- Test and Validate: Thoroughly test and validate the WireGuard split tunneling configuration before deploying it in a production environment. This includes testing different applications, traffic scenarios, and security measures.
- Consider Performance Optimization: Optimize the WireGuard configuration for performance by tuning parameters such as MTU size, encryption algorithms, and connection intervals.
- Provide User Training: Train users on the purpose and operation of WireGuard split tunneling. This will help ensure they understand how to use it effectively and securely.
Case Studies
WireGuard split tunneling has been successfully implemented in various scenarios, offering significant benefits and improved network security. Let’s explore some real-world examples:
Enterprise Use Case
- Company: Global financial institution with multiple international offices
- Challenge: Secure access to sensitive data while allowing employees to access public websites
- Solution: Implemented WireGuard split tunneling to route only work-related traffic through the VPN, while allowing personal browsing through the local internet connection
- Benefits: Enhanced data protection, reduced network congestion, and improved user experience
Remote Work Scenario
- Company: Software development company with remote employees
- Challenge: Secure access to internal resources while using public Wi-Fi networks
- Solution: Configured WireGuard split tunneling to route only work-related traffic through the VPN, while allowing access to local devices and services
- Benefits: Increased security, improved performance, and simplified network management
Personal Use Case
- User: Individual with a gaming console and streaming device
- Challenge: Reduce latency for gaming while maintaining access to streaming services
- Solution: Used WireGuard split tunneling to route gaming traffic directly to the internet, while using the VPN for all other traffic
- Benefits: Enhanced gaming experience, optimized network usage, and improved security
Future Developments
WireGuard split tunneling is a relatively new technology, but it has already gained significant traction in the networking community. As the technology continues to mature, we can expect to see even more developments and trends in the future.
One of the most important areas of development for WireGuard split tunneling is the integration with other technologies. For example, we can expect to see WireGuard split tunneling integrated with cloud computing platforms, network management systems, and security solutions. This integration will make it easier to manage and secure WireGuard split tunneling deployments.
Emerging Technologies
Another area of development for WireGuard split tunneling is the exploration of emerging technologies. For example, we can expect to see WireGuard split tunneling integrated with artificial intelligence (AI) and machine learning (ML). This integration will enable WireGuard split tunneling to automatically adapt to changing network conditions and to make more intelligent decisions about which traffic to route through the tunnel.
Evolution of WireGuard Split Tunneling
Finally, we can expect to see the evolution of WireGuard split tunneling itself. For example, we can expect to see new features and capabilities added to WireGuard split tunneling, such as support for IPv6, multi-hop connections, and network namespaces. These new features and capabilities will make WireGuard split tunneling even more versatile and powerful.
Summary
WireGuard application split tunneling represents a significant advancement in network security and performance optimization. Its ability to selectively route traffic through a VPN while maintaining direct internet access for non-critical traffic provides organizations with unparalleled flexibility and control over their network infrastructure.
By implementing WireGuard split tunneling, organizations can safeguard sensitive data, improve network efficiency, and enhance their overall cybersecurity posture. As technology continues to evolve, WireGuard split tunneling will undoubtedly play an increasingly vital role in shaping the future of secure and optimized networking.