In the realm of web server security, SSH (Secure Shell) stands as a cornerstone, providing a secure channel for remote access and management. Configuring SSH effectively is paramount, and one crucial aspect is selecting the appropriate port number. This decision involves balancing security considerations, ease of use, and potential performance implications.
Delve into this exploration as we uncover the optimal port number for SSH on your web server, ensuring both robust security and seamless functionality.
Navigating the intricacies of port selection for SSH requires a comprehensive understanding of the default SSH port, alternative port options, and the nuances of port forwarding and firewall configuration. Furthermore, implementing effective access control mechanisms, logging and monitoring systems, and adhering to best practices are essential for maintaining a secure SSH environment.
By delving into these aspects, we aim to equip you with the knowledge and strategies necessary to safeguard your web server against unauthorized access and potential vulnerabilities.
Security Considerations
Ensuring restricted access to SSH (Secure Shell) is paramount for safeguarding web servers from potential threats and unauthorized access.
Leaving SSH open on a web server poses significant risks, making it imperative to implement robust security measures to protect against cyberattacks.
Risks Associated with Open SSH
- Unwanted Access: An open SSH port invites unauthorized individuals to gain access to the web server, potentially leading to data breaches, malicious software installations, and website defacements.
- Brute-Force Attacks: Leaving SSH open increases the susceptibility to brute-force attacks, where attackers use automated tools to try numerous password combinations until they succeed in gaining access.
- Exploit Vulnerability: An open SSH port can serve as an entry point for exploiting vulnerabilities in the SSH server or underlying operating system, allowing attackers to escalate privileges and compromise the entire system.
Default SSH Port
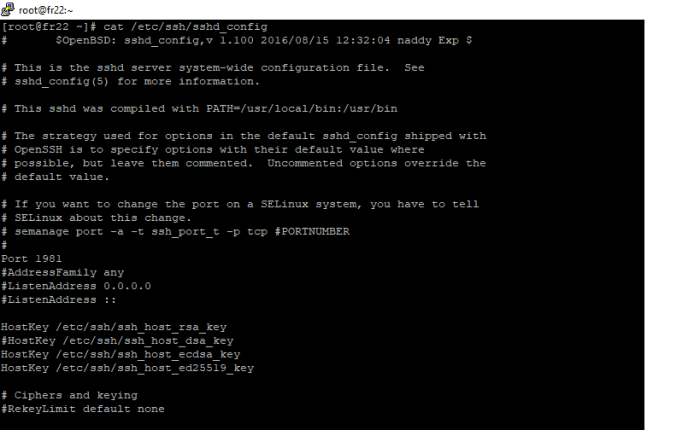
The default port number for SSH is 22.
This port was chosen for several reasons:
- It is a well-known port, which makes it easy to remember and configure.
- It is not commonly used by other services, which reduces the risk of conflict.
- It is a relatively high port number, which makes it less likely to be blocked by firewalls.
Security Considerations
While using the default SSH port has some advantages, it also comes with some security considerations:
- Increased Attack Surface: Using the default port makes it easier for attackers to target SSH servers, as they know where to look.
- Port Scanning: Attackers can use port scanning tools to identify systems running SSH on the default port, making them more vulnerable to targeted attacks.
- DDoS Attacks: Attackers can launch DDoS attacks against the default SSH port, overwhelming the server and making it unavailable to legitimate users.
To mitigate these risks, it is recommended to change the default SSH port to a non-standard one. This makes it more difficult for attackers to target the server and reduces the risk of successful attacks.
Alternative Port Numbers
To enhance SSH security, system administrators can opt for non-default port numbers. This practice helps protect against automated attacks targeting commonly used ports like 22.
Choosing an alternative port offers several advantages. Primarily, it reduces the likelihood of automated attacks, as most malicious scripts are programmed to target default ports. Additionally, it minimizes the risk of port scanning by unauthorized individuals or malicious entities seeking vulnerabilities.
Port Range and Considerations
When selecting an alternative port, system administrators should consider a range of options beyond the default port 22. Common alternatives include ports 2222, 443, 80, and 445, among others. However, it’s crucial to avoid well-known ports assigned to other services, as this may interfere with system functionality.
Choosing an obscure port number further enhances security by making it less predictable for attackers. However, it’s essential to strike a balance between security and practicality. Selecting a port that is too obscure may make it challenging for legitimate users to access the server, potentially hindering productivity and workflow.
Access Control
Access control for SSH can be achieved through a combination of methods, including:
- SSH keys: SSH keys are public-private key pairs that allow users to authenticate to a server without providing a password. The public key is stored on the server, while the private key is kept secret by the user.
- Passwords: Passwords are traditional authentication methods that require users to enter a secret password to access a server.
SSH Keys
SSH keys offer several advantages over passwords:
- Increased security: SSH keys are more secure than passwords because they are not transmitted over the network in plaintext. This makes them less susceptible to eavesdropping and brute-force attacks.
- Convenience: SSH keys eliminate the need to remember and enter passwords, making it easier for users to access servers.
Passwords
Passwords, while less secure than SSH keys, are still a viable option for access control, especially in environments where SSH keys are not practical or desirable.
To enhance the security of passwords, it is recommended to use strong passwords that are at least 12 characters long and contain a mix of upper and lower case letters, numbers, and symbols.
Logging and Monitoring
Logging and monitoring SSH activity is crucial for maintaining security and detecting suspicious behavior. It enables the identification of potential threats, unauthorized access attempts, and security breaches.
To establish a logging and monitoring system for SSH, consider the following steps:
Setting Up Logging
- Configure SSH to log all connection attempts, successful and unsuccessful, including the source IP address, username, and timestamps.
- Set up a centralized logging server to collect and store SSH logs from all relevant systems.
- Use a log management tool or SIEM (Security Information and Event Management) system to analyze and correlate SSH logs with other security data sources.
Monitoring SSH Activity
- Continuously monitor SSH logs for suspicious activities, such as failed login attempts, unusual patterns of access, or attempts from blacklisted IP addresses.
- Set up alerts and notifications to promptly inform administrators about potential security incidents.
- Regularly review SSH logs to identify trends, patterns, or anomalies that may indicate a security compromise.
Troubleshooting
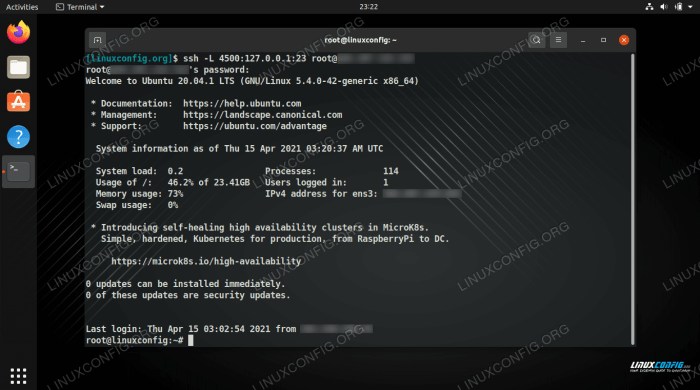
SSH troubleshooting involves identifying and resolving common issues that may arise during SSH sessions.
Identifying common troubleshooting scenarios for SSH can help you quickly pinpoint the source of the problem and take appropriate action to resolve it.
Connection Issues
- Unable to connect to the SSH server: This could be due to incorrect network configuration, firewall blocking, or an issue with the SSH server itself.
- Connection timeout: The SSH connection may time out due to network latency or slow response from the server.
- Authentication failure: Incorrect username or password, disabled SSH user account, or expired SSH keys can cause authentication failures.
Permission Issues
- Permission denied for certain commands or files: This could be due to incorrect file permissions, insufficient user privileges, or SELinux/AppArmor restrictions.
- Unable to create or modify files: Insufficient write permissions or locked files can prevent file operations.
Key Management Issues
- Unable to connect using SSH keys: Incorrectly formatted keys, missing private keys, or issues with the ~/.ssh/config file can cause key-based authentication problems.
- Key fingerprint mismatch: The SSH server’s key fingerprint does not match the expected fingerprint, indicating a potential man-in-the-middle attack.
Network and Firewall Issues
- Blocked SSH port: Ensure that the SSH port (default port 22) is open on the server’s firewall and network configuration.
- Incorrect firewall rules: Misconfigured firewall rules can block SSH traffic, preventing connections.
Server Configuration Issues
- Incorrect SSH configuration: Improper SSH configuration settings in /etc/ssh/sshd_config can cause various issues.
- Disabled SSH service: Ensure that the SSH service is enabled and running on the server.
Advanced Configuration
SSH provides various advanced configuration options to enhance security, control access, and customize its behavior. These options allow system administrators to fine-tune SSH for specific requirements.
One notable advanced feature of SSH is the ability to create SSH tunnels. SSH tunneling allows users to securely forward traffic from one network to another over an encrypted SSH connection. This technique is often used to securely access remote resources, bypass firewalls, or create secure communication channels between two systems.
SSH Tunnels
SSH tunnels operate by establishing an SSH connection between two hosts and then forwarding specific traffic through this connection. This allows data to be securely transmitted between the hosts without being exposed to the public network. SSH tunnels can be used for various purposes, including:
- Securely accessing remote resources: SSH tunnels can be used to securely access remote servers, databases, or other resources over an encrypted connection. This allows users to securely manage and interact with remote systems without exposing sensitive data to the public network.
- Bypassing firewalls: SSH tunnels can be used to bypass firewalls and other network restrictions. By establishing an SSH connection to a remote server, users can forward traffic through this connection and access resources that would otherwise be blocked by the firewall.
- Creating secure communication channels: SSH tunnels can be used to create secure communication channels between two systems. This is useful for establishing secure connections between two networks or for securely transferring sensitive data between two systems.
SSH tunnels can be configured using the -L or -R options of the SSH command. The -L option is used to create a local tunnel, which forwards traffic from a local port to a remote host and port.
The -R option is used to create a remote tunnel, which forwards traffic from a remote host and port to a local port.
In addition to SSH tunnels, SSH also provides other advanced features such as port knocking, X11 forwarding, and support for various authentication methods. These features allow users to customize SSH to meet specific security and usability requirements.
Final Conclusion
In conclusion, selecting the appropriate port number for SSH on your web server is a multifaceted task that demands careful consideration of security, flexibility, and performance. While the default port offers simplicity, alternative ports can enhance security by obscuring the standard SSH port.
Additionally, port forwarding and firewall configuration play crucial roles in managing SSH access. Implementing robust access control, logging, and monitoring mechanisms further strengthens the security posture of your SSH setup. By adhering to best practices and addressing common troubleshooting scenarios, you can ensure that your web server remains secure and accessible, empowering you to manage and maintain it effectively.