Securing your web server is crucial, and one essential aspect of that is managing SSH access. Choosing the right SSH port number is a critical decision that can impact the security and accessibility of your server. In this guide, we will delve into the considerations, best practices, and implications of selecting an SSH port number for your web server.
SSH (Secure Shell) is a vital protocol for remote server management. It provides a secure channel for accessing and controlling your server from anywhere with an internet connection. However, the default SSH port (22) is well-known and often targeted by attackers.
Changing the SSH port number can enhance security by making it less predictable and reducing the risk of automated attacks.
Port Number Selection Criteria
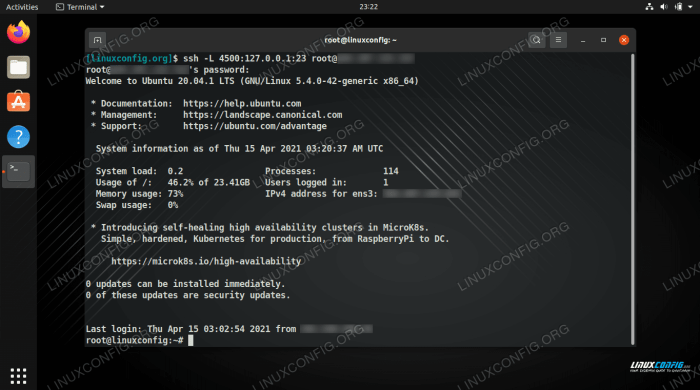
Selecting the right port number for SSH on a web server is crucial for security and accessibility. Here are key factors to consider:
Security: Choose a non-standard port number to reduce the risk of automated attacks that target common ports.
Availability: Ensure the chosen port is not already in use by other services or applications.
Firewall Rules: Configure firewall rules to allow traffic on the selected port.
Commonly Used SSH Port Numbers
- Port 22: The default SSH port, widely used and well-known to attackers. Offers minimal security but is easy to configure.
- Port 443: The standard HTTPS port. Using this port for SSH can enhance security by blending SSH traffic with regular web traffic.
- Non-Standard Ports (e.g., 1022, 8022): Less commonly used ports that provide increased security by obscuring SSH traffic.
Security Implications
Modifying the default SSH port number can have significant security implications, both positive and negative.
On the one hand, changing the SSH port number can enhance security by making it more difficult for attackers to identify and target SSH services. By using a non-standard port, you can reduce the likelihood of automated attacks that scan for open SSH ports on common port numbers.
Recommendations for Securing SSH Access
In addition to changing the SSH port number, there are several other measures you can take to secure SSH access:
- Use strong passwords or SSH keys for authentication.
- Disable password authentication and use SSH keys exclusively.
- Limit the number of login attempts to prevent brute-force attacks.
- Use fail2ban or similar tools to block IP addresses that make multiple failed login attempts.
- Monitor SSH logs for suspicious activity.
- Keep SSH software up to date with the latest security patches.
Best Practices for Port Configuration
Best Practices for SSH Port Configuration
To enhance the security of your web server, consider implementing the following best practices when configuring the SSH port number:
- Use a Non-Standard Port Number: Assign a port number other than the default (22) to make it harder for attackers to target your server.
- Enable Port Knocking: Require a specific sequence of port connections before granting SSH access, adding an extra layer of protection.
- Limit Access to Trusted IP Addresses: Restrict SSH access to specific IP addresses or subnets to prevent unauthorized connections.
- Use Strong Passwords and SSH Keys: Implement robust passwords and SSH keys to prevent brute-force attacks.
- Disable Root Login: Prevent direct login as the root user to minimize the risk of privilege escalation attacks.
- Enable Two-Factor Authentication (2FA): Require an additional authentication factor, such as a one-time password, for enhanced security.
- Regularly Monitor and Audit SSH Logs: Keep track of SSH login attempts and monitor for any suspicious activity to detect and respond to potential threats.
Steps Involved in Changing the SSH Port Number
To change the SSH port number on your web server, follow these steps:
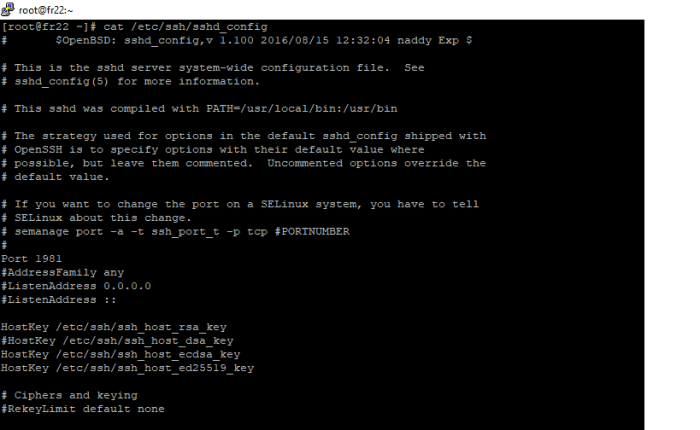
- Edit the SSH configuration file (/etc/ssh/sshd_config) using a text editor.
- Locate the “Port” directive and change the default value (22) to your desired non-standard port number.
- Save the changes to the configuration file.
- Restart the SSH service to apply the new configuration.
Examples of Secure SSH Port Number Configurations
Some examples of secure SSH port number configurations include:
- Port 443: Using the HTTPS port can be effective for stealth, as attackers may not expect SSH traffic on this port.
- Port 8022: This port is commonly used for SSH connections and is less likely to be targeted by attackers.
- Port 10022: A non-standard port number that provides an additional layer of obscurity.
Impact on Firewall Rules
Modifying the SSH port number necessitates updating firewall rules to permit access to the new port. This is crucial to ensure that authorized users can connect to the server securely while blocking unauthorized access.
To update firewall rules, identify the existing rule that allows SSH traffic on the default port (usually port 22). Modify the rule to specify the new SSH port number. Additionally, create a new rule if one does not exist to allow traffic on the new port.
Example Firewall Rule Modifications
- Existing Rule:
iptables
-A INPUT
-p tcp
--dport 22
-j ACCEPT - Modified Rule:
iptables(assuming SSH is moved to port 443)
-A INPUT
-p tcp
--dport 443
-j ACCEPT - New Rule:
iptables(if no existing rule for port 443)
-A INPUT
-p tcp
--dport 443
-j ACCEPT
Remote Access Considerations
Changing the SSH port number affects remote access to the web server by altering the default port that SSH clients use to connect to the server. This means that users will need to specify the new port number when connecting to the server remotely.The
implications for SSH clients and remote management tools are that they may need to be updated to support the new port number. Some SSH clients may have built-in support for non-standard port numbers, while others may require manual configuration. Remote management tools that rely on SSH for communication will also need to be updated to use the new port number.To
ensure seamless remote access, it is important to communicate the new SSH port number to all authorized users and update any SSH clients or remote management tools that are used to access the server. It is also a good idea to test remote access after changing the SSH port number to ensure that everything is working as expected.
Troubleshooting Port Number Issues
Resolving SSH port number issues involves identifying and rectifying errors related to SSH port configuration. Common troubleshooting steps include checking firewall rules, verifying SSH service status, and examining error messages.
To identify errors, check for messages in the SSH log files, such as /var/log/auth.log or /var/log/secure. These logs may indicate connection failures, permission denials, or incorrect port settings.
Error Messages and Solutions
- “Permission denied (publickey).”: This error occurs when the SSH server cannot authenticate the client’s public key. Verify that the key is added to the authorized_keys file on the server.
- “Connection refused.”: This error indicates that the SSH server is not listening on the specified port. Check that the SSH service is running and that the port is open in the firewall.
- “Address already in use.”: This error occurs when another process is already using the specified port. Identify and stop the conflicting process, or change the SSH port number.
Advanced Port Management Techniques
Beyond basic port configuration, advanced techniques enhance SSH security and flexibility.
Two notable techniques are port knocking and port forwarding.
Port Knocking
Port knocking involves sending a specific sequence of connection attempts to pre-defined ports, like a secret knock.
When the correct sequence is received, the SSH port is temporarily opened, providing access only to authorized users.
Port Forwarding
Port forwarding allows SSH connections to be tunneled through an intermediary server, masking the true destination.
This technique is useful for accessing remote systems behind firewalls or for secure communication between untrusted networks.
Integration with Web Server Software
The SSH port number plays a crucial role in the integration of SSH with different web server software. Web servers like Apache and Nginx utilize the SSH port to establish a secure connection between the server and remote users, enabling them to manage and configure the server remotely.
The integration of SSH with web servers involves configuring the SSH port number within the web server’s configuration files. This configuration typically includes specifying the port number, the SSH user, and the authentication method (e.g., password or public key).
Apache Integration
In Apache, the SSH port number is configured within the httpd.conf file. The following directive is used to specify the SSH port:
SSLPort 443
This directive sets the SSH port to 443, which is the default port for HTTPS traffic. Additionally, Apache allows for the use of SSH tunneling, which enables users to securely access other services on the server through the SSH connection.
Nginx Integration
In Nginx, the SSH port number is configured within the nginx.conf file. The following directive is used to specify the SSH port:
listen 443 ssl;
This directive sets the SSH port to 443, which is the default port for HTTPS traffic. Nginx also supports SSH tunneling, allowing users to securely access other services on the server through the SSH connection.
Case Studies and Real-World Examples
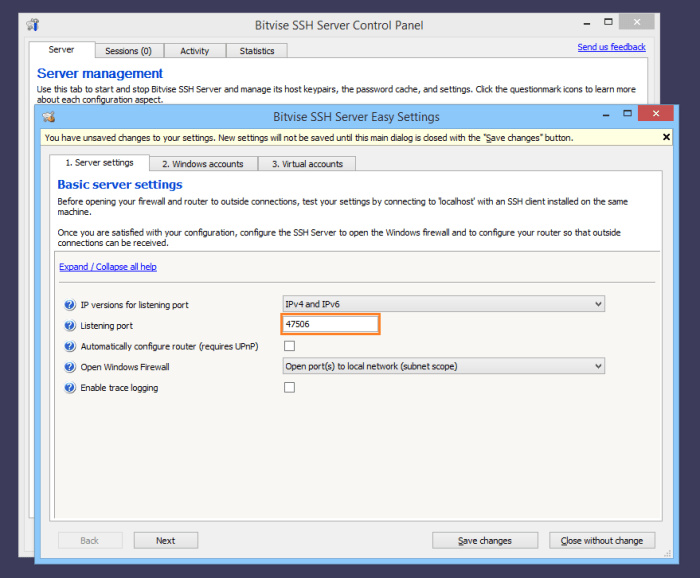
Let’s explore some successful real-world examples of SSH port number configurations and understand the rationale behind them.
Example 1: Security Enhancement with Non-Standard Port
A tech company wanted to enhance the security of their SSH access. They chose to use a non-standard port, such as 45000, instead of the default 22.
This choice reduced the risk of automated attacks, as most malicious bots scan for the standard port. By using an obscure port, they increased the difficulty for attackers to gain unauthorized access.
Example 2: Load Balancing and Redundancy
A large-scale enterprise required high availability and load balancing for their SSH access. They decided to configure multiple SSH servers and use a load balancer to distribute incoming connections across these servers.
By using different port numbers for each server (e.g., 22000, 22001, 22002), they ensured that if one server became unavailable, the load balancer could seamlessly redirect connections to the other servers, maintaining uninterrupted SSH access.
Lessons Learned
- Customizing SSH port numbers can enhance security by reducing the attack surface.
- Using non-standard ports can prevent automated attacks and make brute-force attempts less effective.
- Multiple SSH servers with different port numbers provide redundancy and load balancing, ensuring high availability.
Additional Resources and Further Reading
Expand your knowledge of SSH port number management with these valuable resources:
Official Documentation
- OpenSSH User Manual: https://man.openssh.com/ssh
- SSH Port Forwarding Guide: https://www.ssh.com/ssh/port-forwarding
Technical Articles
- Best Practices for SSH Port Management: https://www.cloudflare.com/learning/security/ssh/best-practices-for-ssh-port-management
- Securing SSH: Choosing the Right Port: https://www.cyberciti.biz/tips/secure-ssh-port.html
Community Forums
- OpenSSH Community Forum: https://forum.openssh.com/
- Server Fault: SSH Port Number Management: https://serverfault.com/questions/tagged/ssh-port-number-management
Last Recap
Selecting the right SSH port number for your web server requires careful consideration of security, accessibility, and integration with other services. By following the best practices Artikeld in this guide, you can optimize your SSH configuration and ensure secure remote access to your server.
Remember to regularly review and update your SSH settings to maintain a robust security posture and adapt to evolving threats.