In the ever-evolving world of cybersecurity, WebSocket VPN has emerged as a game-changer, providing unparalleled security and performance for remote access solutions. This innovative technology leverages the power of WebSocket, a full-duplex communication protocol, to establish secure and reliable connections over the internet, offering a seamless and protected experience for users.
WebSocket VPNs are gaining widespread adoption across industries, enabling secure remote access to corporate networks, applications, and resources. Its versatility extends to various use cases, including remote work, BYOD, and IoT device management, making it an essential tool for businesses seeking to enhance their security posture and operational efficiency.
WebSocket VPN Overview
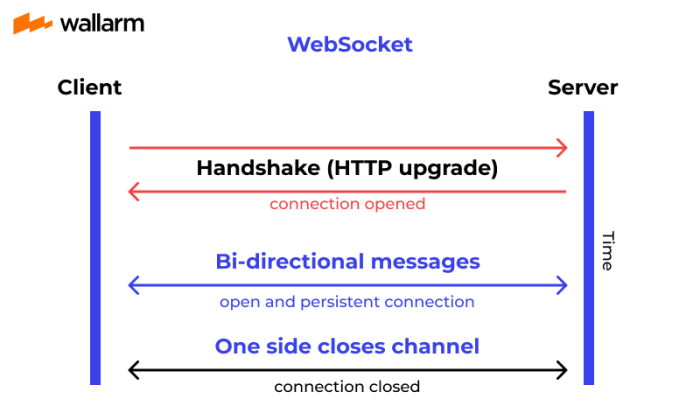
WebSocket VPN is a secure tunneling protocol that uses WebSocket, a modern web technology, to establish a secure connection between a client and a remote server. It encapsulates VPN traffic within WebSocket frames, allowing it to bypass firewalls and proxies that may block traditional VPN protocols.WebSocket
VPN provides several benefits, including:
-
-*Enhanced Security
WebSocket VPN encrypts data using industry-standard encryption algorithms, ensuring data privacy and integrity.
-*Cross-Platform Compatibility
WebSocket is supported by all major browsers and operating systems, making WebSocket VPN accessible from any device with an internet connection.
-*Firewall and Proxy Traversal
WebSocket VPN can bypass firewalls and proxies that block traditional VPN protocols, allowing users to access restricted networks from behind these barriers.
-*Low Latency and High Performance
WebSocket VPN utilizes a low-latency protocol that optimizes data transfer, resulting in faster and more responsive connections.
WebSocket VPN Architecture
WebSocket VPN architecture is designed to establish a secure, encrypted tunnel over a WebSocket connection.
It consists of several key components that work together to provide a seamless and secure VPN experience.The primary components of a WebSocket VPN architecture include:
-
-*WebSocket Server
The WebSocket server acts as the central point of communication for all WebSocket VPN clients. It handles the initial handshake, authenticates clients, and manages the WebSocket connections.
-*WebSocket Client
The WebSocket client is the software that runs on the user’s device and establishes a WebSocket connection to the WebSocket server. It encrypts and sends data through the WebSocket connection.
-*VPN Gateway
The VPN gateway is the endpoint of the VPN tunnel. It receives encrypted data from the WebSocket client, decrypts it, and forwards it to the intended destination.
-*Web Application Firewall (WAF)
A WAF can be integrated into the WebSocket VPN architecture to provide an additional layer of security. It can block malicious traffic and protect the VPN from attacks.
These components interact with each other to provide a secure and reliable VPN connection.
The WebSocket server authenticates clients and establishes the WebSocket connection. The WebSocket client encrypts and sends data through the WebSocket connection. The VPN gateway decrypts the data and forwards it to the intended destination. The WAF provides an additional layer of security by blocking malicious traffic.
WebSocket VPN Protocols
WebSocket VPNs employ various protocols to establish secure and reliable connections. Each protocol offers distinct advantages and drawbacks, influencing the suitability of WebSocket VPNs for specific applications.
WebSocket Protocol
WebSocket is a widely adopted protocol for establishing real-time, bidirectional communication channels over a single TCP connection. It enables WebSocket VPNs to transmit data efficiently and reliably, even in high-latency or unstable network conditions.
SSL/TLS
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are encryption protocols that secure WebSocket connections by encrypting data in transit. This prevents eavesdropping and ensures data confidentiality and integrity.
DTLS
Datagram Transport Layer Security (DTLS) is a variation of TLS designed for use with UDP. It provides encryption and authentication for WebSocket VPNs that operate over UDP, enabling secure communication even in environments with unreliable or intermittent connectivity.
WebSocket VPN Security
WebSocket VPN employs various security mechanisms to protect data transmission, including:
- Encryption: Data is encrypted using industry-standard protocols such as TLS (Transport Layer Security) and DTLS (Datagram Transport Layer Security), ensuring confidentiality and integrity during transmission.
- Authentication: Users are authenticated through secure mechanisms like OAuth or JWT (JSON Web Tokens), verifying their identity before establishing a connection.
- Authorization: Access control policies are enforced to limit user access to authorized resources and prevent unauthorized access.
- Data Integrity: WebSocket VPN uses checksums or hashes to ensure the integrity of data during transmission, detecting and preventing data tampering.
Vulnerabilities and Mitigation Strategies
Despite these security measures, WebSocket VPN may still be susceptible to certain vulnerabilities:
- Cross-Site WebSocket Hijacking (XSS-WSH): An attacker could exploit a vulnerability in a web application to inject malicious code that hijacks WebSocket connections and gains access to sensitive data.
- Man-in-the-Middle (MitM) Attacks: An attacker could intercept and manipulate WebSocket traffic, impersonating legitimate users or injecting malicious payloads.
- Buffer Overflow Attacks: Excessive data sent to the WebSocket server could trigger a buffer overflow, leading to system compromise.
To mitigate these vulnerabilities, WebSocket VPN implementations should adhere to best practices such as:
- Regular Security Updates: Regularly updating WebSocket VPN software and components to patch vulnerabilities.
- Secure WebSocket Libraries: Using well-maintained and secure WebSocket libraries that implement industry-standard security protocols.
- Proper Input Validation: Validating and sanitizing user input to prevent malicious code injection.
- Intrusion Detection Systems (IDS): Deploying IDS to monitor WebSocket traffic for suspicious activity.
- Secure Websockets Header: Setting the “Sec-WebSocket-Protocol” header to ensure the use of a secure WebSocket protocol.
By implementing these security measures and mitigation strategies, organizations can enhance the security of WebSocket VPN connections and protect sensitive data from unauthorized access and manipulation.
WebSocket VPN Performance
WebSocket VPNs offer a unique combination of performance and flexibility, making them an attractive option for a wide range of applications. In this section, we will analyze the performance characteristics of WebSocket VPNs and provide metrics for measuring latency, throughput, and reliability.
WebSocket VPNs achieve high performance by leveraging the WebSocket protocol, which provides a full-duplex communication channel over a single TCP connection. This allows for low-latency, high-throughput data transfer between the client and the server. Additionally, WebSocket VPNs can take advantage of HTTP/2 multiplexing, which allows multiple WebSocket connections to be established over a single TCP connection, further improving performance.
Latency
Latency is a critical performance metric for VPNs, as it determines the responsiveness of the connection. WebSocket VPNs typically have lower latency than traditional VPNs, due to the use of the WebSocket protocol. WebSocket uses a binary framing format, which reduces the overhead associated with data transfer, and it also supports compression, which can further reduce latency.
Latency can be measured using a variety of tools, such as ping or traceroute. A good target for WebSocket VPN latency is less than 100ms, which is imperceptible to most users.
Throughput
Throughput is another important performance metric for VPNs, as it determines the maximum amount of data that can be transferred over the connection. WebSocket VPNs typically have high throughput, due to the use of the WebSocket protocol. WebSocket supports large message sizes and can take advantage of HTTP/2 multiplexing, which allows multiple WebSocket connections to be established over a single TCP connection, increasing throughput.
Throughput can be measured using a variety of tools, such as iperf or netperf. A good target for WebSocket VPN throughput is greater than 100Mbps, which is sufficient for most applications.
Reliability
Reliability is a critical performance metric for VPNs, as it determines the availability and stability of the connection. WebSocket VPNs are generally reliable, due to the use of the WebSocket protocol. WebSocket provides built-in error detection and correction, and it can automatically reconnect if the connection is lost.
Reliability can be measured using a variety of tools, such as ping or traceroute. A good target for WebSocket VPN reliability is 99.9%, which means that the connection is available and stable for 99.9% of the time.
WebSocket VPN Implementations
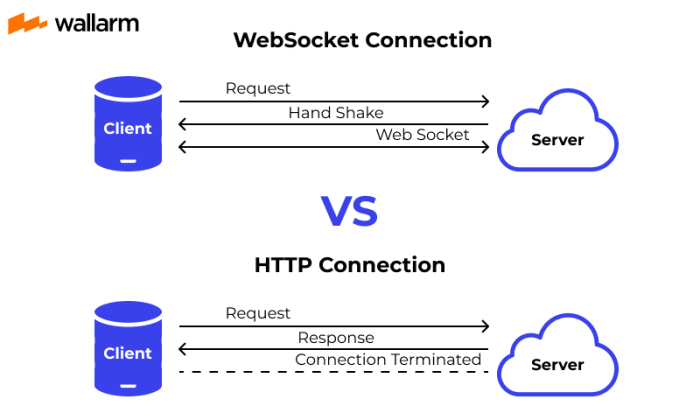
WebSocket VPNs are implemented in various open-source and commercial software. Here’s a table summarizing some popular implementations:
| Implementation | Features | Supported Platforms | Use Cases |
|---|---|---|---|
| OpenVPN for WebSockets | Cross-platform, open source, supports multiple protocols | Windows, Linux, macOS | Remote access, site-to-site VPNs |
| Stunnel over WebSockets | Lightweight, open source, supports SSL/TLS | Windows, Linux, macOS | Secure remote access, application tunneling |
| WebSockets Secure Tunneling Protocol (WSTSP) | Open source, supports multiple protocols, high performance | Linux | Site-to-site VPNs, high-speed data transfer |
| Apache Guacamole | Open source, supports multiple protocols, web-based interface | Windows, Linux, macOS | Remote desktop access, application publishing |
| Tailscale | Commercial, closed source, easy setup and management | Windows, Linux, macOS, iOS, Android | Remote access, mesh networking |
WebSocket VPN Best Practices
To ensure optimal deployment and management of WebSocket VPN, follow these best practices:
Security Configurations
- Enforce strong authentication mechanisms, such as two-factor authentication (2FA), to prevent unauthorized access.
- Implement role-based access control (RBAC) to limit user privileges and prevent privilege escalation.
- Configure firewall rules to restrict access to the WebSocket VPN server only from authorized sources.
- Monitor the WebSocket VPN server for suspicious activities and implement intrusion detection and prevention systems (IDS/IPS).
Performance Optimizations
Maximize WebSocket VPN performance by implementing these optimizations:
- Use a WebSocket server that supports HTTP/2 and TLS 1.3 for improved performance and security.
- Optimize the WebSocket payload size to reduce latency and improve throughput.
- Consider using a WebSocket proxy to improve performance and reliability.
li>Implement load balancing and failover mechanisms to ensure high availability and scalability.
WebSocket VPN Use Cases
WebSocket VPNs offer versatile solutions for various industries and applications. Their ability to establish secure and efficient connections makes them suitable for scenarios where traditional VPNs fall short.
Real-World Use Cases
| Industry | Application | Benefits |
|---|---|---|
| Remote Work | Accessing corporate resources from home or remote locations | Secure and seamless connectivity, reduced latency |
| IoT | Connecting IoT devices to cloud platforms or local networks | Low bandwidth requirements, efficient data transfer |
| Gaming | Enhancing online gaming experiences by reducing lag and improving responsiveness | Real-time data transmission, optimized performance |
| VoIP and Video Conferencing | Establishing secure and reliable connections for voice and video calls | Clear and uninterrupted communication, improved quality of service |
| Cloud Computing | Accessing cloud-based applications and resources securely | Enhanced security, improved flexibility and scalability |
WebSocket VPN Limitations
WebSocket VPNs, while offering numerous benefits, do have certain limitations and challenges that should be considered. These limitations may include:
-
-*Latency and Performance
WebSocket VPNs can introduce additional latency compared to traditional VPN protocols, especially in high-bandwidth or real-time applications. This latency can impact the user experience, particularly for applications that require low latency or high throughput.
-*Security Concerns
WebSocket VPNs rely on the WebSocket protocol, which is inherently less secure than traditional VPN protocols. WebSocket traffic is sent over a single TCP connection, making it susceptible to man-in-the-middle attacks and eavesdropping.
-*Limited Compatibility
WebSocket VPNs may not be compatible with all devices and operating systems. Some older devices or platforms may not support WebSocket connections, limiting the use of WebSocket VPNs in certain scenarios.
-*Resource Consumption
WebSocket VPNs can consume more resources than traditional VPN protocols. This is because WebSocket connections require constant polling and data transfer, which can put a strain on server resources.
-*Limited Support for Complex Network Configurations
WebSocket VPNs may not support complex network configurations, such as multiple subnets or VLANs. This can limit their use in enterprise environments that require granular network segmentation.
Alternative Solutions for Specific Use Cases
In cases where WebSocket VPNs are not suitable due to their limitations, alternative solutions may be considered:
-
-*IPsec VPNs
IPsec VPNs provide a more secure and stable connection compared to WebSocket VPNs. They are widely supported and offer robust encryption and authentication mechanisms.
-*SSL VPNs
SSL VPNs offer a web-based alternative to traditional VPNs. They are easy to deploy and manage, making them suitable for remote access scenarios.
-*SSH Tunneling
SSH Tunneling allows users to create a secure tunnel over an SSH connection. It can be used to access remote resources or bypass network restrictions.
-*Zero Trust Network Access (ZTNA)
ZTNA provides a modern approach to remote access by granting access based on identity and context rather than network location. It can offer a more secure and flexible alternative to traditional VPNs.
The choice of alternative solution depends on the specific use case and requirements.
Factors such as security, performance, compatibility, and cost should be considered when selecting an appropriate solution.
WebSocket VPN Future Trends
WebSocket VPN technology is rapidly evolving, with several emerging trends and advancements shaping its future direction and applications.
One significant trend is the increasing adoption of WebRTC (Web Real-Time Communication) for WebSocket VPN. WebRTC provides a standardized framework for real-time communication over the web, including audio, video, and data transfer. By leveraging WebRTC, WebSocket VPNs can offer enhanced performance, security, and scalability.
Emerging Trends
- Cloud-based WebSocket VPNs: Cloud-based WebSocket VPNs offer increased flexibility, scalability, and cost-effectiveness compared to traditional on-premises VPN solutions.
- Artificial Intelligence (AI) and Machine Learning (ML): AI and ML algorithms can be integrated into WebSocket VPNs to enhance security, optimize performance, and provide personalized user experiences.
- Zero-Trust Security: Zero-trust security principles are increasingly being applied to WebSocket VPNs, focusing on verifying and authorizing users and devices before granting access to network resources.
Future Applications
As WebSocket VPN technology continues to mature, it is expected to find applications in various areas, including:
- Remote work and access: WebSocket VPNs will continue to play a crucial role in enabling secure and reliable remote work and access to corporate networks.
- Cloud gaming and streaming: WebSocket VPNs can provide low-latency and high-bandwidth connections for cloud gaming and streaming services.
- Internet of Things (IoT): WebSocket VPNs can be used to securely connect IoT devices to cloud platforms and manage their communication.
Last Recap
WebSocket VPN technology is rapidly evolving, with advancements in protocols, security mechanisms, and performance optimization promising even greater capabilities in the future. As the demand for secure and reliable remote access solutions continues to grow, WebSocket VPN is poised to play a pivotal role in shaping the future of cybersecurity and enabling seamless connectivity in a connected world.
