SSH.SSHSlowdns.com – In the realm of remote access, SSH (Secure Shell) has emerged as a formidable tool, providing a secure and encrypted channel for accessing remote systems. With UDP-based SSH tunneling, this technology takes a leap forward, offering unparalleled performance and flexibility for a wide range of applications.
This comprehensive guide will delve into the intricacies of UDP SSH tunneling, exploring its advantages, implementation, and practical use cases.
SSH tunneling leverages the User Datagram Protocol (UDP) to establish a secure tunnel between two endpoints, allowing for the transmission of data over an insecure network. By encapsulating SSH traffic within UDP packets, this technique bypasses the limitations of TCP, resulting in faster and more efficient data transfer.
UDP (User Datagram Protocol)
The User Datagram Protocol (UDP) is a connectionless network protocol used in the Internet Protocol suite. It is a simple protocol that provides a way for applications to send and receive messages over a network without the need for a reliable connection.
UDP differs from TCP in several ways. First, UDP is a connectionless protocol, while TCP is a connection-oriented protocol. This means that UDP does not establish a connection with the receiver before sending data, while TCP does. Second, UDP is an unreliable protocol, while TCP is a reliable protocol.
This means that UDP does not guarantee that data will be delivered to the receiver, while TCP does. Third, UDP is a faster protocol than TCP. This is because UDP does not have to establish a connection before sending data, and it does not have to retransmit data that is lost.
The advantages of using UDP include its speed, its simplicity, and its low overhead. The disadvantages of using UDP include its unreliability and its lack of security.
Applications of UDP
UDP is used in a variety of applications, including:
- Domain Name System (DNS)
- Voice over IP (VoIP)
- Online gaming
- Video streaming
SSH (Secure Shell)
SSH (Secure Shell) is a network protocol that provides secure remote access to a computer system. It allows users to log in to a remote machine and execute commands as if they were physically present at the console.
SSH is a secure alternative to the Telnet protocol, which transmits data in plaintext. SSH encrypts all data, including passwords and commands, making it difficult for eavesdroppers to intercept and decode the information.
Benefits of Using SSH
There are many benefits to using SSH for secure remote access, including:
- Encryption: SSH encrypts all data, including passwords and commands, making it difficult for eavesdroppers to intercept and decode the information.
- Authentication: SSH uses strong authentication methods, such as public-key cryptography, to verify the identity of users.
- Tunneling: SSH can be used to create secure tunnels through which other applications can send data.
- Port forwarding: SSH can be used to forward ports on the remote machine to the local machine, allowing users to access services on the remote machine as if they were running locally.
SSH Clients and Servers
There are many different SSH clients and servers available. Some of the most popular clients include:
- OpenSSH
- PuTTY
- Bitvise SSH Client
Some of the most popular servers include:
- OpenSSH
- SSH Tectia
- SolarWinds SSH Server
Free SSH Tools
In the realm of secure remote access, free SSH clients offer a plethora of options for connecting to remote servers. These clients provide robust encryption and authentication mechanisms, empowering users to manage their systems and applications remotely with confidence.
When selecting a free SSH client, it’s crucial to consider factors such as platform compatibility, feature set, and ease of use. Here’s a comprehensive overview of some popular free SSH clients for various platforms:
PuTTY
- Cross-platform support for Windows, Linux, and macOS
- Lightweight and portable, no installation required
- Supports multiple protocols, including SSH, Telnet, and Rlogin
- Extensive configuration options for advanced users
OpenSSH
- Built-in SSH client and server for Linux, macOS, and Unix systems
- Highly secure and widely adopted
- Supports public-key authentication, password authentication, and two-factor authentication
- Command-line interface for advanced control
KiTTY
- Windows-only SSH client
- Lightweight and portable, similar to PuTTY
- Supports multiple tabs and sessions
- Features a user-friendly graphical interface
Bitvise SSH Client
- Windows-only SSH client with a commercial version
- Offers a comprehensive feature set, including session management, file transfer, and port forwarding
- Supports multiple authentication methods and key management
- User-friendly interface with drag-and-drop functionality
MobaXterm
- Windows-only SSH client with a tabbed interface
- Includes a range of tools for remote system management, such as a terminal emulator, file manager, and X server
- Supports multiple protocols, including SSH, Telnet, RDP, and VNC
- Extensive customization options and plugins
To install and use a free SSH client, follow these general steps:
- Download the client installer from the official website or repository.
- Follow the installation wizard to complete the setup.
- Configure the client with your SSH server details, such as hostname, port, and authentication credentials.
- Establish an SSH connection to your remote server.
With a free SSH client, you can securely access and manage your remote servers from anywhere with an internet connection. These tools empower system administrators, developers, and remote workers with the ability to perform essential tasks, troubleshoot issues, and collaborate efficiently.
UDP-based SSH Tunneling
UDP-based SSH tunneling is a technique for creating a secure tunnel over a UDP network. This is achieved by encapsulating UDP packets within SSH packets, which are then transmitted over an encrypted SSH connection. The SSH connection provides authentication, encryption, and integrity protection for the UDP packets, making it a secure way to transmit data over an untrusted network.One
of the main benefits of using UDP-based SSH tunneling is that it can improve performance over TCP-based SSH tunneling. UDP is a connectionless protocol, which means that it does not require a three-way handshake to establish a connection. This can reduce latency and improve throughput, making it a good choice for applications that require real-time data transmission.UDP-based
SSH tunneling can be used in a variety of applications, including:
- Securely accessing remote resources: UDP-based SSH tunneling can be used to securely access remote resources, such as files, databases, and applications, over an untrusted network.
- Creating a secure VPN: UDP-based SSH tunneling can be used to create a secure VPN, which can be used to protect traffic from eavesdropping and man-in-the-middle attacks.
- Bypassing firewalls: UDP-based SSH tunneling can be used to bypass firewalls that block TCP traffic. This can be useful for accessing resources that are behind a firewall.
Security Considerations
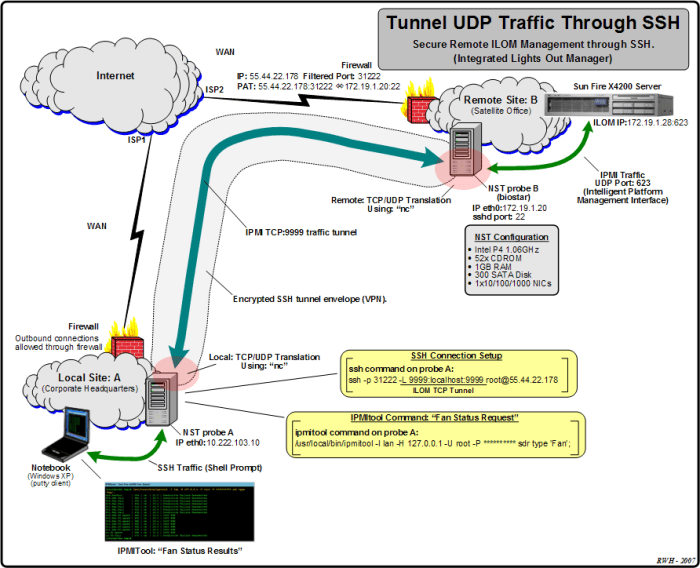
Using UDP-based SSH tunneling introduces potential security risks that differ from traditional TCP-based connections. Understanding these implications and implementing best practices is crucial to mitigate vulnerabilities.
Best Practices for Securing UDP-Based SSH Connections
To enhance the security of UDP-based SSH connections, consider the following measures:
- Use strong encryption algorithms: Employ robust encryption protocols such as AES-256 or ChaCha20 to protect data from eavesdropping.
- Enable two-factor authentication: Require users to provide additional authentication factors, such as a hardware token or biometrics, to prevent unauthorized access.
- Limit access to authorized users: Restrict access to the SSH server to only authorized users and IP addresses using firewall rules or access control lists.
- Use a dedicated port: Configure the SSH server to listen on a non-standard port, making it less susceptible to automated attacks.
- Monitor for suspicious activity: Implement intrusion detection systems or log analysis tools to monitor for unusual network traffic or failed login attempts.
Preventing Unauthorized Access and Attacks
To prevent unauthorized access and attacks on UDP-based SSH connections, consider the following tips:
- Disable password authentication: Rely on public key authentication instead of password-based authentication to prevent brute-force attacks.
- Use a strong firewall: Configure a robust firewall to block unauthorized access attempts and restrict inbound and outbound traffic.
- Keep software up to date: Regularly update the SSH server and client software to patch security vulnerabilities.
- Educate users: Train users on best practices for secure SSH usage, including password management and recognizing phishing attempts.
- Conduct regular security audits: Periodically perform security audits to identify potential vulnerabilities and implement appropriate mitigation measures.
Advanced Configuration
UDP-based SSH tunneling offers a wide range of advanced configuration options to customize the tunneling experience and enhance security. These options allow users to tailor the tunneling settings to meet specific requirements.
To configure advanced settings, users can edit the SSH configuration file (typically located at ~/.ssh/config) and add or modify the following directives:
SSH Tunneling Settings
- LocalForward: Forwards a local port to a remote port on the SSH server.
- RemoteForward: Forwards a remote port on the SSH server to a local port.
- DynamicForward: Dynamically assigns a local port for each forwarded remote port.
- GatewayPorts: Enables the SSH server to act as a gateway for forwarding traffic to other hosts.
Security Considerations
When configuring advanced SSH tunneling settings, it’s crucial to consider security implications:
-
- Firewall Rules: Ensure that firewall rules allow traffic on the configured ports.
- Authentication: Use strong authentication methods (e.g., public-key cryptography) to prevent unauthorized access.
li> Port Scanning : Be aware of potential port scanning attempts and implement appropriate countermeasures.
Advanced Configuration Scenarios
Advanced configuration options enable various scenarios, such as:
- Remote Access to Local Services: Forwarding local ports to the SSH server allows remote access to local services (e.g., web server, database).
- Secure Tunneling for Remote Hosts: Forwarding remote ports to the local machine enables secure communication with remote hosts that are not directly accessible.
- Network Segmentation: Using DynamicForward and GatewayPorts allows for network segmentation, isolating traffic between different hosts.
Real-World Applications
UDP-based SSH tunneling finds numerous practical applications in various industries and use cases. It provides secure and efficient data transmission over unreliable networks, enabling remote access, secure file transfers, and network monitoring.
Remote Access
SSH tunneling allows users to securely access remote computers over public networks, such as the internet. By creating an SSH tunnel, users can establish a secure connection between their local machine and a remote server, allowing them to access applications, files, and resources as if they were on the local network.
This is particularly useful for system administrators, developers, and remote workers who need to access corporate resources from outside the office.
Secure File Transfers
SSH tunneling can be used to securely transfer files between two computers over an untrusted network. By creating an SSH tunnel, users can establish a secure channel for file transfers, protecting the data from eavesdropping and unauthorized access. This is commonly used for transferring sensitive data, such as financial records, medical information, or intellectual property.
Network Monitoring
SSH tunneling can be used for network monitoring purposes. By creating an SSH tunnel between two network devices, administrators can securely monitor network traffic, troubleshoot network issues, and collect performance metrics. This is particularly useful for monitoring remote networks or devices that are not directly accessible.
Alternative Solutions
UDP-based SSH tunneling is not the only remote access solution available. Here are some alternatives:
- Virtual Private Networks (VPNs): VPNs create a secure tunnel between two networks, allowing users to access resources on the remote network as if they were physically connected. VPNs are typically more secure than SSH tunneling, but they can also be more complex to set up and manage.
- Remote Desktop Protocol (RDP): RDP allows users to remotely control a computer over a network connection. RDP is a proprietary protocol developed by Microsoft, and it is only available for Windows computers. RDP is relatively easy to set up and use, but it is not as secure as SSH tunneling or VPNs.
- VNC (Virtual Network Computing): VNC is a platform-independent remote access protocol that allows users to remotely control a computer over a network connection. VNC is open source and free to use, and it is available for a wide range of operating systems. VNC is not as secure as SSH tunneling or VPNs, but it is a good option for basic remote access needs.
Choosing the Right Solution
The best remote access solution for your needs will depend on a number of factors, including:
- Security: SSH tunneling is the most secure remote access solution, followed by VPNs, RDP, and VNC.
- Ease of use: RDP is the easiest remote access solution to set up and use, followed by VNC, SSH tunneling, and VPNs.
- Cost: SSH tunneling and VNC are free to use, while RDP and VPNs can be expensive.
- Compatibility: SSH tunneling is available for a wide range of operating systems, while RDP is only available for Windows computers, and VNC is available for a wide range of operating systems but may not be compatible with all applications.
Future Developments
The future of UDP-based SSH tunneling is promising, with new technologies and trends emerging that may impact its capabilities and applications. One potential development is the integration of UDP-based SSH tunneling with software-defined networking (SDN) and network function virtualization (NFV).
SDN and NFV technologies enable greater flexibility and control over network resources, which could be leveraged to enhance the performance and security of UDP-based SSH tunnels.
New Encryption Algorithms
Another potential development is the adoption of new encryption algorithms, such as post-quantum cryptography (PQC), to enhance the security of UDP-based SSH tunnels. PQC algorithms are designed to resist attacks from quantum computers, which could potentially break the security of current encryption algorithms.
Multi-Path Tunneling
Multi-path tunneling is another promising development that could improve the reliability and performance of UDP-based SSH tunnels. Multi-path tunneling involves establishing multiple tunnels between two endpoints, allowing traffic to be distributed across multiple paths. This can provide redundancy and reduce the impact of network congestion or outages on the tunnel’s performance.
Automated Management
Automated management tools could simplify the deployment and management of UDP-based SSH tunnels. These tools could provide a centralized interface for configuring, monitoring, and troubleshooting tunnels, reducing the need for manual intervention and improving overall efficiency.