In the realm of secure remote access, UDP SSH accounts have emerged as a game-changer, offering a unique blend of speed, efficiency, and enhanced security. Unlike traditional SSH connections that utilize TCP, UDP SSH leverages the User Datagram Protocol, opening up a world of possibilities for seamless data transfer and enhanced performance.
This comprehensive guide delves into the intricacies of UDP SSH accounts, exploring their purpose, advantages, and potential security considerations. We will navigate the intricacies of configuration and setup, unravel the role of port forwarding, and delve into advanced usage scenarios.
By the end of this journey, you will possess a deep understanding of UDP SSH accounts, empowering you to harness their full potential for secure and efficient remote access.
UDP SSH Account Overview
A UDP SSH account utilizes the User Datagram Protocol (UDP) to establish secure remote connections. UDP is a connectionless protocol, meaning it doesn’t require the establishment of a three-way handshake like TCP. This makes UDP faster and more efficient for applications that don’t require guaranteed delivery or ordered transmission of data.
Using UDP for SSH offers several benefits. Firstly, it reduces latency, as there is no need to wait for acknowledgements or retransmissions. Secondly, it minimizes resource consumption, as UDP packets are smaller and require less overhead. However, UDP also has limitations.
It doesn’t provide guaranteed delivery or ordering of packets, which can be problematic for applications that require reliable data transfer.
Benefits of UDP SSH
- Reduced latency due to faster packet transmission.
- Lower resource consumption due to smaller packet sizes and reduced overhead.
- Suitable for applications that don’t require guaranteed delivery or ordered transmission.
Limitations of UDP SSH
- Doesn’t guarantee delivery or ordering of packets.
- May not be suitable for applications that require reliable data transfer.
Security Considerations
UDP SSH accounts, while offering advantages, also introduce certain security risks. It’s essential to be aware of these risks and take appropriate measures to mitigate them.
One primary concern with UDP SSH is its potential vulnerability to amplification attacks. Amplification attacks exploit the fact that UDP packets are not subject to the same rate limits as TCP packets. An attacker can send a small UDP packet to a UDP SSH server, which then responds with a much larger packet.
This can be used to amplify the attacker’s bandwidth and launch denial-of-service attacks on targeted systems.
Mitigation Measures
- Use Strong Authentication: Implement strong authentication mechanisms, such as two-factor authentication or public key cryptography, to prevent unauthorized access.
- Limit Access: Restrict access to UDP SSH accounts to authorized users only. Use access control lists (ACLs) or firewalls to limit connections from specific IP addresses or subnets.
- Monitor Network Traffic: Regularly monitor network traffic for suspicious activity, such as large volumes of UDP packets or unusual patterns. Use intrusion detection systems (IDS) or network monitoring tools to detect and respond to potential attacks.
- Use Rate Limiting: Implement rate limiting mechanisms to limit the number of UDP packets that can be sent to the UDP SSH server from a single source. This can help mitigate amplification attacks.
- Educate Users: Educate users about the security risks associated with UDP SSH accounts and provide guidance on best practices for using them securely.
Configuration and Setup
Configuring and setting up a UDP SSH account involves defining specific parameters and options to establish a secure and functional connection.
The process typically includes selecting a suitable port, enabling UDP forwarding, and configuring firewall rules to allow traffic.
Port Selection
UDP SSH accounts operate on a specific port, which can be customized to enhance security or avoid conflicts with other services.
The default UDP port for SSH is 443, but it’s recommended to choose a non-standard port for increased protection against automated attacks.
UDP Forwarding
To establish a UDP SSH connection, UDP forwarding must be enabled on the server.
This allows the server to accept incoming UDP packets on the chosen port and forward them to the SSH service.
Firewall Configuration
Firewall rules are essential to ensure that UDP traffic destined for the SSH port is allowed through.
The firewall should be configured to permit incoming UDP packets on the selected port from authorized IP addresses or networks.
Port Forwarding
Port forwarding is a technique used in UDP SSH connections to establish secure communication between two computers over a network. It allows a user to access services running on a remote computer as if they were running on the local computer.Port
forwarding works by creating a tunnel between the local and remote computers. Data sent through this tunnel is encrypted, ensuring that it is protected from eavesdropping or interception. Port forwarding can be used to access a variety of services, including web servers, email servers, and remote desktops.
Example Uses of Port Forwarding
*
-*Remote Desktop Access
Port forwarding can be used to access a remote desktop on another computer. This allows a user to control the remote computer as if they were sitting in front of it.
-
- -*Secure Web Browsing Port forwarding can be used to create a secure connection to a web server. This ensures that all data sent between the browser and the web server is encrypted, protecting it from eavesdropping.
-*Email Access
Port forwarding can be used to access email accounts on a remote server. This allows a user to read and send email from anywhere with an internet connection.
Performance Analysis
UDP SSH generally exhibits faster performance compared to TCP SSH, particularly in scenarios involving high latency or packet loss.
UDP’s connectionless nature allows it to establish connections more swiftly, and its use of datagrams enables data transmission without the need for acknowledgment or retransmission mechanisms, resulting in lower overhead and reduced latency.
Factors Affecting Performance
Several factors can influence the performance of both UDP SSH and TCP SSH connections:
- Network Latency: High latency can significantly impact the performance of TCP SSH, as it relies on acknowledgments and retransmissions, which can introduce delays. UDP SSH, on the other hand, is less affected by latency due to its connectionless nature.
- Packet Loss: Packet loss can degrade the performance of both UDP SSH and TCP SSH. However, UDP SSH is more resilient to packet loss because it does not require acknowledgments. TCP SSH, on the other hand, may experience performance issues due to retransmissions caused by lost packets.
- Bandwidth: The available bandwidth can impact the performance of both UDP SSH and TCP SSH. In scenarios with limited bandwidth, UDP SSH may perform better due to its lower overhead compared to TCP SSH.
- Network Congestion: Network congestion can affect the performance of both UDP SSH and TCP SSH. UDP SSH may experience packet drops during congestion, while TCP SSH may experience reduced throughput due to retransmissions.
- Server Configuration: The configuration of the SSH server can also influence performance. Optimizing server settings, such as the cipher suite and packet size, can enhance the performance of both UDP SSH and TCP SSH.
Troubleshooting
UDP SSH accounts can occasionally encounter issues. To resolve these issues effectively, it is important to understand the potential causes and available solutions. This troubleshooting guide will provide a comprehensive overview of common problems and their respective resolutions.
Common Issues and Resolutions
- Unable to establish a UDP SSH connection: Verify that the UDP port specified in the SSH configuration matches the port configured on the SSH server. Ensure that both the client and server firewalls allow UDP traffic on the designated port.
- Slow or unstable UDP SSH connection: Check for network congestion or latency issues. Consider using a different UDP port or adjusting the UDP buffer size to optimize performance.
- Authentication issues: Ensure that the username and password used for authentication are correct. Verify that the SSH server is configured to allow UDP SSH connections and that the client is using the appropriate authentication method.
- Port forwarding issues: Check that the port forwarding rules are configured correctly on both the client and server. Ensure that the target port is accessible and that the firewall settings permit the forwarded traffic.
- Security vulnerabilities: Regularly update the SSH server and client software to address potential security vulnerabilities. Implement strong encryption algorithms and consider using additional security measures, such as two-factor authentication or intrusion detection systems.
Advanced Usage
UDP SSH accounts offer advanced techniques and use cases that extend their capabilities. These techniques can enhance security, performance, and functionality.
SSH Multiplexing
SSH multiplexing allows multiple SSH sessions to be established over a single UDP port. This technique can improve efficiency and reduce latency, particularly for applications that require multiple concurrent connections.
Port Knocking
Port knocking is a technique that involves sending a specific sequence of packets to a UDP port to establish a connection. This technique adds an extra layer of security by requiring authorized clients to “knock” on the port before being granted access.
UDP Tunneling
UDP tunneling allows non-UDP traffic, such as TCP or HTTP, to be encapsulated within UDP packets. This technique can bypass firewalls or network restrictions that block certain protocols.
Advanced Encryption
UDP SSH accounts support a wide range of encryption algorithms, including AES-256, ChaCha20-Poly1305, and Ed25519. These algorithms provide strong encryption to protect data in transit.
Custom Port Forwarding
UDP SSH accounts allow for custom port forwarding, where specific ports on the server can be forwarded to arbitrary ports on the client. This technique enables flexible network configurations and can be used for specialized applications.
Table of UDP SSH Parameters
UDP SSH configuration involves specifying several parameters to control its behavior and functionality. Here’s a comprehensive table listing the key parameters, their descriptions, and default values:
| Parameter | Description | Default Value |
|---|---|---|
| ListenPort | Specifies the UDP port on which the SSH server listens for incoming connections. | 10000 |
| TargetPort | Specifies the TCP port on which the SSH server forwards traffic to the remote host. | 22 |
| LocalAddress | Specifies the local IP address that the SSH server binds to. | 0.0.0.0 (all available interfaces) |
| RemoteAddress | Specifies the IP address of the remote host that the SSH server connects to. | Required, not set by default |
| UDPSendBuffer | Specifies the size of the UDP send buffer in bytes. | 32768 |
| UDPRecvBuffer | Specifies the size of the UDP receive buffer in bytes. | 32768 |
| GatewayPorts | Specifies whether the SSH server should advertise itself as a gateway to other hosts. | No (false) |
Comparison of UDP SSH to Other Protocols
UDP SSH stands out from other protocols due to its unique characteristics. Let’s compare UDP SSH to popular protocols like TCP SSH, SFTP, and SCP to highlight their strengths and limitations.
TCP SSH (Secure Shell) is a widely used protocol for secure remote access and command execution. It operates over the TCP transport layer, ensuring reliable and ordered data transmission. TCP SSH excels in environments where data integrity and reliability are paramount.
Advantages of TCP SSH:
- Reliable and ordered data transmission
- Suitable for applications requiring data integrity
Disadvantages of TCP SSH:
- Higher latency due to TCP’s handshake and acknowledgment mechanisms
- May not be ideal for applications requiring real-time data transfer
SFTP (SSH File Transfer Protocol) is another protocol built on SSH. It provides a secure way to transfer files over an SSH connection. SFTP offers a reliable and encrypted channel for file transfers, making it suitable for sensitive data transmission.
Advantages of SFTP:
- Secure and encrypted file transfer
- Ideal for transferring sensitive data
Disadvantages of SFTP:
- Limited to file transfer operations
- May not be suitable for interactive or real-time applications
SCP (Secure Copy) is a simplified version of SFTP, designed specifically for secure file transfers. It operates over an SSH connection and provides a straightforward way to copy files between remote systems.
Advantages of SCP:
- Simple and easy to use
- Suitable for basic file transfer tasks
Disadvantages of SCP:
- Limited functionality compared to SFTP
- May not be suitable for complex file transfer scenarios
In contrast to TCP SSH, SFTP, and SCP, UDP SSH offers unique advantages for applications requiring low latency and real-time data transfer. UDP SSH utilizes the User Datagram Protocol (UDP), which is a connectionless protocol that prioritizes speed over reliability.
Advantages of UDP SSH:
- Ultra-low latency due to UDP’s connectionless nature
- Suitable for applications requiring real-time data transfer, such as gaming, video streaming, and remote control
Disadvantages of UDP SSH:
- Data integrity may be compromised due to UDP’s unreliable nature
- May not be suitable for applications where data integrity is critical
Choosing the right protocol depends on the specific requirements of the application. For applications requiring reliable data transmission and integrity, TCP SSH is a suitable choice. For secure file transfers, SFTP or SCP can be employed. UDP SSH excels in applications where low latency and real-time data transfer are essential.
Best Practices
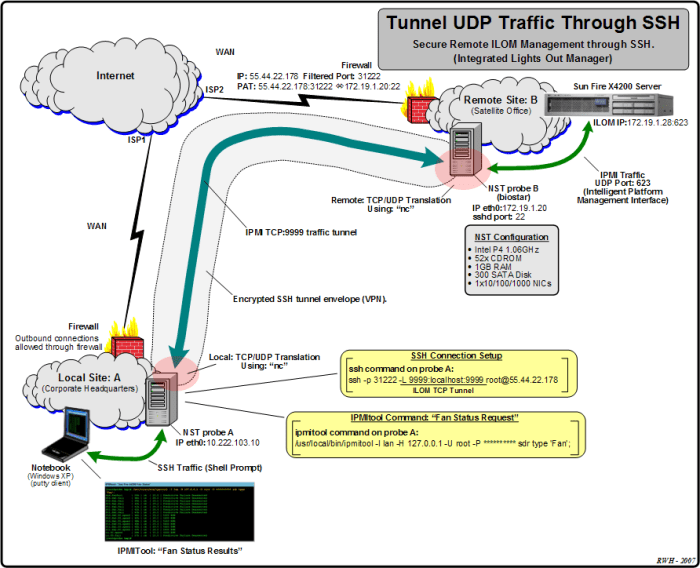
To ensure the security and effective management of UDP SSH accounts, adhering to best practices is crucial. These guidelines minimize vulnerabilities and optimize account functionality.
One key practice is to use strong passwords and enable two-factor authentication. Complex passwords with a combination of uppercase, lowercase, numbers, and special characters enhance security. Two-factor authentication adds an extra layer of protection by requiring a second form of verification, such as a code sent to a mobile device.
Common Pitfalls to Avoid
- Weak Passwords: Using simple or easily guessable passwords compromises account security.
- Lack of Two-Factor Authentication: Relying solely on passwords increases the risk of unauthorized access.
- Unrestricted Access: Granting excessive privileges to users can lead to potential security breaches.
- Outdated Software: Failure to update SSH software and operating systems leaves accounts vulnerable to known exploits.
- Insecure Port Forwarding: Allowing unrestricted port forwarding can expose internal networks to external threats.
Conclusion
UDP SSH accounts have revolutionized the landscape of remote access, providing a secure, efficient, and flexible solution for managing remote systems. By understanding the nuances of UDP SSH, you can optimize your network configurations, enhance security measures, and unlock a world of possibilities for seamless remote connectivity.
Embrace the power of UDP SSH today and elevate your remote access experience to new heights.