In the realm of network connectivity, the advent of UDP SSH (User Datagram Protocol Secure Shell) has revolutionized secure remote access. UDP SSH harnesses the power of UDP, a connectionless protocol, to establish secure communication channels with remarkable speed and efficiency, making it an ideal solution for applications demanding real-time data transfer and low latency.
This comprehensive guide delves into the intricacies of UDP SSH, exploring its benefits, drawbacks, configuration nuances, security considerations, and troubleshooting techniques. We will also delve into advanced features, cloud applications, and future prospects of this innovative protocol.
UDP SSH Overview
UDP SSH, or User Datagram Protocol Secure Shell, is a secure remote access protocol that utilizes the User Datagram Protocol (UDP) instead of the more common Transmission Control Protocol (TCP). This shift from TCP to UDP offers unique advantages and drawbacks, making UDP SSH a suitable choice for specific use cases.UDP
is a connectionless protocol, unlike TCP, which is connection-oriented. This distinction means that UDP SSH does not establish a persistent connection between the client and server, as is the case with TCP SSH. Instead, UDP SSH transmits data in the form of datagrams, which are independent units of information.
Benefits of UDP SSH
The use of UDP in SSH brings several benefits:
-
- -*Lower Latency
UDP has lower latency compared to TCP, making it ideal for real-time applications such as remote desktop sessions and interactive gaming.
- -*Lower Latency
-*Reduced Overhead
UDP has less overhead than TCP, as it does not require the establishment and maintenance of a connection. This can result in improved performance, especially in scenarios with limited bandwidth.
-*Broadcast Support
UDP supports broadcasting, which allows for the transmission of data to multiple recipients simultaneously. This can be useful for certain applications, such as remote monitoring or network management.
Drawbacks of UDP SSH
While UDP SSH offers advantages, it also has some drawbacks:
-
- -*Unreliable Delivery
UDP does not guarantee the delivery of datagrams, which can lead to data loss or corruption. This unreliability can be a concern for applications that require reliable data transmission.
- -*Unreliable Delivery
-*Limited Flow Control
UDP does not have built-in flow control mechanisms like TCP, which can result in network congestion and packet loss. This can be problematic in situations with high network traffic.
-*Vulnerability to Spoofing
UDP is vulnerable to spoofing attacks, where attackers can forge the source IP address of datagrams. This can be a security risk, as it can allow unauthorized access to systems.
Configuring UDP SSH
Configuring UDP SSH involves modifying the SSH configuration file on both the server and client sides.
The configuration file typically resides at /etc/ssh/sshd_config on the server and ~/.ssh/config on the client.
Server-Side Configuration
To enable UDP SSH on the server, add the following line to the sshd_config file:
ListenAddress 0.0.0.0:2222
This line specifies that the SSH server should listen for UDP connections on all IPv4 addresses on port 2222. You can specify a different port if desired.
Additionally, you may need to adjust the following settings in the sshd_config file:
- Protocol: Set this to “2” to enable SSH version 2 only.
- Ciphers: Specify the encryption algorithms to be used for UDP SSH connections.
- MACs: Specify the message authentication codes to be used for UDP SSH connections.
Client-Side Configuration
On the client side, add the following line to the ~/.ssh/config file:
Host - Port 2222
This line specifies that the SSH client should connect to all hosts using UDP SSH on port 2222.
You can also specify additional options in the ~/.ssh/config file, such as the following:
- User: Specify the username to be used for UDP SSH connections.
- IdentityFile: Specify the private key file to be used for UDP SSH connections.
Security Considerations
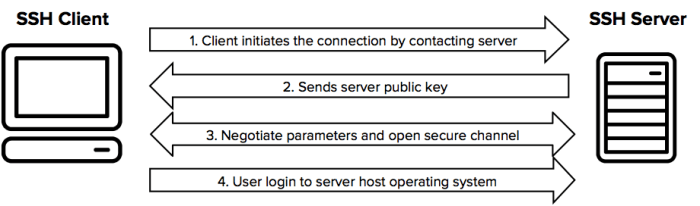
Using UDP SSH carries certain security implications that should be acknowledged and addressed for a secure connection. These include the potential for spoofing, eavesdropping, and denial-of-service (DoS) attacks.
To enhance security, it is recommended to use strong encryption algorithms, such as AES-256, and to disable weak ciphers. Additionally, it is crucial to implement firewalls to limit access to the UDP SSH port and to monitor network traffic for suspicious activity.
Best Practices
- Use strong encryption algorithms (e.g., AES-256).
- Disable weak ciphers.
- Implement firewalls to restrict access to the UDP SSH port.
- Monitor network traffic for suspicious activity.
Troubleshooting UDP SSH
UDP SSH, while generally reliable, can occasionally encounter issues. Here are some common problems and troubleshooting tips:
Connectivity Problems
- Ensure that UDP port 53 is open on both the client and server machines.
- Check if firewalls or network security policies are blocking UDP traffic.
- Verify that the client and server have matching UDP SSH configuration settings.
Authentication Issues
- Confirm that the client and server are using the same authentication methods.
- Ensure that the user credentials are correct and have sufficient privileges.
- Check if there are any issues with the SSH keys or certificates being used.
Performance Problems
- Adjust the UDP SSH packet size to optimize performance.
- Consider increasing the UDP buffer size on the client or server.
- Monitor network traffic to identify any potential bottlenecks or congestion.
Other Issues
- Check for any error messages in the SSH logs on both the client and server.
- Try restarting the SSH service on the server to resolve temporary issues.
- If the problem persists, consult the SSH documentation or seek assistance from a network administrator.
Performance Comparison
UDP SSH exhibits superior performance compared to TCP SSH, primarily due to its reduced latency and higher throughput. UDP’s connectionless nature eliminates the need for establishing and maintaining connections, resulting in significantly faster response times.
Factors Affecting Performance
Several factors influence the performance of UDP SSH:
- Network Conditions: High network latency and packet loss can impact UDP SSH performance.
- Server Configuration: Optimizing the SSH server’s buffer sizes and thread pools can enhance throughput.
- Client Configuration: Using a low latency SSH client can improve response times.
Optimization Tips
- Enable UDP Forwarding: Configure routers and firewalls to allow UDP traffic on the SSH port.
- Use a Fast SSH Client: Consider using SSH clients specifically designed for UDP, such as Mosh or tmate.
- Tune Server Parameters: Adjust the server’s buffer sizes and thread pool settings to match the network conditions.
Use Cases for UDP SSH
UDP SSH excels in scenarios where speed, efficiency, and reliability are paramount. Its unique characteristics make it an ideal choice for various applications, including:
Interactive Shell Access
UDP SSH enables seamless interactive shell access over UDP, providing a responsive and efficient experience for remote administration and troubleshooting.
Secure File Transfers
UDP SSH can securely transfer files over UDP, leveraging its low latency and fast data transfer capabilities to enhance file sharing efficiency.
Remote Desktop Applications
UDP SSH supports remote desktop applications, enabling users to access graphical user interfaces (GUIs) remotely with minimal lag and improved responsiveness.
Network Monitoring and Management
UDP SSH facilitates network monitoring and management tasks, allowing administrators to remotely access and control network devices with enhanced speed and efficiency.
Industrial Automation
UDP SSH finds application in industrial automation systems, where reliable and real-time communication is crucial for controlling and monitoring industrial processes.
Alternatives to UDP SSH
UDP SSH offers several advantages, but it may not be suitable for all scenarios. Several alternative protocols and techniques can be considered:
TCP SSH
TCP SSH is the traditional SSH implementation that uses TCP as the transport protocol. Compared to UDP SSH, TCP SSH:
-*Advantages
More reliable due to TCP’s connection-oriented nature
-
- Wider compatibility with firewalls and network devices
-*Disadvantages
Higher latency due to TCP’s three-way handshake and retransmission mechanisms
Not as efficient as UDP SSH for real-time applications
WireGuard
WireGuard is a modern VPN protocol designed for high performance and low overhead. It offers several advantages over UDP SSH:
-*Advantages
Extremely fast and efficient, making it suitable for real-time applications
Simpler configuration and management compared to UDP SSH
-
- Open-source and actively developed
-*Disadvantages
May not be as widely supported as SSH
Lacks some of the advanced features of SSH, such as port forwarding
mDNS
Multicast Domain Name System (mDNS) is a protocol used for discovering services and devices on a local network. It can be used as an alternative to UDP SSH for certain scenarios:
-*Advantages
Simple and easy to configure
No need for a dedicated server or complex setup
-
- Automatically discovers services and devices on the network
-*Disadvantages
Limited functionality compared to SSH
Not suitable for remote access or secure connections over the internet
Advanced UDP SSH Features
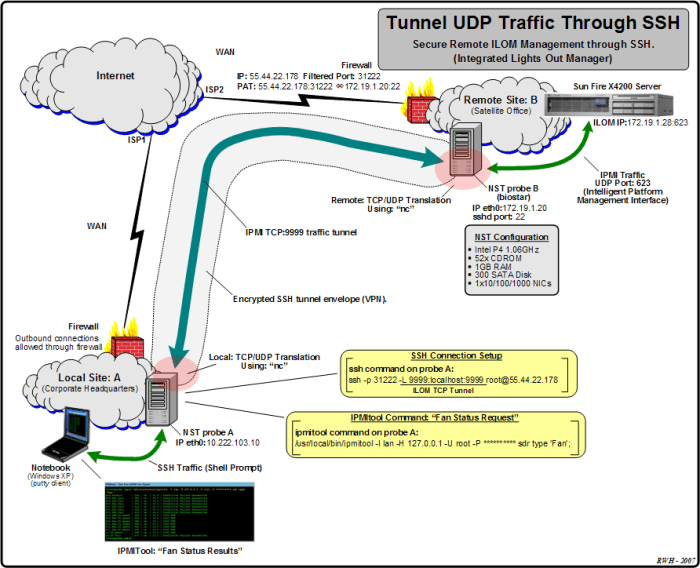
UDP SSH offers advanced features that enhance its security and performance. These features include:
- Encryption Algorithms: UDP SSH supports a wide range of encryption algorithms, including AES-256, AES-192, AES-128, and ChaCha20-Poly1305. These algorithms provide strong encryption to protect data in transit from eavesdropping and unauthorized access.
- Key Exchange Methods: UDP SSH utilizes various key exchange methods to establish a secure connection. These methods include Diffie-Hellman, ECDH, and Ed25519. These methods provide perfect forward secrecy, ensuring that compromised keys cannot be used to decrypt past sessions.
Additional Features
- Port Forwarding: UDP SSH supports port forwarding, allowing users to securely access remote services on a private network from a public network.
- Dynamic Port Allocation: UDP SSH can dynamically allocate ports, reducing the risk of port conflicts and improving connection reliability.
- Packet Fragmentation: UDP SSH can fragment large packets into smaller fragments, improving performance over networks with limited bandwidth or high latency.
UDP SSH in the Cloud
UDP SSH is gaining popularity in cloud computing environments due to its advantages in performance and scalability. Cloud providers such as AWS, Azure, and Google Cloud Platform offer support for UDP SSH, making it easy to configure and manage.
Configuring UDP SSH in the Cloud
Configuring UDP SSH in the cloud is similar to configuring it on-premises. However, there are some additional considerations to keep in mind:
-
- -*Firewall rules
Ensure that the cloud firewall rules allow UDP traffic on port 443.
- -*Firewall rules
-*Security groups
Create security groups that allow UDP traffic from specific IP addresses or ranges.
-*Instance configuration
Configure the cloud instance to listen for UDP traffic on port 443.
Future of UDP SSH
UDP SSH is a relatively new technology, and its future is still uncertain. However, there are a number of factors that suggest that it has the potential to become a widely used protocol.One
of the biggest advantages of UDP SSH is its speed. UDP is a connectionless protocol, which means that it does not require a three-way handshake to establish a connection. This makes it much faster than TCP, which is a connection-oriented protocol.Another
advantage of UDP SSH is its security. UDP SSH uses the same encryption algorithms as TCP SSH, but it is more difficult to attack because it does not require a connection. This makes it a more secure option for remote access.Finally,
UDP SSH is also more efficient than TCP SSH. UDP SSH does not need to maintain a connection, so it uses less bandwidth and resources. This makes it a more efficient option for use in low-bandwidth environments.Overall, UDP SSH has a number of advantages over TCP SSH.
It is faster, more secure, and more efficient. As a result, it is likely to become a more widely used protocol in the future.
Closure
UDP SSH has emerged as a game-changer in network connectivity, offering a compelling blend of speed, security, and versatility. Its ability to traverse firewalls, optimize performance for latency-sensitive applications, and provide robust encryption makes it an indispensable tool for network administrators and IT professionals alike.
As technology continues to evolve, UDP SSH is poised to play an increasingly prominent role in shaping the future of secure and efficient network communication.