SSH.SSHSlowdns.com – In the ever-evolving landscape of networking, User Datagram Protocol (UDP) servers have emerged as a powerful tool for real-time and efficient data transfer. However, the inherent nature of UDP, being a connectionless protocol, poses security challenges. This is where Secure Shell (SSH) comes into play, offering a robust encryption layer to protect UDP connections.
This guide delves into the intricacies of UDP server SSH integration, exploring its benefits, implementation methods, and best practices. We’ll uncover the potential security risks associated with UDP servers and provide strategies for mitigating them using SSH. Furthermore, we’ll discuss performance optimization techniques and industry standards, ensuring your UDP server operates at peak efficiency.
UDP Server Overview
UDP (User Datagram Protocol) is a connectionless network protocol that operates on the Internet Protocol (IP) network layer. Unlike TCP, which establishes a connection before transmitting data, UDP sends data in small packets called datagrams without any prior connection setup.
This makes UDP faster and more efficient for certain types of applications, such as online gaming and video streaming, where real-time data transfer is crucial.
A UDP server is a computer program that listens for incoming UDP packets on a specific port. When a UDP packet arrives, the server processes the data and sends a response back to the client. UDP servers are often used in applications where low latency and high throughput are more important than reliability, as UDP does not guarantee that all packets will be delivered or received in the correct order.
UDP Server Architecture
A UDP server typically consists of the following components:
- Socket: A socket is an endpoint in a communication network. UDP servers create a socket and bind it to a specific port, which is used to identify the server.
- Buffer: A buffer is a temporary storage area used to store incoming and outgoing data. UDP servers use buffers to store incoming UDP packets until they can be processed.
- Packet Handler: The packet handler is a function or thread that processes incoming UDP packets. The packet handler typically extracts the data from the packet and passes it to the appropriate application.
- Response Generator: The response generator is a function or thread that generates responses to incoming UDP packets. The response generator typically creates a new UDP packet and sends it back to the client.
SSH Integration
SSH (Secure Shell) is a secure network protocol that can be used to secure UDP connections. SSH encrypts all traffic between the client and the server, making it impossible for eavesdroppers to intercept the data.
There are several benefits to using SSH with UDP servers. First, SSH provides strong encryption, which makes it difficult for attackers to intercept and decrypt the data. Second, SSH provides authentication, which ensures that only authorized users can access the server.
Third, SSH provides data integrity, which ensures that the data is not tampered with in transit.
Benefits of Using SSH with UDP Servers
- Provides strong encryption
- Provides authentication
- Provides data integrity
Implementation Methods
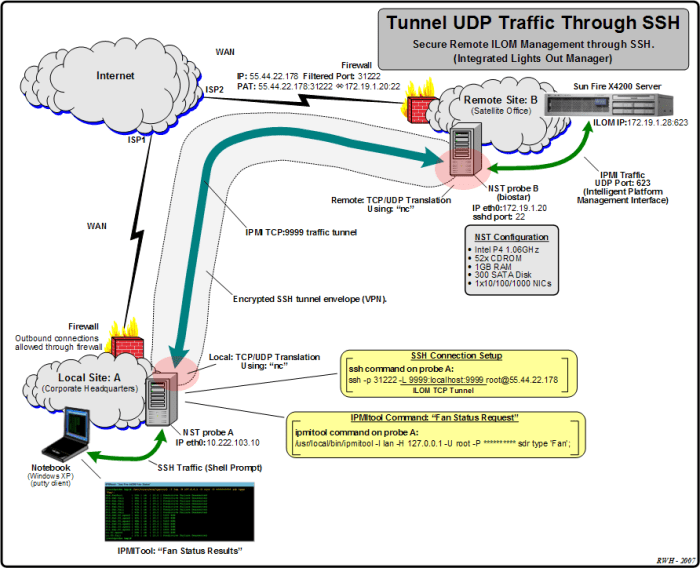
Implementing a UDP server with SSH encryption involves utilizing a library or framework that supports SSH encryption. This allows for secure communication between the server and client.
Using OpenSSH
OpenSSH is a widely used SSH implementation that can be utilized to create a UDP server with SSH encryption. Here’s a code example in Python using the paramiko library:
“`pythonimport paramiko# Create an SSH server socketsock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM)sock.bind((‘localhost’, 22))# Create an SSH transport and authenticate the clienttransport = paramiko.Transport(sock)transport.start_server(server=paramiko.ServerInterface())client = transport.accept()# Handle UDP data exchangewhile True: data, addr = client.recvfrom(1024)
client.sendto(data, addr)“`
Using SSH2 Library
The SSH2 library is another option for implementing SSH encryption in a UDP server. Here’s a code example in C:
“`c#include int main() // Initialize the SSH2 library ssh2_init(); // Create an SSH2 session ssh2_session
session = ssh2_session_init();
// Set the session parameters ssh2_session_set_hostname(session, “localhost”); ssh2_session_set_port(session, 22); ssh2_session_set_username(session, “username”); ssh2_session_set_password(session, “password”); // Start the SSH session if (ssh2_session_startup(session, SSH2_SESS_SERVER) != 0) // Error handling // Handle UDP data exchange while (1) // Receive data from the client int len = ssh2_session_read_from_channel(session, channel, buffer, sizeof(buffer)); // Send data to the client ssh2_session_write_to_channel(session, channel, buffer, len); // Close the SSH session ssh2_session_free(session); // Clean up the SSH2 library ssh2_finalize(); return 0;“`
Security Considerations
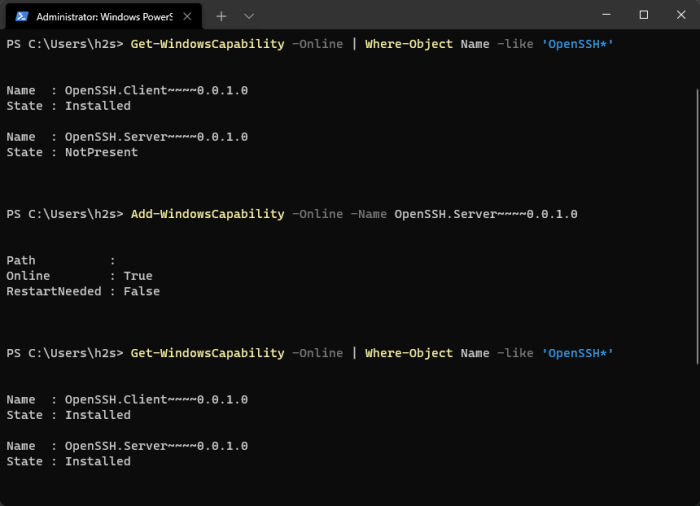
UDP servers, while offering performance advantages, can present unique security challenges. Understanding and addressing these risks is crucial for securing UDP-based applications.SSH integration provides a secure channel for UDP traffic, mitigating potential vulnerabilities. However, it’s essential to implement additional security measures to enhance the overall protection of UDP servers.
Performance Optimization
UDP servers can exhibit unique performance characteristics compared to TCP-based servers. Understanding these characteristics is crucial for optimizing performance. UDP servers handle data in datagrams, which are independent units of data transmission. This can lead to lower latency and higher throughput compared to TCP, which establishes a connection-oriented session.
However, UDP lacks mechanisms for error correction and flow control, which can impact reliability and performance.To optimize UDP server performance, consider the following tips:
Datagrams Size
The size of UDP datagrams can significantly impact performance. Smaller datagrams may result in lower latency, but can also lead to increased overhead due to the larger number of packets required to transmit the same amount of data. Conversely, larger datagrams can reduce overhead but may increase latency due to potential fragmentation and reassembly.
Buffering
Proper buffering strategies can improve UDP server performance. Input and output buffers help absorb bursts of data and reduce the impact of temporary network congestion. The size and management of these buffers should be carefully tuned to match the expected traffic patterns and network conditions.
Thread Management
UDP servers often handle multiple concurrent connections, making thread management critical for performance. The number of threads and their scheduling strategy should be optimized to minimize contention and maximize throughput. Consider using thread pools or asynchronous I/O techniques to improve scalability and efficiency.
Error Handling
UDP does not provide built-in mechanisms for error correction or flow control. Therefore, UDP servers should implement custom error handling strategies to detect and recover from lost or corrupted packets. This may involve using checksums, retransmission mechanisms, or alternative protocols for reliable data transfer.
Network Optimization
Optimizing the underlying network infrastructure can also improve UDP server performance. Techniques such as traffic shaping, QoS prioritization, and load balancing can help ensure that UDP traffic is handled efficiently and with minimal congestion.
Error Handling
Error handling is a crucial aspect of UDP server operations. Various errors can occur during server operation, including network connectivity issues, invalid data packets, and resource exhaustion. To ensure reliable and robust server operation, it’s essential to implement effective error handling strategies.
When an error occurs, the UDP server should gracefully handle the situation and provide meaningful error messages or status codes to the client. This allows the client to understand the cause of the error and take appropriate actions, such as retrying the request or providing alternative data.
Error Detection
The UDP server should employ mechanisms to detect errors in data packets received from clients. Common error detection methods include:
- Checksum Verification: Each data packet can include a checksum field that is calculated based on the packet’s contents. The server can verify the checksum upon receiving the packet and reject it if the checksum is incorrect, indicating data corruption.
- Sequence Number Checking: UDP packets can include a sequence number to ensure that packets are received in the correct order. The server can maintain a sequence number tracker and reject packets with incorrect sequence numbers.
Error Handling Strategies
Once errors are detected, the UDP server should implement appropriate error handling strategies to mitigate the impact of errors and ensure continued server operation. Common error handling strategies include:
- Logging: Log error messages and details, including the time of occurrence, the source of the error (e.g., client IP address), and the error code or description.
- Error Codes and Messages: Provide meaningful error codes and messages to the client, allowing them to understand the cause of the error and take appropriate actions.
- Automatic Retries: In some cases, the UDP server can automatically retry failed requests to improve reliability.
- Server Restart: In severe cases, such as resource exhaustion or critical errors, the UDP server may need to be restarted to recover.
Application Examples
UDP servers with SSH are commonly used in various real-world applications, offering advantages in specific scenarios:
- Secure Remote Access: SSH tunneling over UDP provides a secure channel for remote access to servers or devices, enabling secure file transfers, command execution, and remote desktop sessions.
- Streaming Media: UDP is often used for streaming media applications, such as live video or audio, due to its low latency and ability to handle fluctuating bandwidth.
- Network Monitoring: UDP servers are employed in network monitoring systems to collect performance metrics, such as packet loss and latency, providing real-time insights into network health.
- Gaming: UDP is commonly used in multiplayer online games to facilitate real-time communication and synchronization between players, ensuring smooth gameplay and minimal lag.
While UDP servers offer benefits in these scenarios, it’s important to note their limitations:
- Reliability: UDP is an unreliable protocol, meaning packets may be lost or reordered during transmission. This can be a disadvantage in applications where data integrity is crucial.
- Security: UDP does not provide built-in encryption or authentication, making it susceptible to eavesdropping and spoofing attacks. SSH integration helps address these concerns, but additional security measures may be necessary.
Overall, UDP servers with SSH provide a valuable solution for applications requiring secure and low-latency communication, but their limitations should be carefully considered when selecting the appropriate protocol for specific scenarios.
Industry Standards
Adhering to industry standards and best practices is crucial for developing robust and secure UDP servers. These standards provide guidelines for implementation, ensuring interoperability, security, and reliability.
Compliance with relevant standards is often a requirement for certification and accreditation, which can enhance the credibility and trustworthiness of your UDP server.
Compliance Requirements
- IETF RFCs: The Internet Engineering Task Force (IETF) publishes Request for Comments (RFCs) that define protocols and standards for internetworking. RFCs 768 (User Datagram Protocol) and 1122 (Requirements for Internet Hosts
— Communication Layers) are essential for UDP server implementation. - ISO/IEC 27001: This international standard provides a framework for implementing an information security management system (ISMS). It includes requirements for secure network and system administration, including the use of UDP servers.
- PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) is a set of security requirements for organizations that process, store, or transmit payment card data. It includes requirements for secure network configuration and management, which may involve the use of UDP servers.
Troubleshooting Techniques
Troubleshooting UDP servers involves identifying and resolving issues that may arise during their operation. These issues can range from connection problems to data transmission errors. To effectively troubleshoot UDP servers, it is essential to understand the underlying protocols and network configurations involved.
One common issue with UDP servers is connection problems. This can be caused by incorrect port configuration, firewall blocking, or network connectivity issues. To resolve these issues, verify that the server is listening on the correct port and that the firewall is not blocking the connection.
Additionally, check the network connectivity to ensure that there are no issues with the network infrastructure.
Tools and Resources
Several tools and resources are available to assist in troubleshooting UDP servers. These include:
- Packet sniffers: Tools like Wireshark can be used to capture and analyze network traffic, helping to identify issues with UDP packets.
- Network diagnostic tools: Tools like ping and traceroute can be used to test network connectivity and identify any issues with the network infrastructure.
- Server logs: UDP servers often generate logs that can provide valuable information about errors and connection issues.
Future Trends
UDP server technology is rapidly evolving, driven by advancements in networking and cloud computing. Here are some emerging trends and future projections:
The rise of 5G and edge computing will enable UDP servers to handle even more data at faster speeds, with lower latency. This will open up new possibilities for real-time applications, such as streaming video, gaming, and virtual reality.
Cloud-based UDP Servers
Cloud-based UDP servers are becoming increasingly popular, as they offer scalability, reliability, and cost-effectiveness. Cloud providers can offer UDP servers with dedicated resources and high-performance networks, which can be scaled up or down as needed.
Security Enhancements
Security is a top priority for UDP servers, and new technologies are being developed to protect against attacks. These technologies include encryption, authentication, and intrusion detection.