In the realm of network security, SSH (Secure Shell) has long been a trusted protocol for establishing secure remote connections. However, with the increasing demand for faster and more efficient network protocols, UDP (User Datagram Protocol) custom SSH has emerged as a promising alternative to traditional SSH.
UDP custom SSH leverages the advantages of UDP, a connectionless protocol known for its low latency and high throughput, to provide enhanced performance and security for network communications. By tailoring UDP to the specific requirements of SSH, this custom implementation offers a unique set of benefits that make it an attractive choice for a wide range of applications.
UDP Custom SSH Configuration
Customizing SSH over UDP involves modifying the configuration settings of the SSH server and client to utilize the UDP protocol instead of the default TCP.
Configuring the SSH Server
- Edit the SSH server configuration file (/etc/ssh/sshd_config).
- Locate the “Protocol” directive and change it to “Protocol 2 1”.
- Restart the SSH server.
Configuring the SSH Client
- Edit the SSH client configuration file (~/.ssh/config).
- Add the following line: “Protocol 2 1”.
- Connect to the SSH server using the modified configuration.
By following these steps, you can configure UDP custom SSH, allowing for faster and more efficient SSH connections in certain scenarios.
Benefits of Using UDP Custom SSH
UDP custom SSH offers several advantages over traditional SSH, enhancing security, performance, and reliability.
Security
UDP custom SSH is more secure than traditional SSH due to its use of UDP, which is a connectionless protocol. This means that each packet is treated independently, making it more difficult for attackers to intercept and exploit data. Additionally, UDP custom SSH supports strong encryption algorithms, ensuring the confidentiality and integrity of transmitted data.
Performance
UDP custom SSH is significantly faster than traditional SSH, as it does not require the establishment of a TCP connection. This eliminates the overhead associated with TCP handshakes, resulting in reduced latency and improved throughput.
Reliability
UDP custom SSH is more reliable than traditional SSH, as it is not susceptible to packet loss. UDP packets are simply discarded if they are not received, and the sender is not notified of the loss. This makes UDP custom SSH ideal for applications that require reliable data transmission over unreliable networks.
Security Considerations
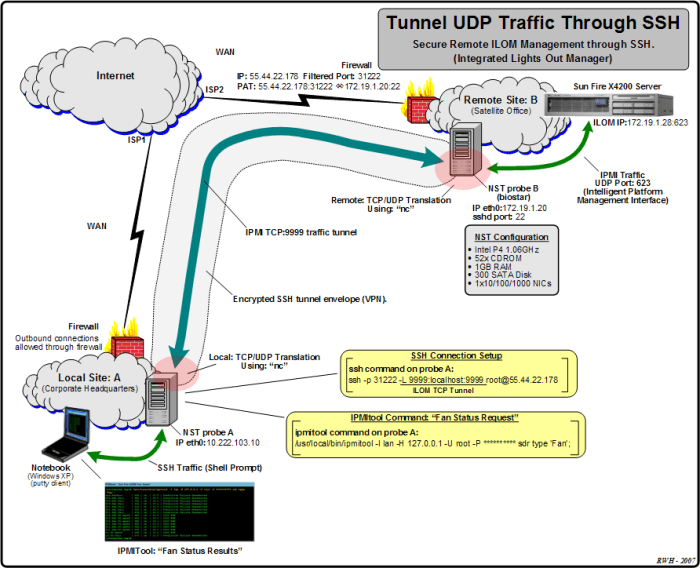
UDP custom SSH poses certain security risks that require careful consideration. The primary concern lies in the fact that UDP is a connectionless protocol, meaning that it lacks the built-in mechanisms for error detection and recovery present in TCP. This can potentially lead to data loss or corruption during transmission.
Additionally, UDP’s stateless nature makes it vulnerable to spoofing attacks, where malicious actors can impersonate legitimate sources to gain unauthorized access.To mitigate these risks, it is crucial to implement robust security measures. One effective approach is to use a combination of encryption and authentication mechanisms.
Encryption ensures the confidentiality of data transmitted over the connection, while authentication verifies the identity of both parties involved in the communication. Additionally, implementing intrusion detection and prevention systems (IDS/IPS) can help detect and block malicious activities. Regular security audits and updates are also essential for maintaining a secure connection.
Data Protection
Data protection is paramount when using UDP custom SSH. Employing strong encryption algorithms, such as AES-256 or ChaCha20, is crucial to safeguard data from unauthorized access. Additionally, utilizing message authentication codes (MACs) ensures the integrity of data by detecting any unauthorized modifications during transmission.
Authentication
Robust authentication mechanisms are essential to prevent unauthorized access. Implementing two-factor authentication (2FA) adds an extra layer of security by requiring users to provide additional credentials, such as a one-time password (OTP) or a hardware token, in addition to their username and password.
Network Security
Implementing firewalls and intrusion detection systems (IDS) is vital to protect the network from unauthorized access and malicious activities. Firewalls can restrict access to specific ports and IP addresses, while IDS can detect and block suspicious traffic patterns. Additionally, using a virtual private network (VPN) can provide an additional layer of security by encrypting traffic and obscuring the user’s IP address.
Performance Optimization
Optimizing UDP custom SSH for maximum performance involves minimizing latency, increasing throughput, and enhancing overall efficiency. Techniques to achieve this include:
Latency Reduction
- Using a high-performance network with low latency and jitter.
- Minimizing the number of hops between the client and server.
- Tuning the operating system’s network stack for performance.
- Configuring the SSH server to use fast encryption algorithms and key exchange methods.
Throughput Optimization
- Increasing the packet size to reduce protocol overhead.
- Using multiplexing to send multiple SSH sessions over a single UDP connection.
- Enabling compression to reduce the size of data packets.
- Optimizing the network buffer size to accommodate larger packets and minimize packet loss.
Efficiency Improvements
- Enabling keepalive packets to maintain the connection and reduce retransmissions.
- Using a custom SSH client that is optimized for UDP performance.
- Monitoring and analyzing network traffic to identify and resolve performance bottlenecks.
Compatibility and Interoperability
UDP custom SSH maintains compatibility across various operating systems, including Linux, Windows, and macOS. Its implementation ensures seamless interoperability between devices using UDP custom SSH, allowing for secure communication regardless of the underlying operating system.
Ensuring Interoperability
- Use Standardized Protocols: Adhere to industry-standard protocols, such as IETF RFC 4253, to guarantee interoperability among different implementations.
- Test and Validate: Conduct thorough testing and validation processes to verify interoperability between devices using UDP custom SSH.
- Update Regularly: Keep software and firmware up to date with the latest security patches and updates to ensure compatibility with evolving standards.
Troubleshooting Common Issues
When using UDP custom SSH, several common issues may arise. Understanding these issues and their solutions is crucial for effective troubleshooting.
Connection Issues
If you encounter connection problems, verify the following:
- Confirm that the UDP port used for SSH is open on both the client and server firewalls.
- Ensure that the IP addresses and ports specified in the SSH configuration files are correct.
- Check if the SSH service is running on both the client and server.
Authentication Issues
Authentication issues can occur due to incorrect credentials or configuration errors.
- Verify that the username and password or SSH key used for authentication are correct.
- Check the SSH configuration files for any incorrect settings related to authentication methods.
Performance Issues
Performance issues may arise due to network congestion or suboptimal configurations.
- Monitor network traffic to identify any bottlenecks or congestion.
- Optimize SSH configuration parameters such as packet size and encryption algorithms to improve performance.
Security Issues
Security issues can be caused by misconfigurations or vulnerabilities in the SSH implementation.
- Ensure that strong encryption algorithms are used and that SSH keys are securely managed.
- Keep the SSH software up to date to patch any known vulnerabilities.
Comparison with Other SSH Protocols
UDP custom SSH stands out from other SSH protocols like OpenSSH and SSH2 due to its unique characteristics and use cases. Let’s delve into their similarities, differences, and specific applications.
OpenSSH
OpenSSH is a widely adopted SSH implementation known for its robust security, compatibility, and flexibility. It operates over TCP and provides a secure channel for remote login, file transfer, and command execution. While OpenSSH excels in stability and widespread support, it may not be the most efficient option for latency-sensitive applications due to its TCP-based nature.
SSH2
SSH2 is an updated version of the SSH protocol that offers enhanced security features and improved performance over its predecessor, SSH1. It supports both TCP and UDP transport, providing greater flexibility in network environments. SSH2 is commonly used in modern applications that demand a balance between security and efficiency.
Use Cases and Applications
UDP custom SSH offers a versatile range of applications, extending its utility beyond traditional SSH usage. Its high performance and optimized security make it suitable for various network-based tasks.
Remote Access
UDP custom SSH enables secure remote access to servers, allowing administrators to perform maintenance, troubleshooting, and other tasks remotely. Its fast and reliable connections minimize latency, ensuring efficient and responsive remote management.
Secure File Transfer
UDP custom SSH provides a secure channel for file transfer, ensuring data integrity and confidentiality. It can be used to transfer sensitive data, such as financial records or confidential documents, across networks without compromising security.
Other Network-Based Tasks
UDP custom SSH can also be used for various other network-based tasks, such as port forwarding, tunneling, and remote execution. Its flexibility and customization options allow it to be tailored to specific requirements, making it a versatile tool for network administration and management.
Design Considerations
When designing and implementing UDP custom SSH solutions, consider the following guidelines:
- Prioritize security: Implement strong encryption algorithms and authentication mechanisms to protect against unauthorized access and data breaches.
- Optimize performance: Utilize efficient data transfer techniques, such as packet fragmentation and compression, to minimize latency and maximize throughput.
- Ensure reliability: Employ mechanisms for error detection and correction, such as checksums and retransmission, to ensure reliable data delivery.
Best Practices
Follow these best practices to enhance the security, performance, and reliability of UDP custom SSH solutions:
- Use strong encryption: Employ robust encryption algorithms, such as AES-256 or ChaCha20, to protect data in transit.
- Implement multi-factor authentication: Require multiple authentication methods, such as passwords and OTPs, to prevent unauthorized access.
- Configure firewalls: Restrict access to SSH ports and only allow connections from trusted sources.
- Monitor and log activity: Regularly review SSH logs to detect suspicious activity and identify potential security breaches.
- Keep software up to date: Apply security patches and updates promptly to address vulnerabilities.
10. Future Trends and Developments
The future of UDP custom SSH holds promising advancements that will enhance its capabilities and adoption.
Potential Advancements
* Improved Security: Ongoing research explores advancements in encryption algorithms and authentication methods to strengthen the security posture of UDP custom SSH.
Increased Performance
Innovations in network optimization techniques aim to enhance the speed and efficiency of UDP custom SSH connections.
Enhanced Compatibility
Future developments focus on broadening compatibility with diverse operating systems and devices, ensuring seamless integration.
Last Word
In summary, UDP custom SSH is a powerful tool that combines the security of SSH with the performance advantages of UDP. By optimizing network configurations, implementing security best practices, and understanding the compatibility and interoperability aspects, organizations can harness the full potential of UDP custom SSH to enhance the security and efficiency of their network communications.