ssh.sshslowdns.com – In the realm of secure remote access, the Ubuntu SSH server emerges as a formidable solution, offering a robust platform for managing and connecting to systems from afar. Its versatility and customizable nature make it an ideal choice for system administrators, network engineers, and anyone seeking secure and efficient remote connectivity.
This comprehensive guide delves into the intricacies of the Ubuntu SSH server, empowering you with the knowledge and skills to install, configure, and optimize this essential tool. From understanding its fundamental principles to implementing advanced security measures and troubleshooting common issues, we will explore every aspect of this powerful server to maximize its potential.
Introduction to Ubuntu SSH Server
Ubuntu SSH Server is a secure and versatile tool that allows remote access and management of Ubuntu systems. It utilizes the Secure Shell (SSH) protocol to establish encrypted connections between client and server machines, enabling secure file transfer, command execution, and remote administration.explanatory
paragraphSSH servers play a crucial role in modern IT infrastructure, providing secure remote access to servers, network devices, and other systems. They offer several benefits, including:
-
- -*Enhanced security
SSH employs strong encryption algorithms to protect data in transit, preventing unauthorized access and eavesdropping.
- -*Enhanced security
-*Remote administration
SSH enables administrators to manage systems remotely, eliminating the need for physical access or local logins.
-*File transfer
SSH supports secure file transfer protocols such as SFTP and SCP, allowing users to securely transfer files between remote systems.
-*Port forwarding
SSH can be used to forward ports, allowing access to specific services or applications on the remote system from the client machine.
Use Cases
SSH servers find application in various scenarios, including:
-
- -*Remote server management
Administering servers remotely, performing tasks such as software updates, configuration changes, and troubleshooting.
- -*Remote server management
-*Network device configuration
Managing network switches, routers, and other devices remotely, configuring settings and monitoring performance.
-*Secure file transfer
Transferring sensitive files between systems securely, preventing unauthorized access during transmission.
-*Remote collaboration
Enabling multiple users to access and work on a shared system remotely, facilitating collaboration and knowledge sharing.
Installation and Configuration
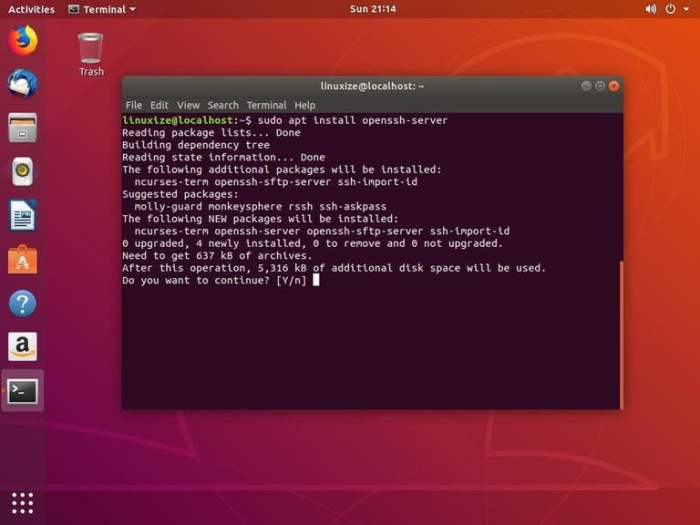
Installing and configuring an SSH server on Ubuntu is a straightforward process. Begin by updating your system’s packages:“`sudo apt update && sudo apt upgrade“`Next, install the OpenSSH server:“`sudo apt install openssh-server“`After installation, edit the SSH configuration file (/etc/ssh/sshd_config):“`sudo nano /etc/ssh/sshd_config“`Enable key-based authentication by setting “PasswordAuthentication” to “no” and “PermitRootLogin” to “without-password”.“`PasswordAuthentication
noPermitRootLogin without-password“`Restart the SSH service:“`sudo systemctl restart ssh“`
Key-based Authentication
Key-based authentication provides a more secure alternative to password authentication. Generate an SSH key pair:“`ssh-keygen
- t rsa
- b 4096
“`Copy the public key to the server:“`ssh-copy-id username@server_address“`On the server, verify that the key was added to the authorized_keys file:“`cat ~/.ssh/authorized_keys“`
Security Enhancements

Securing your SSH server is crucial to protect your system from unauthorized access and malicious attacks. Here are some best practices to enhance the security of your SSH server:
Limiting access, using strong encryption, and monitoring for suspicious activity are key measures to secure your SSH server.
Limiting Access
Restricting access to your SSH server is essential to prevent unauthorized users from gaining access to your system. Implement the following measures:
-
- Use strong passwords or SSH keys for authentication.
- Disable root login and create a separate user with limited privileges.
- Use IP-based access control lists (ACLs) to restrict access to specific IP addresses or subnets.
li>Enable two-factor authentication (2FA) for added security.
Using Strong Encryption
Employing strong encryption algorithms ensures that data transmitted over the SSH connection is protected from eavesdropping and interception:
- Use strong encryption algorithms such as AES-256 or ChaCha20-Poly1305.
- Enable SSH compression to prevent data leaks due to predictable patterns.
- Use a strong key exchange algorithm, such as ECDH or DH.
Monitoring for Suspicious Activity
Monitoring your SSH server for suspicious activity is crucial for detecting and responding to potential threats:
- Enable SSH logging to record all login attempts and other activities.
- Use log analysis tools to identify patterns and anomalies in SSH traffic.
- Set up alerts to notify you of suspicious activity, such as failed login attempts or unusual commands.
Managing SSH Connections

SSH connections are essential for managing remote servers securely. This section covers the management of SSH connections, including starting, stopping, and restarting the service, as well as connecting to remote servers using SSH commands.
Starting, Stopping, and Restarting SSH Service
To start the SSH service on Ubuntu, use the following command:
sudo systemctl start ssh
To stop the SSH service, use the following command:
sudo systemctl stop ssh
To restart the SSH service, use the following command:
sudo systemctl restart ssh
Connecting to Remote Servers using SSH
To connect to a remote server using SSH, use the following command:
ssh username@server_ip_address
Replace ‘username’ with your username on the remote server, and ‘server_ip_address’ with the IP address of the remote server.
Advanced Configuration
Beyond the basics, SSH offers a plethora of advanced configuration options to tailor the server to specific needs. These settings empower administrators to enhance security, optimize performance, and cater to unique requirements.
Customization options abound, allowing administrators to modify settings such as port forwarding, compression, and authentication methods. These advanced configurations enable fine-tuning of the SSH server to suit diverse environments and applications.
Port Forwarding
Port forwarding, a crucial aspect of SSH, enables secure tunneling of connections between remote systems. This feature allows users to access services on remote hosts as if they were running locally. Advanced configuration options provide granular control over port forwarding, allowing administrators to specify specific ports, protocols, and even dynamic forwarding for flexible access to remote resources.
Troubleshooting Common Issues
SSH servers can encounter various problems. This section will help you identify and resolve common issues, including connection problems, authentication errors, and other malfunctions.
Connection Problems
If you cannot connect to the SSH server, check the following:*
-*Firewall
Ensure that the firewall allows SSH traffic on port 22.
-
- -*Network
Verify that the network connection is stable and that the server is reachable.
- -*Network
-*SSH service
Confirm that the SSH service is running on the server.
Authentication Errors
Authentication errors occur when the client cannot authenticate with the server. Common causes include:*
-*Incorrect credentials
Ensure that the username and password are correct.
-
- -*Disabled account
Check if the user account is disabled or locked.
- -*Disabled account
-*Public key mismatch
If using public key authentication, verify that the public key is correctly added to the server.
Other Malfunctions
Other malfunctions may arise, such as:*
-*Slow performance
Optimize the SSH configuration for performance by adjusting parameters like compression and cipher algorithms.
-
- -*Security breaches
Monitor the SSH logs for suspicious activity and implement additional security measures as needed.
- -*Security breaches
-*Failed password changes
Reset the password through alternative methods, such as using the recovery console.
By following these troubleshooting steps, you can effectively diagnose and resolve common SSH server issues, ensuring secure and reliable remote access.
Integrating with Other Services
Integrating the SSH server with other services enhances security and functionality. Firewalls restrict unauthorized access, VPNs provide secure remote access, and authentication systems verify user identities.
Firewall Integration
Integrating with firewalls allows granular control over network access. Firewalls can block unauthorized IP addresses, limit port access, and monitor network traffic. This integration enhances security by preventing malicious actors from exploiting vulnerabilities.
VPN Integration
Integrating with VPNs provides secure remote access to the SSH server. VPNs establish encrypted tunnels between devices, allowing remote users to access the server as if they were on the local network. This integration is beneficial for employees working remotely or accessing sensitive data from external locations.
Authentication System Integration
Integrating with authentication systems centralizes user authentication and authorization. Authentication systems verify user identities through various methods, such as passwords, biometrics, or two-factor authentication. This integration enhances security by preventing unauthorized access and reducing the risk of brute-force attacks.
Performance Optimization
Optimizing the performance of an SSH server is crucial to ensure seamless connections and efficient data transfer. By implementing the following tips, you can enhance the speed and reliability of your SSH service:
Tune SSH settings
Adjust the SSH configuration file (/etc/ssh/sshd_config) to optimize parameters such as the cipher algorithm, compression, and maximum number of connections.
Enable SSH compression
Enabling compression reduces the size of data transmitted over the SSH connection, improving transfer speeds, especially over low-bandwidth networks.
Implement SSH caching
Caching mechanisms, such as the use of a reverse proxy or SSHFS, can store frequently accessed files locally, reducing the need for repeated retrieval from the remote server and enhancing performance.
Use fast ciphers and key exchange algorithms
Opt for efficient ciphers like AES-256-GCM and key exchange algorithms like ECDH (Elliptic Curve Diffie-Hellman) to minimize computational overhead and improve connection speeds.
Disable unnecessary services
If certain SSH services are not required, disable them to reduce the server’s resource consumption and improve performance.
Monitor SSH performance
Regularly monitor SSH performance metrics, such as connection times and data transfer rates, to identify and address any potential bottlenecks or performance issues.
Caching Mechanisms
Caching mechanisms play a vital role in improving SSH performance by storing frequently accessed files locally, reducing the need for repeated retrieval from the remote server. Here are some commonly used caching mechanisms:
SSHFS (SSH File System)
SSHFS mounts a remote directory as a local file system, allowing users to access remote files as if they were stored locally, reducing latency and improving performance.
Reverse proxy
A reverse proxy server, such as nginx or Apache, can cache frequently requested SSH connections, reducing the load on the SSH server and improving response times.
Remote Access and Management
SSH is a powerful tool that allows you to remotely access and manage Ubuntu systems securely over a network. It provides a secure channel for executing commands, transferring files, and performing system administration tasks.
With SSH, you can perform various tasks on remote Ubuntu systems, including:
File Transfers
- Transferring files to and from remote systems using commands like scp and sftp.
- Synchronizing files and directories between local and remote systems using rsync.
System Updates
- Updating system packages and software using apt-get or apt update/upgrade commands.
- Installing new software and applications remotely.
Troubleshooting
- Diagnosing and resolving system issues by accessing logs and running diagnostic commands.
- Remotely monitoring system performance and resource usage.
Comparison with Other SSH Servers
Ubuntu SSH server is a powerful and versatile SSH server that offers a wide range of features and options. However, it is not the only SSH server available. Other popular SSH servers include OpenSSH and Dropbear.
Each SSH server has its own advantages and disadvantages. The best choice for a particular use case will depend on the specific requirements of that use case.
OpenSSH
OpenSSH is the most popular SSH server in the world. It is a mature and stable server that offers a wide range of features and options. OpenSSH is also very well documented and supported.
Advantages of OpenSSH:
- Mature and stable
- Wide range of features and options
- Well documented and supported
Disadvantages of OpenSSH:
- Can be complex to configure
- Not as lightweight as some other SSH servers
Dropbear
Dropbear is a lightweight SSH server that is designed for embedded systems and other resource-constrained environments. Dropbear is very small and efficient, and it offers a basic set of features.
Advantages of Dropbear:
- Lightweight and efficient
- Easy to configure
- Suitable for embedded systems and other resource-constrained environments
Disadvantages of Dropbear:
- Limited feature set
- Not as well documented and supported as OpenSSH
Choosing the Right SSH Server
The best SSH server for a particular use case will depend on the specific requirements of that use case. If you need a mature and stable server with a wide range of features and options, then OpenSSH is a good choice.
If you need a lightweight and efficient server for an embedded system or other resource-constrained environment, then Dropbear is a good choice.