Secure Shell (SSH) is a vital protocol for remote server management and secure file transfer. Ensuring that the SSH server is running smoothly is crucial for maintaining system accessibility and security. This guide will provide a comprehensive overview of how to check if the SSH server is running on Ubuntu, covering basic and advanced methods, firewall configuration, server configuration, troubleshooting, automation, security considerations, performance optimization, remote access, and real-world use cases.
Understanding how to check the SSH server status is essential for system administrators and anyone responsible for managing remote servers. This guide will equip you with the knowledge and techniques to effectively monitor and maintain the SSH server, ensuring secure and reliable remote access.
Basic SSH Server Check
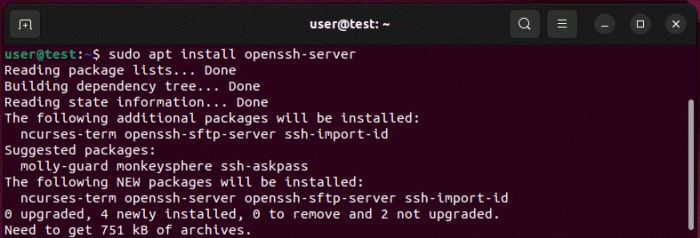
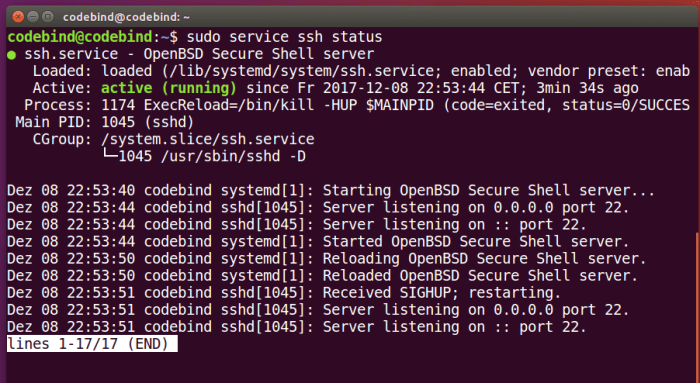
To verify if the SSH server is active, you can utilize the “systemctl” command. This command provides a convenient method for managing system services.
The syntax for checking the SSH server status is as follows:
systemctl status sshd
Upon executing this command, you will receive output similar to the example below:
● sshd.service
- OpenSSH server
Loaded: loaded (/lib/systemd/system/sshd.service; enabled; vendor preset: enabled)
Active: active (running) since Wed 2023-03-08 14:37:23 UTC; 11min ago
Docs: man:sshd(8)
https://www.openssh.com/
Main PID: 1411 (sshd) Tasks: 1 (limit: 11514) Memory: 2.3M CPU: 34ms CGroup: /system.slice/system-sshd.slice/sshd.service ├─1411 /usr/sbin/sshd -D └─1440 /usr/sbin/sshd -D
The output includes essential information about the SSH server’s status.
The “Active: active (running)” line indicates that the server is currently operational. Other details provided include the time since the server was started, the main process ID (PID), and resource usage.
In case the SSH server is not running, the output will display “Active: inactive (dead)” instead.
Variations for Different Systemd Versions
Depending on the version of systemd installed on your system, there might be slight variations in the syntax of the systemctl command. For instance, in older versions of systemd, you may need to use “service” instead of “systemctl”:
service ssh status
Advanced SSH Server Check
In addition to “systemctl”, you can also use the “ss” command to check the status of the SSH server. This command provides more detailed information about network connections, including the status of SSH connections.
Filtering the Output
To filter the output of “ss” and display only information related to SSH, use the following command:
ss -ant | grep ssh
This command will display a list of all SSH connections, including the source and destination addresses, the port numbers, and the connection status.
Advantages and Disadvantages of Using “ss” Over “systemctl”
- Advantages:
- Provides more detailed information about network connections.
- Can be used to filter the output to display only relevant information.
- Disadvantages:
- May be more difficult to use for beginners.
- Does not provide as much information about the SSH service itself.
Firewall Configuration
In addition to the SSH server, the firewall also plays a crucial role in determining whether incoming SSH connections are allowed. The firewall acts as a gatekeeper, controlling which network ports are accessible from the outside world.
Checking SSH Port Status
To verify if the SSH port (typically port 22) is open in the firewall, you can use the following commands:
- ufw:
sudo ufw status | grep 22 - firewalld:
sudo firewall-cmd
--zone=public
--list-ports | grep 22
If the output of these commands shows that port 22 is open or allowed, then SSH connections can pass through the firewall.
Implications of Closed SSH Port
If the SSH port is closed or blocked in the firewall, incoming SSH connections will be denied. This can have the following consequences:
- Remote access to the server via SSH will not be possible.
- Automated tasks and scripts that rely on SSH may fail.
- Troubleshooting and maintenance tasks that require SSH access may become more difficult.
Therefore, it is essential to ensure that the SSH port is open in the firewall when SSH access is required.
Server Configuration
The SSH server configuration file is typically located at /etc/ssh/sshd_config. This file contains various settings that control the behavior of the SSH server, including whether it is enabled or disabled.
To modify the configuration, you can use a text editor such as nano or vi. Once you have opened the file, you can search for the following settings:
Enable or Disable SSH Server
- PermitRootLogin: This setting controls whether root login is allowed. By default, it is set to “no”, which means that root login is disabled.
- PasswordAuthentication: This setting controls whether password authentication is allowed. By default, it is set to “yes”, which means that password authentication is enabled.
- ChallengeResponseAuthentication: This setting controls whether challenge-response authentication is allowed. By default, it is set to “no”, which means that challenge-response authentication is disabled.
To enable or disable the SSH server, you can simply change the value of the PermitRootLogin setting to “yes” or “no”.
Troubleshooting
Troubleshooting common issues that prevent the SSH server from running is essential to maintain secure and reliable remote access. Identifying the root cause of these issues allows for timely resolution and prevents further disruptions.
Common Issues
Some common issues that can disrupt SSH server functionality include:
Incorrect SSH configuration
Misconfigurations in the SSH configuration file (/etc/ssh/sshd_config) can lead to the server failing to start or preventing connections.
Firewall blocking
Firewall rules may inadvertently block incoming SSH connections, restricting access to the server.
Port conflicts
SSH may fail to start if another service is already using port 22, the default SSH port.
Insufficient permissions
The SSH server requires specific file and directory permissions to function correctly. Incorrect permissions can prevent the server from starting or accessing necessary resources.
System resource exhaustion
Excessive system load or resource consumption can hinder the SSH server’s ability to operate smoothly.
Possible Solutions
Addressing these issues involves a combination of service restarts, configuration adjustments, and system troubleshooting:
Restart SSH service
Restarting the SSH service can resolve temporary glitches or configuration errors. Use the command ‘sudo systemctl restart ssh’ to restart the service.
Check SSH configuration
Review the SSH configuration file (/etc/ssh/sshd_config) to ensure correct settings, such as the SSH port, permitted ciphers, and authentication methods.
Configure firewall
Adjust firewall rules to allow incoming SSH connections on port 22. Use commands like ‘sudo ufw allow 22’ or ‘sudo iptables
-
- A INPUT
- p tcp
- -dport 22
- j ACCEPT’ to open the port.
Verify permissions
Ensure that the SSH server files and directories have the correct permissions. Use commands like ‘sudo chown root:root /etc/ssh’ and ‘sudo chmod 755 /etc/ssh’ to set appropriate permissions.
Monitor system resources
Monitor system resources, such as CPU usage, memory utilization, and disk space, to identify potential bottlenecks that may impact SSH server performance.
Additional Support
If the troubleshooting steps do not resolve the issue, additional support resources are available:
Ubuntu community forums
Engage with the Ubuntu community for assistance and insights.
SSH documentation
Refer to the official SSH documentation for detailed information on configuration and troubleshooting.
System logs
Examine system logs, such as ‘/var/log/auth.log’ and ‘/var/log/syslog’, for clues about SSH server errors.
6. Automation
Automating SSH server checks enhances efficiency and consistency. Here’s how to design and schedule a script for this purpose.
Script Design
- #!/bin/bash: Specifies the interpreter for the script.
- ssh
-q
-o ConnectTimeout=5 root@localhost exit: Attempts an SSH connection to localhost as root, with a 5-second timeout. If successful, it exits with code 0 (indicating a running SSH server). - echo “SSH server is running.”: If the connection succeeds, this message is printed.
- exit 0: The script exits with code 0, signifying a successful execution.
- else: If the SSH connection fails, the following block executes.
- echo “SSH server is not running.”: This message is printed.
- exit 1: The script exits with code 1, indicating a failed execution.
Scheduling
To schedule the script, use crontab. Open the crontab file with crontab -e and add the following line:
*/5
-
-
-
- /path/to/script.sh This will run the script every 5 minutes.
7. Security Considerations
Maintaining the security of your SSH server is paramount to prevent unauthorized access and data breaches. Regular updates are crucial to patch vulnerabilities and address potential security risks.
SSH Key Management
Utilize strong SSH keys to enhance security. Avoid using default or weak passwords, and opt for complex passphrases or key pairs. Implement key rotation policies to regularly generate new keys and revoke old ones.
Password Security
Enforce strong password policies for SSH access. Require the use of complex passwords with a minimum length, special characters, and regular expiration intervals. Consider implementing two-factor authentication (2FA) for added security.
Mitigating SSH Vulnerabilities
Regularly review and implement security patches to address known SSH vulnerabilities. Disable unused SSH protocols and services to reduce the attack surface. Monitor SSH logs for suspicious activity and investigate any potential threats promptly.
Performance Optimization
Ensuring optimal performance for your SSH server is crucial for maintaining smooth and reliable remote access. Several factors can impact SSH server performance, including network latency, server hardware, SSH configuration, and the number of concurrent connections.
To optimize SSH performance, consider the following recommendations:
SSH Configuration
- Disable unnecessary ciphers and algorithms: Limit the number of ciphers and algorithms supported by your SSH server to improve performance. Choose strong but efficient ciphers and algorithms that balance security and speed.
- Optimize packet size: Adjust the packet size to match your network conditions. A larger packet size can improve throughput, but it may introduce latency issues on slower networks.
- Enable SSH compression: Compressing SSH traffic can significantly reduce bandwidth usage and improve performance, especially over high-latency networks.
- Use a fast key exchange algorithm: The key exchange algorithm is responsible for establishing a secure connection between the client and server. Choose a fast key exchange algorithm like ECDH (Elliptic Curve Diffie-Hellman) or DH (Diffie-Hellman) to reduce connection overhead.
Server Configuration
- Increase server resources: Allocate sufficient CPU, memory, and network resources to your SSH server to handle the expected load. Consider using a dedicated server or upgrading hardware if necessary.
- Optimize server software: Ensure that your SSH server software is up-to-date and configured for optimal performance. Consider using a lightweight SSH server like OpenSSH or Dropbear.
Other Performance-Enhancing Techniques
- Use a reverse SSH tunnel: Reverse SSH tunneling allows you to establish an SSH connection from the server to the client, which can improve performance by reducing network latency and avoiding firewall restrictions.
- Implement load balancing: Distribute SSH connections across multiple servers to balance the load and improve overall performance.
- Monitor and troubleshoot: Regularly monitor SSH server performance and troubleshoot any issues that may arise. Use tools like SSH profiling or server monitoring software to identify bottlenecks and optimize performance.
9. Remote Access
Securely accessing remote SSH servers from different computers is crucial for managing and maintaining systems. SSH keys provide a secure and convenient method for authentication, eliminating the need for passwords.
To connect to a remote SSH server, you can use SSH clients such as OpenSSH, PuTTY, or Bitvise SSH Client. The basic syntax for connecting to a server is:
ssh username@server_address
p port_number
where username is your user name on the server, server_address is the IP address or domain name of the server, and port_number is the SSH port (usually 22).
SSH Keys
Using SSH keys is a more secure alternative to passwords for authentication. SSH keys are cryptographic key pairs that consist of a private key stored on your local computer and a public key stored on the remote server.
To generate an SSH key pair, use the following command:
ssh-keygen
t rsa
Follow the prompts to create a passphrase for your private key. Once the key pair is generated, copy the public key to the remote server using the following command:
ssh-copy-id username@server_address
You will be prompted to enter the password for your user account on the remote server. Once the public key is copied, you can log in to the server without a password using the following command:
ssh username@server_address
10. Use Cases
Regular monitoring of SSH server status is crucial for system administrators and network security. It allows them to identify and address potential issues promptly, ensuring the smooth operation and security of the network.
SSH server status monitoring can be beneficial in various real-world scenarios:
- Ensuring SSH server availability: Monitoring the SSH server’s status helps ensure that it is always up and running, allowing authorized users to connect and perform essential tasks.
- Detecting unauthorized access attempts: Regular monitoring can help detect suspicious activities, such as failed login attempts or unusual traffic patterns, indicating potential unauthorized access attempts.
- Identifying configuration issues: SSH server status monitoring can reveal configuration errors or vulnerabilities that may compromise the server’s security.
- Tracking server performance: Monitoring the SSH server’s performance metrics, such as response times and resource utilization, helps identify potential bottlenecks and optimize the server’s configuration.
Last Recap
In conclusion, checking the SSH server status is a critical aspect of system administration and network security. By utilizing the methods Artikeld in this guide, you can effectively monitor and manage the SSH server, ensuring that it is running smoothly, secure, and optimized for performance.
Regular SSH server status checks contribute to overall system stability, security, and efficient remote access.