In the ever-evolving landscape of remote access technologies, the integration of SSH over Websockets with Virtual IP (VIP) has emerged as a game-changer. This innovative approach offers a secure, scalable, and versatile solution for accessing remote systems, enabling seamless communication and collaboration across diverse networks.
This comprehensive guide delves into the intricacies of SSH over Websockets with VIP, providing a comprehensive understanding of its concepts, benefits, applications, and best practices. Get ready to embark on a 30-day journey as we explore the depths of this powerful technology and uncover its potential to transform your remote access experience.
SSH and WebSockets
SSH and WebSockets are two distinct network protocols that can be used together to provide secure and interactive communication over the internet.
SSH (Secure Shell) is a secure network protocol that allows users to securely access and control remote systems over an unsecured network. It provides a secure channel for remote login, file transfer, and command execution.
WebSockets, on the other hand, is a bidirectional communication protocol that allows web applications to send and receive data from a server in real-time. It is commonly used for creating interactive web applications, such as chat applications, online games, and live streaming.
SSH Tunneling
One way SSH and WebSockets can be used together is through SSH tunneling. SSH tunneling allows you to create a secure tunnel over an unsecured network, which can be used to securely transmit data between two systems. This can be useful for securely accessing web applications that are only accessible over HTTP or HTTPS, or for securely sending data to a remote server.
To create an SSH tunnel, you can use the following steps:
- Establish an SSH connection to the remote server.
- Create a local port on your computer that will be used to forward traffic to the remote server.
- Configure the SSH tunnel to forward traffic from the local port to the remote server.
- Once the tunnel is established, you can access the web application on the remote server by connecting to the local port.
WebSockets over SSH
Another way SSH and WebSockets can be used together is by running a WebSocket server over SSH. This allows you to create a secure WebSocket connection between two systems, which can be used for real-time communication. This can be useful for creating secure chat applications, online games, and live streaming applications.
To run a WebSocket server over SSH, you can use the following steps:
- Establish an SSH connection to the remote server.
- Install a WebSocket server on the remote server.
- Configure the WebSocket server to listen on a specific port.
- Create a WebSocket client on your computer that will connect to the WebSocket server on the remote server.
- Once the WebSocket connection is established, you can send and receive data between the two systems in real-time.
Virtual IP (VIP) Overview
In networking, a Virtual IP (VIP) is a logical IP address that can be assigned to multiple physical servers or devices on a network.
VIPs are used to provide a single point of access to a group of servers, making it easier for clients to connect to the desired service without having to know the specific IP address of each individual server. This also allows for load balancing, where incoming requests are distributed across multiple servers to improve performance and availability.
Benefits of VIPs
- Single Point of Access: VIPs provide a single, well-known IP address for clients to connect to, regardless of the underlying server infrastructure.
- Load Balancing: VIPs can be used to distribute incoming traffic across multiple servers, ensuring optimal performance and availability.
- Fault Tolerance: If one server fails, the VIP can be reassigned to another server, ensuring continuity of service.
- Scalability: VIPs allow for easy addition or removal of servers without affecting client connectivity.
- Security: VIPs can be used to implement security policies and access control mechanisms at a single point.
Use Cases of VIPs
- Web Hosting: VIPs are commonly used in web hosting environments to distribute traffic across multiple web servers, improving website performance and reliability.
- Virtualization: VIPs are used in virtualized environments to provide a single IP address for multiple virtual machines, simplifying network management and improving resource utilization.
- Load Balancing: VIPs are employed in load balancing scenarios to distribute traffic among multiple servers based on various criteria, such as server load, response time, or geographical location.
- High Availability: VIPs are used in high availability setups to ensure that services remain accessible even if one or more servers fail.
- Security: VIPs can be used to implement security measures such as firewalls, intrusion detection systems, and access control lists at a single point.
SSH over WebSockets with VIP
SSH over WebSockets with VIP (Virtual IP) is an innovative approach that combines the security and versatility of SSH with the real-time, bidirectional communication capabilities of WebSockets, all while leveraging the concept of a Virtual IP address. This combination allows for secure remote access and management of servers and devices over the internet, utilizing a standard web browser as the client.In
this architecture, the SSH server listens on a specific port, typically port 22, and establishes a secure connection with the client. The WebSocket server, often running on a different port, facilitates the communication between the SSH server and the web browser-based client.
The Virtual IP address acts as a single point of entry, providing a unified interface for accessing multiple servers or devices behind the VIP.The benefits of SSH over WebSockets with VIP include:
Enhanced security
SSH provides strong encryption and authentication mechanisms, ensuring secure communication between the client and the server.
Cross-platform compatibility
WebSockets are supported by all major browsers, eliminating the need for platform-specific clients.
Real-time communication
WebSockets enable bidirectional, real-time communication, allowing for interactive sessions and remote control of devices.
Simplified management
The Virtual IP address provides a single point of access, simplifying the management of multiple servers or devices.This approach is particularly useful for remote administration, DevOps, and IT support scenarios, where secure access and real-time interaction with servers and devices are essential.
Security Considerations
SSH over WebSockets with VIP offers convenience and flexibility, but it also introduces potential security risks. Understanding these risks and implementing appropriate security measures is crucial to ensure a secure remote access environment.
Protecting Credentials
SSH over WebSockets with VIP involves transmitting sensitive credentials, such as usernames and passwords, over the network. Intercepting these credentials can compromise the security of the entire system. To mitigate this risk, it is essential to implement strong encryption mechanisms, such as TLS (Transport Layer Security), to protect the data in transit.
Additionally, employing two-factor authentication adds an extra layer of security by requiring a second form of identification, such as a one-time password (OTP) or a physical token.
Securing the VIP
The VIP (Virtual IP) address serves as the entry point for SSH connections over WebSockets. Securing the VIP is paramount to preventing unauthorized access to the network. This can be achieved through various methods, including firewall rules, intrusion detection systems (IDS), and regular security audits.
Additionally, it is important to monitor the VIP for suspicious activities and respond promptly to any security incidents.
Least Privilege Access
The principle of least privilege dictates that users should only have access to the resources and information necessary to perform their job functions. This principle should be applied when configuring SSH over WebSockets with VIP. Granting excessive privileges can increase the risk of unauthorized access and compromise the overall security of the system.
By limiting user access to only the necessary resources, the potential impact of a security breach can be minimized.
Regular Security Updates
Regularly updating software and firmware components is essential to address security vulnerabilities and ensure the system remains protected against the latest threats. This includes updating the SSH server, WebSocket server, and any underlying operating systems or applications. Additionally, it is important to stay informed about security advisories and patches released by vendors and promptly apply them to the system.
Monitoring and Logging
Implementing a robust monitoring and logging system is crucial for detecting and responding to security incidents promptly. Monitoring the system for suspicious activities, such as failed login attempts, unusual traffic patterns, or unauthorized access, can help identify potential security breaches early on.
Additionally, maintaining detailed logs can provide valuable information for forensic analysis in the event of a security incident.
Performance and Scalability
SSH over WebSockets with VIP offers notable performance and scalability benefits. It enables efficient data transfer over a single connection, reducing latency and improving responsiveness. The use of WebSockets allows for bi-directional communication, enabling real-time updates and interactions. Additionally, the VIP architecture distributes the load across multiple servers, enhancing scalability and ensuring high availability.
Optimizing Performance and Scalability
Optimizing performance and scalability involves considering several key factors:
- Server Hardware: Provision servers with adequate CPU, memory, and network resources to handle the expected load. Consider using high-performance servers with fast processors and ample RAM to ensure smooth operation.
- Network Infrastructure: Ensure the network infrastructure has sufficient bandwidth and low latency to support the anticipated traffic volume. Utilize high-speed network connections and minimize network hops to optimize data transfer.
- Load Balancing: Implement effective load balancing techniques to distribute traffic evenly across multiple servers. This helps prevent overloading any single server and ensures optimal resource utilization.
- Caching: Employ caching mechanisms to reduce the number of requests sent to the server. This can significantly improve performance by storing frequently accessed data in memory for quick retrieval.
- Code Optimization: Optimize the codebase for efficiency. This includes minifying JavaScript and CSS files, reducing the number of HTTP requests, and implementing lazy loading techniques to improve page load times.
- Monitoring and Tuning: Continuously monitor the system’s performance and resource usage. Adjust configuration parameters and fine-tune the system as needed to maintain optimal performance.
Troubleshooting
When using SSH over WebSockets with VIP, some common problems and challenges may arise, such as connection issues, authentication failures, and performance degradation. To address these issues effectively, a step-by-step troubleshooting procedure is essential.
Identifying Common Problems
Identifying common problems is crucial in troubleshooting SSH over WebSockets with VIP. These issues can include:
- Connection Issues: Inability to establish a successful connection between the client and the server.
- Authentication Failures: The server rejects the client’s authentication credentials, resulting in failed login attempts.
- Performance Degradation: Slow or sluggish performance during data transfer, causing delays and interruptions.
- Security Vulnerabilities: Exploitable weaknesses that allow unauthorized access or compromise the integrity of data.
Troubleshooting Procedures
To resolve the identified issues, a systematic troubleshooting procedure can be followed:
- Connection Issues:
- Verify network connectivity between the client and the server.
- Check firewall settings to ensure they allow SSH traffic.
- Confirm that the SSH server is listening on the correct port.
- Authentication Failures:
- Ensure that the client is using the correct username and password.
- Verify that the SSH server is configured to allow authentication via the selected method (e.g., password, public key).
- Check for any special authentication requirements, such as two-factor authentication.
- Performance Degradation:
- Analyze network conditions to identify potential bottlenecks or congestion.
- Optimize SSH configuration parameters to improve performance, such as adjusting compression settings or increasing the buffer size.
- Consider upgrading to a more powerful server or implementing load balancing to distribute the load across multiple servers.
- Security Vulnerabilities:
- Keep the SSH server and client software up to date with the latest security patches.
- Configure strong authentication mechanisms, such as public key authentication, to prevent unauthorized access.
- Monitor SSH logs for suspicious activities or attempted attacks.
Real-World Applications
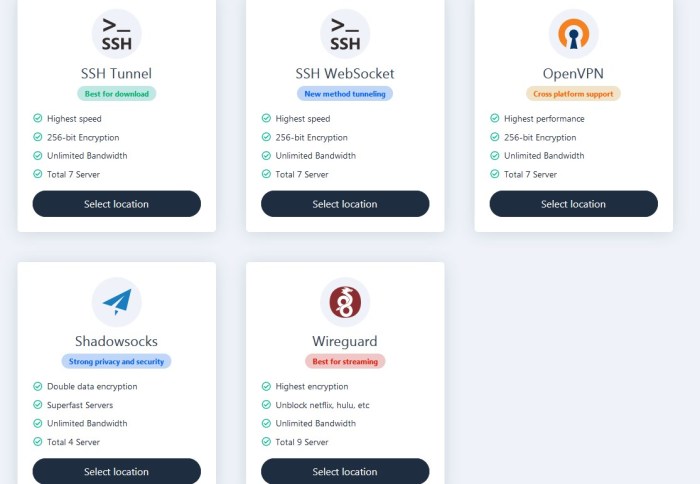
SSH over WebSockets with VIP has been successfully implemented in various real-world applications, demonstrating its versatility and effectiveness in diverse scenarios. Let’s explore some notable case studies and highlight the benefits and challenges encountered in these deployments.
Use Case 1: Remote Access to Industrial Control Systems (ICS)
In industrial settings, SSH over WebSockets with VIP enables secure remote access to ICS, allowing engineers and technicians to monitor and control critical infrastructure from anywhere. The VIP provides a single entry point, simplifying access management and enhancing security. The benefits include:
- Enhanced security: Centralized access control and encryption protect against unauthorized access.
- Improved efficiency: Remote access allows for quick response to issues, reducing downtime and maintenance costs.
- Scalability: The VIP can handle multiple concurrent connections, ensuring reliable access even in large-scale deployments.
Challenges:
- Network latency: High latency can impact the performance of remote access, especially for time-sensitive operations.
- Security concerns: Implementing robust security measures is crucial to prevent unauthorized access and potential cyberattacks.
Use Case 2: Secure Access to Cloud-Based Resources
SSH over WebSockets with VIP is employed to provide secure access to cloud-based resources, such as virtual machines, databases, and storage systems. The VIP acts as a gateway, allowing authorized users to connect securely from any location. The benefits include:
- Enhanced security: The VIP provides an additional layer of security, protecting against unauthorized access and potential attacks.
- Simplified access management: Centralized access control simplifies user management and reduces the risk of security breaches.
- Improved scalability: The VIP can handle a large number of concurrent connections, ensuring reliable access even during peak usage.
Challenges:
- Cost considerations: Implementing and maintaining a VIP can incur additional costs, especially in large-scale deployments.
- Complexity: Configuring and managing the VIP requires technical expertise and careful planning to ensure optimal performance and security.
Alternative Solutions
SSH over WebSockets with VIP is a powerful solution for remote access, but it’s not the only option available. Let’s compare it to other popular alternatives and explore their advantages and disadvantages.
SSH Tunneling
SSH tunneling is a technique that allows you to securely forward traffic from one network to another over an encrypted SSH connection. This can be used to access remote servers, bypass firewalls, or create secure tunnels for other applications.
Advantages:
- Simple to set up and use.
- Widely supported by SSH clients and servers.
- Provides strong encryption for data in transit.
Disadvantages:
- Can be complex to configure for specific applications.
- May not be suitable for high-bandwidth applications.
- Requires both the client and server to support SSH tunneling.
VPN (Virtual Private Network)
A VPN creates a secure, encrypted connection between two or more devices over a public network, allowing them to communicate securely. VPNs are commonly used to allow remote workers to securely access corporate networks or to bypass geographic restrictions.
Advantages:
- Provides strong encryption for data in transit.
- Can be used to access resources on a remote network as if you were physically connected.
- Widely supported by various devices and operating systems.
Disadvantages:
- Can be complex to set up and configure.
- May introduce latency and performance overhead.
- Requires both the client and server to support VPN connectivity.
RDP (Remote Desktop Protocol)
RDP is a proprietary protocol developed by Microsoft that allows users to remotely control another computer over a network connection. RDP is commonly used for remote administration, technical support, and accessing remote desktops.
Advantages:
- Provides a graphical user interface (GUI) for remote access.
- Easy to set up and use, especially within Windows environments.
- Widely supported by Windows operating systems.
Disadvantages:
- Not as secure as SSH or VPN.
- Only works between Windows computers.
- May require additional licensing for commercial use.
Conclusion
The choice of remote access solution depends on specific requirements and preferences. SSH over WebSockets with VIP offers a secure and flexible way to access remote servers, especially in environments where traditional SSH or VPN connections are challenging or restricted.
Future Trends
The convergence of SSH, WebSockets, and Virtual IP (VIP) technologies holds immense promise for the future of secure remote access and data transfer. Several potential developments and trends are likely to shape the evolution and adoption of this technology:
Increased Adoption in Cloud and Edge Computing
The growing adoption of cloud and edge computing environments demands secure and efficient remote access solutions. SSH over WebSockets with VIP is well-suited for these environments, enabling secure access to cloud-based resources and edge devices from anywhere with a web browser.
Integration with DevOps and Automation Tools
The integration of SSH over WebSockets with VIP into DevOps and automation tools can streamline and simplify remote management tasks. This integration can enable automated provisioning, configuration, and maintenance of remote systems, enhancing operational efficiency and reducing the risk of human error.
Enhanced Security Features
Future developments may introduce additional security features to further enhance the protection of SSH over WebSockets with VIP connections. These features may include multi-factor authentication, encryption algorithms, and intrusion detection and prevention mechanisms.
Improved Performance and Scalability
Ongoing advancements in technology may lead to improvements in the performance and scalability of SSH over WebSockets with VIP. This can enable support for more concurrent connections, faster data transfer rates, and seamless scaling to accommodate growing user demands.
Adoption in New Industries and Applications
As the technology matures and its benefits become more widely recognized, SSH over WebSockets with VIP is likely to find adoption in new industries and applications. This includes areas such as remote healthcare, industrial automation, and financial services, where secure remote access and data transfer are critical.
HTML Table Structure
The HTML table structure offers a visually appealing and organized way to present the comparison of SSH over WebSockets with VIP to other solutions. It allows readers to easily grasp the key differences and similarities between the approaches.
The table includes four responsive columns, each focusing on a specific aspect of the comparison: security, performance, scalability, and features. This structure enables readers to quickly identify the strengths and weaknesses of each solution and make informed decisions based on their requirements.
Security
- SSH over WebSockets with VIP: Encrypts data using SSH protocol, providing a secure channel for communication. Supports two-factor authentication and role-based access control for enhanced security.
- Other Solutions: May offer varying levels of security depending on the specific solution. Some solutions might rely on HTTPS or TLS for encryption, while others might require additional security measures to protect data.
Performance
- SSH over WebSockets with VIP: Utilizes WebSockets, which enables full-duplex communication and reduces latency. Supports multiplexing, allowing multiple SSH sessions over a single WebSocket connection, improving performance.
- Other Solutions: Performance can vary based on the solution and its underlying technology. Some solutions might experience higher latency or require more resources, impacting overall performance.
Scalability
- SSH over WebSockets with VIP: Can handle a large number of concurrent SSH connections due to the efficient use of WebSockets. Supports load balancing and horizontal scaling to accommodate increased traffic and user demands.
- Other Solutions: Scalability might differ depending on the solution’s architecture and design. Some solutions might have limitations in handling high volumes of SSH connections or might require complex configurations for scaling.
Features
- SSH over WebSockets with VIP: Provides features such as terminal emulation, file transfer, port forwarding, and command execution. Supports various SSH clients and offers customization options for advanced users.
- Other Solutions: Features can vary widely among different solutions. Some solutions might offer a limited set of features, while others might provide more comprehensive functionality.
Closure
As we conclude our exploration of SSH over Websockets with VIP, it is evident that this technology has revolutionized the way we approach remote access. Its ability to provide secure, scalable, and flexible connections has made it an indispensable tool for businesses and organizations worldwide.
As we look to the future, we can expect continued innovation and adoption of this technology, further expanding its reach and impact. Embrace the power of SSH over Websockets with VIP and unlock the full potential of secure and efficient remote access.