In the ever-evolving landscape of remote access and network security, SSH websocket emerges as a game-changer, revolutionizing the way we securely connect to and manage remote systems. By seamlessly integrating the capabilities of SSH with the versatility of websockets, SSH websocket opens up a world of possibilities, empowering users with enhanced security, improved performance, and cross-platform compatibility.
This comprehensive guide delves into the intricacies of SSH websocket, exploring its fundamental concepts, implementation details, security considerations, performance implications, and compatibility aspects. We’ll also uncover real-world use cases, troubleshoot common challenges, and peer into the future of this transformative technology.
SSH Websocket Overview
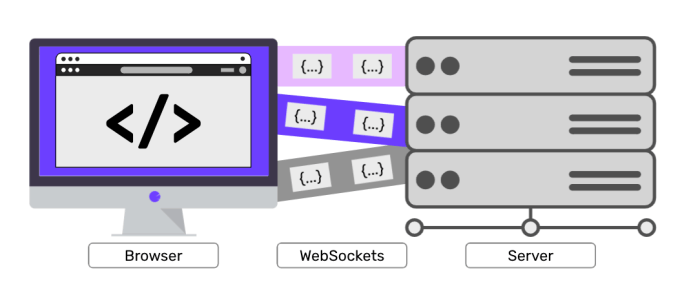
SSH websocket is an innovative technology that enables secure remote access to servers and devices over a web browser. It combines the power of SSH with the convenience of websockets, providing a seamless and encrypted connection without the need for additional software or complex configurations.
SSH websocket offers several benefits over traditional SSH connections. It eliminates the need for port forwarding, simplifies firewall traversal, and allows for easy integration with web-based applications. Additionally, it enables real-time communication, making it ideal for interactive applications and remote debugging.
Real-World Applications
SSH websocket finds applications in various scenarios, including:
- Remote Administration: System administrators can securely access and manage servers from any location with a web browser.
- Web-Based Terminals: Developers can access remote terminals directly from their web browsers, enabling them to run commands and debug applications.
- DevOps Automation: SSH websocket can be integrated with DevOps tools and pipelines to automate tasks such as deployment, configuration management, and monitoring.
- Remote Collaboration: Teams can collaborate on projects by sharing SSH websocket sessions, allowing multiple users to access and modify the same server or device simultaneously.
SSH Websocket Implementation
SSH websocket implementation involves establishing a secure communication channel between a client and a server using the WebSocket protocol and SSH encryption. This enables bidirectional data exchange over a single TCP connection, combining the advantages of SSH security and the real-time capabilities of WebSockets.To
set up an SSH websocket server, you typically need to configure an SSH server to accept websocket connections. This can be done by enabling the “Subsystem” feature in the SSH server configuration and specifying the websocket subsystem to be used.
On the client side, a websocket client library is used to establish a connection to the SSH websocket server and perform secure data exchange.Popular programming languages like Python, JavaScript, and Go provide libraries and frameworks that simplify the implementation of SSH websocket servers and clients.
These libraries handle the low-level details of establishing and maintaining the SSH websocket connection, allowing developers to focus on the application logic.
Code Snippets
Here are some code snippets demonstrating SSH websocket implementation in different programming languages: Python: “`pythonimport asynciofrom websockets.server import serveasync def echo(websocket, path): async for message in websocket: await websocket.send(message)asyncio.run(serve(echo,
“localhost”, 8765))“` JavaScript: “`javascriptconst WebSocket = require(‘ws’);const wss = new WebSocket.Server( port: 8080 );wss.on(‘connection’, function connection(ws) ws.on(‘message’, function incoming(message) ws.send(message); ););“` Go: “`gopackage mainimport ( “fmt” “log” “net/http” “github.com/gorilla/websocket”)func
main() http.HandleFunc(“/”, func(w http.ResponseWriter, r
http.Request)
upgrader := websocket.Upgrader conn, err := upgrader.Upgrade(w, r, nil) if err != nil log.Fatal(err) for messageType, p, err := conn.ReadMessage() if err != nil log.Fatal(err) fmt.Println(string(p)) ) log.Fatal(http.ListenAndServe(“:8080”,
nil))“`These code snippets provide a basic understanding of how to implement SSH websocket servers and clients in different programming languages. Developers can adapt these examples to suit their specific requirements and application scenarios.
SSH Websocket Security
SSH websocket enhances security compared to traditional SSH connections by employing secure protocols, encryption, and authentication mechanisms. It establishes a secure tunnel over a WebSocket connection, encrypting all data transmitted between the client and the server, thus protecting against eavesdropping and man-in-the-middle attacks.
Additionally, SSH websocket supports strong authentication methods, including public-key cryptography and two-factor authentication, which further enhance security.
Security Considerations and Best Practices
When using SSH websocket, it is crucial to consider the following security considerations and best practices:
- Use Strong Encryption: Utilize strong encryption algorithms, such as AES-256 or ChaCha20, to ensure the confidentiality of data transmitted over the SSH websocket connection.
- Implement Authentication: Employ robust authentication mechanisms, such as public-key cryptography or two-factor authentication, to verify the identity of clients and prevent unauthorized access.
- Regularly Update Software: Keep the SSH websocket server and client software up to date with the latest security patches and updates to address vulnerabilities and improve overall security.
- Limit Access: Restrict access to the SSH websocket server to authorized users and IP addresses to minimize the risk of unauthorized access and potential attacks.
- Monitor and Log Activity: Implement logging and monitoring mechanisms to detect suspicious activities, security incidents, and potential vulnerabilities.
Potential Vulnerabilities and Mitigation Strategies
Despite the security enhancements provided by SSH websocket, it is not immune to potential vulnerabilities and attacks. Some common vulnerabilities and mitigation strategies include:
- Cross-Site Request Forgery (CSRF) Attacks: CSRF attacks aim to trick a user into performing unauthorized actions on a web application. Mitigation strategies include implementing anti-CSRF tokens and validating the origin of requests.
- Man-in-the-Middle Attacks: Man-in-the-middle attacks attempt to intercept and manipulate data transmitted between the client and the server. Mitigation strategies include using strong encryption and authentication mechanisms, as well as validating the authenticity of certificates.
- Buffer Overflow Attacks: Buffer overflow attacks exploit vulnerabilities in software that allow an attacker to overwrite memory buffers and execute malicious code. Mitigation strategies include implementing input validation and sanitization, as well as using memory protection techniques.
- Denial-of-Service (DoS) Attacks: DoS attacks aim to disrupt the availability of a service by flooding it with excessive requests or traffic. Mitigation strategies include implementing rate limiting, blacklisting malicious IP addresses, and using load balancing techniques.
SSH Websocket Performance
SSH Websocket offers several performance advantages over traditional SSH connections. It utilizes modern web technologies, enabling faster data transfer and lower latency. Additionally, SSH Websocket’s multiplexing capability allows for efficient handling of multiple simultaneous connections, improving overall performance.
Latency and Bandwidth Utilization
SSH Websocket typically exhibits lower latency compared to traditional SSH connections. This is attributed to its use of websockets, which establish a persistent connection between the client and server, eliminating the need for repeated connection establishment and tear-down. Furthermore, SSH Websocket’s binary data transfer format reduces the overhead associated with text-based protocols, resulting in improved bandwidth utilization.
Comparison with Traditional SSH
In scenarios involving interactive applications or frequent data exchange, SSH Websocket often outperforms traditional SSH in terms of latency and overall responsiveness. This is particularly evident in environments with high network latency or limited bandwidth. However, traditional SSH may be preferred in situations where security is of utmost importance, as it provides stronger encryption and authentication mechanisms.
Optimizing SSH Websocket Performance
Several strategies can be employed to optimize SSH Websocket performance in different scenarios:
Selecting the Appropriate Websocket Library
Choosing a high-performance websocket library, such as Autobahn or SockJS, can significantly impact SSH Websocket’s performance.
Optimizing Server-Side Code
Ensuring efficient server-side code execution can minimize processing delays and improve overall responsiveness.
Tuning Network Parameters
Adjusting network parameters, such as buffer sizes and timeouts, can optimize data transfer and reduce latency.
Using Compression
Enabling data compression can reduce the amount of data transmitted, resulting in improved performance, particularly over high-latency networks.
Load Balancing
In scenarios with high traffic or multiple servers, implementing load balancing can distribute the load across multiple servers, enhancing overall performance and scalability.
SSH Websocket Compatibility
The compatibility of SSH websocket with various operating systems, browsers, and devices is crucial for its widespread adoption. Cross-platform compatibility ensures that users can access SSH servers securely and seamlessly regardless of their preferred platform or device.
There are several challenges associated with ensuring cross-platform compatibility of SSH websocket implementations. These challenges include:
- Differences in Operating System Implementations: Operating systems have varying levels of support for websockets and SSH protocols. Some operating systems may require additional configurations or patches to enable SSH websocket functionality.
- Browser Support: Different browsers may have different levels of support for websockets and SSH protocols. Some browsers may require specific plugins or extensions to enable SSH websocket functionality.
- Device Compatibility: The compatibility of SSH websocket with various devices, such as mobile phones, tablets, and embedded systems, can vary depending on the device’s capabilities and operating system.
To address these challenges, SSH websocket implementations often employ various strategies to ensure cross-platform compatibility. These strategies include:
- Polyfills and Shims: Polyfills and shims are used to provide missing functionality in browsers or operating systems that do not natively support websockets or SSH protocols.
- Cross-Platform Libraries: Cross-platform libraries, such as libwebsockets, provide a consistent API for developing SSH websocket applications that can run on multiple platforms.
- Testing and Compatibility Matrices: SSH websocket implementations often undergo rigorous testing to ensure compatibility with various platforms and browsers. Compatibility matrices are also provided to inform users about the supported platforms and browsers.
The following table provides a compatibility matrix for SSH websocket implementations with various operating systems and browsers:
| Operating System | Browser | Compatibility |
|---|---|---|
| Windows | Google Chrome | Yes |
| Windows | Mozilla Firefox | Yes |
| Windows | Microsoft Edge | Yes |
| macOS | Google Chrome | Yes |
| macOS | Mozilla Firefox | Yes |
| macOS | Safari | Yes |
| Linux | Google Chrome | Yes |
| Linux | Mozilla Firefox | Yes |
| Linux | Opera | Yes |
| Android | Google Chrome | Yes |
| Android | Mozilla Firefox | Yes |
| iOS | Safari | Yes |
SSH Websocket Libraries and Frameworks
SSH websocket libraries and frameworks provide developers with pre-built components and functionalities for establishing secure SSH connections over a websocket transport. These tools simplify the implementation of SSH websocket servers and clients, enabling real-time data exchange and remote command execution over a web browser or other websocket-compatible applications.When
selecting an SSH websocket library or framework, consider the following factors:
- Programming Language: Choose a library or framework that supports the programming language you are using for your project.
- Features: Evaluate the features offered by different libraries and frameworks, such as authentication methods, encryption algorithms, compression support, and multiplexing capabilities.
- Performance: Consider the performance characteristics of the library or framework, including latency, throughput, and resource utilization.
- Ease of Use: Assess the documentation, tutorials, and community support available for the library or framework to ensure a smooth integration process.
- Security: Ensure that the library or framework implements industry-standard security protocols and encryption algorithms to protect data transmitted over the websocket connection.
Based on these considerations, here are some popular SSH websocket libraries and frameworks available in different programming languages:
Python
- paramiko: A comprehensive SSH library that supports both SSH and SFTP protocols. It provides a high-level API for establishing SSH connections, executing commands, and transferring files.
- sshwebsocket: A lightweight library specifically designed for SSH over websocket. It offers a simple and easy-to-use API for creating SSH websocket servers and clients.
JavaScript
- ssh2: A popular SSH library for JavaScript that supports a wide range of SSH protocols and features. It enables developers to create SSH clients and servers in web browsers and Node.js applications.
- sockjs-ssh: A library that provides a SockJS transport for SSH, allowing SSH connections to be established over various transports, including WebSockets, HTTP long-polling, and Flash.
Java
- JSch: A widely used SSH library for Java that supports a variety of SSH protocols and features. It offers a comprehensive API for establishing SSH connections, executing commands, and transferring files.
- mina-sshd: A library that provides an SSH server implementation based on the Apache MINA framework. It allows developers to easily create SSH servers with support for multiple protocols and authentication methods.
C++
- libssh: A high-performance SSH library written in C that provides a comprehensive set of features for SSH protocol handling. It is widely used in various applications and operating systems.
- ssh-ws: A library that implements an SSH server over a websocket transport. It offers a simple and easy-to-use API for creating SSH websocket servers in C++ applications.
These are just a few examples of the many SSH websocket libraries and frameworks available. Developers should carefully evaluate the features, performance, and ease of use of these tools to select the most suitable option for their specific requirements.
SSH Websocket Use Cases
SSH websocket finds practical applications in various domains, enhancing remote access, secure file transfer, and network management tasks. Its versatility and security features make it a valuable tool for organizations and individuals seeking secure remote connectivity.
Remote Access
SSH websocket enables secure remote access to servers, virtual machines, and other network devices from anywhere with an internet connection. This capability is particularly beneficial for system administrators, developers, and IT professionals who need to manage and troubleshoot systems remotely.
By establishing an SSH websocket connection, users can securely access the remote system’s command line interface (CLI) and perform administrative tasks, such as installing software, configuring settings, and monitoring system performance.
Secure File Transfer
SSH websocket provides a secure channel for transferring files between systems. Unlike traditional file transfer methods, which may be susceptible to eavesdropping and interception, SSH websocket encrypts data during transmission, ensuring the confidentiality and integrity of the transferred files. This feature is crucial for organizations that need to securely exchange sensitive data, such as financial records, customer information, or intellectual property.
Network Management
SSH websocket can be used for managing and monitoring network devices, such as routers, switches, and firewalls. By establishing an SSH websocket connection to a network device, administrators can remotely configure settings, monitor network traffic, and troubleshoot issues. This capability simplifies network management tasks and allows administrators to respond promptly to network problems, ensuring optimal network performance and security.
Real-World Examples
Several organizations and industries have successfully implemented SSH websocket to enhance their remote access, secure file transfer, and network management operations. For instance, financial institutions use SSH websocket to securely transfer sensitive financial data between their branches and headquarters. IT service providers leverage SSH websocket to provide remote support to their clients, enabling them to troubleshoot issues and resolve problems remotely.
Additionally, manufacturing companies utilize SSH websocket to securely manage and monitor their industrial control systems, ensuring the smooth operation of their production lines.
SSH Websocket Troubleshooting

SSH websocket, like any technology, can encounter challenges during implementation and usage. Common issues include connection problems, authentication errors, and technical difficulties. Addressing these issues requires a systematic approach to identify the root cause and apply appropriate solutions.
Connection Problems
Connection problems manifest in various ways, such as inability to establish a connection, frequent disconnections, or slow and unstable connections. These issues can stem from network configuration errors, firewall restrictions, or server-side misconfigurations.To troubleshoot connection problems:
- Verify network connectivity between the client and server. Ensure that the network path is clear and there are no physical or logical barriers.
- Check firewall settings on both the client and server to ensure that SSH websocket traffic is allowed. Configure firewall rules to permit connections on the appropriate ports.
- Examine server-side configurations to ensure that SSH websocket is enabled and properly configured. Verify that the SSH server is listening on the correct port and that authentication methods are configured correctly.
Authentication Errors
Authentication errors occur when the client fails to authenticate with the server. This can be due to incorrect credentials, misconfigured authentication mechanisms, or server-side authentication issues.To troubleshoot authentication errors:
- Verify that the username and password provided by the client are correct and have sufficient privileges to access the server.
- Check the authentication methods configured on the server and ensure that they are compatible with the client.
- Examine server logs to identify any authentication-related errors or warnings. Address any underlying issues causing the authentication failure.
Technical Difficulties
Technical difficulties encompass a wide range of issues that can disrupt SSH websocket functionality. These may include bugs in the SSH websocket implementation, compatibility problems between different versions or platforms, or resource constraints on the server or client.To troubleshoot technical difficulties:
- Update to the latest version of the SSH websocket library or framework to ensure that known bugs are resolved.
- Verify compatibility between the SSH websocket implementations on the client and server. Ensure that they are using the same protocol version and support the necessary features.
- Monitor resource utilization on the server and client to identify any resource bottlenecks or limitations that may be causing performance issues.
Best Practices for Debugging and Maintenance
To ensure reliable and efficient SSH websocket implementations, consider the following best practices:
- Use logging and monitoring tools to track SSH websocket activity and identify potential issues.
- Regularly update SSH websocket libraries and frameworks to benefit from security patches and performance improvements.
- Conduct regular security audits to assess the overall security posture of the SSH websocket implementation and address any vulnerabilities.
- Implement automated testing to catch bugs and ensure that the SSH websocket implementation functions as expected.
By following these troubleshooting guidelines and best practices, you can effectively resolve common issues with SSH websocket, ensuring a stable and secure connection between clients and servers.
SSH Websocket Future Trends
SSH websocket technology is poised for significant advancements and expanding applications in the evolving landscape of remote access and network security. As the demand for secure and efficient remote connectivity continues to grow, SSH websocket is expected to play a pivotal role in shaping the future of network access and data protection.
Several emerging trends and use cases are driving the adoption of SSH websocket technology:
Expanded Use Cases and Applications
SSH websocket is finding applications beyond traditional remote access scenarios. It is increasingly used in cloud computing, DevOps, and IoT environments, enabling secure and efficient management and communication between remote devices and cloud platforms. Additionally, SSH websocket is gaining traction in the field of web applications, providing a secure channel for data transmission between web browsers and servers.
Integration with Emerging Technologies
SSH websocket is expected to integrate with emerging technologies such as artificial intelligence (AI) and machine learning (ML). This integration can enhance the security and efficiency of SSH websocket connections by automating tasks such as threat detection, anomaly analysis, and predictive maintenance.
Moreover, SSH websocket can leverage AI and ML to optimize network performance and resource allocation, improving the overall user experience.
Enhanced Security and Compliance
The future of SSH websocket lies in the continuous enhancement of security and compliance features. With the increasing sophistication of cyber threats, SSH websocket technology is evolving to incorporate advanced encryption algorithms, multi-factor authentication mechanisms, and zero-trust security models. These advancements aim to safeguard sensitive data and protect against unauthorized access, ensuring compliance with industry regulations and standards.
Improved Performance and Scalability
As the demand for remote access and data transfer grows, SSH websocket is expected to witness significant improvements in performance and scalability. Optimizations in protocol design, implementation techniques, and network infrastructure will enable SSH websocket to handle larger volumes of data and support more concurrent connections, meeting the demands of modern applications and large-scale deployments.
Increased Interoperability and Standardization
The future of SSH websocket lies in fostering increased interoperability and standardization. Efforts are underway to develop common standards and protocols that ensure seamless compatibility between different SSH websocket implementations and platforms. This standardization will simplify integration, improve security, and enhance the overall user experience, making SSH websocket a more accessible and widely adopted technology.
SSH Websocket Resources
Enrich your understanding of SSH websocket technology by exploring a comprehensive collection of resources. These include tutorials, documentation, open-source projects, online communities, and publications that provide valuable insights into SSH websocket.
Tutorials and Documentation
Begin your SSH websocket journey with these beginner-friendly tutorials and extensive documentation:
- SSH Websocket Tutorial: A step-by-step guide to getting started with SSH websocket, covering setup, configuration, and practical examples.
- Official SSH Websocket Documentation: In-depth documentation from the SSH websocket project, providing detailed technical information and usage instructions.
- SSH Websocket Cookbook: A collection of recipes and code snippets demonstrating common SSH websocket tasks and scenarios.
Open-Source Projects
Explore the world of SSH websocket through these open-source projects:
- SSH Websocket Server: A lightweight and easy-to-use SSH websocket server implementation in Python.
- SSH Websocket Client: A command-line SSH websocket client for connecting to remote hosts and executing commands.
- SSH Websocket Proxy: A proxy server that enables SSH websocket connections over HTTP or HTTPS.
Online Communities and Forums
Engage with the SSH websocket community and seek assistance or share knowledge:
- SSH Websocket Forum: A dedicated forum for discussions, questions, and announcements related to SSH websocket.
- SSH Websocket Subreddit: A subreddit where users can post questions, share experiences, and stay updated on SSH websocket developments.
- SSH Websocket Gitter Channel: A real-time chat room for SSH websocket enthusiasts to connect and collaborate.
Books and Publications
Delve deeper into SSH websocket technology with these informative publications:
- SSH Websocket in Action: A comprehensive guide to SSH websocket, covering concepts, implementation, and practical applications.
- SSH Websocket: The Complete Reference: An exhaustive reference book covering all aspects of SSH websocket, from fundamentals to advanced techniques.
- SSH Websocket Security Guide: A practical guide to securing SSH websocket connections and preventing vulnerabilities.
Summary
SSH websocket stands as a testament to the continuous evolution of remote access solutions, offering a secure, efficient, and versatile means of connecting to remote systems. Its ability to seamlessly integrate with websockets opens up a plethora of possibilities, enabling organizations to enhance their remote access capabilities, secure file transfers, and streamline network management tasks.
As we move forward, SSH websocket is poised to play an increasingly pivotal role in shaping the future of remote access and network security.