In the realm of secure communication, SSH WebSockets emerge as a beacon of innovation, enabling seamless and encrypted data transmission over the web. Embark on a journey through the world of SSH WebSockets, where we unravel their significance, explore real-world applications, and delve into the intricacies of their security and performance.
From enhancing security and performance to revolutionizing industries, SSH WebSockets are transforming the way we communicate online. Let’s uncover the secrets behind this groundbreaking technology and witness its impact on the digital landscape of Brazil.
SSH WebSocket Technology
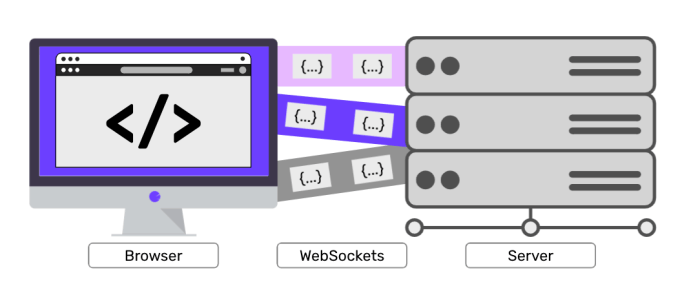
SSH WebSockets are a powerful technology that combines the security of SSH with the real-time communication capabilities of WebSockets. This allows for secure communication over the web, enabling a wide range of applications such as remote desktop access, file transfer, and interactive command-line sessions.
SSH WebSockets work by establishing a secure connection between a client and a server using the SSH protocol. Once the connection is established, the WebSocket protocol is used to send and receive data in real-time. This combination of SSH and WebSockets provides a secure and efficient way to communicate over the web.
Advantages of SSH WebSockets
There are several advantages to using SSH WebSockets, including:
- Security: SSH WebSockets provide a secure connection between the client and the server, protecting data from eavesdropping and man-in-the-middle attacks.
- Performance: SSH WebSockets use the WebSocket protocol, which is designed for real-time communication. This results in fast and efficient data transfer.
- Cross-platform compatibility: SSH WebSockets are supported by a wide range of platforms, including Windows, macOS, Linux, and mobile devices.
- Ease of use: SSH WebSockets are easy to use and can be integrated into a variety of applications.
SSH WebSocket Applications
SSH WebSockets have gained significant traction in various industries due to their ability to establish secure, real-time connections between web applications and remote servers.
Let’s explore some real-world applications and success stories highlighting the benefits and impact of SSH WebSockets:
Remote Terminal Access
SSH WebSockets enable remote access to command-line interfaces (CLIs) of servers and devices from a web browser. This allows IT administrators, developers, and system engineers to securely manage and troubleshoot remote systems from anywhere with an internet connection.
- Example: A network engineer uses an SSH WebSocket to remotely access a router’s CLI to configure and monitor network traffic.
Secure File Transfer
SSH WebSockets provide a secure channel for transferring files between a web application and a remote server. This eliminates the need for insecure file transfer protocols (FTPs) and enables secure file sharing and management.
- Example: A web developer uses an SSH WebSocket to securely transfer code updates from a local development environment to a production server.
Real-Time Data Streaming
SSH WebSockets facilitate real-time data streaming from remote devices and sensors to web applications. This enables applications to receive live updates and respond accordingly, enhancing decision-making and operational efficiency.
- Example: A manufacturing company uses SSH WebSockets to stream real-time production data from sensors on the factory floor to a web-based dashboard, allowing managers to monitor production status and make adjustments as needed.
DevOps and Continuous Integration/Continuous Delivery (CI/CD)
SSH WebSockets play a crucial role in DevOps and CI/CD pipelines by enabling automated tasks such as code deployment, testing, and infrastructure management. This streamlines development and deployment processes, reducing time to market and improving software quality.
- Example: A software development team uses SSH WebSockets to automate the deployment of new code to production servers, ensuring a seamless and reliable release process.
SSH WebSocket Security
SSH WebSockets incorporate robust security mechanisms to safeguard data transmission. This section delves into the security measures employed and explores potential vulnerabilities and mitigation strategies.
Encryption and Authentication
SSH WebSockets utilize strong encryption algorithms, such as AES-256, to protect data in transit. This encryption ensures that even if data is intercepted, it remains unreadable to unauthorized parties. Additionally, SSH WebSockets implement authentication mechanisms, including public-key cryptography, to verify the identity of clients and servers, preventing unauthorized access.
Integrity Protection
SSH WebSockets employ integrity protection mechanisms to detect and prevent data tampering during transmission. These mechanisms, such as message authentication codes (MACs), ensure that data remains unaltered and has not been tampered with.
Potential Vulnerabilities and Mitigation Strategies
While SSH WebSockets provide strong security, certain vulnerabilities and attack vectors may arise. These include:
- Man-in-the-Middle Attacks: In this scenario, an attacker intercepts and modifies data transmitted between the client and server. To mitigate this risk, SSH WebSockets should be used in conjunction with secure protocols like HTTPS.
- Denial-of-Service Attacks: Attackers may attempt to overwhelm a server with excessive traffic, causing it to become unavailable. Implementing rate-limiting mechanisms and deploying intrusion detection systems can help mitigate this threat.
SSH WebSocket Performance
SSH WebSockets leverage the full-duplex nature of the WebSocket protocol, providing a persistent and bi-directional communication channel between a client and a server. This section analyzes the performance characteristics of SSH WebSockets, identifying key factors that influence latency and throughput.
The latency of SSH WebSockets is influenced by several factors, including network conditions, the efficiency of the WebSocket implementation, and the computational overhead associated with SSH encryption and decryption. Network latency, determined by factors such as distance, congestion, and packet loss, can significantly impact the overall latency of SSH WebSockets.
Additionally, the efficiency of the WebSocket implementation, including the underlying transport protocol and the handling of control and data frames, can affect latency. Furthermore, the computational overhead associated with SSH encryption and decryption can introduce additional latency, particularly for high-bandwidth applications.
Throughput
The throughput of SSH WebSockets is influenced by factors such as network bandwidth, the efficiency of the WebSocket implementation, and the computational overhead associated with SSH encryption and decryption. Network bandwidth limitations, such as congested links or limited capacity, can restrict the maximum achievable throughput.
Additionally, the efficiency of the WebSocket implementation, including the underlying transport protocol and the handling of control and data frames, can impact throughput. Furthermore, the computational overhead associated with SSH encryption and decryption can introduce additional overhead, reducing the effective throughput, particularly for high-bandwidth applications.
Comparison with Alternative Technologies
SSH WebSockets offer several advantages over alternative technologies for secure communication, including:
- Encryption: SSH WebSockets provide end-to-end encryption, ensuring the confidentiality and integrity of data in transit.
- Authentication: SSH WebSockets support various authentication mechanisms, including password-based authentication, public-key authentication, and certificate-based authentication, allowing for secure access control.
- Multiplexing: SSH WebSockets allow for multiplexing of multiple data channels over a single WebSocket connection, enabling efficient utilization of network resources.
- Tunneling: SSH WebSockets can be used to tunnel other protocols, such as HTTP, FTP, or Telnet, over a secure connection, providing a versatile and flexible communication mechanism.
However, SSH WebSockets may exhibit higher latency and lower throughput compared to alternative technologies, such as HTTP long-polling or WebSocket over TLS (WSS), due to the additional overhead associated with SSH encryption and decryption.
SSH WebSocket Protocols
SSH WebSockets utilize a combination of protocols to establish and maintain secure WebSocket connections. These protocols work together to provide authentication, encryption, and data transfer capabilities.
The primary protocols involved in SSH WebSockets are:
- WebSocket: The WebSocket protocol enables full-duplex communication between a client and a server over a single TCP connection. It allows for real-time, bi-directional data exchange, making it suitable for interactive applications and data streaming.
- SSH: The SSH protocol is a secure network protocol that provides secure remote login and other secure network services. It establishes an encrypted channel between two parties, ensuring the confidentiality and integrity of the data transmitted.
- Additional Protocols: Depending on the specific application and requirements, additional protocols may be used in conjunction with SSH WebSockets. These could include protocols for application-specific data formats, compression, or security enhancements.
Role of Each Protocol
Each protocol plays a specific role in establishing and maintaining a secure WebSocket connection:
- WebSocket: The WebSocket protocol handles the establishment and management of the WebSocket connection. It defines the framing and messaging format used for data exchange, enabling real-time, bi-directional communication.
- SSH: The SSH protocol is responsible for providing secure authentication and encryption. It establishes a secure channel between the client and server, ensuring that all data transmitted over the WebSocket connection is encrypted and protected from eavesdropping.
- Additional Protocols: Additional protocols, if used, provide application-specific functionality or enhancements. They may define data formats, compression algorithms, or security mechanisms tailored to the specific application requirements.
SSH WebSocket Libraries and Tools
To facilitate the integration of SSH WebSockets into various applications, numerous libraries and tools have been developed in diverse programming languages. These resources provide a simplified and structured approach for developers to establish secure and efficient SSH WebSocket connections.
The availability of these libraries and tools empowers developers to leverage the benefits of SSH WebSockets, including secure data transmission, real-time communication, and remote access capabilities, without the need for extensive coding efforts. They offer a range of functionalities, from establishing SSH WebSocket connections to sending and receiving data securely, making them invaluable assets for developers working with SSH WebSockets.
Libraries for SSH WebSockets
Several programming languages have dedicated libraries specifically designed for working with SSH WebSockets. These libraries provide a comprehensive set of features and functions, simplifying the development process and enabling developers to focus on the core aspects of their applications.
- Python: The ssh-websocket library offers a straightforward and well-documented interface for establishing SSH WebSocket connections and sending/receiving data.
- JavaScript: The novnc library provides a comprehensive solution for implementing SSH WebSockets in JavaScript applications, featuring support for various protocols and encryption algorithms.
- Java: The hawtdispatch library offers a versatile toolkit for working with SSH WebSockets in Java applications, including support for secure data transmission and real-time communication.
- C++: The libssh2 library is a widely used and feature-rich library for SSH connectivity in C++ applications, providing support for SSH WebSockets and a range of other SSH-related functionalities.
Tools for SSH WebSockets
In addition to libraries, there are also dedicated tools available to assist developers in working with SSH WebSockets. These tools provide graphical user interfaces (GUIs) or command-line interfaces (CLIs) that simplify the process of establishing SSH WebSocket connections, sending and receiving data, and managing SSH WebSocket sessions.
- PuTTY: PuTTY is a popular SSH and Telnet client that offers support for SSH WebSockets, enabling users to establish secure connections to remote servers and communicate with them in real time.
- KiTTY: KiTTY is a fork of PuTTY that provides enhanced features and customization options, including support for SSH WebSockets, making it a versatile tool for working with SSH-based applications.
- MobaXterm: MobaXterm is a comprehensive terminal emulator and SSH client that includes support for SSH WebSockets, providing a user-friendly interface for managing SSH connections and transferring data securely.
SSH WebSocket Deployment
SSH WebSocket deployment involves setting up and configuring the necessary components for secure and reliable SSH WebSocket communication in a production environment. It encompasses tasks such as server configuration, firewall rule management, and load balancing strategies.
Server Configuration
SSH WebSocket server configuration involves setting up the necessary software and configuring parameters for secure communication. This includes installing and configuring an SSH server, such as OpenSSH, and enabling the WebSocket protocol. Additionally, authentication mechanisms, such as password-based or public key authentication, should be configured to ensure secure access to the SSH WebSocket server.
Firewall Rules
Firewall rules are crucial for controlling access to the SSH WebSocket server and protecting it from unauthorized access. These rules specify which network ports and IP addresses are allowed to connect to the server. Proper firewall configuration ensures that only authorized clients can establish SSH WebSocket connections, while blocking malicious attempts.
Load Balancing Strategies
In scenarios where there is a high volume of SSH WebSocket connections, load balancing strategies can be employed to distribute the load across multiple servers. This improves scalability and ensures that all clients experience consistent performance. Load balancers can be configured to distribute connections based on various factors, such as server load, client location, or connection type.
SSH WebSocket Troubleshooting
SSH WebSockets, despite their robust nature, may encounter various challenges and issues. Identifying these problems and implementing effective troubleshooting techniques can ensure seamless connectivity, authentication, and overall performance.
Troubleshooting SSH WebSockets involves identifying common issues and applying suitable solutions to resolve connection problems, authentication errors, and other challenges. Here are some common issues and troubleshooting tips:
Connection Problems
SSH WebSocket connection problems can arise due to various factors. Some common causes and troubleshooting tips include:
- Incorrect URL or Port: Verify that the WebSocket URL and port are correct. Ensure that the WebSocket server is listening on the specified port and that the client is attempting to connect to the correct address.
- Firewall or Proxy Issues: Check if a firewall or proxy is blocking the WebSocket connection. Configure firewall rules to allow WebSocket traffic or configure the proxy to support WebSocket connections.
- Network Connectivity: Ensure that there is a stable network connection between the client and the server. Check for any network issues or connectivity problems that may be preventing the WebSocket connection from being established.
Authentication Errors
SSH WebSocket authentication errors can occur due to incorrect credentials or misconfiguration. Some common causes and troubleshooting tips include:
- Invalid Credentials: Verify that the username and password provided for authentication are correct. Ensure that the user has the necessary permissions to establish a WebSocket connection.
- Incorrect Authentication Method: Check if the correct authentication method is being used. Some SSH WebSocket servers may support multiple authentication methods, such as password-based authentication or public key authentication. Ensure that the client and server are using the same authentication method.
- Misconfigured Server: Verify that the SSH WebSocket server is configured correctly. Check the server logs for any errors or warnings related to authentication.
Other Common Issues
In addition to connection problems and authentication errors, other common issues that may arise with SSH WebSockets include:
- Slow Performance: If the SSH WebSocket connection is slow or experiencing performance issues, check the network bandwidth and latency. Ensure that there are no network bottlenecks or high latency that may be affecting the WebSocket performance.
- Data Corruption: In some cases, data corruption may occur during the WebSocket transmission. This can be caused by network issues or incorrect data handling on either the client or server side. Implement error-checking mechanisms to detect and handle data corruption.
- Unexpected Termination: If the SSH WebSocket connection terminates unexpectedly, check the server logs for any errors or warnings. This can help identify the cause of the termination and provide insights for troubleshooting.
SSH WebSocket Standards and RFCs

The standardization of SSH WebSockets ensures interoperability, security, and adherence to best practices in the implementation and use of SSH over WebSocket connections. By following these standards, developers can create SSH WebSocket applications that are compatible with various platforms and environments, reducing the risk of security vulnerabilities and improving the overall performance and reliability of SSH WebSocket connections.
RFC 6455: The WebSocket Protocol
RFC 6455 defines the WebSocket protocol, which provides a full-duplex communication channel over a single TCP connection. It establishes the framework for establishing WebSocket connections, handling data transfer, and closing connections. Adherence to RFC 6455 ensures that SSH WebSocket applications can communicate seamlessly with other WebSocket-compliant applications and servers.
RFC 4251: The Secure Shell (SSH) Protocol Architecture
RFC 4251 defines the architecture and fundamental principles of the SSH protocol, including the transport layer, authentication mechanisms, and connection management. It provides a foundation for understanding the integration of SSH with WebSocket technology. By following RFC 4251, developers can ensure that SSH WebSocket applications adhere to the core principles of SSH security and interoperability.
RFC 8332: SSH over WebSocket
RFC 8332 specifically addresses the use of SSH over WebSocket, defining the mechanisms for tunneling SSH traffic over WebSocket connections. It Artikels the process of establishing SSH WebSocket connections, handling data transfer, and managing connection state. Adherence to RFC 8332 ensures that SSH WebSocket applications can interoperate with other SSH WebSocket-compliant applications and servers, promoting seamless and secure communication.
SSH WebSocket Future Trends
The future of SSH WebSockets holds immense potential, driven by emerging technologies and industry trends. As the digital landscape continues to evolve, SSH WebSockets are poised to play a pivotal role in shaping the way we access and manage remote systems and applications.
Advancements in Security and Authentication
The security and authentication mechanisms employed by SSH WebSockets are expected to undergo significant advancements. Innovations in cryptography, such as post-quantum cryptography, will further enhance the security of SSH WebSockets, mitigating the risk of unauthorized access and data breaches. Additionally, the integration of biometrics and multi-factor authentication will provide additional layers of security, ensuring that only authorized users can access remote systems.
Enhanced Performance and Scalability
The performance and scalability of SSH WebSockets are likely to improve significantly. The adoption of modern protocols, such as QUIC (Quick UDP Internet Connections), will optimize data transfer and reduce latency, enabling faster and more responsive remote access. Moreover, advancements in hardware and software technologies will allow SSH WebSockets to handle increased traffic loads and support more concurrent connections, making them suitable for large-scale deployments.
Integration with Emerging Technologies
SSH WebSockets are expected to be integrated with emerging technologies, such as artificial intelligence (AI) and machine learning (ML). These technologies can be leveraged to automate tasks, enhance security, and improve the overall user experience. For instance, AI-powered algorithms can analyze network traffic patterns and identify potential threats, while ML models can be trained to detect and respond to security incidents in real-time.
New Applications and Use Cases
The versatility of SSH WebSockets will lead to the development of new applications and use cases. For example, SSH WebSockets can be utilized to enable remote access to virtual and augmented reality environments, facilitating immersive experiences for users. Additionally, SSH WebSockets can be integrated with Internet of Things (IoT) devices, allowing for secure and efficient remote management and control of IoT devices from anywhere.
Closing Summary
As we reach the end of our exploration, it’s evident that SSH WebSockets have revolutionized secure communication. Their ability to safeguard data, optimize performance, and empower diverse applications makes them an indispensable tool in today’s digital age. As technology continues to evolve, SSH WebSockets stand poised to play an even more pivotal role in shaping the future of secure communication.