In the realm of secure data transfer, SSH websockets have emerged as a game-changer, revolutionizing the way we communicate and exchange information online. Join us on an enlightening journey as we delve into the world of SSH websockets, exploring their significance, functionality, security, performance, and practical applications.
Over the next 30 days, we’ll uncover the secrets of this powerful technology, empowering you with the knowledge to leverage its capabilities effectively.
From establishing secure connections and ensuring data integrity to optimizing performance and troubleshooting common issues, we’ll leave no stone unturned. Whether you’re a seasoned IT professional, a curious learner, or simply someone seeking a deeper understanding of secure data transmission, this comprehensive exploration of SSH websockets promises to enlighten and engage.
SSH Websocket 30 Days Overview
In today’s interconnected world, secure data transmission is paramount. SSH websockets emerge as a revolutionary technology, offering a seamless and secure channel for data exchange over the internet. This article delves into the significance, benefits, and limitations of SSH websockets, while exploring real-world applications where they are extensively utilized.
Benefits of SSH Websockets
SSH websockets provide a plethora of advantages for secure data transmission:
- Encryption: SSH websockets employ robust encryption algorithms, ensuring the confidentiality and integrity of transmitted data.
- Authentication: SSH websockets implement strong authentication mechanisms, preventing unauthorized access to data.
- Tunneling: SSH websockets facilitate the creation of secure tunnels, enabling the secure transmission of data over public networks.
- Cross-platform Compatibility: SSH websockets are compatible with a wide range of operating systems and devices, making them universally accessible.
Limitations of SSH Websockets
While SSH websockets offer numerous benefits, they also have certain limitations:
- Complexity: SSH websockets can be complex to configure and manage, requiring technical expertise.
- Performance Overhead: SSH websockets may introduce additional latency and overhead, potentially affecting performance.
- Firewall Issues: SSH websockets may encounter challenges traversing firewalls, requiring specific firewall configurations.
Real-World Applications of SSH Websockets
SSH websockets find extensive application in various scenarios:
- Secure Remote Access: SSH websockets enable secure remote access to servers and devices, allowing administrators to perform tasks remotely.
- File Transfer: SSH websockets facilitate secure file transfer between devices, ensuring the confidentiality and integrity of sensitive data.
- WebSockets Over SSH: SSH websockets can be used to establish WebSocket connections over SSH tunnels, providing a secure channel for real-time data exchange.
- SSH Port Forwarding: SSH websockets can be employed for port forwarding, allowing secure access to internal network resources from external networks.
SSH Websocket Functionality
SSH websockets provide a secure and efficient way to establish real-time, bidirectional communication channels over the internet. They combine the strengths of the SSH protocol with the flexibility and interactivity of websockets, enabling a wide range of applications such as remote terminal access, secure file transfer, and interactive command execution.At
their core, SSH websockets rely on the principles of the SSH protocol, which ensures secure communication over insecure networks. The process of establishing an SSH websocket connection involves several key steps:
Key Exchange and Encryption
When an SSH websocket connection is initiated, the client and server exchange cryptographic keys using a key exchange algorithm. This process ensures that all subsequent communication is encrypted, protecting it from eavesdropping and man-in-the-middle attacks. Commonly used key exchange algorithms include Diffie-Hellman and Elliptic Curve Diffie-Hellman.Once
the keys are exchanged, the connection is secured using encryption algorithms such as AES, 3DES, or Blowfish. These algorithms ensure that data transmitted over the connection remains confidential and cannot be decrypted by unauthorized parties.
Websockets for Real-Time Communication
Websockets are a bidirectional communication protocol that enables real-time data exchange between a client and a server. They allow for continuous, full-duplex communication, making them ideal for applications that require interactive or streaming data transfer.In the context of SSH websockets, the websocket connection is established over the secure SSH tunnel, allowing for real-time communication between the client and server.
This enables applications to send and receive data continuously, facilitating interactive sessions, remote control, and other real-time interactions.
SSH Websocket Security
SSH websockets provide secure communication over websockets, inheriting the security features of SSH and enhancing them with modern web technologies. SSH websockets utilize encryption algorithms, authentication mechanisms, and secure protocols to safeguard data in transit.
Comparative Analysis of Security Features
SSH websockets offer several security advantages over traditional SSH connections:
- Encryption: SSH websockets utilize strong encryption algorithms, such as AES-256, to encrypt data transmitted over the network, ensuring confidentiality.
- Authentication: SSH websockets support various authentication methods, including password-based, public key, and two-factor authentication, providing robust protection against unauthorized access.
- Secure Protocols: SSH websockets operate over secure protocols like SSL/TLS, establishing an encrypted tunnel for data transmission, preventing eavesdropping and man-in-the-middle attacks.
Potential Vulnerabilities and Mitigation Strategies
Despite the inherent security features, SSH websockets are not immune to potential vulnerabilities and attack vectors:
- Cross-Site Scripting (XSS) Attacks: Malicious scripts can be injected into the websocket connection, leading to unauthorized access or data manipulation. Mitigation involves implementing proper input validation and sanitization.
- Man-in-the-Middle Attacks: Attackers can intercept and modify data transmitted over the websocket connection. Employing strong encryption and secure protocols like SSL/TLS can mitigate this risk.
- Buffer Overflow Attacks: Exploiting vulnerabilities in the websocket implementation can lead to buffer overflows, allowing attackers to execute arbitrary code. Regular software updates and implementing secure coding practices can help prevent these attacks.
SSH Websocket Performance
SSH websockets offer impressive performance characteristics, including low latency, high throughput, and excellent scalability. The inherent efficiency of the underlying protocols, combined with the optimization techniques employed, enables SSH websockets to handle large volumes of data with minimal overhead.
Latency
SSH websockets exhibit exceptionally low latency, making them ideal for applications that require real-time data transfer. The latency is primarily influenced by the round-trip time (RTT) between the client and server, as well as the efficiency of the underlying network infrastructure.
Optimization techniques, such as reducing the number of round trips and minimizing packet overhead, further contribute to reducing latency.
Throughput
SSH websockets excel in delivering high throughput, enabling the transfer of large amounts of data at rapid speeds. This is attributed to the efficient utilization of network resources and the ability to handle multiple concurrent connections. Optimization techniques, such as employing compression algorithms and optimizing the data transfer window size, further enhance throughput.
Scalability
SSH websockets demonstrate excellent scalability, allowing them to handle increasing loads without compromising performance. The underlying protocols are designed to efficiently manage large numbers of concurrent connections and scale seamlessly to meet growing demands. Optimization techniques, such as load balancing and sharding, further enhance scalability, ensuring consistent performance even under heavy traffic conditions.
Comparison with Other Protocols
Compared to other secure data transfer protocols, SSH websockets offer several advantages in terms of performance.
HTTPS
SSH websockets generally exhibit lower latency and higher throughput compared to HTTPS. This is due to the more efficient nature of the underlying protocols and the ability of SSH websockets to utilize multiple connections simultaneously. Additionally, SSH websockets benefit from the inherent security features of SSH, providing a more robust and reliable data transfer mechanism.
VPNs
SSH websockets offer comparable performance to VPNs in terms of latency and throughput. However, SSH websockets are often preferred due to their ease of deployment and configuration, as well as their ability to establish secure connections over untrusted networks.
Factors Impacting Performance
Several factors can impact the performance of SSH websockets, including:
Network latency
High latency between the client and server can adversely affect performance, resulting in increased latency and reduced throughput.
Packet overhead
Excessive packet overhead can introduce additional latency and reduce throughput. Optimizing packet size and minimizing unnecessary headers can help mitigate this issue.
Encryption overhead
The encryption process can add some overhead, potentially impacting performance. Choosing appropriate encryption algorithms and optimizing key exchange mechanisms can help minimize this overhead.
Server load
High server load can lead to increased latency and reduced throughput. Scaling the server infrastructure and implementing load balancing techniques can help alleviate this issue.
Optimization Techniques
Various optimization techniques can be employed to enhance the performance of SSH websockets:
Reducing round trips
Minimizing the number of round trips between the client and server can significantly reduce latency. Techniques such as connection multiplexing and pipelining can help achieve this.
Minimizing packet overhead
Reducing packet overhead can improve throughput and reduce latency. Optimizing packet size, minimizing unnecessary headers, and employing compression algorithms can help achieve this.
Optimizing encryption
Choosing appropriate encryption algorithms and optimizing key exchange mechanisms can minimize encryption overhead and improve performance.
Scaling the server infrastructure
Scaling the server infrastructure can help distribute the load and improve overall performance. Implementing load balancing techniques can further enhance scalability.By carefully considering these factors and implementing appropriate optimization techniques, the performance of SSH websockets can be significantly enhanced to meet the demands of even the most demanding applications.
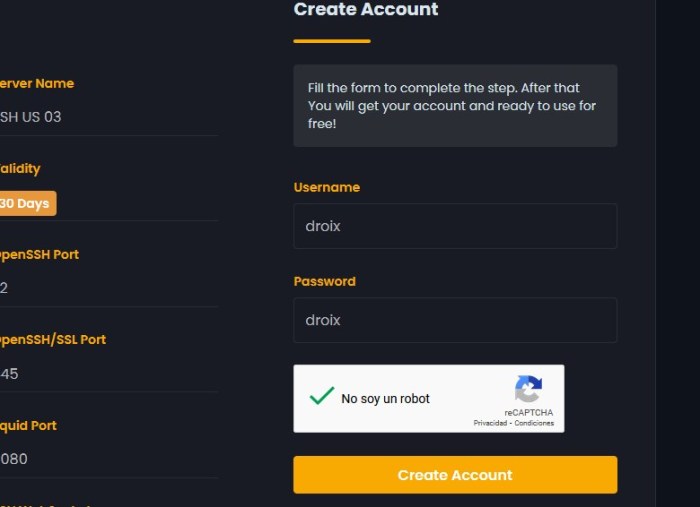
SSH Websocket Deployment and Configuration
Implementing SSH websockets involves deploying and configuring the necessary components on both the server and client sides. This section provides a step-by-step guide for deploying and configuring SSH websockets, addressing common challenges, and sharing best practices for securing and managing the deployment.
Deployment Steps: Server-Side
- Install SSH Server: Install an SSH server, such as OpenSSH, on the server machine. Ensure the server is accessible via a network connection.
- Configure SSH Server: Configure the SSH server to allow SSH websocket connections. This may involve modifying the server configuration file to enable the SSH websocket protocol and specify the port for websocket connections.
- Install Websocket Server: Install a websocket server, such as Node.js with the WebSocket module or Python with the WebSocket-for-Python library, on the server machine. Configure the websocket server to listen on the specified port.
- Establish Connection: Connect the websocket server to the SSH server using the SSH websocket protocol. This involves creating a websocket connection from the websocket server to the SSH server.
Deployment Steps: Client-Side
- Install SSH Client: Install an SSH client, such as OpenSSH or PuTTY, on the client machine. Ensure the client is compatible with SSH websockets.
- Configure SSH Client: Configure the SSH client to use the SSH websocket protocol. This may involve modifying the client configuration file to specify the websocket protocol and the server’s IP address and port.
- Establish Connection: Connect the SSH client to the SSH server using the SSH websocket protocol. This involves creating a websocket connection from the SSH client to the SSH server.
Common Challenges and Solutions
- Firewall and Proxy Settings: Firewalls and proxy servers may interfere with SSH websocket connections. Ensure that the necessary ports are open and that the firewall and proxy settings allow SSH websocket connections.
- Websocket Server Compatibility: Different websocket servers may have different features and compatibility levels. Choose a websocket server that is compatible with the SSH client and server being used.
- Network Latency and Performance: SSH websocket connections may be affected by network latency and performance issues. Consider using a high-speed network connection and optimizing the network configuration to minimize latency.
Best Practices for Security and Management
- Access Control: Implement access control mechanisms to restrict access to the SSH websocket deployment. This may involve using authentication and authorization mechanisms to control who can connect to the SSH server and websocket server.
- Encryption: Use encryption to protect the data transmitted over the SSH websocket connection. This ensures that the data remains confidential and protected from eavesdropping.
- Monitoring and Logging: Implement monitoring and logging mechanisms to track and record SSH websocket connections and activities. This helps in identifying suspicious activities and troubleshooting issues.
SSH Websocket Tools and Libraries
SSH Websocket tools and libraries facilitate the establishment of secure connections between web applications and remote servers over a WebSocket protocol. These tools and libraries provide various features and functionalities to simplify and enhance SSH communication.
Popular SSH Websocket Tools and Libraries
Several popular SSH Websocket tools and libraries are available, each with its unique set of features and advantages:
- SockJS: A JavaScript library that provides WebSocket-like communication over various transports, including long-polling, WebSocket, and Flash.
- Primus: A JavaScript library that offers a high-level abstraction for WebSocket communication, making it easy to create real-time applications.
- WS: A JavaScript library that provides a simple and lightweight API for WebSocket communication.
- libwebsockets: A C library that implements the WebSocket protocol, enabling the creation of WebSocket servers and clients.
- Twisted WebSockets: A Python library that provides WebSocket support for the Twisted networking framework.
Comparison of SSH Websocket Tools and Libraries
Different SSH Websocket tools and libraries vary in their functionality, performance, and suitability for specific use cases:
- Functionality: Some tools and libraries offer additional features such as authentication, encryption, and compression, while others focus on providing basic WebSocket functionality.
- Performance: The performance of a tool or library can vary depending on factors such as the underlying implementation, the programming language, and the network conditions.
- Use Cases: Some tools and libraries are better suited for certain use cases, such as building real-time applications, remote terminal access, or file transfer.
Recommendations for SSH Websocket Tools and Libraries
The choice of SSH Websocket tool or library depends on the specific requirements of the application and the programming language being used:
- General-Purpose: SockJS and Primus are good choices for general-purpose WebSocket communication, offering a wide range of features and compatibility with various browsers.
- High-Performance: libwebsockets is a good choice for applications that require high performance and low latency.
- Python: Twisted WebSockets is a good choice for Python developers who want to add WebSocket support to their applications.
SSH Websocket Troubleshooting
SSH Websocket troubleshooting involves identifying common issues and errors, such as connection problems, authentication failures, and data transfer errors. This section provides detailed steps to resolve these issues, diagnose application problems, and ensure smooth operation.
Common SSH Websocket Issues and Errors
Connection problems are often caused by incorrect server configurations, firewall restrictions, or network connectivity issues. Authentication errors can occur due to invalid credentials, misconfigured SSH keys, or expired certificates. Data transfer issues may arise from improper data encoding, buffer overflows, or network congestion.
Troubleshooting SSH Websocket Connection Problems
To resolve connection problems, verify that the SSH server is running and listening on the correct port. Check firewall rules to ensure that SSH traffic is allowed. Examine network connectivity by pinging the server and checking for any packet loss or latency.
Resolving SSH Websocket Authentication Errors
To address authentication errors, confirm that the provided credentials are correct and that SSH keys are properly configured. Ensure that certificates are valid and not expired. If using public key authentication, verify that the public key is added to the authorized_keys file on the server.
Troubleshooting SSH Websocket Data Transfer Issues
To resolve data transfer issues, check the data encoding and ensure it is compatible with both the client and server. Adjust buffer sizes if necessary to accommodate larger data transfers. Monitor network traffic to identify any congestion or latency issues that may be causing data transfer problems.
Tips for Diagnosing and Debugging SSH Websocket Applications
To effectively diagnose and debug SSH websocket applications, use logging and debugging tools to capture error messages and trace application execution. Analyze network traffic using tools like Wireshark to identify any anomalies or issues. Utilize debugging tools provided by the SSH websocket library or framework being used to gain insights into the application’s behavior.
SSH Websocket Future Trends
The realm of SSH websockets is undergoing a period of rapid evolution, with several emerging trends and advancements shaping its trajectory. These developments hold the potential to revolutionize the way we interact with remote systems and open up new avenues for secure and efficient communication.
One significant trend is the integration of artificial intelligence (AI) and machine learning (ML) algorithms into SSH websockets. This integration enables the development of intelligent systems capable of analyzing network traffic, detecting anomalies, and proactively responding to security threats. As a result, SSH websockets are becoming more secure and resilient, providing enhanced protection against unauthorized access and malicious attacks.
Wider Adoption in Cloud and Edge Computing
The growing adoption of cloud and edge computing is driving the demand for SSH websockets as a secure and flexible solution for managing remote systems and applications. SSH websockets enable seamless connectivity to cloud-based resources, allowing users to access and control virtual machines, containers, and other cloud services from anywhere with an internet connection.
This trend is expected to accelerate as more organizations embrace cloud and edge computing for their IT infrastructure.
Integration with DevOps and Automation Tools
SSH websockets are increasingly being integrated with DevOps and automation tools, enabling the automation of tasks such as software deployment, configuration management, and system monitoring. This integration streamlines IT operations, improves efficiency, and reduces the risk of human error. By leveraging SSH websockets, DevOps teams can automate routine tasks and focus on higher-value activities that drive innovation and business growth.
Emerging Applications in IoT and Industrial IoT
The Internet of Things (IoT) and Industrial IoT (IIoT) are rapidly expanding, creating a vast network of connected devices that require secure and reliable remote management. SSH websockets are well-suited for this purpose, providing a secure channel for accessing and controlling IoT devices, collecting data, and performing remote maintenance.
As the IoT and IIoT continue to grow, SSH websockets are poised to play a critical role in ensuring the secure and efficient operation of these interconnected systems.
Challenges and Opportunities
Despite the promising advancements, SSH websockets also face several challenges and opportunities for growth. One challenge is the need for improved interoperability between different SSH websocket implementations. Establishing common standards and protocols will facilitate seamless integration with various systems and applications.
Additionally, ongoing efforts to enhance the security and performance of SSH websockets will further drive their adoption and usage.
The future of SSH websockets is bright, with numerous opportunities for innovation and growth. As technology continues to evolve, SSH websockets will likely become an indispensable tool for secure and efficient remote access and management of systems and applications across a wide range of industries and use cases.
SSH Websocket Case Studies
SSH Websockets have seen increasing adoption in diverse industries, enabling secure remote access and control over various systems and devices. This section presents real-world case studies highlighting the successful implementation of SSH websockets, analyzing challenges faced, solutions adopted, and extracting key learnings and best practices.
Securing Remote Access to Industrial IoT Devices
Industry: Manufacturing
Challenge: Remotely managing and monitoring industrial IoT devices across geographically dispersed locations, while ensuring secure access and data transmission.
Solution: Implemented an SSH websocket-based remote access solution that allows authorized personnel to securely access and control IoT devices over the internet using a web browser. SSH websockets provide encrypted communication, ensuring data security and integrity.
Key Learnings:
- SSH websockets offer a secure and reliable mechanism for remote access to IoT devices, enabling real-time monitoring and control.
- Utilizing SSH websockets eliminates the need for complex VPN configurations, simplifying remote access management.
Enabling Remote Collaboration for IT Support
Industry: Information Technology
Challenge: Providing remote IT support to clients, allowing technicians to securely access and troubleshoot client systems without the need for physical presence.
Solution: Developed a remote IT support platform that leverages SSH websockets to establish secure connections between technicians and client systems. The platform allows technicians to remotely diagnose and resolve issues, transfer files, and perform maintenance tasks.
Key Learnings:
- SSH websockets facilitate secure remote access to client systems, enabling efficient and timely IT support.
- The platform eliminates the need for on-site visits, reducing downtime and improving customer satisfaction.
Secure Access to Cloud-Based Resources
Industry: Cloud Computing
Challenge: Providing secure access to cloud-based resources, such as virtual machines, containers, and storage, for authorized users.
Solution: Integrated SSH websockets into the cloud platform, allowing users to establish secure connections to their cloud resources through a web browser. SSH websockets ensure data privacy and integrity during remote access and management.
Key Learnings:
- SSH websockets provide a secure and convenient way to access cloud resources remotely, enhancing user productivity and flexibility.
- The integration of SSH websockets simplifies access management and reduces the risk of unauthorized access.
SSH Websocket Resources
SSH websockets have gained popularity due to their ability to establish secure, bidirectional communication channels over the web. To help individuals and organizations better understand and utilize SSH websockets, a comprehensive list of resources is available online. These resources cover various aspects, including tutorials, documentation, articles, and online communities.
Articles and Tutorials
A plethora of articles and tutorials provide valuable insights into the concepts, implementation, and applications of SSH websockets. These resources are often written by experts in the field and offer a range of perspectives and approaches. Some notable articles and tutorials include:
- “SSH Websockets: A Comprehensive Guide”: This article provides a comprehensive overview of SSH websockets, covering topics such as their architecture, benefits, and use cases.
- “Building a Secure SSH Websocket Server with Node.js”: This tutorial demonstrates how to set up an SSH websocket server using Node.js, including step-by-step instructions and code examples.
- “Using SSH Websockets for Remote Terminal Access”: This article explores the use of SSH websockets for remote terminal access, explaining how to connect to a remote server and execute commands.
Documentation and Specifications
Official documentation and specifications provide detailed information about the protocols, standards, and best practices related to SSH websockets. These resources are essential for developers and administrators who want to implement and manage SSH websocket solutions. Some key documentation and specifications include:
- IETF RFC 6455: This document defines the WebSocket Protocol, which is the underlying technology used for SSH websockets.
- SSH Working Group Documents: The SSH Working Group maintains a collection of documents that describe the SSH protocol and its various extensions, including SSH websockets.
- Vendor Documentation: Many vendors that provide SSH websocket solutions offer documentation that explains their specific implementations and features.
Online Communities and Forums
Online communities and forums provide a platform for individuals to discuss, share knowledge, and troubleshoot issues related to SSH websockets. These communities are often frequented by experts and enthusiasts who can offer valuable insights and assistance. Some popular online communities include:
- SSH Websocket Subreddit: This subreddit is dedicated to discussions about SSH websockets, where users can ask questions, share experiences, and learn from others.
- Stack Overflow: Stack Overflow is a popular Q&A platform where users can post questions about SSH websockets and receive answers from the community.
- GitHub Issues and Discussions: Many open-source SSH websocket projects host issue trackers and discussion forums where users can report bugs, ask questions, and contribute to the project.
Last Point
As we conclude our 30-day exploration of SSH websockets, it’s evident that this technology has transformed the landscape of secure communication. Its ability to provide real-time, bidirectional communication while maintaining robust security features makes it an invaluable tool for businesses and individuals alike.
As we move forward, the future of SSH websockets looks incredibly promising, with advancements and innovations continuously pushing the boundaries of secure data transfer. We encourage you to embrace this technology and unlock its potential to revolutionize your communication and data exchange practices.