SSH.SSHSlowdns.com – In the realm of remote access, SSH WebSockets have emerged as a game-changer, offering a secure and versatile way to connect to and manage systems from anywhere in the world. This comprehensive guide will delve into the intricacies of SSH WebSockets, exploring their benefits, use cases, setup, security considerations, and more.
Get ready to unlock the power of SSH WebSockets and revolutionize your remote access experience.
With the increasing adoption of cloud computing and IoT devices, the need for secure and reliable remote access solutions has become paramount. SSH WebSockets provide an elegant solution by combining the robust security of SSH with the flexibility and ease of use of WebSockets, making them an ideal choice for a wide range of applications.
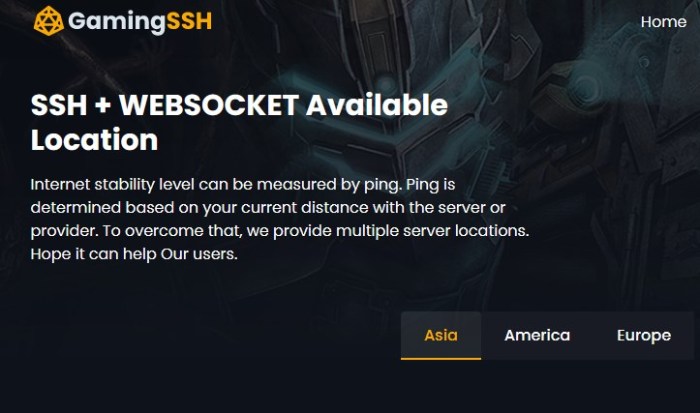
Overview of SSH WebSockets
SSH WebSockets, an innovative technology, enables secure and interactive remote access to servers and devices via a web browser. By leveraging the WebSocket protocol, SSH WebSockets establish a persistent, bidirectional communication channel over HTTP, eliminating the need for traditional SSH clients.
This approach provides enhanced flexibility and accessibility, allowing users to connect to remote systems from any device with a modern web browser.SSH WebSockets offer numerous benefits, including:
- Cross-platform compatibility: Access remote systems from any device with a web browser, regardless of operating system or device type.
- Enhanced security: WebSockets provide a secure and encrypted communication channel, protecting data in transit from eavesdropping and tampering.
- Simplified access: Eliminate the need for dedicated SSH clients, making remote access more convenient and user-friendly.
SSH WebSockets find applications in various real-world scenarios, such as:
- Remote system administration: Manage and configure remote servers from anywhere with a web browser, enabling quick troubleshooting and maintenance.
- Web-based terminals: Provide access to command-line interfaces within web browsers, allowing users to execute commands and scripts remotely.
- Interactive applications: Develop web-based applications that interact with remote systems, enabling remote monitoring, control, and data visualization.
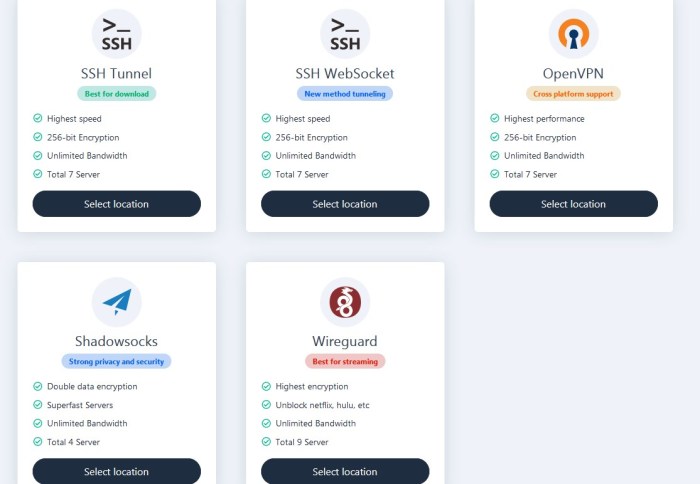
Setting Up SSH WebSockets
Setting up SSH WebSockets involves configuring both the server and client sides to enable secure, browser-based SSH connections. Here’s a step-by-step guide:
Server Configuration
- Install an SSH WebSocket server, such as “websocket-ssh” or “ws-ssh-server.”
- Configure the server to listen on a specific port (e.g., 8080) for incoming WebSocket connections.
- Enable SSH authentication and specify the allowed users and authentication methods (e.g., password, public key).
Client Configuration
- Use a WebSocket-compatible browser or JavaScript library (e.g., “socket.io” or “websocket-stream”).
- Establish a WebSocket connection to the server using the specified port and server address.
- Authenticate using the SSH credentials (e.g., username, password, or private key).
Security Best Practices
- Use strong encryption protocols (e.g., AES-256) to protect data transmitted over the WebSocket connection.
- Limit access to the SSH WebSocket server by using firewalls or access control lists.
- Regularly update the SSH server and client software to patch security vulnerabilities.
Using SSH WebSockets
SSH WebSockets provide a secure and efficient way to establish a connection between a client and a server over the web. It allows for real-time, bidirectional communication, making it suitable for various remote access and data transfer tasks.
To use SSH WebSockets, a client initiates a connection to the server using the WebSocket protocol. Once the connection is established, the client can send and receive data using the WebSocket interface. The data is encrypted using SSH, ensuring secure transmission.
Sending and Receiving Data
SSH WebSockets support different methods for sending and receiving data. The most common methods are:
- Text Messages: Allows sending and receiving plain text messages.
- Binary Messages: Enables the transfer of binary data, such as files or images.
- Control Frames: Used for controlling the WebSocket connection, such as opening, closing, or sending ping/pong messages.
Common Use Cases
SSH WebSockets can be used for various tasks, including:
- Remote Shell Access: Allows users to access a remote shell on the server and execute commands.
- File Transfer: Enables secure file transfer between the client and the server.
- Interactive Applications: Supports running interactive applications, such as text editors or terminal emulators, over the WebSocket connection.
Security Considerations for SSH WebSockets
SSH WebSockets introduce a new set of security considerations compared to traditional SSH connections. The WebSocket protocol operates over an unencrypted channel, making it susceptible to eavesdropping and man-in-the-middle attacks. Additionally, the use of a browser-based client opens up the possibility of cross-site scripting (XSS) and other web-based vulnerabilities.To
secure SSH WebSockets, it is crucial to implement strong encryption, authentication, and authorization mechanisms. Encryption should be used to protect the data transmitted over the WebSocket connection, while authentication and authorization should be used to verify the identity of the client and grant access to the appropriate resources.Here
are some best practices for securing SSH WebSockets:
Encryption
Use TLS/SSL to encrypt the WebSocket connection. This will protect the data transmitted over the connection from eavesdropping and man-in-the-middle attacks.
Authentication
Use a strong authentication mechanism, such as public key authentication or two-factor authentication, to verify the identity of the client. This will prevent unauthorized users from accessing the SSH server.
Authorization
Implement authorization mechanisms to control access to the SSH server’s resources. This will ensure that users can only access the resources that they are authorized to access.
Additional Security Tips
- Use a firewall to block unauthorized access to the SSH server.
- Keep the SSH server software up to date with the latest security patches.
- Monitor the SSH server for suspicious activity.
- Use a web application firewall (WAF) to protect against web-based attacks, such as XSS.
Troubleshooting SSH WebSockets
SSH WebSockets can occasionally encounter issues, but understanding the common problems and troubleshooting steps can help resolve them efficiently.
One common problem is connection failures . Ensure that the SSH server is running and accessible, and that the WebSocket port is open. Check if firewalls or network configurations are blocking the connection.
Another issue is authentication problems . Verify that the credentials used for authentication are correct and that the SSH server is configured to allow WebSocket connections.
Slow or unstable connections can indicate network issues. Check the network connection, bandwidth availability, and any potential bottlenecks. Consider using a different network or optimizing the WebSocket connection parameters.
For further assistance, consult the SSH WebSocket documentation or seek support from online communities and forums.
SSH WebSockets in Cloud Environments
SSH WebSockets provide a secure and efficient way to access and manage cloud-based resources from a web browser. They are particularly useful for tasks that require remote command execution, file transfer, and interactive shell access.
Setting up SSH WebSockets in the cloud involves creating an SSH server on the cloud instance and configuring a WebSocket gateway to relay traffic between the browser and the SSH server. Several cloud providers, such as AWS and Azure, offer managed SSH WebSocket services that simplify the setup and management process.
Best Practices for Securing SSH WebSockets in the Cloud
Securing SSH WebSockets in the cloud is crucial to prevent unauthorized access and data breaches. Best practices include:
- Using strong encryption algorithms and key exchange mechanisms.
- Implementing authentication and authorization mechanisms to control access to the SSH server.
- Restricting access to the SSH WebSocket gateway from specific IP addresses or domains.
- Monitoring and logging SSH WebSocket activity for security auditing and incident response.
SSH WebSockets for IoT Devices
SSH WebSockets offer a secure and efficient way to connect and manage IoT devices remotely. By establishing a WebSocket connection over an SSH tunnel, IoT devices can securely transmit data, execute commands, and receive updates without exposing sensitive information to the public network.
Using SSH WebSockets in IoT environments comes with its own set of challenges and considerations. IoT devices often operate in constrained environments with limited resources, so the overhead of SSH WebSockets must be carefully managed. Additionally, the security of IoT devices is paramount, and proper authentication and authorization mechanisms must be implemented to prevent unauthorized access.
Examples of SSH WebSockets in IoT Applications
- Remote device management: SSH WebSockets can be used to remotely access and manage IoT devices, allowing administrators to perform tasks such as firmware updates, configuration changes, and troubleshooting.
- Data collection and monitoring: SSH WebSockets can be used to establish a secure channel for data collection from IoT devices. This data can be used for monitoring, analysis, and decision-making purposes.
- Device-to-device communication: SSH WebSockets can be used to facilitate secure communication between IoT devices, enabling them to exchange data and coordinate actions.
Future of SSH WebSockets
SSH WebSockets technology is continuously evolving, driven by the increasing need for secure and efficient remote access. Here are some key trends and developments to watch out for:
-
- -*Enhanced security features
SSH WebSockets is expected to incorporate advanced security measures, such as multi-factor authentication, biometrics, and encryption algorithms, to further strengthen its security posture.
- -*Enhanced security features
-*Improved performance and scalability
As the number of users and devices accessing remote systems increases, SSH WebSockets is expected to optimize its performance and scalability to handle increased traffic and maintain a seamless user experience.
-*Integration with cloud platforms
SSH WebSockets is likely to become more tightly integrated with cloud platforms, enabling seamless access to cloud-based resources and services.
-*Expanded use in IoT devices
The growing adoption of IoT devices is expected to drive the use of SSH WebSockets for secure remote management and control of these devices.
-*Support for new protocols
SSH WebSockets is expected to support additional protocols beyond SSH, such as Telnet and RDP, providing users with a wider range of remote access options.
These trends indicate that SSH WebSockets will continue to play a vital role in enabling secure and efficient remote access in the future.
As technology advances, SSH WebSockets is poised to evolve and adapt to meet the changing needs of users and organizations.