SSH.SSHSlowdns.com – In the realm of secure remote access, SSH stands as a titan, facilitating seamless connections between distant systems. Its versatility extends to its utilization of two fundamental transport protocols: TCP and UDP. This article delves into the intricacies of SSH’s relationship with these protocols, exploring their advantages, drawbacks, and implications for performance and security.
The choice between TCP and UDP for SSH hinges on the specific requirements of the connection. TCP, with its reliable and ordered delivery mechanism, excels in scenarios demanding stability and data integrity. UDP, on the other hand, prioritizes speed and efficiency, making it suitable for applications where latency is critical.
Port Numbers
SSH primarily utilizes TCP for its connections, with port 22 being the default port number.
However, SSH can also operate over UDP, using port 53 for DNS tunneling and port 123 for UDP-based SSH connections.
TCP
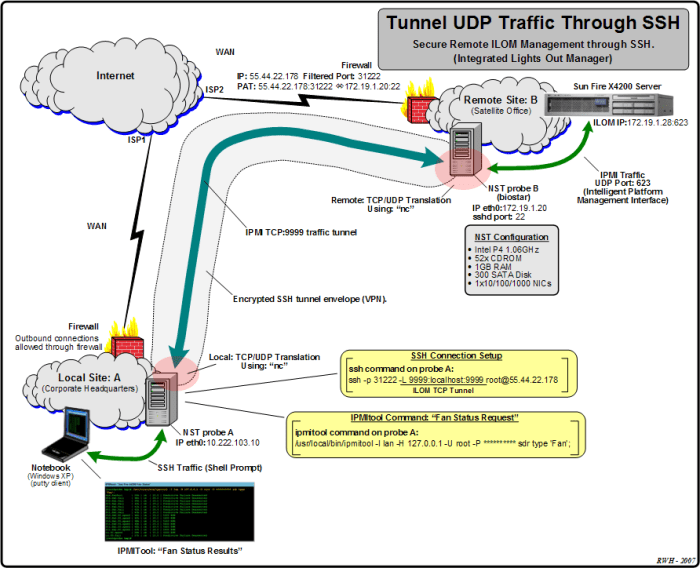
- TCP (Transmission Control Protocol) is a reliable, connection-oriented transport layer protocol.
- TCP establishes a virtual circuit between two endpoints, ensuring reliable data delivery and flow control.
- SSH over TCP provides a secure and reliable channel for remote access and data transfer.
UDP
- UDP (User Datagram Protocol) is a connectionless, unreliable transport layer protocol.
- UDP sends data packets without establishing a prior connection, making it faster but less reliable than TCP.
- SSH over UDP is used for specific scenarios, such as DNS tunneling or UDP-based SSH connections, where speed is prioritized over reliability.
TCP vs. UDP
When establishing an SSH connection, the choice between TCP and UDP as the underlying transport protocol is a crucial consideration. Each protocol offers distinct advantages and drawbacks that impact SSH performance and reliability.
TCP: Advantages and Disadvantages
- Reliability: TCP ensures reliable data delivery by establishing a connection-oriented session, guaranteeing that data packets are received in the correct order and without loss.
- Congestion Control: TCP incorporates congestion control mechanisms to prevent network congestion by dynamically adjusting the data transmission rate based on network conditions.
- Overhead: TCP introduces significant overhead due to its connection establishment and maintenance processes, which can impact performance in low-latency environments.
UDP: Advantages and Disadvantages
- Speed: UDP is a connectionless protocol, allowing for faster data transmission by eliminating the overhead associated with connection establishment and maintenance.
- Low Latency: UDP minimizes latency by sending data packets without waiting for acknowledgments, making it suitable for real-time applications.
- Unreliable: UDP does not guarantee reliable data delivery, as it does not establish a connection or track packet delivery status, which can lead to data loss.
Impact on SSH Performance
The choice between TCP and UDP for SSH depends on the specific requirements of the connection.
- Interactive SSH Sessions: TCP is preferred for interactive SSH sessions where reliable data delivery and congestion control are crucial for maintaining a stable and responsive connection.
- Bulk Data Transfer: UDP may be more suitable for bulk data transfer over high-speed networks where speed and low latency are prioritized over reliability.
Security Implications
When considering the security of SSH over TCP and UDP, several factors come into play. These protocols employ distinct encryption and authentication mechanisms, each with its own advantages and potential vulnerabilities.
Encryption
Both TCP and UDP support various encryption algorithms, including AES, 3DES, and Blowfish. TCP typically operates in a connection-oriented manner, establishing a secure channel before data transmission. This allows for more robust encryption and key exchange mechanisms, such as Diffie-Hellman and RSA.
UDP, on the other hand, is connectionless and operates on a datagram basis. While it supports encryption, the lack of a persistent connection may limit the effectiveness of certain encryption schemes.
Authentication
SSH over TCP and UDP relies on strong authentication mechanisms to prevent unauthorized access. Both protocols support public-key cryptography, where users generate key pairs (private and public keys) for secure authentication. TCP typically employs SSHv2, which offers more advanced authentication features, including support for multiple authentication methods and passwordless login.
UDP, on the other hand, primarily uses SSHv1, which has limited authentication options compared to SSHv2. This can make UDP more vulnerable to brute-force attacks and other authentication exploits.
Performance Optimization
To enhance SSH performance, it’s crucial to select the appropriate protocol based on network conditions. TCP excels in reliable and stable connections, while UDP offers lower latency but may sacrifice reliability in congested networks.
SSH configuration allows for customization of port numbers and protocols. Specifying specific ports enhances security by obscuring standard SSH ports, while protocol selection optimizes performance based on network characteristics.
Port Configuration
- Modify the SSH configuration file (/etc/ssh/sshd_config) to define custom port numbers.
- Set the “Port” parameter to the desired port number (e.g., Port 2222).
- Restart the SSH service to apply the changes.
Protocol Selection
- In the SSH configuration file, set the “Protocol” parameter to either “2” for TCP or “1” for UDP.
- TCP provides reliable data transmission, making it suitable for stable networks.
- UDP offers faster response times, but reliability may be compromised in congested or unstable networks.
Use Cases
Choosing between TCP and UDP for SSH depends on the specific requirements and use cases. Let’s explore different scenarios where each protocol is more suitable.
TCP Use Cases
- Interactive Logins: TCP is preferred for interactive login sessions as it ensures reliable data transmission and guarantees that data arrives in the correct order.
- File Transfers: For secure file transfers using SCP or SFTP, TCP provides reliable and ordered data delivery, minimizing data loss or corruption.
- Port Forwarding: TCP is often used for port forwarding, allowing remote access to services running on the server, as it maintains persistent connections.
UDP Use Cases
- Monitoring and Logging: UDP is suitable for monitoring and logging applications where data integrity is less critical, such as network traffic analysis or system health checks.
- Network Scans: UDP is commonly used for network scans and discovery tools, as it allows for quick and efficient probing of hosts and services without requiring a connection.
- Performance-Sensitive Applications: In situations where latency is crucial, such as real-time data transmission or remote control, UDP can provide better performance than TCP.
Protocol Tunneling
SSH can be used to establish secure tunnels over TCP or UDP connections, allowing other protocols to be securely transmitted over an encrypted channel.
This technique, known as protocol tunneling, offers several benefits:
- Secure Data Transmission: Data transmitted through the tunnel is encrypted, protecting it from eavesdropping and unauthorized access.
- Access Control: SSH provides strong authentication mechanisms, ensuring that only authorized users can access the tunnel.
- Flexibility: SSH tunnels can be used to transport various protocols, including HTTP, FTP, and email, providing versatility and convenience.
Limitations of SSH Tunneling
- Performance Overhead: Encryption and decryption processes can introduce latency and reduce performance, especially for bandwidth-intensive applications.
- Firewall Restrictions: Some firewalls may block SSH traffic, limiting the use of tunneling.
- Configuration Complexity: Setting up SSH tunnels requires technical knowledge and proper configuration, which can be challenging for non-technical users.
Historical Evolution
The use of TCP and UDP in SSH has evolved over time to support different use cases and enhance security and performance.
Initially, SSH primarily relied on TCP for secure remote access. TCP provided reliable, ordered, and error-corrected data transmission, ensuring the integrity and confidentiality of communication.
UDP Support
Later, SSH incorporated support for UDP to cater to specific use cases where low latency and faster response times were crucial. UDP, being a connectionless protocol, offered reduced overhead and faster packet delivery, making it suitable for applications like interactive remote desktops and real-time audio/video streaming.
Alternative Protocols
In addition to SSH, there are other secure remote access protocols available. Two popular alternatives are SFTP and SCP.
SFTP (SSH File Transfer Protocol)
SFTP is a secure file transfer protocol that uses SSH for secure communication. It provides a secure way to transfer files between remote hosts. SFTP is similar to FTP, but it uses SSH for encryption and authentication, making it more secure than FTP.
SCP (Secure Copy Protocol)
SCP is another secure file transfer protocol that uses SSH for secure communication. It is similar to SFTP, but it is specifically designed for copying files between remote hosts. SCP is a command-line tool that is often used for scripting and automation tasks.
Comparison of SSH, SFTP, and SCP
The following table compares the features and capabilities of SSH, SFTP, and SCP:| Feature | SSH | SFTP | SCP ||—|—|—|—|| Secure communication | Yes | Yes | Yes || File transfer | No | Yes | Yes || Command-line interface | Yes | No | Yes || Scripting and automation | Yes | No | Yes |
-Line Usage
SSH supports both TCP and UDP as transport protocols. The choice of protocol depends on the specific requirements of the application and the network environment.
TCP is a reliable, connection-oriented protocol that provides guaranteed delivery of data in order. UDP, on the other hand, is a connectionless, unreliable protocol that does not guarantee delivery of data or the order in which it is sent.
TCP
- Reliable, connection-oriented protocol
- Guarantees delivery of data in order
- More overhead than UDP
- Suitable for applications that require reliable data transfer, such as file transfers and remote desktop sessions
UDP
- Connectionless, unreliable protocol
- Does not guarantee delivery of data or the order in which it is sent
- Less overhead than TCP
- Suitable for applications that can tolerate data loss, such as streaming media and online gaming
Port Numbers
SSH uses different port numbers for TCP and UDP connections. The default port number for TCP is 22, while the default port number for UDP is 123.
The port number can be specified using the -p option. For example, to specify TCP port 2222, you would use the following command:
ssh
p 2222 user@host
To specify UDP port 1234, you would use the following command:
ssh
- p 1234
- u user host
Configuration File
The SSH configuration file, typically named ~/.ssh/config , allows users to specify various parameters for SSH connections, including the protocol and port number.
To configure SSH to use TCP or UDP on a specific port, add the following options to the configuration file:
TCP Configuration
- Protocol 2: Specifies the SSH protocol version 2, which supports both TCP and UDP.
- Port <port_number>: Sets the TCP port number to be used for the connection. The default port for SSH is 22.
UDP Configuration
- Protocol 2: Specifies the SSH protocol version 2, which supports both TCP and UDP.
- Port <port_number>: Sets the UDP port number to be used for the connection.
For example, to configure SSH to use TCP on port 443, add the following line to the configuration file:
Protocol 2 Port 443
Similarly, to configure SSH to use UDP on port 53, add the following line:
Protocol 2 Port 53