ssh.sshslowdns.com – In the realm of network connectivity, SSH UDP tunneling has emerged as a powerful tool to establish secure and efficient communication channels across diverse networks. This guide delves into the intricacies of SSH UDP tunneling, providing a comprehensive overview of its concepts, implementation, security considerations, performance optimization, troubleshooting, advanced configuration options, and practical applications.
Whether you’re a network administrator seeking to enhance network security or a developer seeking to optimize data transfer, this guide will equip you with the knowledge and expertise to harness the full potential of SSH UDP tunneling.
SSH UDP Tunnel Overview
SSH UDP tunneling involves creating a secure channel over a network using the Secure Shell (SSH) protocol. It allows for the transmission of UDP packets through an encrypted SSH connection, enabling the secure transfer of data between two hosts.
SSH UDP tunneling provides several benefits, including secure communication, bypassing firewalls, and accessing restricted networks. It is particularly useful in scenarios where direct UDP communication is blocked or restricted, allowing for seamless data transfer even in challenging network environments.
Purpose of SSH UDP Tunneling
- Securely transmit UDP packets over an SSH connection.
- Bypass firewalls and network restrictions.
- Access restricted networks or resources.
- Enable remote access to applications and services.
Technical Implementation
Establishing an SSH UDP tunnel involves several steps and configurations. Let’s explore the technical aspects of setting up a tunnel.
Command Syntax
The basic syntax for creating an SSH UDP tunnel is:
ssh -f -N -L local_port:destination_host:destination_port user@remote_host
- -f : Runs the tunnel in the background.
- -N : Prevents execution of remote commands.
- -L : Specifies the local port forwarding.
- local_port : The port on the local machine to forward traffic to.
- destination_host : The remote host to forward traffic to.
- destination_port : The port on the remote host to forward traffic to.
- user : The username to use for SSH authentication.
- remote_host : The remote host to connect to.
Configuration Options
In addition to the basic syntax, several configuration options can be used to customize the tunnel behavior:
- -p: Specifies the SSH port (default: 22).
- -i: Specifies the SSH private key file.
- -C: Enables compression.
- -D: Specifies a SOCKS proxy port.
Security Considerations
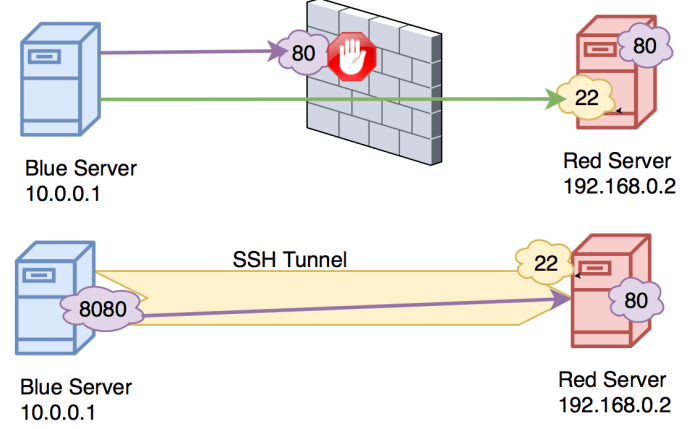
SSH UDP tunneling offers significant advantages, but it’s essential to be aware of potential security risks associated with it.Best practices for mitigating these risks include:
Encryption
Encryption is crucial for protecting data transmitted through the SSH UDP tunnel. Use strong encryption algorithms, such as AES-256, to ensure that data remains confidential.
Authentication
Strong authentication mechanisms, such as two-factor authentication, should be implemented to prevent unauthorized access to the tunnel.
Access Control
Limit access to the SSH UDP tunnel to authorized users and devices. Implement firewalls and access control lists to restrict access to specific IP addresses or networks.
Monitoring
Regularly monitor the SSH UDP tunnel for suspicious activity. Use intrusion detection systems or log analysis tools to detect and respond to potential security threats.
Vulnerability Management
Keep the SSH server and client software up to date with the latest security patches to address any known vulnerabilities.
Performance Optimization
Optimizing SSH UDP tunnels enhances their efficiency and performance. Consider the following factors and techniques:
Buffer size: Larger buffers can reduce the frequency of packet fragmentation and reassembly, improving throughput. Adjust the buffer size to match the network conditions and application requirements.
TCP Segmentation Offloading (TSO)
Enable TSO on both the client and server to offload TCP segmentation to the network interface card (NIC). This frees up CPU resources and improves overall performance.
Multiple UDP Ports
Using multiple UDP ports can distribute the load across multiple network interfaces or physical links, increasing bandwidth and reducing latency.
Packet Coalescing
Enable packet coalescing on the network interface to reduce the number of interrupts generated by incoming packets. This reduces CPU overhead and improves performance.
Hardware Acceleration
Consider using hardware-accelerated NICs that support features like SR-IOV (Single Root I/O Virtualization) to offload processing from the CPU to dedicated hardware.
Troubleshooting Common Issues
When establishing and using SSH UDP tunnels, various issues may arise. Understanding these common problems and implementing appropriate troubleshooting procedures can help resolve them efficiently.
Connection Problems
-
- -*Issue Unable to establish a connection through the tunnel.
-*Troubleshooting
Verify that the SSH server is running and listening on the specified port.
Check firewall settings on both the client and server to ensure that UDP traffic is allowed.
Confirm that the client and server have the correct IP addresses and port numbers configured.
Check for any network connectivity issues or outages.
Performance Issues
-
- -*Issue Slow or intermittent data transfer through the tunnel.
-*Troubleshooting
Monitor network traffic to identify any bottlenecks or packet loss.
Adjust the MTU (Maximum Transmission Unit) size on the client and server to optimize packet fragmentation.
Consider using a different encryption algorithm or compression method to improve performance.
Check for any resource limitations on the client or server, such as CPU or memory usage.
Security Issues
-
- -*Issue Suspected security breach or unauthorized access through the tunnel.
-*Troubleshooting
Review SSH configuration files for any vulnerabilities or misconfigurations.
Implement strong authentication mechanisms, such as two-factor authentication or public-key cryptography.
Monitor SSH logs for any suspicious activity or unauthorized login attempts.
Regularly update SSH software to patch any known security flaws.
Configuration Errors
-
- -*Issue Incorrect configuration of SSH UDP tunnel parameters.
-*Troubleshooting
Check that the client and server have matching tunnel settings, including port numbers, encryption algorithms, and authentication methods.
Ensure that the local and remote addresses specified for the tunnel are correct.
Review SSH configuration files to verify that the tunnel is properly defined and enabled.
Other Issues
-
- -*Issue Unable to access specific services or applications through the tunnel.
-*Troubleshooting
Check if the target services are running on the remote server.
Verify that the firewall on the remote server allows access to the services from the client.
Consider using a different port forwarding method, such as TCP port forwarding or SOCKS proxy.
Advanced Configuration Options
SSH UDP tunnels offer a range of advanced configuration options that enhance their functionality and security. These options allow users to tailor the tunnel to specific requirements and address various scenarios.
Understanding the impact of these options is crucial for optimizing the performance and security of the tunnel. They provide granular control over aspects such as authentication, encryption, and port forwarding.
Port Forwarding Options
- Local Port Forwarding: Allows specifying the local port to which incoming UDP traffic will be forwarded.
- Remote Port Forwarding: Specifies the remote port to which the forwarded traffic will be directed on the target host.
- Dynamic Port Forwarding: Enables the automatic allocation of ports for dynamic applications that require multiple connections.
Security Options
- Authentication Methods: Configurable authentication methods include password-based, public-key, and two-factor authentication, providing varying levels of security.
- Encryption Algorithms: Allows selection of encryption algorithms such as AES, Blowfish, and 3DES, offering different levels of encryption strength and performance.
- IP Address Binding: Restricts the tunnel to specific IP addresses, preventing unauthorized access from other sources.
Performance Optimization
- Compression: Enables data compression to reduce bandwidth consumption and improve performance.
- Buffer Size: Adjusts the size of the buffer used for data transmission, affecting latency and throughput.
- Keepalive Interval: Configures the interval at which keepalive messages are sent to maintain the tunnel connection.
Comparison with Other Tunneling Methods
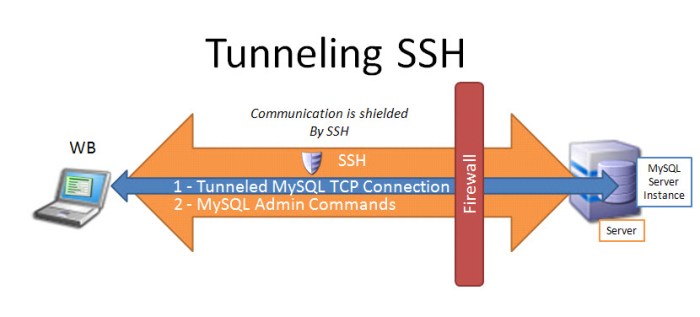
SSH UDP tunneling offers unique advantages and disadvantages compared to other tunneling methods. Understanding these differences can help you select the most suitable tunneling method for your specific needs.
Alternative Tunneling Methods
Several alternative tunneling methods exist, including:
- VPN Tunneling: Establishes a secure, encrypted connection between two networks, allowing users to access remote resources securely.
- SOCKS Tunneling: A protocol that allows applications to securely access remote servers through a proxy server.
- HTTP Tunneling: A technique that encapsulates TCP traffic within HTTP requests, enabling communication through firewalls.
Advantages of SSH UDP Tunneling
- Security: SSH UDP tunneling provides a highly secure connection, as it encrypts both the control channel and the data tunnel using strong encryption algorithms.
- Cross-Platform Compatibility: SSH is widely supported across different operating systems, making it easy to establish tunnels between devices running different platforms.
- Flexibility: SSH UDP tunneling allows for the tunneling of UDP traffic, which is not supported by all tunneling methods.
- Customization: SSH UDP tunneling offers advanced configuration options, allowing you to customize the tunnel parameters and optimize performance.
Disadvantages of SSH UDP Tunneling
- Latency: SSH UDP tunneling can introduce additional latency compared to other tunneling methods, especially for applications that are sensitive to network delays.
- Resource Consumption: Establishing and maintaining SSH UDP tunnels can consume more system resources than other tunneling methods, particularly on resource-constrained devices.
- Limited Support: SSH UDP tunneling may not be supported by all network devices and applications, especially those that are designed for high-performance or real-time applications.
Practical Applications
SSH UDP tunneling offers a myriad of practical applications in real-world scenarios, enabling seamless network connectivity and enhanced security measures.
By encapsulating UDP traffic within a secure SSH connection, organizations can overcome network restrictions, securely access remote resources, and establish reliable communication channels even in challenging network environments.
Enhancing Network Connectivity
- Remote Access to Internal Networks: SSH UDP tunneling allows remote users to securely access internal network resources, such as file servers, databases, and applications, from anywhere with an internet connection.
- Bypassing Network Firewalls: Organizations can bypass restrictive network firewalls by tunneling UDP traffic through an SSH connection, enabling access to blocked websites or services.
- Establishing Secure VPN Connections: SSH UDP tunneling can be used to establish secure VPN connections, providing remote users with encrypted access to corporate networks.
Improving Security
- Protecting Sensitive Data: SSH UDP tunneling encrypts UDP traffic, safeguarding sensitive data from eavesdropping and interception.
- Mitigating Man-in-the-Middle Attacks: By establishing a secure SSH connection, UDP tunneling prevents man-in-the-middle attacks, ensuring the integrity and authenticity of data.
- Enhancing Authentication and Authorization: SSH UDP tunneling supports strong authentication mechanisms, such as public-key cryptography and two-factor authentication, providing robust access control.
Case Studies and Examples
SSH UDP tunneling has been successfully implemented in various scenarios. Let’s explore a few case studies to understand its practical applications.
Consider a scenario where a remote team needs to securely access a private network behind a firewall. SSH UDP tunneling can establish a secure connection, allowing team members to access internal resources and collaborate effectively.
Successful Implementation for Remote Access
- Setup: SSH server installed on a gateway machine within the private network. SSH client configured on remote team members’ devices.
- Configuration: UDP port forwarded on the gateway machine to the internal network using SSH tunneling.
- Results: Remote team members could access internal resources securely and efficiently, enabling seamless collaboration.
SSH UDP Tunnel for Gaming
In another example, SSH UDP tunneling has been used to improve gaming experiences. When online gaming servers are inaccessible due to firewalls or network restrictions, SSH UDP tunneling can create a secure connection to bypass these obstacles.
- Setup: SSH server running on a machine with access to the gaming server. SSH client configured on the gaming device.
- Configuration: UDP port forwarded on the SSH server to the gaming server.
- Results: Gamers can enjoy improved connectivity and reduced latency, enhancing their gaming experience.
Best Practices and Recommendations
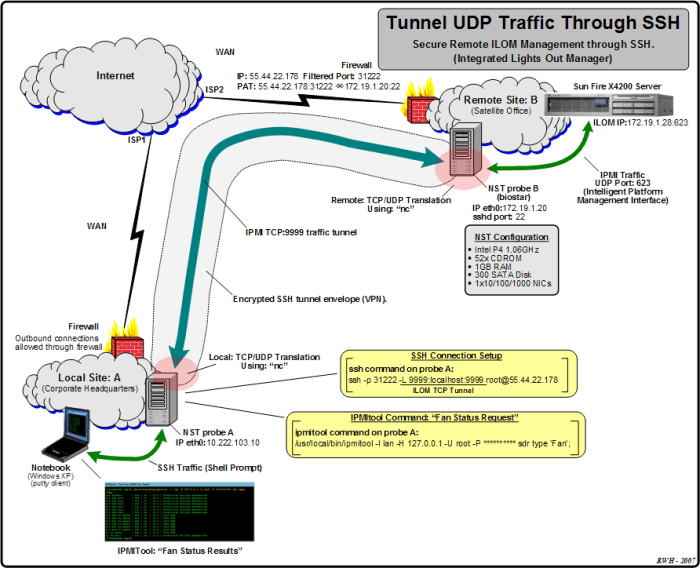
When using SSH UDP tunnels, it’s crucial to adhere to best practices for security and efficiency. Consider the following guidelines: