In the realm of secure and efficient data transmission, SSH UDP tunneling emerges as a powerful tool that enables seamless communication across networks. This technique harnesses the capabilities of the Secure Shell (SSH) protocol to establish encrypted tunnels, allowing users to bypass firewalls, access remote resources, and optimize network performance.
SSH UDP tunneling offers a myriad of benefits, making it an invaluable asset for network administrators, IT professionals, and anyone seeking to enhance their data security and network connectivity. By delving into the intricacies of this technology, we will explore its fundamental concepts, practical applications, and best practices for implementation.
SSH UDP Tunneling Overview
SSH UDP tunneling is a technique that allows you to establish a secure tunnel over a UDP-based network, such as a virtual private network (VPN). This technique is commonly used to bypass firewalls and other network restrictions, as well as to provide secure access to remote services and applications.
SSH UDP tunneling works by encapsulating UDP packets within SSH packets. This allows the UDP packets to be transmitted over an SSH connection, which is typically encrypted and authenticated. The SSH connection provides a secure channel for the UDP packets, allowing them to bypass firewalls and other network restrictions.
Benefits and Use Cases
SSH UDP tunneling offers several benefits, including:
- Secure access to remote services and applications
- Bypass firewalls and other network restrictions
- Provide a secure channel for UDP-based applications
SSH UDP tunneling can be used in a variety of scenarios, including:
- Accessing remote servers and applications that are behind a firewall
- Bypassing internet censorship and accessing blocked websites
- Providing a secure channel for VoIP and other UDP-based applications
Establishing SSH UDP Tunnels
SSH UDP tunnels are established by initiating an SSH connection with the
w flag, specifying the remote port and host, and optionally, the source port.
On the client side, the command is:“`ssh
-w
p @
“`For example, to establish a UDP tunnel from a local port 10000 to a remote port 5000 on the server 192.168.1.100, the command would be:“`ssh
-w 5000
192.168.1.100
p 10000 [email protected]
“`On the server side, no additional configuration is typically required. The SSH server will automatically accept the UDP traffic on the specified port.
Configuring SSH UDP Tunnels
SSH UDP tunnels offer a range of configuration options to tailor them to specific applications. Understanding these options empowers you to optimize tunnel performance and adapt it to diverse scenarios.
To configure an SSH UDP tunnel, you typically specify the following parameters:
Source Port Binding
- The source port on the client machine that will be bound to the tunnel.
- This allows applications to connect to the tunnel using a specific port.
Destination Port Binding
- The destination port on the remote server that will be forwarded to the client machine.
- This determines the port on the server that the tunnel will connect to.
Target Host
- The IP address or hostname of the remote server that the tunnel will connect to.
- This specifies the destination of the tunnel.
Additional Options
- Additional options may include specifying a specific SSH key or passphrase, setting the tunnel timeout, and controlling the verbosity of tunnel logging.
- These options provide fine-grained control over the tunnel’s behavior.
Troubleshooting SSH UDP Tunnels
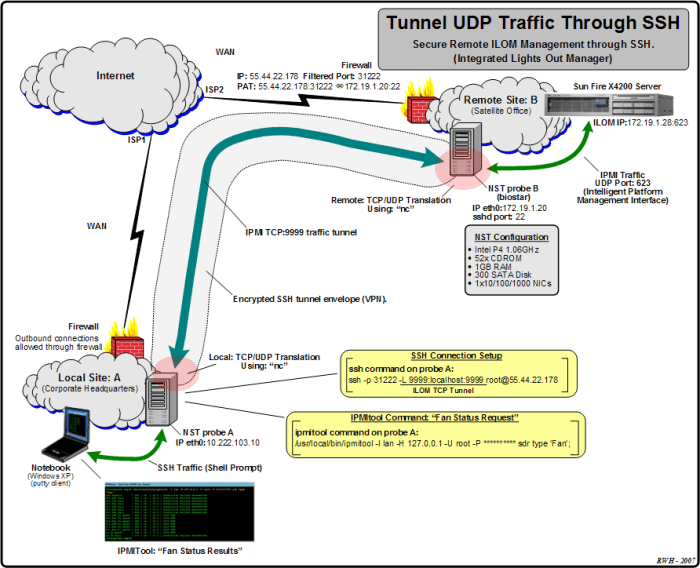
Troubleshooting SSH UDP tunnels involves identifying and resolving issues that may arise during their establishment or operation. Some common issues and their solutions include:
Connectivity Problems
- Firewall Blocking: Ensure that the firewall on both the client and server systems allows UDP traffic on the specified port used for the tunnel.
- Network Configuration: Verify that the network configuration is correct, including IP addresses, subnet masks, and default gateways.
Authentication Issues
- Incorrect Credentials: Double-check that the username and password or SSH key used for authentication are correct.
- SSH Server Configuration: Ensure that the SSH server is configured to allow UDP tunneling and that the user has appropriate permissions.
Performance Issues
- Bandwidth Limitations: Monitor network traffic to ensure that the tunnel is not saturating the available bandwidth.
- Packet Loss: Check for any network congestion or packet loss that may affect the tunnel’s performance.
Other Issues
- Port Conflicts: Avoid using the same port for multiple tunnels or other applications that may interfere with UDP traffic.
- SSH Client Version: Ensure that the SSH client version supports UDP tunneling.
Securing SSH UDP Tunnels
While SSH UDP tunnels offer many advantages, it’s crucial to understand the security implications associated with their use. Unlike TCP tunnels, UDP tunnels do not establish a persistent connection, making them more vulnerable to eavesdropping and other attacks.
To ensure the security of SSH UDP tunnels, it’s essential to implement robust encryption and authentication mechanisms.
Encryption
Encryption plays a vital role in protecting data transmitted through SSH UDP tunnels. By encrypting the data, you can prevent unauthorized parties from accessing sensitive information even if they intercept it.
- Use strong encryption algorithms, such as AES-256 or ChaCha20-Poly1305, to protect data from unauthorized access.
- Ensure that the encryption keys are securely generated and managed.
Authentication
Authentication is crucial for ensuring that only authorized users can access the SSH UDP tunnel. Implement robust authentication mechanisms to prevent unauthorized access.
- Use strong passwords or public-key authentication for user authentication.
- Consider using two-factor authentication (2FA) for added security.
- Limit access to the SSH UDP tunnel to authorized users only.
By implementing these best practices, you can significantly enhance the security of your SSH UDP tunnels and protect your data from unauthorized access.
Applications of SSH UDP Tunnels
SSH UDP tunnels offer a versatile range of applications, enabling users to establish secure connections and bypass network restrictions.
Remote Access
SSH UDP tunnels allow users to securely access remote networks, such as corporate intranets or home networks, from any location with an internet connection. This enables remote workers, travelers, or individuals behind restrictive firewalls to access resources and applications as if they were physically present on the remote network.
Network Management
Network administrators can utilize SSH UDP tunnels to manage and monitor remote networks securely. By tunneling network traffic through an SSH connection, administrators can access and control network devices, perform troubleshooting tasks, and update configurations remotely, ensuring uninterrupted network operations.
Bypassing Firewalls
SSH UDP tunnels can be employed to bypass firewalls and access blocked websites or services. By encapsulating UDP traffic within an SSH connection, users can tunnel through firewalls that restrict direct UDP connections, allowing them to access content and applications that would otherwise be inaccessible.
Comparison with Other Tunneling Methods
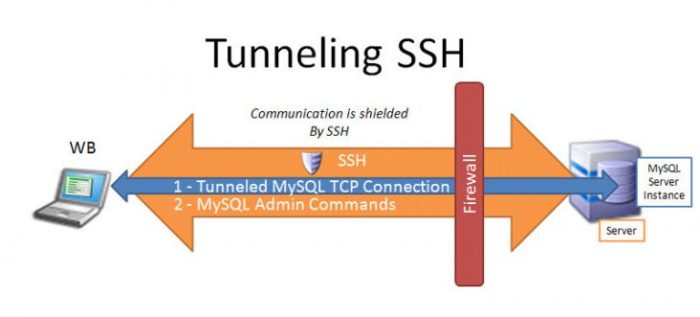
SSH UDP tunneling offers distinct advantages and drawbacks compared to other tunneling methods like VPNs and SOCKS proxies. Understanding these differences is crucial for selecting the most suitable tunneling solution for specific needs.
VPNs
- VPNs (Virtual Private Networks) create encrypted tunnels over public networks, allowing secure access to remote resources.
- Pros:
- Provide comprehensive network-level security.
- Easy to configure and manage.
- Cons:
- Can be slower than direct connections.
- May not support all applications or protocols.
SOCKS Proxies
- SOCKS proxies forward traffic from a client to a destination server, providing anonymity and bypassing network restrictions.
- Pros:
- Offer greater flexibility and application support than VPNs.
- Can be configured to handle specific protocols.
- Cons:
- Less secure than SSH UDP tunnels due to lack of encryption.
- May require complex configuration and maintenance.
SSH UDP Tunneling Tools
SSH UDP tunneling is a powerful technique for establishing secure and efficient connections over UDP-based protocols. Several tools and software are available to facilitate SSH UDP tunneling, each offering unique features and benefits.
PuTTY
PuTTY is a widely used SSH and telnet client that supports UDP tunneling. It provides a user-friendly interface and allows for the configuration of various tunneling options, including the source and destination ports, the remote host, and the SSH user and password.
OpenSSH
OpenSSH is an open-source implementation of the SSH protocol. It includes support for UDP tunneling through thew option. OpenSSH is highly configurable and offers advanced features such as multiplexing, compression, and key management.
stunnel
stunnel is a dedicated UDP tunneling tool that provides secure connections for various protocols, including DNS, SMTP, and POP3. It operates as a proxy server, listening on a UDP port and forwarding traffic to the remote host through an encrypted SSH tunnel.
SSH Redirector
SSH Redirector is a Windows-based tool that simplifies the configuration and management of SSH UDP tunnels. It provides a graphical user interface (GUI) for creating and managing tunnels, making it accessible to users with limited technical expertise.
Features and Benefits
These tools offer a range of features and benefits, including:
- Secure and encrypted connections
- Support for multiple protocols
- Customizable tunneling options
- User-friendly interfaces
- Cross-platform compatibility
The choice of tool depends on the specific requirements and preferences of the user. PuTTY and OpenSSH are suitable for general-purpose tunneling, while stunnel and SSH Redirector offer specialized features for specific protocols and ease of use, respectively.
Advanced SSH UDP Tunneling Techniques
Beyond the basic establishment and configuration of SSH UDP tunnels, there are advanced techniques that enhance their functionality and versatility.
Multiplexing
Multiplexing allows multiple UDP applications to share a single SSH UDP tunnel. This is achieved by assigning each application a specific port number on the remote host. When a UDP packet arrives at the tunnel, the SSH server forwards it to the correct application based on its port number.
Load Balancing
Load balancing distributes UDP traffic across multiple SSH UDP tunnels. This improves performance and reliability by ensuring that no single tunnel becomes overloaded. Load balancing can be implemented using techniques such as round-robin or weighted round-robin, where different tunnels are assigned different weights based on their capacity.
10. Real-World Examples of SSH UDP Tunneling
SSH UDP tunneling is a versatile technique that finds applications in various real-world scenarios. Let’s explore some practical examples to understand its benefits and challenges.
Enhancing Remote Access Security
SSH UDP tunneling can be used to securely access remote servers, particularly in environments where direct access is restricted by firewalls or network configurations. By tunneling UDP traffic over an SSH connection, administrators can establish a secure and encrypted channel for remote management and data transfer.
Bypass Network Restrictions
SSH UDP tunneling can be used to bypass network restrictions, such as firewalls or proxy servers, that may block certain types of traffic. By encapsulating UDP traffic within an SSH connection, it can be transmitted over the network without being detected or blocked.
Improving Performance
In some cases, SSH UDP tunneling can improve performance by optimizing the transmission of UDP traffic. UDP packets are often fragmented and sent over multiple network hops, which can lead to delays and packet loss. By encapsulating UDP traffic within an SSH connection, it can be sent over a single, optimized channel, reducing latency and improving overall performance.
Creating Virtual Private Networks
SSH UDP tunneling can be used to create virtual private networks (VPNs) that extend private networks across public networks. By establishing SSH UDP tunnels between multiple devices, organizations can securely connect remote locations, allowing users to access resources as if they were on the same local network.
Challenges of SSH UDP Tunneling
While SSH UDP tunneling offers numerous benefits, it also comes with certain challenges:
- Increased Latency: SSH UDP tunneling adds an additional layer of encapsulation, which can introduce some latency in the transmission of UDP packets.
- Firewall Compatibility: SSH UDP tunneling may not be compatible with all firewalls, particularly those that inspect traffic at the application layer.
- Bandwidth Limitations: SSH UDP tunneling can be bandwidth-intensive, especially when transmitting large amounts of data.
Closure
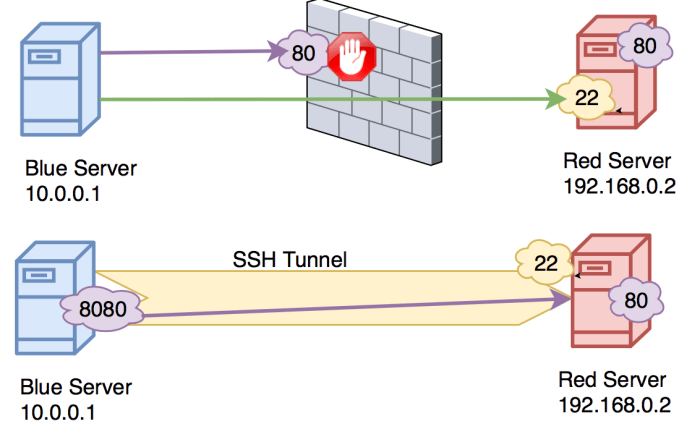
SSH UDP tunneling has revolutionized the way we secure and manage data transmission across networks. Its versatility, security, and ease of implementation make it an indispensable tool for network administrators, IT professionals, and anyone seeking to optimize their network connectivity.
By understanding the concepts, applications, and best practices Artikeld in this comprehensive guide, you can harness the power of SSH UDP tunneling to enhance your data security, improve network performance, and unlock a world of possibilities.