SSH.SSHSlowdns.com – In the realm of secure remote access, SSH (Secure Shell) has emerged as a cornerstone technology, providing a robust and versatile means of connecting to remote systems. While traditionally associated with TCP, SSH also offers support for UDP (User Datagram Protocol), opening up new possibilities for efficient and secure data transfer.
In this comprehensive guide, we will delve into the intricacies of SSH UDP servers, exploring their purpose, benefits, and limitations. We will examine the key exchange process, authentication mechanisms, encryption algorithms, and security measures employed in SSH UDP connections. Additionally, we will discuss performance considerations, scalability, configuration, and management best practices.
SSH UDP Server Overview
An SSH UDP server enables secure remote access and management of devices over UDP (User Datagram Protocol), a connectionless transport protocol. Unlike TCP, UDP does not establish a persistent connection, making it more suitable for applications requiring low latency and bandwidth, such as interactive command-line interfaces, DNS lookups, and network management tools.
Benefits of SSH over UDP
- Lower latency: UDP’s connectionless nature eliminates the need for handshakes and acknowledgements, resulting in faster response times.
- Reduced bandwidth usage: UDP does not require the transmission of control packets, reducing network traffic and bandwidth consumption.
- Simpler implementation: UDP’s stateless design simplifies the implementation and maintenance of SSH servers.
Limitations of SSH over UDP
- Unreliable delivery: UDP does not guarantee packet delivery, which can lead to data loss in certain network conditions.
- Limited error handling: UDP does not provide built-in error handling mechanisms, requiring custom implementations to handle packet loss and retransmissions.
- Security concerns: UDP’s connectionless nature can make it vulnerable to spoofing and eavesdropping attacks.
UDP Port and Protocol
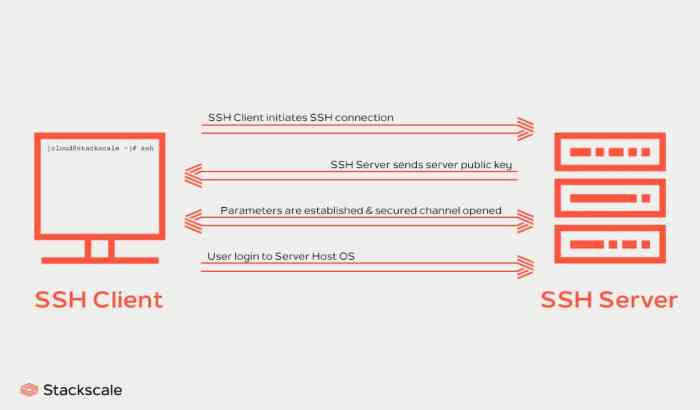
SSH utilizes UDP for specific purposes, such as exchanging initial connection requests and key negotiation. Understanding the default UDP port and the characteristics of the UDP protocol is crucial for configuring and troubleshooting SSH connections.
Default UDP Port
The default UDP port for SSH connections is 49154 . This port is reserved for SSH and is used for sending and receiving UDP packets during the initial connection establishment phase.
UDP Protocol
UDP (User Datagram Protocol) is a connectionless protocol that operates over IP networks. It is a lightweight and efficient protocol, suitable for applications that require low latency and do not rely on reliable delivery. UDP does not establish a connection before sending data, which reduces overhead and improves performance.
In the context of SSH, UDP is used for:
- Exchanging initial connection requests
- Negotiating SSH keys
- Transporting SSH management messages
SSH Key Exchange and Authentication
SSH over UDP utilizes a Diffie-Hellman key exchange algorithm to establish a secure communication channel. During this process, both the client and server generate ephemeral public keys and exchange them. These keys are then used to derive a shared secret, which forms the basis for subsequent encryption and decryption.SSH
UDP servers support various authentication methods, including:
Password Authentication
The most straightforward method, where the user provides a password to authenticate their identity.
Public Key Authentication
A more secure method that involves the use of public and private key pairs. The public key is stored on the server, while the private key is kept secret by the user.
Keyboard-Interactive Authentication
A method where the server prompts the user for additional information, such as a one-time password or a security question, to verify their identity.
Certificate-Based Authentication
A method that utilizes digital certificates to establish the identity of the user and the server.
Encryption and Security
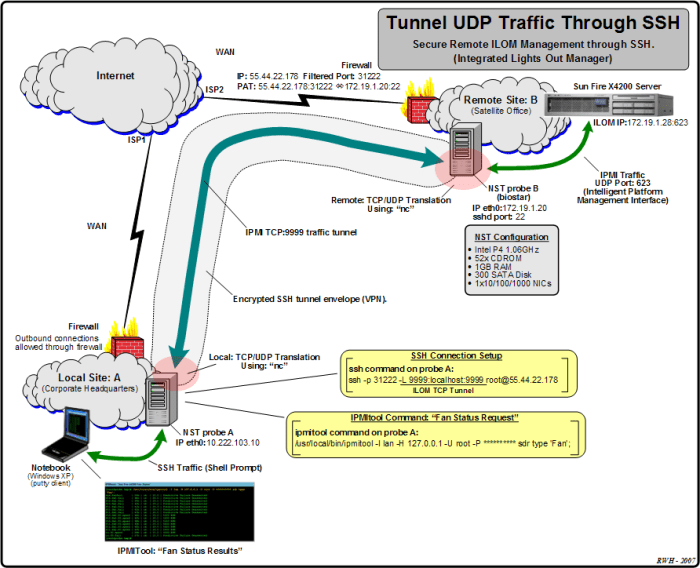
SSH UDP connections employ robust encryption algorithms to safeguard data transmission. The Advanced Encryption Standard (AES) is a widely adopted cipher that operates in multiple modes, including Cipher Block Chaining (CBC) and Galois/Counter Mode (GCM), to provide confidentiality and integrity protection.
Furthermore, SSH UDP leverages the HMAC (Hash-based Message Authentication Code) mechanism to ensure data authenticity and prevent tampering. HMAC utilizes a secret key to generate a digest of the transmitted data, which is then appended to the message. The recipient verifies the digest using the same secret key, ensuring that the data has not been altered during transit.
Security Measures
To enhance security, SSH UDP incorporates several defense mechanisms against potential attacks.
- Packet Authentication: Each UDP packet is authenticated using a Message Authentication Code (MAC), preventing unauthorized access and data manipulation.
- Replay Protection: Sequence numbers are utilized to safeguard against replay attacks, where an attacker attempts to reuse previously captured packets.
- Port Knocking: SSH UDP can be configured to require a specific sequence of UDP packets to be sent to a specific port before allowing access. This adds an additional layer of protection against unauthorized access.
- Rate Limiting: To mitigate brute-force attacks, SSH UDP can impose rate limits on incoming connection attempts, preventing excessive connection requests from a single source.
Performance and Scalability
SSH UDP servers offer efficient performance and scalability in large networks.
Performance Considerations
UDP’s connectionless nature reduces overhead, resulting in faster communication. SSH UDP servers minimize latency and maximize throughput, particularly for short-lived or high-volume data transfers.
Scalability in Large Networks
SSH UDP servers scale effectively in large networks due to their low resource consumption and lightweight protocol. They can handle multiple concurrent connections with minimal impact on system resources, making them suitable for high-traffic environments.
Configuration and Management

Configuring an SSH UDP server involves specifying settings such as the listening port, authentication methods, and encryption algorithms. The server’s configuration file typically includes parameters like Port, Protocol, ListenAddress, and Cipher.
Managing and maintaining SSH UDP servers require regular tasks like monitoring system logs, updating software, and patching security vulnerabilities. Log files provide insights into server activity and can be analyzed to detect suspicious behavior or identify potential issues.
SSH Configuration File
The SSH configuration file is typically located at /etc/ssh/sshd_config on Linux systems. It contains various parameters that control the server’s behavior, including:
- Port: Specifies the port number on which the server listens for incoming connections (default: 22).
- Protocol: Defines the SSH protocol version to be used (default: 2).
- ListenAddress: Specifies the IP address or hostname on which the server listens for connections (default: all).
- Cipher: Lists the encryption algorithms that the server supports (default: aes128-ctr,aes192-ctr,aes256-ctr).
Troubleshooting and Diagnostics
Troubleshooting SSH UDP servers involves identifying and resolving connection issues and errors. Common problems include:
Incorrect configuration
Check the UDP port, protocol, and key exchange algorithms to ensure they are configured correctly.
Firewall or network restrictions
Verify that UDP traffic is allowed through firewalls and network configurations.
Server downtime
Check if the server is running and listening on the specified UDP port.
Authentication failures
Verify the SSH key or password is correct and matches the server’s configuration.
Diagnostic Tools
SSH clients with debug mode
Use SSH clients that provide debug output to identify connection errors and authentication issues.
Packet sniffers
Analyze network traffic using packet sniffers to capture and inspect SSH UDP packets.
Log files
Check server log files for error messages or clues about connection problems.
Best Practices
Securing and optimizing SSH UDP servers is essential to maintain the integrity and confidentiality of data transmitted over the network. Industry standards and best practices should be followed to ensure the highest level of security and performance.
Industry Standards and Recommendations
* Implement the latest version of SSH to benefit from the most recent security enhancements and bug fixes.
- Use strong encryption algorithms, such as AES-256-GCM or ChaCha20-Poly1305, to protect data in transit.
- Disable weak or outdated algorithms, such as DES, MD5, and SHA-1, to prevent potential vulnerabilities.
- Configure a strong authentication mechanism, such as public-key authentication, to prevent unauthorized access.
- Limit the number of authentication attempts to prevent brute-force attacks.
- Implement intrusion detection and prevention systems to monitor for suspicious activities and block unauthorized access.
- Regularly review and update SSH server configurations to ensure they meet the latest security standards and best practices.
Advanced Features
SSH UDP servers offer advanced capabilities that extend their functionality beyond traditional SSH applications.
These features enable SSH UDP servers to be used in specialized scenarios and applications, providing enhanced security, performance, and flexibility.
Specialized Applications
SSH UDP servers are employed in specialized applications where traditional TCP-based SSH connections are not suitable or face limitations.
- Network Monitoring and Management: SSH UDP servers can be used for remote network monitoring and management tasks, providing secure and efficient access to network devices.
- Industrial Automation: SSH UDP servers are utilized in industrial automation systems, allowing for secure remote control and monitoring of industrial equipment.
- Embedded Systems: SSH UDP servers are integrated into embedded systems, providing a secure means of remote access and configuration for devices with limited resources.
10. Examples and Case Studies
In this section, we’ll provide real-world examples and case studies that demonstrate the practical applications and benefits of SSH UDP server deployments.
Case Study: Securing Remote Access for Industrial Control Systems
In an industrial setting, an organization deployed an SSH UDP server to secure remote access to critical control systems. By leveraging the speed and efficiency of UDP, they were able to establish secure connections with remote engineers, enabling real-time monitoring and troubleshooting, while minimizing latency and maintaining the reliability of their operations.