In the realm of secure remote access, SSH UDP servers have emerged as a versatile and efficient solution. Leveraging the User Datagram Protocol (UDP), these servers offer a unique combination of speed, flexibility, and enhanced security.
This comprehensive guide delves into the intricacies of SSH UDP servers, exploring their functionality, configuration, security considerations, performance optimization, and advanced features. We will also delve into their integration with other services, troubleshooting techniques, and future trends in this dynamic technology.
SSH UDP Server Overview
An SSH UDP server provides secure remote access to a host system using the User Datagram Protocol (UDP). Unlike TCP-based SSH connections, UDP is a connectionless protocol that doesn’t require handshaking or session maintenance.
Using UDP for SSH offers certain benefits, including lower overhead and faster response times. However, it also has limitations, such as lack of reliability and ordered delivery of packets, which may impact the stability and performance of the connection.
Benefits of SSH UDP Server
- Lower overhead due to the connectionless nature of UDP.
- Faster response times as UDP doesn’t require handshaking or session maintenance.
- Reduced resource consumption on both the server and client sides.
Limitations of SSH UDP Server
- Lack of reliability as UDP doesn’t guarantee packet delivery or order.
- Potential for packet loss and reordering, which can affect the integrity of the SSH connection.
- Limited suitability for applications that require reliable and ordered data transfer.
Configuration and Setup
Setting up an SSH UDP server requires specific configuration and parameters to ensure secure and efficient operation. This section provides a step-by-step guide to configure and manage an SSH UDP server, including key configuration parameters and techniques for enabling and disabling UDP forwarding.
To begin, you will need to install and configure an SSH server on your system. Once the SSH server is operational, you can proceed with the following steps:
Configuration Parameters
- Port Number: The UDP port number that the SSH server will listen on. This can be any available port, but it is recommended to use a port that is not commonly used by other services.
- Listen Address: The IP address that the SSH server will listen on. This can be either the loopback address (127.0.0.1) or a public IP address.
- Forwarding: Enable or disable SSH UDP forwarding. This option allows you to forward UDP traffic through the SSH tunnel.
Enabling SSH UDP Forwarding
To enable SSH UDP forwarding, you will need to add the following line to your SSH configuration file (/etc/ssh/sshd_config):
GatewayPorts yes
Once this line is added, you will need to restart the SSH server for the changes to take effect.
Disabling SSH UDP Forwarding
To disable SSH UDP forwarding, you will need to remove the following line from your SSH configuration file (/etc/ssh/sshd_config):
GatewayPorts no
Once this line is removed, you will need to restart the SSH server for the changes to take effect.
Security Considerations
SSH UDP servers inherit the security features of SSH, including encryption and authentication. However, UDP’s connectionless nature introduces unique security challenges.
Potential Risks
* Eavesdropping: UDP packets are broadcast and can be intercepted by unauthorized parties.
Spoofing
Attackers can forge UDP packets to impersonate legitimate users.
Denial-of-Service (DoS) attacks
UDP’s lack of connection tracking makes it vulnerable to DoS attacks that flood the server with packets.
Best Practices
To secure SSH UDP connections:* Use strong encryption algorithms: AES-256 is recommended for data confidentiality.
Enable authentication
Use public-key authentication or two-factor authentication to prevent unauthorized access.
Limit access
Restrict access to the SSH UDP server to authorized users and trusted networks.
Monitor traffic
Use network monitoring tools to detect suspicious activity and identify potential threats.
Keep software up-to-date
Apply security patches and updates to address vulnerabilities.
Role of Encryption and Authentication
Encryption protects data transmitted over UDP by converting it into an unreadable format. Authentication verifies the identity of users and prevents unauthorized access. SSH UDP servers use strong encryption algorithms, such as AES-256, and support various authentication methods, including public-key authentication and two-factor authentication.
Performance Optimization
Optimizing the performance of SSH UDP servers is crucial for maintaining a seamless user experience. Factors like network latency and packet size significantly impact performance.
Troubleshooting and Resolving Performance Issues
Identifying and resolving performance issues requires a methodical approach. Monitor network latency and packet size to pinpoint potential bottlenecks. Consider using tools like Wireshark or tcpdump to analyze network traffic and identify performance-degrading factors.
Advanced Features
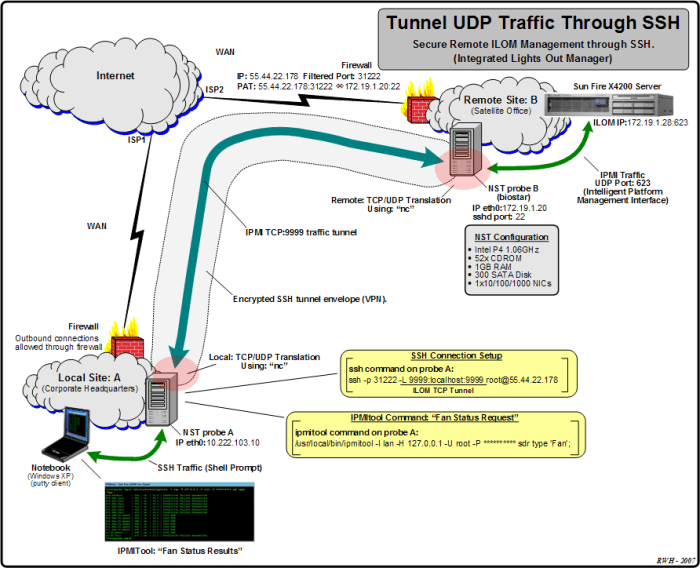
SSH UDP servers offer advanced features that extend their functionality beyond basic port forwarding. These features include dynamic port allocation and advanced security mechanisms.
Dynamic Port Allocation
Dynamic port allocation allows SSH UDP servers to automatically assign temporary port numbers to incoming connections. This enhances security by making it more difficult for attackers to guess the port numbers used by the server. It also simplifies configuration, as administrators do not need to manually specify port numbers for each connection.
Example:
A company uses an SSH UDP server to provide secure remote access to its employees. To enhance security, the server is configured to use dynamic port allocation. When an employee connects to the server, the server assigns a random port number to the connection.
This makes it more difficult for attackers to target the connection, as they would need to know the specific port number used.
Comparison with TCP
SSH UDP servers differ from SSH TCP servers in several key aspects. UDP is a connectionless protocol, while TCP is a connection-oriented protocol. This means that SSH UDP servers do not establish a persistent connection with clients, while SSH TCP servers do.
Advantages of SSH UDP
- Faster performance: UDP is a faster protocol than TCP, as it does not require the establishment of a persistent connection.
- Lower overhead: UDP has lower overhead than TCP, as it does not need to maintain a connection state.
- Less complex: UDP is a simpler protocol than TCP, which makes it easier to implement and manage.
Advantages of SSH TCP
- More reliable: TCP is a more reliable protocol than UDP, as it guarantees the delivery of packets in order and without errors.
- More secure: TCP provides more security features than UDP, such as encryption and authentication.
- More versatile: TCP can be used for a wider range of applications than UDP, as it supports both connection-oriented and connectionless communication.
When to Use SSH UDP or SSH TCP
SSH UDP is best suited for applications that require high performance and low overhead, such as gaming and streaming media. SSH TCP is best suited for applications that require reliability and security, such as file transfer and remote access.
Use Cases and Applications
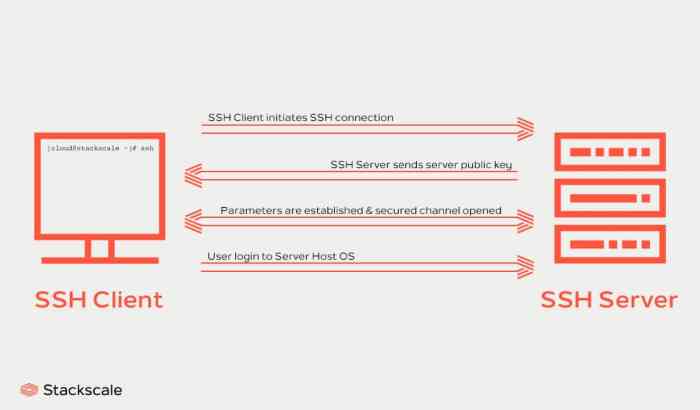
SSH UDP servers offer a wide range of use cases and applications in various industries and scenarios.
Remote Device Management
SSH UDP can be used to remotely manage and configure devices, such as routers, switches, and servers, even when they are behind firewalls or NAT devices. This is especially useful for network administrators who need to manage remote devices securely and efficiently.
Secure File Transfer
SSH UDP can be used to transfer files securely between two computers or devices. This is an ideal solution for transferring sensitive or confidential data over a network.
Secure Tunneling
SSH UDP can be used to create secure tunnels between two computers or devices. This allows users to securely access remote applications or resources, such as databases or web servers, even if they are behind firewalls or NAT devices.
Remote Desktop Access
SSH UDP can be used to provide remote desktop access to a computer or device. This allows users to control a remote computer or device from anywhere with an internet connection.
Troubleshooting
Troubleshooting SSH UDP servers involves identifying and resolving issues related to connectivity, authentication, and other operational aspects. Here are some common troubleshooting tips:
To diagnose and resolve connection issues, check if the UDP port is open and accessible. Verify firewall settings and network configurations to ensure proper connectivity. Additionally, examine system logs for any errors or warnings related to UDP communication.
Authentication Problems
Authentication issues can arise due to incorrect credentials or misconfigured SSH settings. Verify the username and password, and ensure that the SSH server is configured to allow UDP authentication. Check the server logs for any authentication-related errors, such as invalid login attempts or permission denied messages.
Other Errors
Other errors may occur due to incorrect server configurations, software bugs, or network issues. Review the server logs to identify any error messages or unusual activity. Consult documentation or online resources to find solutions for specific error codes or messages.
Logs and Troubleshooting Tools
System logs provide valuable information for troubleshooting SSH UDP servers. Check the /var/log/auth.log or /var/log/secure files for authentication-related events. Additionally, use tools like tcpdump or Wireshark to capture network traffic and analyze UDP communication patterns.
Integration with Other Services
Integrating SSH UDP servers with other services, such as firewalls, load balancers, and intrusion detection systems, enhances security and performance.Integrating with firewalls allows for granular control over network traffic, ensuring only authorized connections reach the SSH UDP server. Load balancers distribute incoming connections across multiple servers, improving scalability and preventing overloading.
Intrusion detection systems monitor network traffic for malicious activity and can block or alert administrators to potential threats.
Firewall Integration
Configure firewall rules to allow UDP traffic on port 53 and specify the IP addresses or ranges that should be allowed to connect to the SSH UDP server.
Load Balancer Integration
Configure the load balancer to distribute incoming UDP traffic to multiple SSH UDP servers. This improves scalability and ensures that all servers are utilized efficiently.
Intrusion Detection System Integration
Configure the intrusion detection system to monitor network traffic for suspicious activity. Set up rules to detect and block or alert on attempts to exploit SSH UDP vulnerabilities.
Future Trends and Developments
The realm of SSH UDP technology is poised for continued evolution, driven by the convergence of emerging trends and advancements. These developments are shaping the future of SSH UDP servers, expanding their capabilities and unlocking new possibilities.
One significant trend is the rise of quantum computing. As quantum computers become more powerful, they pose a potential threat to traditional encryption methods. SSH UDP servers are actively exploring quantum-resistant algorithms to ensure the long-term security of their communications.
Enhanced Performance and Scalability
Future SSH UDP servers will prioritize performance and scalability. Advancements in hardware and software technologies will enable servers to handle a higher volume of connections and data transfers. This will be crucial for supporting the growing demands of cloud computing, IoT, and other bandwidth-intensive applications.
Increased Security and Compliance
Security remains a top concern for SSH UDP servers. Future developments will focus on implementing stronger encryption algorithms, improving authentication mechanisms, and incorporating advanced security features. This will ensure that SSH UDP servers continue to meet the stringent compliance requirements of various industries and regulations.
Integration with Cloud and DevOps
SSH UDP servers are becoming increasingly integrated with cloud computing and DevOps environments. This integration allows for automated provisioning, configuration management, and monitoring of SSH UDP servers. It also simplifies the deployment and management of SSH UDP-based applications in cloud environments.
New Use Cases and Applications
The future of SSH UDP servers extends beyond traditional remote access and management. Emerging use cases include secure data transfer, IoT device management, and even gaming. As technology evolves, SSH UDP servers will continue to adapt and find new applications in various domains.
Summary
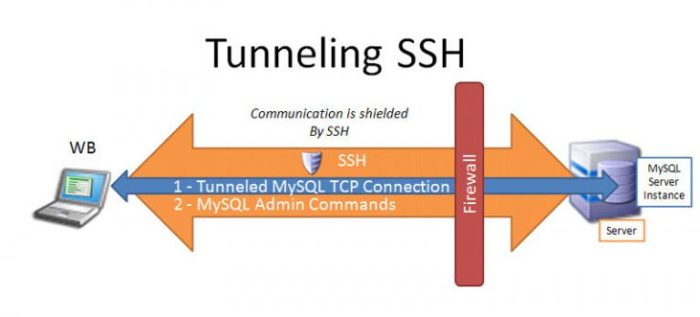
SSH UDP servers have proven their worth in a wide range of applications, from remote system administration to secure file transfers. By understanding their capabilities, implementing best practices, and leveraging advanced features, you can harness the full potential of SSH UDP servers to enhance the security, performance, and flexibility of your remote access infrastructure.