SSH.SSHSlowdns.com – In the realm of secure remote access, SSH UDP requests stand as a powerful tool for establishing secure connections. This protocol, leveraging the speed and efficiency of UDP, offers a unique approach to managing remote sessions, data transfer, and secure tunneling.
In this comprehensive guide, we will delve into the intricacies of SSH UDP requests, exploring their purpose, benefits, structure, and security considerations. We will also provide practical insights into troubleshooting, performance optimization, and best practices, empowering you to harness the full potential of SSH UDP requests.
Whether you’re a seasoned network administrator or a curious explorer of the digital realm, this guide will provide you with a thorough understanding of SSH UDP requests, enabling you to navigate the complexities of secure remote access with confidence.
SSH UDP Request Basics
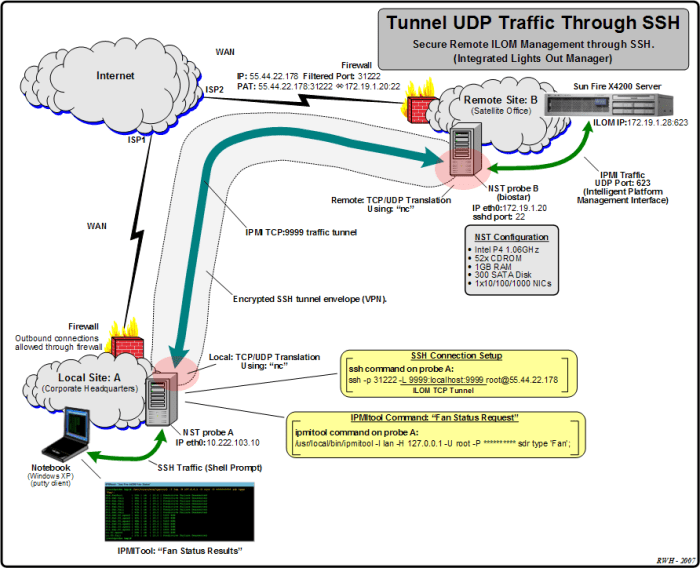
SSH UDP requests are a specialized type of SSH communication that utilizes the User Datagram Protocol (UDP) instead of the more common Transmission Control Protocol (TCP). UDP is a connectionless protocol, meaning it does not establish a persistent connection between the client and server, unlike TCP.
This makes UDP faster and more efficient for certain types of SSH requests, such as those that involve short bursts of data or that do not require reliable delivery.
Benefits of Using UDP for SSH Requests
There are several benefits to using UDP for SSH requests, including:
- Speed: UDP is faster than TCP because it does not need to establish a connection before sending data. This makes it ideal for applications that require real-time communication, such as video conferencing or gaming.
- Efficiency: UDP is more efficient than TCP because it does not need to maintain a connection state. This reduces the amount of overhead involved in SSH requests, making them more efficient for small amounts of data.
- Reliability: UDP is not as reliable as TCP, but it is still suitable for many applications that do not require guaranteed delivery. For example, UDP is often used for streaming media, where it is more important to have a fast and efficient connection than to have a reliable one.
Common Use Cases for SSH UDP Requests
SSH UDP requests are commonly used for a variety of applications, including:
- Port forwarding: SSH UDP requests can be used to forward UDP ports from one host to another. This can be useful for applications that require UDP communication, such as gaming or video conferencing.
- Remote desktop: SSH UDP requests can be used to establish a remote desktop connection to another host. This can be useful for accessing a remote computer from anywhere with an internet connection.
- File transfer: SSH UDP requests can be used to transfer files between two hosts. This can be useful for quickly transferring small files, such as configuration files or scripts.
SSH UDP Request Format
An SSH UDP request packet follows a specific structure to ensure efficient communication between the client and server. It consists of several fields, each serving a crucial purpose in the request-response process.
SSH UDP Request Packet Structure
- Source Port: The port number of the client sending the request.
- Destination Port: The port number of the SSH server listening for incoming requests.
- Length: The length of the SSH UDP request packet in bytes.
- Request Type: Specifies the type of SSH request being made, such as “open” or “close.”
- Payload: Additional data specific to the request type, such as the channel number or file name.
Example SSH UDP Request Packets
Here are some examples of valid SSH UDP request packets:
- Open Channel Request:
- Source Port: 1024
- Destination Port: 22
- Length: 128
- Request Type: “open”
- Payload: “channel=1,type=session”
- Close Channel Request:
- Source Port: 1024
- Destination Port: 22
- Length: 64
- Request Type: “close”
- Payload: “channel=1”
SSH UDP Request Processing
SSH UDP requests are processed by SSH servers in a specific manner, involving several key steps:
1. Receiving the request: The SSH server receives the SSH UDP request from the client.
2. Parsing the request: The server parses the request to determine its type and the requested action.
3. Authenticating the client: The server authenticates the client to ensure it is authorized to make the request.
4. Handling the request: The server processes the request based on its type, such as establishing a new SSH session or forwarding traffic.
5. Sending the response: The server sends a response to the client, which may include the result of the request or an error message.
SSH UDP Request Security
Using SSH UDP requests involves security implications that need to be addressed to prevent potential vulnerabilities and attacks.
SSH UDP requests can be susceptible to attacks due to the inherent nature of UDP, which is a connectionless protocol. This means that UDP packets are sent without establishing a connection, making it easier for attackers to intercept and manipulate them.
Mitigating Security Risks
To secure SSH UDP requests, several recommendations can be implemented:
- Use strong encryption: Employ robust encryption algorithms, such as AES-256 or ChaCha20, to protect the data transmitted over the UDP connection.
- Implement authentication mechanisms: Utilize strong authentication methods, like public-key cryptography or two-factor authentication, to verify the identity of the requesting client and prevent unauthorized access.
- Limit access to the SSH UDP port: Restrict access to the UDP port used for SSH requests to only authorized clients or networks, minimizing the risk of unauthorized access attempts.
- Monitor network traffic: Regularly monitor network traffic for suspicious activities or unauthorized access attempts. This allows for prompt detection and mitigation of potential security breaches.
SSH UDP Request Tools
SSH UDP request tools provide a means to generate, analyze, and interact with SSH UDP requests, facilitating troubleshooting, testing, and security assessments.
Several tools are available for this purpose, each offering unique features and capabilities.
ssh-probe
ssh-probe is a versatile tool for testing SSH servers and clients, including UDP-based SSH connections. It allows users to send custom SSH UDP packets, analyze responses, and perform vulnerability assessments.
Example usage: ssh-probe -u -p 22 hostname
nmap
nmap is a popular network scanning tool that can also be used to probe SSH UDP services. It provides options to detect SSH UDP servers, identify vulnerabilities, and perform port scanning.
Example usage: nmap -sU -p 22 hostname
hping3
hping3 is a packet crafting and analysis tool that supports SSH UDP requests. It allows users to generate custom SSH UDP packets, set various parameters, and analyze the responses.
Example usage: hping3 -S -p 22 -c 1 hostname
scapy
scapy is a powerful Python-based packet manipulation framework that includes support for SSH UDP requests. It provides a comprehensive set of tools for packet generation, analysis, and manipulation.
Example usage: scapy.send(scapy.UDP(dport=22, sport=50000))
SSH UDP Request Troubleshooting
SSH UDP requests, while efficient and secure, can sometimes encounter issues. This section will explore common problems and provide troubleshooting tips to resolve them.
Diagnosing and fixing SSH UDP request problems requires a systematic approach. Here are some common issues and their potential solutions:
Incorrect Configuration
- Problem: Incorrect SSH server or port configuration.
- Solution: Verify the SSH server’s UDP port is enabled and listening. Check the SSH configuration file for the correct settings.
Firewall or Network Issues
- Problem: Firewall or network device blocking UDP traffic.
- Solution: Configure the firewall or network device to allow UDP traffic on the SSH server’s port.
Client-Side Issues
- Problem: Incorrect client configuration or outdated SSH client software.
- Solution: Ensure the SSH client is configured correctly and updated to the latest version.
Server-Side Issues
- Problem: SSH server overload or resource exhaustion.
- Solution: Monitor the SSH server’s resource usage and scale up if necessary.
Connection Issues
- Problem: Network connectivity issues or unstable network conditions.
- Solution: Check the network connection and ensure it is stable. Use a network monitoring tool to identify any connectivity problems.
Other Issues
- Problem: Insufficient permissions or user authentication errors.
- Solution: Verify the user has the necessary permissions to access the SSH server. Ensure the user credentials are correct.
SSH UDP Request Performance
The performance of SSH UDP requests is crucial for ensuring a seamless and efficient user experience. There are various factors that can impact the performance of SSH UDP requests, and understanding these factors is essential for optimizing performance.
One of the key factors affecting SSH UDP request performance is the network latency between the client and the server. High latency can result in significant delays in the transmission of UDP packets, leading to slow response times and a degraded user experience.
To mitigate this, it is important to ensure that the network infrastructure is optimized for low latency and that there are no bottlenecks or congestion points along the path.
Packet Size Optimization
Another important factor is the size of the UDP packets being sent. Larger packets can be more efficient in terms of bandwidth utilization, but they can also be more susceptible to fragmentation and dropped packets, especially in congested networks. It is recommended to use smaller packet sizes for UDP requests, typically around 512 bytes to 1024 bytes, to minimize the risk of packet loss and improve overall performance.
Server Load
The load on the server can also have a significant impact on SSH UDP request performance. When the server is under heavy load, it may not be able to process UDP requests as quickly, leading to increased response times and potential timeouts.
To address this, it is important to ensure that the server has sufficient resources, such as CPU and memory, to handle the expected load and maintain optimal performance.
Security Considerations
Security considerations can also affect SSH UDP request performance. For example, enabling encryption can add overhead to the processing of UDP packets, which can impact performance. It is important to strike a balance between security and performance, and to use encryption only when necessary.
Tips for Optimizing Performance
Here are some additional tips for optimizing SSH UDP request performance:
- Use a reliable network connection with low latency.
- Optimize the size of UDP packets for the network environment.
- Ensure that the server has sufficient resources to handle the expected load.
- Consider using encryption only when necessary to balance security and performance.
- Monitor and troubleshoot the network and server performance regularly to identify and resolve any potential issues.
SSH UDP Request Extensions
SSH UDP extensions enhance the protocol’s functionality by introducing new features and capabilities. These extensions provide greater flexibility, security, and performance.
Channel Multiplexing
Channel multiplexing allows multiple SSH channels to be established over a single UDP connection. This optimizes bandwidth utilization and reduces latency by eliminating the need to establish separate connections for each channel.
Data Compression
Data compression extensions reduce the size of data packets sent over the UDP connection. This improves performance by reducing bandwidth requirements and minimizing transmission delays.
Authentication and Encryption Algorithms
Extensions introduce additional authentication and encryption algorithms to enhance security. These algorithms provide stronger protection against eavesdropping and man-in-the-middle attacks.
Port Forwarding
Port forwarding extensions allow remote access to specific ports on the client machine from the server. This enables secure remote administration and access to services that are not directly accessible through the firewall.
Packet Fragmentation
Packet fragmentation extensions allow large data packets to be broken down into smaller fragments for transmission over the UDP connection. This ensures reliable delivery even over networks with limited bandwidth or high latency.
SSH UDP Request Best Practices
Implementing SSH UDP requests securely and efficiently requires careful planning and adherence to best practices. By following these guidelines, organizations can maximize the benefits of SSH UDP while mitigating potential risks.
One crucial best practice is to limit the scope of SSH UDP requests. This involves restricting the use of SSH UDP to specific applications or services that genuinely require the benefits of UDP transport. By limiting the attack surface, organizations can reduce the likelihood of unauthorized access or data breaches.
Common Pitfalls to Avoid
To ensure the secure and efficient use of SSH UDP requests, it is essential to avoid common pitfalls. One such pitfall is failing to implement proper authentication and authorization mechanisms. SSH UDP requests should be authenticated using strong passwords or public-key cryptography to prevent unauthorized access.
Another pitfall is neglecting network security measures. Organizations should implement firewalls and intrusion detection systems to monitor and block malicious traffic, including SSH UDP requests from untrusted sources.
Recommendations for Production Environments
When implementing SSH UDP requests in production environments, organizations should consider the following recommendations:
- Use strong encryption algorithms to protect data transmitted over SSH UDP connections.
- Implement role-based access controls to restrict access to SSH UDP requests based on user privileges.
- Regularly monitor SSH UDP logs for suspicious activity and investigate any anomalies promptly.
- Consider using SSH UDP request management tools to automate tasks and enhance security.
By following these best practices, organizations can leverage the benefits of SSH UDP requests while maintaining a secure and efficient IT infrastructure.
SSH UDP Request Case Studies
SSH UDP requests have found numerous applications in real-world scenarios, offering advantages such as improved performance, reduced latency, and enhanced security. In this section, we will explore some case studies to illustrate how SSH UDP requests can be leveraged to address specific challenges.
One notable use case is in the field of remote access and management. By utilizing SSH UDP requests, administrators can establish secure connections to remote devices, even in environments with limited bandwidth or high latency. This allows for efficient execution of tasks such as software updates, configuration changes, and troubleshooting, without compromising security.
Secure Remote Access
SSH UDP requests play a crucial role in enabling secure remote access to servers, network devices, and other systems. In this scenario, the client initiates an SSH UDP request to establish a secure tunnel to the remote host. This tunnel provides a secure channel for transmitting data, allowing administrators to remotely manage and control the target system as if they were physically present.
The benefits of using SSH UDP requests for remote access include improved performance, reduced latency, and enhanced security. UDP’s connectionless nature eliminates the need for TCP’s three-way handshake, resulting in faster connection establishment and reduced overhead. Additionally, the use of strong encryption algorithms ensures the confidentiality and integrity of transmitted data.
Network Monitoring and Management
SSH UDP requests can be effectively employed for network monitoring and management tasks. By sending SSH UDP requests to network devices, administrators can gather real-time information about device status, performance, and configuration. This data can be used to identify potential issues, optimize network performance, and ensure the availability of critical services.
The advantages of using SSH UDP requests for network monitoring include reduced latency and improved efficiency. UDP’s connectionless nature allows for faster data retrieval, enabling administrators to obtain real-time insights into network behavior. Additionally, the use of SSH ensures the security and privacy of transmitted data, preventing unauthorized access to sensitive information.
Troubleshooting and Diagnostics
SSH UDP requests can be valuable for troubleshooting and diagnostics purposes. By sending SSH UDP requests to specific ports or services, administrators can test connectivity, identify potential issues, and gather diagnostic information. This can help pinpoint the root cause of problems and facilitate timely resolution.
The benefits of using SSH UDP requests for troubleshooting include improved performance and reduced overhead. UDP’s connectionless nature allows for faster and more efficient data transmission, enabling administrators to quickly gather diagnostic information. Additionally, the use of SSH ensures the security and confidentiality of transmitted data, preventing unauthorized access to sensitive information.