In the realm of secure remote access, SSH UDP requests play a crucial role. SSH (Secure Shell) is a widely used protocol for establishing encrypted connections over insecure networks, and its UDP (User Datagram Protocol) variant offers unique advantages for specific use cases.
This comprehensive guide will delve into the intricacies of SSH UDP requests, exploring their functionality, structure, processing, security, troubleshooting, applications, tools, best practices, alternatives, and future trends.
UDP, a connectionless protocol, provides faster transmission speeds compared to TCP (Transmission Control Protocol), making SSH UDP ideal for applications that prioritize speed over reliability, such as interactive shell sessions, real-time data transfer, and remote desktop access.
SSH UDP Request Overview
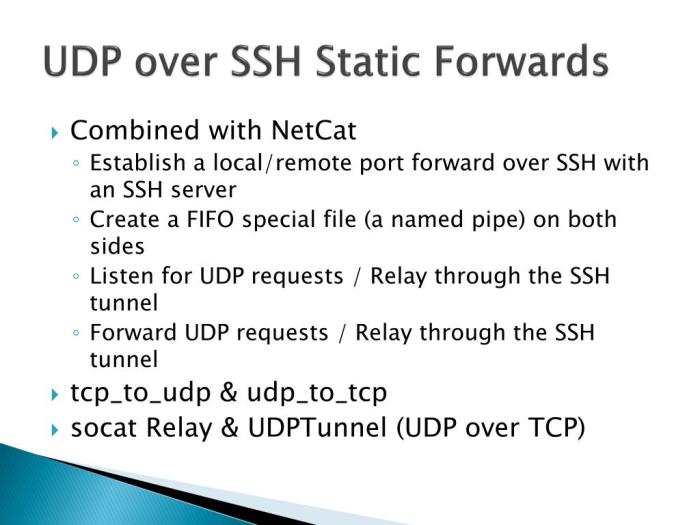
SSH UDP request allows for secure communication over the User Datagram Protocol (UDP) in place of the Transmission Control Protocol (TCP). This provides several advantages, including reduced overhead and improved performance in certain network environments.
Unlike TCP, which establishes a reliable connection between the client and server, UDP is a connectionless protocol. This means that data is sent without the need for handshaking or acknowledgment, resulting in lower overhead and potentially faster transmission speeds.
Benefits of Using UDP for SSH
- Reduced overhead: UDP’s connectionless nature eliminates the need for session establishment and maintenance, reducing the overhead associated with TCP.
- Improved performance: In networks with high latency or packet loss, UDP can provide better performance than TCP due to its ability to tolerate packet loss without retransmission.
Limitations of Using UDP for SSH
- Unreliable delivery: UDP does not guarantee delivery of packets, which can lead to data loss in some cases.
- Limited compatibility: Not all SSH clients and servers support UDP, which may limit its usability in certain environments.
SSH UDP Request Structure
An SSH UDP request packet is a structured message that follows a specific format. It consists of various fields, each with a specific purpose and significance in the SSH UDP communication process.
Source and Destination Ports
The source and destination ports in an SSH UDP request packet specify the endpoints of the communication channel. The source port identifies the port on the client machine from which the request is sent, while the destination port identifies the port on the server machine where the request should be received.
SSH UDP Header
The SSH UDP header contains information about the SSH version, packet type, and length. The SSH version field indicates the version of the SSH protocol being used, while the packet type field specifies the type of request being made. The length field indicates the total length of the packet, including the header and the payload.
Payload
The payload of an SSH UDP request packet contains the actual data being sent. The payload format varies depending on the type of request being made. For example, an authentication request would contain the username and password of the user attempting to authenticate.
SSH UDP Request Processing
When an SSH UDP request arrives at the server, it is processed through a series of steps to establish a secure connection between the client and the server.
The process involves authentication and key exchange, which are essential for ensuring the security and integrity of the connection.
Authentication
During authentication, the server verifies the identity of the client. This is typically done using a combination of methods, such as password-based authentication, public-key authentication, or certificate-based authentication.
- Password-based authentication requires the client to provide a username and password to the server. The server checks the credentials against its database and grants access if they match.
- Public-key authentication uses a pair of cryptographic keys, a public key and a private key. The public key is stored on the server, while the private key is kept secret by the client. The client sends its public key to the server, which verifies it and grants access if it matches the stored public key.
- Certificate-based authentication uses digital certificates to establish the identity of the client. The client sends its certificate to the server, which verifies it and grants access if it is valid and trusted.
Key Exchange
After authentication, the client and server exchange cryptographic keys to establish a secure channel for communication. This process is known as key exchange.
- Diffie-Hellman key exchange is a widely used key exchange algorithm. It involves the client and server generating random numbers and exchanging them over the network. These numbers are used to calculate a shared secret key, which is then used to encrypt and decrypt data transmitted over the connection.
- Elliptic-curve Diffie-Hellman (ECDH) key exchange is a variant of Diffie-Hellman that uses elliptic curves for increased security and efficiency.
SSH UDP Request Security
SSH UDP provides several security mechanisms to protect against eavesdropping and man-in-the-middle attacks.
SSH UDP Security Measures
SSH UDP utilizes the following security measures:
- Encryption: SSH UDP encrypts all data transmitted over the network, making it extremely difficult for eavesdroppers to intercept and decipher the information.
- Authentication: SSH UDP employs strong authentication mechanisms, such as public-key cryptography, to verify the identities of both the client and the server. This prevents unauthorized users from gaining access to the network.
- Integrity Checking: SSH UDP incorporates integrity checking mechanisms to ensure that the data transmitted between the client and the server has not been tampered with or altered during transmission.
SSH UDP Request Troubleshooting
SSH UDP requests may encounter issues due to various factors, such as network connectivity, server configuration, or client software compatibility. Identifying and resolving these problems can ensure seamless SSH UDP communication.
Common Problems and Solutions
-
- -*Network Connectivity Issues Ensure that the network path between the client and server is established and functioning properly. Check for any firewalls, routers, or network devices that may be blocking UDP traffic on the designated port (typically port 22).
-*Server Configuration Errors
Verify that the SSH server is configured to accept UDP requests. This involves checking the server’s configuration files (e.g., /etc/ssh/sshd_config) and ensuring that the “UseDNS” and “PasswordAuthentication” options are set to “no”.
-*Client Software Compatibility
Ensure that the SSH client software used on the client side supports UDP requests. Older versions of SSH clients may not have UDP support, so updating the client software to the latest version is recommended.
-*Port Forwarding Issues
If port forwarding is used to redirect UDP traffic to the SSH server, verify that the port forwarding rules are correctly configured on both the client and server sides. Check for any conflicting port assignments or incorrect port numbers.
-*Firewall or Antivirus Interference
Firewalls or antivirus software may interfere with SSH UDP requests. Configure exceptions or create firewall rules to allow UDP traffic on the designated port for SSH communication.
SSH UDP Request Applications
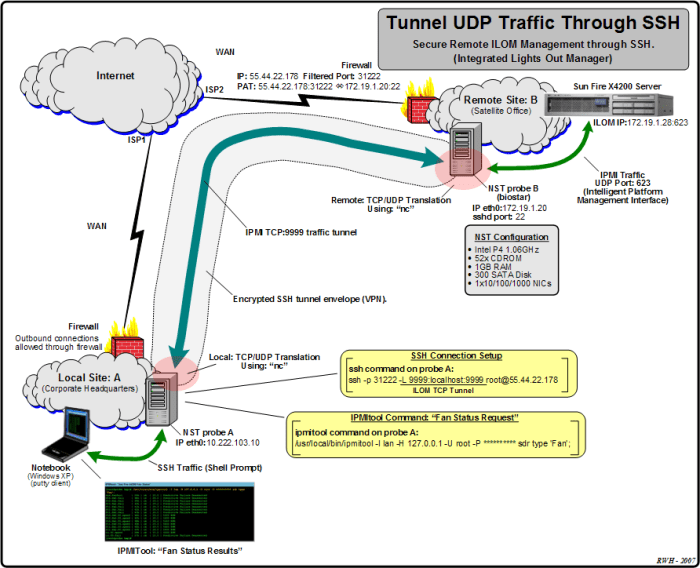
SSH UDP requests have found applications in various industries and use cases, offering secure and efficient data transfer over UDP.One
significant application is in secure tunneling. SSH UDP can establish a secure tunnel between two hosts, allowing applications to transmit data securely over an untrusted network. This is particularly useful in scenarios where the network infrastructure is not fully trusted or when sensitive data needs to be transferred over public networks.SSH
UDP is also employed in remote management and access. System administrators can use SSH UDP to remotely manage servers and network devices, even if the target devices are behind firewalls or NAT devices. This enables secure access to remote systems for maintenance, troubleshooting, and configuration tasks.Furthermore,
SSH UDP is utilized in secure file transfer. File transfer protocols such as SCP and SFTP can be encapsulated within SSH UDP, providing a secure channel for transferring files between hosts. This ensures the confidentiality and integrity of the transferred data, even over insecure networks.
SSH UDP Request Tools
SSH UDP request tools are essential for analyzing and manipulating SSH UDP requests in various scenarios, such as network troubleshooting, security assessments, and research purposes.
These tools provide a range of capabilities, including packet capture, analysis, manipulation, and simulation, enabling users to gain deep insights into the behavior of SSH UDP requests and the underlying network traffic.
Open-Source Tools
- Wireshark: A widely used network protocol analyzer that supports SSH UDP request capture and analysis. It offers deep packet inspection capabilities, allowing users to examine individual packets, identify anomalies, and troubleshoot network issues.
- Nmap: A popular network scanner that includes an SSH UDP request scanning module. It can detect SSH servers listening on UDP ports, determine their versions, and perform vulnerability scans.
- Scapy: A powerful packet manipulation library that allows users to craft and send custom SSH UDP requests. It provides a comprehensive set of tools for building and dissecting network packets, enabling advanced network testing and research.
Commercial Tools
- NetWitness Investigator: A commercial network security monitoring solution that includes SSH UDP request analysis capabilities. It provides real-time monitoring, intrusion detection, and forensic analysis, helping organizations protect their networks from SSH-related threats.
- Splunk: A popular log management and security information and event management (SIEM) platform that supports SSH UDP request analysis. It allows users to collect, analyze, and visualize SSH UDP request data from various sources, enabling comprehensive threat detection and incident response.
- Mandiant RedLine: A cloud-based threat intelligence and incident response platform that includes SSH UDP request analysis capabilities. It provides real-time threat detection, automated incident response, and threat hunting capabilities, helping organizations respond quickly to SSH-related attacks.
SSH UDP Request Best Practices
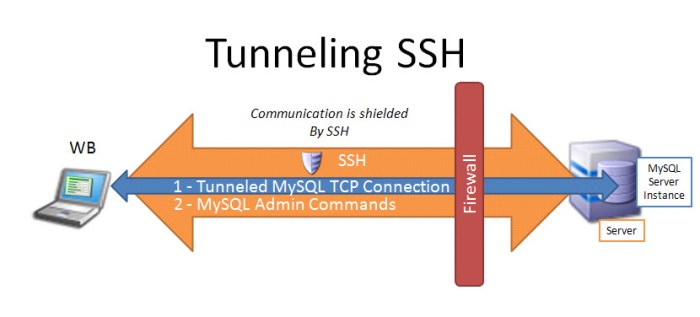
Ensuring secure SSH UDP request configuration and usage requires adherence to best practices. These include hardening techniques and avoiding common pitfalls.
Hardening Techniques
- Disable unused services: Disable any unnecessary SSH UDP services to minimize potential attack surfaces.
- Use strong encryption: Employ robust encryption algorithms (e.g., AES-256-CBC) to protect data in transit.
- Limit access: Restrict access to SSH UDP services only to authorized users and IP addresses.
- Monitor activity: Regularly monitor SSH UDP traffic for suspicious patterns or unauthorized access attempts.
- Keep software updated: Apply security patches and updates promptly to address vulnerabilities.
Common Pitfalls to Avoid
- Default configurations: Avoid using default configurations, which may be vulnerable to known exploits.
- Weak passwords: Use strong, unique passwords for SSH UDP accounts.
- Unprotected ports: Ensure SSH UDP ports are protected by firewalls and intrusion detection systems.
- Lack of authentication: Implement multi-factor authentication to enhance security.
- Ignoring security alerts: Respond promptly to security alerts and investigate any suspicious activity.
SSH UDP Request Alternatives
SSH UDP is a secure remote access protocol that allows users to securely connect to and control remote systems over an untrusted network. However, there are other protocols that can be used for secure remote access, each with its own advantages and disadvantages.
Comparison of SSH UDP with Other Protocols
| Protocol | Advantages | Disadvantages ||—|—|—|| SSH UDP |
- Secure |
- Requires a UDP port to be open on the remote system |
| SSH TCP |
- Secure |
- Requires a TCP port to be open on the remote system |
| RDP |
- Easy to use |
- Not as secure as SSH |
| VNC |
- Easy to use |
- Not as secure as SSH |
The choice of which protocol to use for secure remote access depends on the specific requirements of the application. SSH UDP is a good choice when security is a top priority, while RDP and VNC are good choices when ease of use is more important.
SSH UDP Request Future
The future of SSH UDP requests holds promising advancements and innovations that will enhance its capabilities and expand its applications.
One significant trend is the integration of SSH UDP requests with emerging technologies such as cloud computing and Internet of Things (IoT) devices. This integration will enable remote management and secure access to devices and resources in these environments, facilitating seamless and efficient operations.
Security Enhancements
Future developments will focus on enhancing the security of SSH UDP requests. This includes the adoption of advanced encryption algorithms and authentication protocols to protect data and prevent unauthorized access. Additionally, intrusion detection and prevention systems will be integrated to monitor and mitigate potential threats.
Performance Improvements
Performance optimizations will also be a key area of development. Techniques such as traffic shaping, load balancing, and caching will be employed to improve the speed and efficiency of SSH UDP requests. This will enable faster and more reliable access to remote resources.
New Applications
As SSH UDP requests become more robust and secure, they will find applications in various new domains. These include secure remote desktop access, remote software updates, and even remote gaming. The versatility and flexibility of SSH UDP requests will make them a valuable tool for a wide range of applications.
Last Word
SSH UDP requests offer a secure and efficient means of establishing remote connections, particularly for applications that demand high speed. Understanding the concepts, structure, and security aspects of SSH UDP is essential for network administrators and security professionals alike. By leveraging the insights provided in this guide, organizations can optimize their SSH UDP configurations, troubleshoot potential issues effectively, and ensure the integrity and confidentiality of their remote access operations.