In the realm of remote access and secure communication, SSH (Secure Shell) stands as a cornerstone technology. As organizations and individuals embrace the benefits of remote work and cloud computing, SSH has become an indispensable tool for establishing secure connections over the internet.
This comprehensive guide delves into the world of SSH, exploring the advantages of UDP (User Datagram Protocol) in SSH connections, the benefits of premium SSH services, and the nuances of free SSH options.
SSH, built upon the foundation of the TCP (Transmission Control Protocol), provides a robust and versatile platform for remote access. However, the adoption of UDP in SSH introduces a unique set of performance enhancements and considerations. This guide will navigate the intricacies of UDP in SSH, empowering readers to make informed decisions about their remote access strategies.
SSH Protocol Overview
The SSH protocol (Secure Shell) is a secure network protocol that provides a secure channel over an insecure network. It is commonly used to securely access remote systems, transfer files, and execute commands.
SSH works by establishing an encrypted connection between two computers. This connection is secured using strong encryption algorithms, such as AES and Blowfish, to protect data from eavesdropping and tampering.
Key Features and Benefits of SSH
- Encryption: SSH encrypts all data transmitted between the two computers, protecting it from eavesdropping and tampering.
- Authentication: SSH uses a variety of authentication methods, including passwords, public-key cryptography, and Kerberos, to verify the identity of the user.
- Data Integrity: SSH uses message authentication codes (MACs) to ensure that data is not modified in transit.
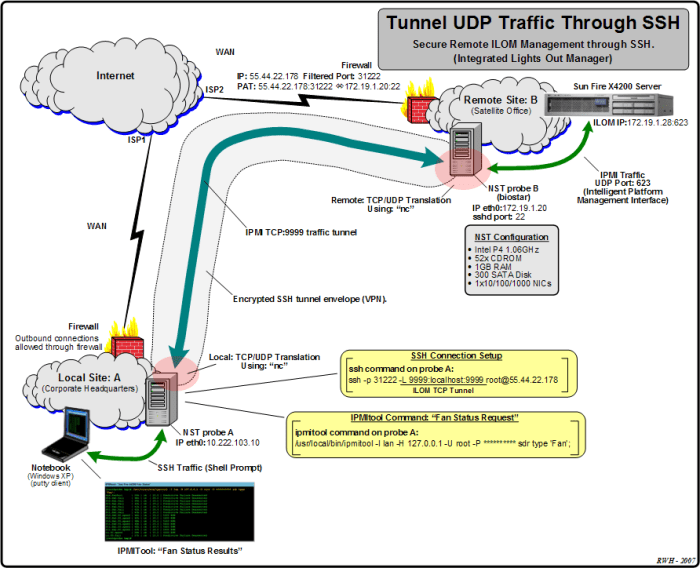
- Tunneling: SSH can be used to create secure tunnels through which other applications can send data. This allows applications to communicate securely over an insecure network.
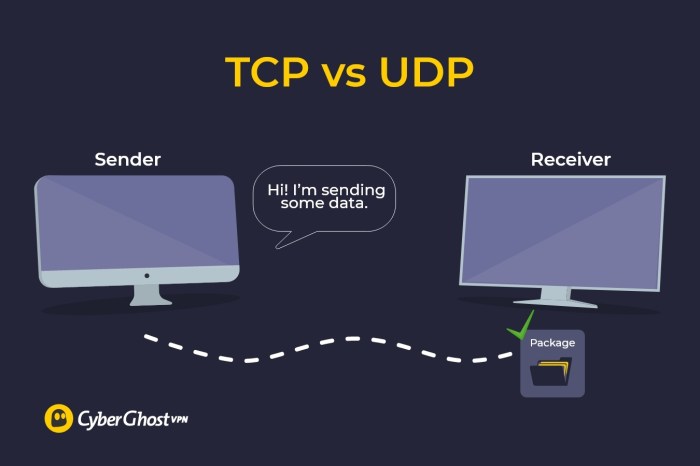
UDP vs. TCP in SSH
UDP and TCP are two fundamental protocols used in networking. In the context of SSH, they serve different purposes and offer distinct advantages and disadvantages.SSH primarily relies on TCP for secure and reliable data transmission. TCP establishes a connection-oriented session, ensuring that data packets are delivered in the correct order and acknowledged by the recipient.
This makes TCP suitable for interactive sessions and applications that require reliable data transfer.UDP, on the other hand, is a connectionless protocol that does not establish a session before sending data. UDP packets are sent independently, without the need for acknowledgment or error checking.
This makes UDP faster and more efficient for applications that require real-time data transfer or where reliability is not critical.
Advantages of Using UDP for SSH
Using UDP for SSH offers several advantages:
- Faster Performance: UDP’s connectionless nature eliminates the overhead associated with session establishment and acknowledgment, resulting in faster data transmission.
- Lower Latency: UDP packets are sent without waiting for acknowledgment, reducing latency and improving responsiveness for real-time applications.
- Reduced Overhead: UDP has a smaller header size compared to TCP, which translates to lower overhead and improved efficiency for applications that send small packets.
Disadvantages of Using UDP for SSH
However, using UDP for SSH also comes with some disadvantages:
- Unreliable Data Delivery: UDP does not guarantee that packets will be delivered in the correct order or even at all. This can be problematic for applications that require reliable data transfer.
- Limited Error Handling: UDP does not provide mechanisms for error checking or retransmission, which can lead to data loss or corruption in the event of network issues.
- Security Concerns: UDP’s lack of acknowledgment can make it vulnerable to spoofing attacks, where malicious actors can send packets that appear to come from a trusted source.
Performance Implications of Using UDP in SSH
The performance implications of using UDP for SSH depend on the specific application and network conditions. For applications that require real-time data transfer, such as audio or video streaming, UDP can significantly improve performance by reducing latency and overhead.However, for applications that require reliable data delivery, such as file transfers or interactive sessions, TCP is the preferred choice due to its built-in mechanisms for error handling and acknowledgment.In
summary, UDP offers advantages of speed and efficiency, while TCP provides reliability and security. The choice between UDP and TCP for SSH depends on the specific requirements and constraints of the application.
SSH Premium Services
Premium SSH services offer enhanced features and capabilities beyond those provided by standard SSH. These services typically come with a monthly or annual subscription fee and provide additional benefits such as:
- Increased security measures, such as two-factor authentication and intrusion detection systems.
- Faster connection speeds and improved performance.
- Access to premium support and technical assistance.
- Additional features, such as port forwarding, dynamic DNS, and SOCKS5 proxy support.
The cost of premium SSH services varies depending on the provider and the features included. However, the value proposition of these services can be significant, especially for businesses and individuals who rely on SSH for critical operations.
Free SSH Options
There are several free SSH options available, each with its own set of features and capabilities.
One of the most popular free SSH options is OpenSSH. OpenSSH is an open-source SSH implementation that is available for a wide range of platforms, including Linux, macOS, and Windows.
Another popular free SSH option is PuTTY. PuTTY is a free and open-source SSH client that is available for Windows.
Features and Capabilities
The features and capabilities of free SSH options vary depending on the specific software. However, most free SSH options offer the following features:
- Strong encryption to protect data in transit
- Authentication using passwords or public-key cryptography
- Support for SSH tunneling
- Ability to manage SSH keys
Pros and Cons
There are several pros and cons to using free SSH options.
Pros
- Free and open-source
- Widely available
- Easy to use
- Secure
Cons
- May not have all the features of commercial SSH options
- May not be as well-supported as commercial SSH options
SSH Security Considerations
Utilizing SSH requires careful consideration of security measures to protect against potential risks and vulnerabilities. Common security concerns associated with SSH include:
Vulnerabilities
- Brute-force attacks: Attempts to guess passwords or SSH keys by trying numerous combinations.
- Man-in-the-middle attacks: Interception and manipulation of SSH traffic by unauthorized parties.
- Buffer overflow attacks: Exploiting vulnerabilities in SSH software to execute malicious code.
- Denial-of-service attacks: Overwhelming SSH servers with excessive traffic, rendering them unavailable.
Recommendations for Enhancing SSH Security
To enhance SSH security, consider implementing the following recommendations:
- Strong authentication: Use complex passwords or SSH keys to prevent brute-force attacks.
- SSH key management: Generate and manage SSH keys securely, using strong passphrases and keeping them confidential.
- Packet authentication: Use packet authentication mechanisms, such as MAC, to protect against man-in-the-middle attacks.
- Secure SSH configuration: Configure SSH settings securely, such as disabling root login and enabling only necessary services.
- Intrusion detection and prevention systems: Implement IDS/IPS systems to monitor and block suspicious SSH activity.
SSH Configuration Options
Secure Shell (SSH) provides a secure channel over an unsecured network. It allows users to access remote systems, transfer files, and execute commands. SSH has a wide range of configuration options that can be customized to meet specific security and performance requirements.
The most important SSH configuration options are summarized in the following table:
| Option | Purpose | Default Value |
|---|---|---|
| Port | The port number on which SSH listens for incoming connections. | 22 |
| Protocol | The SSH protocol version to use. | 2 |
| Cipher | The encryption algorithm to use for data encryption. | aes256-ctr |
| MAC | The message authentication code algorithm to use for data integrity. | hmac-sha2-256 |
| KexAlgorithms | The key exchange algorithms to use for key generation. | curve25519-sha256, ecdh-sha2-nistp256, ecdh-sha2-nistp384, ecdh-sha2-nistp521 |
| HostKeyAlgorithms | The host key algorithms to use for server authentication. | ssh-ed25519, ssh-rsa, ssh-dss |
| UseDNS | Whether to resolve hostnames using DNS. | no |
| StrictHostKeyChecking | Whether to verify the server’s host key against a known list of trusted keys. | yes |
| PasswordAuthentication | Whether to allow password authentication. | no |
| PermitRootLogin | Whether to allow root login. | no |
These options can be configured in the SSH configuration file, typically located at /etc/ssh/sshd_config on Linux systems and /etc/ssh_config on macOS and Windows systems.
For example, to disable password authentication, add the following line to the SSH configuration file:
PasswordAuthentication no
To change the SSH port number, add the following line to the SSH configuration file:
Port 2222
SSH Key Management
SSH key management involves generating, managing, and using cryptographic keys to secure SSH connections. It is essential for maintaining the integrity and confidentiality of remote access and data transfers.
To ensure the security of SSH keys, it is important to follow best practices such as:
- Generating strong and unique keys
- Storing keys securely
- Revoking compromised keys
- Using key management tools
Generating SSH Keys
To generate an SSH key pair, you can use the following steps:
- Open a terminal window or command prompt.
- Type the following command:
ssh-keygen- t rsa
- b 4096
- Follow the prompts to specify a location for the keys and a passphrase (optional).
This will generate two files: a public key (with a .pub extension) and a private key (with no extension).
Managing SSH Keys
Once generated, SSH keys can be managed using the following steps:
- Storing keys securely: Store private keys in a secure location, such as a password manager or hardware security module.
- Backing up keys: Create backups of your SSH keys in case of loss or damage.
- Revoking compromised keys: If a key is compromised, revoke it immediately using the
ssh-keygencommand.
-R - Using key management tools: Utilize tools like OpenSSH’s
ssh-addandssh-agentto manage multiple keys and simplify authentication.
SSH Port Forwarding
SSH port forwarding is a technique that allows you to securely access remote network services through an SSH connection. It involves creating a secure tunnel between your local computer and a remote server, allowing you to redirect traffic from your local machine to the remote server.
To set up SSH port forwarding, you need to specify the remote port you want to access and the local port you want to use on your computer. Once configured, you can access the remote service through the local port as if it were running on your local machine.
Use Cases
- Accessing remote servers from behind firewalls or network restrictions.
- Testing and debugging applications that require access to remote services.
- Providing secure access to internal network resources for remote users.
Limitations
- Port forwarding can only be established over an SSH connection.
- The remote server must support SSH port forwarding.
- Port forwarding may not be suitable for applications that require high bandwidth or low latency.
SSH Remote Execution
SSH provides a secure method for remote execution of commands on a remote host. This allows administrators to manage and configure remote systems without the need for physical access.To perform remote execution over SSH, use the following syntax:“`ssh user@host command“`Where:
- `user` is the username on the remote host.
- `host` is the IP address or hostname of the remote host.
- `command` is the command to be executed on the remote host.
For example, to execute the `ls` command on a remote host with the IP address 192.168.1.100, use the following command:“`ssh [email protected] ls“`SSH remote execution provides several benefits, including:
Secure communication
SSH uses strong encryption to protect data transmitted over the network, ensuring the confidentiality and integrity of commands and data.
Remote management
SSH allows administrators to manage and configure remote systems from any location with an internet connection.
Automation
SSH remote execution can be automated using scripts or tools, enabling efficient and consistent management of multiple remote hosts.However, it’s important to consider the security implications of SSH remote execution:
Unauthorized access
SSH remote execution can provide unauthorized users with access to sensitive information or systems if the SSH server is not properly configured or if credentials are compromised.
Privilege escalation
If the user executing commands on the remote host has elevated privileges, they could potentially gain unauthorized access to other systems or data on the network.
Denial of service
SSH remote execution can be used to launch denial of service attacks by flooding the remote host with excessive commands or data.To mitigate these security risks, it’s crucial to implement strong security measures, such as:
- Using strong passwords or SSH keys for authentication.
- Restricting access to SSH only to authorized users.
- Configuring SSH to use secure protocols and encryption algorithms.
- Monitoring SSH logs for suspicious activity.
SSH Troubleshooting
Troubleshooting SSH connections involves identifying and resolving issues that prevent successful remote access or data transfer. This section provides a structured approach to diagnosing and fixing common SSH problems.
Common SSH Troubleshooting Scenarios
| Scenario | Resolution Steps |
|---|---|
| Connection Refused |
|
| Authentication Failed |
|
| Host Key Mismatch |
|
| Timeout Errors |
|
| Permission Denied |
|
Advanced SSH Troubleshooting Techniques
In addition to the basic troubleshooting steps, advanced techniques may be necessary for resolving complex SSH issues. These include:
- SSH Debugging: Enable SSH debugging to generate detailed logs for analysis.
- Network Packet Analysis: Use tools like Wireshark to capture and inspect SSH network traffic.
- SSH Configuration File Analysis: Review the SSH configuration files on both the client and server for any errors or misconfigurations.
Final Summary
Whether seeking enhanced performance, comprehensive security features, or cost-effective solutions, this guide has provided a comprehensive overview of SSH, UDP, and the spectrum of SSH options available. By leveraging the insights and recommendations Artikeld herein, readers can confidently navigate the landscape of remote access, ensuring secure and efficient connections.