SSH.SSHSlowdns.com – In the realm of secure remote access, SSH (Secure Shell) reigns supreme. This versatile protocol has revolutionized the way we manage servers, transfer files, and establish secure connections over insecure networks. At the heart of SSH lies a fundamental choice: UDP (User Datagram Protocol) or TCP (Transmission Control Protocol).
Understanding the nuances of each protocol is crucial for optimizing SSH performance and security.
In this comprehensive guide, we will delve into the intricacies of SSH over UDP and TCP, exploring their advantages, disadvantages, and practical applications. We will also provide practical tips on port forwarding, SSH tunneling, security best practices, and troubleshooting common issues.
By the end of this discussion, you will have a thorough understanding of SSH and the factors to consider when choosing between UDP and TCP for your specific needs.
SSH Connection Protocol
The Secure Shell (SSH) protocol is a network protocol that provides secure communication between two computers. It is designed to replace insecure protocols such as Telnet and FTP, which send data in plaintext.
SSH works by encrypting all data transmitted between the two computers. This encryption makes it very difficult for eavesdroppers to intercept and read the data.
Versions of SSH
There are several versions of SSH, each with its own set of features. The most common version is SSH-2, which was released in 1999. SSH-2 is more secure than SSH-1 and includes a number of new features, such as support for public-key authentication.
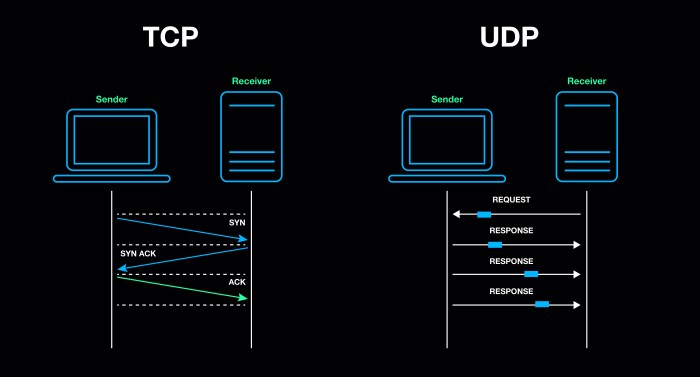
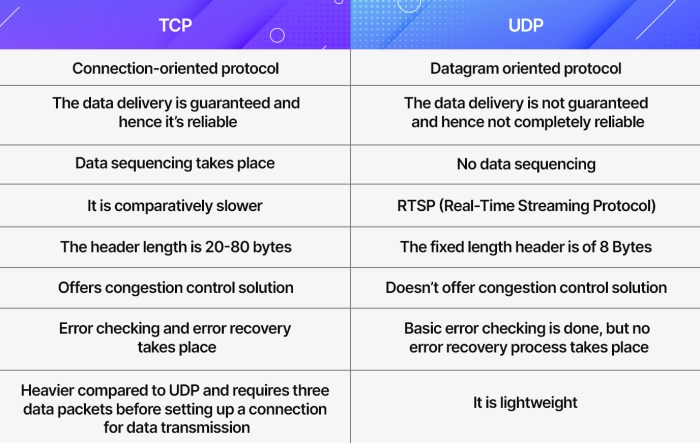
SSH over UDP vs. TCP
SSH connections can be established over either UDP or TCP. UDP is a connectionless protocol, while TCP is a connection-oriented protocol. This difference has several implications for the use of SSH over UDP and TCP.
Advantages of UDP for SSH
- UDP is a faster protocol than TCP, as it does not require the establishment of a connection before data can be sent.
- UDP is a more lightweight protocol than TCP, as it does not maintain state information for each connection.
- UDP is a more resilient protocol than TCP, as it does not rely on a single connection to maintain communication.
Disadvantages of UDP for SSH
- UDP is a less reliable protocol than TCP, as it does not guarantee that data will be delivered in order or without errors.
- UDP is a less secure protocol than TCP, as it does not provide any encryption or authentication mechanisms.
- UDP is not supported by all SSH clients and servers.
Advantages of TCP for SSH
- TCP is a more reliable protocol than UDP, as it guarantees that data will be delivered in order and without errors.
- TCP is a more secure protocol than UDP, as it provides encryption and authentication mechanisms.
- TCP is supported by all SSH clients and servers.
Disadvantages of TCP for SSH
- TCP is a slower protocol than UDP, as it requires the establishment of a connection before data can be sent.
- TCP is a more heavyweight protocol than UDP, as it maintains state information for each connection.
- TCP is a less resilient protocol than UDP, as it relies on a single connection to maintain communication.
Port Forwarding
SSH provides a secure channel for remote access and data transfer. Port forwarding is a feature that allows users to redirect traffic from one port on the local computer to another port on the remote computer through the SSH connection.
When port forwarding is enabled, the SSH client acts as a proxy, listening for incoming connections on a specified local port. When a connection is received, the SSH client forwards the traffic over the secure SSH tunnel to the specified port on the remote computer.
This allows users to access remote services securely, even if they are not directly accessible from the local network.
Benefits of Port Forwarding
- Secure remote access: Port forwarding provides a secure way to access remote services, even if the services are not directly accessible from the local network.
- Bypass firewalls: Port forwarding can be used to bypass firewalls that block direct access to certain ports or services.
- Test and debug applications: Port forwarding can be used to test and debug applications that require access to specific ports on a remote computer.
SSH Tunneling
SSH tunneling is a technique that establishes a secure, encrypted channel between two remote hosts over an untrusted network.
This technique allows users to securely access remote resources, such as applications, files, and databases, by encapsulating traffic within an SSH connection.
Benefits of SSH Tunneling
- Secure Communication: Encrypts data, ensuring privacy and protection against eavesdropping.
- Access Remote Resources: Allows secure access to remote resources, such as file servers, databases, and applications.
- Bypass Firewalls: Can bypass firewalls and network restrictions by encapsulating traffic within SSH connections.
- Network Segmentation: Isolates and secures specific network segments by creating dedicated SSH tunnels.
Applications of SSH Tunneling
- Remote Desktop Access: Securely access remote desktops and applications.
- File Transfer: Securely transfer files between remote hosts.
- Database Access: Establish secure connections to remote databases.
- Network Management: Securely manage and troubleshoot network devices.
SSH Security
SSH incorporates robust security measures to safeguard remote connections. It utilizes advanced encryption algorithms and authentication methods to protect data and prevent unauthorized access.
Encryption algorithms, such as AES-256, 3DES, and Blowfish, are employed to encrypt data transmitted over the SSH connection. These algorithms make it virtually impossible for eavesdroppers to intercept and decipher the information.
Authentication Methods
SSH supports various authentication methods to ensure secure access:
- Password Authentication: Requires the user to provide a password to authenticate.
- Public Key Authentication: Uses public-private key pairs to verify the user’s identity without transmitting the password.
- Kerberos Authentication: Leverages the Kerberos network authentication protocol for secure authentication.
SSH also offers additional security features, such as host key verification, which helps prevent man-in-the-middle attacks, and session multiplexing, which allows multiple secure channels to be established over a single SSH connection.
SSH Configuration
Configuring SSH is essential for securing remote connections. Here’s a guide to configuring SSH on various operating systems.
SSH configuration involves specifying parameters such as:
- Port number
- Authentication methods
- Key exchange algorithms
- Cipher algorithms
- Logging options
These options influence the security and usability of SSH connections.
Configuring SSH on Linux
Edit the SSH configuration file located at /etc/ssh/sshd_config. Adjust the following parameters:
- Port: Change the default port (22) to enhance security.
- Authentication: Enable strong authentication methods like public-key authentication and disable password authentication.
- Key exchange algorithms: Choose secure algorithms like ECDH or DH.
- Cipher algorithms: Select strong ciphers like AES-256-GCM or ChaCha20-Poly1305.
- Logging: Enable verbose logging for troubleshooting and security analysis.
Configuring SSH on Windows
Use the SSH configuration tool or edit the SSH configuration file located at %ProgramData%\OpenSSH\sshd_config. Configure the following:
- Port: Change the default port (22) for increased security.
- Authentication: Enable public-key authentication and disable password authentication.
- Key exchange algorithms: Choose secure algorithms like ECDH or DH.
- Cipher algorithms: Select strong ciphers like AES-256-GCM or ChaCha20-Poly1305.
- Logging: Enable verbose logging for troubleshooting and security analysis.
Configuring SSH on macOS
Edit the SSH configuration file located at /etc/ssh/sshd_config. Adjust the following parameters:
- Port: Change the default port (22) to enhance security.
- Authentication: Enable strong authentication methods like public-key authentication and disable password authentication.
- Key exchange algorithms: Choose secure algorithms like ECDH or DH.
- Cipher algorithms: Select strong ciphers like AES-256-GCM or ChaCha20-Poly1305.
- Logging: Enable verbose logging for troubleshooting and security analysis.
SSH Tools and Utilities
SSH comes with a suite of tools and utilities that enhance its functionality and ease of use. These tools provide various capabilities, from secure file transfer to port forwarding and tunneling.
File Transfer
- scp: Securely copies files between remote hosts. It uses SSH to establish a secure channel for file transfer.
- sftp: Interactive file transfer program that provides a secure file browsing and transfer interface over SSH.
Port Forwarding
- ssh
-L: Forwards a local port to a remote host, allowing access to remote services through a local port. - ssh
-R: Forwards a remote port to a local host, enabling access to local services from a remote host.
Tunneling
- ssh
-D: Creates an SSH tunnel, which can be used to securely route traffic through an intermediary server. - ProxyCommand: Allows SSH to use an external proxy for connecting to remote hosts.
Other Utilities
- ssh-keygen: Generates SSH key pairs for authentication.
- ssh-copy-id: Copies SSH public keys to remote hosts, simplifying login without passwords.
- ssh-add: Adds SSH private keys to the SSH agent, enabling passwordless authentication.
SSH Best Practices
To enhance the security of SSH connections, it’s crucial to adopt best practices that mitigate common vulnerabilities. Here are some key measures to consider:
Use Strong Passwords and Key-Based Authentication
Weak passwords pose a significant security risk. Employ strong passwords that are complex, unique, and difficult to guess. Alternatively, implement key-based authentication, which utilizes public-private key pairs to provide a more secure alternative to passwords.
Disable Root Login and Create Limited User Accounts
Disabling root login prevents direct access to the system with elevated privileges. Instead, create limited user accounts with restricted permissions to minimize the potential impact of compromised credentials.
Keep Software Updated
Regularly update SSH software and the operating system to patch vulnerabilities and enhance security. Outdated software can contain exploitable flaws that could be targeted by attackers.
Enable Two-Factor Authentication
Implement two-factor authentication (2FA) to add an extra layer of security. This requires users to provide a second form of authentication, such as a one-time password or a hardware token, in addition to their password.
Use SSH Port Forwarding Securely
When using SSH port forwarding, configure it properly to avoid exposing services to unauthorized access. Use strong passwords or key-based authentication, and limit access to specific hosts and ports.
Monitor SSH Logs and Use Intrusion Detection Systems
Monitor SSH logs regularly to detect suspicious activity and identify potential attacks. Additionally, deploy intrusion detection systems (IDS) to detect and alert on unauthorized access attempts.
SSH Troubleshooting
SSH is a robust protocol, but it can occasionally encounter issues. This guide provides a troubleshooting guide for common SSH problems, helping you identify and resolve connection problems, authentication errors, and other issues.
Before troubleshooting, ensure that the SSH server is running and listening on the correct port. Check firewall settings to ensure SSH traffic is allowed, and verify that the client and server have compatible SSH versions.
Connection Problems
- Connection refused: This error occurs when the SSH server is not running or is not listening on the specified port. Verify that the SSH service is active and configured to listen on the correct port.
- Connection timed out: This error indicates that the SSH client could not establish a connection within the specified timeout period. Increase the timeout value or check network connectivity.
- Host key mismatch: This error occurs when the client’s cached host key does not match the server’s current host key. Accept the new host key or manually verify its authenticity.
Authentication Errors
- Invalid username or password: Ensure that the username and password are correct. Check for typos or caps lock issues.
- Permission denied (publickey): This error occurs when the client does not have the correct public key configured for authentication. Verify that the public key is added to the server’s authorized_keys file.
- Permission denied (keyboard-interactive): This error indicates that the client needs to provide additional authentication, such as a one-time password or a challenge-response.
Other Issues
- Slow performance: Check network connectivity and ensure that the SSH server is not overloaded. Consider using SSH compression or optimizing network settings.
- Tunneling issues: Verify that port forwarding is correctly configured on both the client and server. Check firewall rules and ensure that the target port is accessible.
- Permission denied for specific commands: Ensure that the user has the necessary permissions to execute the commands on the remote server.
SSH Alternatives
SSH is a widely used protocol for secure remote access, but there are alternative protocols and technologies that offer similar or even enhanced capabilities. Here are some notable SSH alternatives:
- Secure Shell (OpenSSH): OpenSSH is an open-source implementation of the SSH protocol that is widely used on Linux and Unix systems. It provides strong encryption, authentication, and data integrity.
- Telnet: Telnet is a simple network protocol that allows users to access remote computers over a network. While it is less secure than SSH, it is still widely used for basic remote administration tasks.
- Remote Desktop Protocol (RDP): RDP is a proprietary protocol developed by Microsoft that allows users to remotely control a Windows computer. It provides a graphical user interface (GUI) and supports features such as file transfer and audio/video streaming.
- Virtual Private Network (VPN): A VPN creates a secure tunnel between two networks, allowing users to securely access resources on a remote network. VPNs can be used for both remote access and secure communication.
- Secure Sockets Layer (SSL)/Transport Layer Security (TLS): SSL/TLS are encryption protocols that are used to secure web traffic. They can also be used to secure other types of network traffic, such as email and file transfers.
Each of these alternatives has its own strengths and weaknesses, and the best choice for a particular application will depend on the specific requirements. SSH is generally considered to be the most secure and versatile of these protocols, but it may not be the best choice for all applications.