In the realm of secure remote access, SSH (Secure Shell) reigns supreme. This versatile protocol allows for secure data transfer and remote command execution, empowering users with unparalleled control over their systems. At the heart of SSH lies a fundamental choice: UDP (User Datagram Protocol) or TCP (Transmission Control Protocol).
This article delves into the intricacies of SSH UDP and TCP, comparing their strengths, weaknesses, and applications to provide a comprehensive guide for informed decision-making.
SSH UDP and TCP offer distinct advantages and drawbacks. UDP, known for its speed and efficiency, is ideal for applications that prioritize low latency, such as interactive shell sessions and real-time data transfer. TCP, on the other hand, excels in reliability and error correction, making it the preferred choice for secure file transfers and bulk data operations.
SSH Overview
SSH, or Secure Shell, is a powerful network protocol designed to provide secure remote access to computer systems over an unsecured network. It enables users to securely connect to remote hosts, execute commands, transfer files, and manage systems as if they were physically present.
SSH operates on a client-server model, where the SSH client establishes a secure connection to an SSH server running on the remote host. The connection is encrypted using strong cryptographic algorithms, ensuring that all data transmitted between the client and server remains confidential and protected from eavesdropping or interception.
Benefits of SSH
- Secure Remote Access: SSH provides a secure channel for remote access, allowing users to connect to and manage systems from anywhere with an internet connection.
- Encrypted Communication: All data transmitted over an SSH connection is encrypted, protecting sensitive information from unauthorized access.
- Authentication and Authorization: SSH supports multiple authentication methods, including password-based, public key-based, and two-factor authentication, ensuring strong user authentication and access control.
- Port Forwarding: SSH allows users to forward ports between the client and server, enabling access to applications and services running on the remote host from the local machine.
- File Transfer: SSH includes built-in support for secure file transfer using the Secure Copy (SCP) and SFTP protocols, allowing users to transfer files between the client and server securely.
Drawbacks of SSH
- Complexity: SSH can be complex to configure and manage, especially for non-technical users.
- Potential Vulnerabilities: Like any software, SSH is subject to vulnerabilities that could be exploited by attackers.
- Limited Compatibility: SSH may not be supported on all operating systems or devices.
- Performance Overhead: Encryption and authentication processes in SSH can introduce some performance overhead, especially on low-powered devices or slow network connections.
SSH Protocols
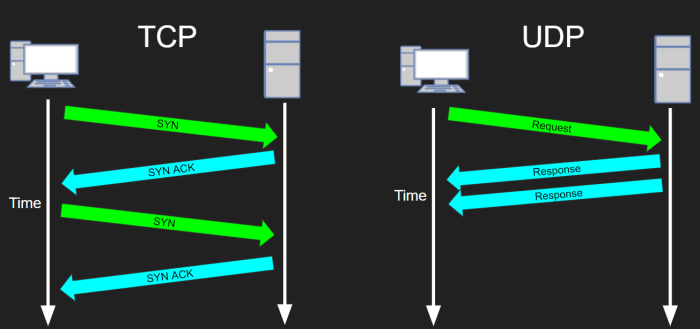
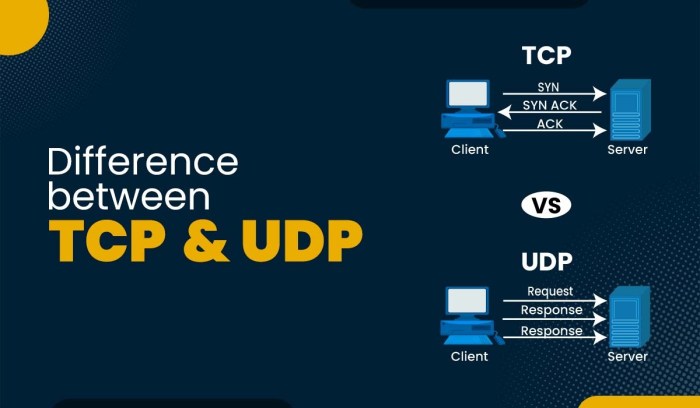
SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication between two systems over an unsecured network. SSH operates on two different transport protocols: UDP and TCP.
UDP vs. TCP
UDP (User Datagram Protocol) and TCP (Transmission Control Protocol) are two different transport protocols that provide different features and guarantees for data transmission.
UDP
- Connectionless: UDP does not establish a connection between the sender and receiver before sending data. This makes UDP faster and more efficient for small, occasional data transfers.
- Unreliable: UDP does not guarantee that data will be delivered in order or without errors. This can be a disadvantage for applications that require reliable data transmission.
TCP
- Connection-oriented: TCP establishes a connection between the sender and receiver before sending data. This ensures that data is delivered in order and without errors.
- Reliable: TCP guarantees that data will be delivered in order and without errors. This makes TCP more suitable for applications that require reliable data transmission.
Advantages and Disadvantages
The choice of SSH transport protocol depends on the specific requirements of the application.
UDP
- Advantages: Faster, more efficient for small data transfers
- Disadvantages: Unreliable, not suitable for applications that require reliable data transmission
TCP
- Advantages: Reliable, guarantees data delivery in order and without errors
- Disadvantages: Slower, less efficient for small data transfers
SSH Port Usage
SSH relies on specific ports for communication between the client and server. Understanding these ports is crucial for effective SSH deployment and troubleshooting.
Default Ports
By default, SSH uses the following ports:
- TCP port 22: This is the standard port for SSH connections over TCP.
- UDP port 3306: This is the default port for SSH connections over UDP.
Implications of Non-Default Ports
While using non-default ports can enhance security by obscuring the SSH service from attackers, it also introduces potential complications:
- Configuration complexity: The SSH client and server must be manually configured to use non-default ports, which can be time-consuming and error-prone.
- Firewall issues: Firewalls must be configured to allow traffic on the non-default ports, otherwise SSH connections will be blocked.
- Port scanning detection: Attackers may use port scanning tools to identify non-default SSH ports, potentially exposing the system to vulnerabilities.
SSH Encryption
SSH employs a range of robust encryption algorithms to safeguard communication. These algorithms ensure data privacy and integrity during transmission, preventing eavesdropping and unauthorized access.
Symmetric Encryption Algorithms
SSH utilizes symmetric encryption algorithms such as AES (Advanced Encryption Standard) and Blowfish. These algorithms use the same key for both encryption and decryption. The shared secret key is securely exchanged during the SSH handshake process, ensuring only authorized parties can access the data.
Asymmetric Encryption Algorithms
SSH also employs asymmetric encryption algorithms like RSA (Rivest-Shamir-Adleman) and DSA (Digital Signature Algorithm). These algorithms utilize a pair of keys, a public key and a private key. The public key is used to encrypt data, while the private key is used to decrypt it.
This mechanism ensures that only the intended recipient with the corresponding private key can access the data.
Key Exchange Algorithms
SSH relies on key exchange algorithms like Diffie-Hellman and Elliptic Curve Diffie-Hellman (ECDH) to establish a shared secret key securely. These algorithms allow two parties to agree on a secret key over an insecure channel without revealing it to any eavesdroppers.These
encryption algorithms work in conjunction to provide a highly secure communication channel for SSH. The combination of symmetric, asymmetric, and key exchange algorithms ensures that data transmitted over SSH is protected from unauthorized access, interception, and modification.
SSH Authentication
SSH supports a variety of authentication methods, including password-based, public-key, and two-factor authentication. Each method has its own strengths and weaknesses, and the best choice for a particular application will depend on the security requirements and the level of convenience desired.
Password-based Authentication
Password-based authentication is the most common SSH authentication method. It is easy to set up and use, but it is also the least secure. Passwords can be easily guessed or stolen, and they do not provide any protection against replay attacks.
Public-key Authentication
Public-key authentication is a more secure alternative to password-based authentication. It uses a pair of cryptographic keys, a public key and a private key. The public key is stored on the server, and the private key is kept secret by the client.
When a client connects to a server using public-key authentication, the server sends the client a challenge. The client then uses its private key to sign the challenge and send it back to the server. The server verifies the signature and, if it is valid, grants the client access.
Two-factor Authentication
Two-factor authentication is the most secure SSH authentication method. It requires the user to provide two pieces of information, such as a password and a one-time code, in order to log in. This makes it much more difficult for an attacker to gain access to an account, even if they have stolen the user’s password.
SSH Tunneling
SSH tunneling is a technique that allows you to create a secure tunnel between two remote hosts over an unsecured network. This tunnel can be used to securely transfer data between the two hosts, even if the network is hostile.
SSH tunneling works by creating a virtual network interface on each of the two hosts. These virtual network interfaces are then connected to each other using an SSH connection. All traffic that passes through the tunnel is encrypted, making it secure from eavesdropping and other attacks.
Types of SSH Tunnels
There are two main types of SSH tunnels:
- Local port forwarding: This type of tunnel allows you to connect to a remote port on the SSH server from a local port on your computer. This can be useful for accessing services that are only available on the SSH server, such as a web server or a database server.
- Remote port forwarding: This type of tunnel allows you to connect to a local port on your computer from a remote port on the SSH server. This can be useful for exposing services on your computer to the outside world, such as a web server or a file server.
Applications of SSH Tunneling
SSH tunneling has a wide range of applications, including:
- Securely accessing remote services: SSH tunneling can be used to securely access remote services, such as web servers, database servers, and file servers, even if the network is hostile.
- Bypassing firewalls: SSH tunneling can be used to bypass firewalls that block certain ports. This can be useful for accessing services that are blocked by a firewall, such as a web server or a file server.
- Creating a secure network: SSH tunneling can be used to create a secure network between two hosts, even if the network is hostile. This can be useful for creating a secure connection between two offices or between two data centers.
SSH Configuration
SSH configuration involves setting parameters for secure remote access. Proper configuration is crucial for ensuring the security and efficiency of SSH connections.
SSH UDP and TCP Configuration
SSH can operate over both UDP and TCP protocols. Here’s how to configure them on different operating systems:
Linux and macOS
- Edit the SSH configuration file (/etc/ssh/sshd_config) using a text editor.
- Set the “Protocol” directive to “2” for SSH2, which supports both UDP and TCP.
- Restart the SSH service using “sudo service sshd restart”.
Windows
- Open the “Services” control panel.
- Find the “SSH Server” service and right-click to select “Properties”.
- Switch to the “Connection” tab and set the “Preferred protocol version” to “2”.
- Click “Apply” and then “OK” to save changes.
Importance of SSH Configuration
Proper SSH configuration is essential for the following reasons:
- Security: It allows you to disable insecure protocols and algorithms, restrict access to specific users or IP addresses, and enable logging for audit purposes.
- Performance: Configuration can optimize SSH performance by adjusting parameters like packet size, compression, and cipher algorithms.
- Compatibility: It ensures compatibility with different SSH clients and servers, allowing seamless remote access across various platforms.
SSH Security Best Practices
SSH connections, whether using UDP or TCP, require proper security measures to protect against unauthorized access and data breaches. Here are some best practices to enhance SSH security:
- Use Strong Passwords or SSH Keys: Employ complex passwords with a combination of upper and lowercase letters, numbers, and symbols. Alternatively, consider using SSH keys for authentication, which are more secure than passwords.
- Disable Root Login: Prevent direct login as the root user, as this grants excessive privileges. Instead, create a non-root user account and grant it sudo privileges for administrative tasks.
- Enable Two-Factor Authentication (2FA): Implement 2FA to add an extra layer of security by requiring a second form of authentication, such as a one-time password or hardware token.
- Use SSH Port Knocking: Configure SSH port knocking to require a specific sequence of port connections before granting access. This adds an additional layer of protection against automated attacks.
- Restrict SSH Access: Limit SSH access to specific IP addresses or subnets using firewall rules. This prevents unauthorized users from attempting to connect from outside trusted networks.
- Keep SSH Software Up to Date: Regularly update SSH software and firmware to patch vulnerabilities and security flaws. Outdated software can expose systems to known exploits.
- Monitor SSH Logs: Monitor SSH logs for suspicious activity, such as failed login attempts, unauthorized access, or unusual traffic patterns. This enables timely detection and response to security incidents.
- Use SSH Tunneling: Establish secure tunnels using SSH to encrypt data transmitted over insecure networks, preventing eavesdropping and data breaches.
Common SSH Vulnerabilities and Mitigation
Despite security measures, SSH can be vulnerable to attacks. Here are common vulnerabilities and mitigation strategies:
- Brute-Force Attacks: Implement rate-limiting measures to prevent repeated login attempts and lock out accounts after a certain number of failed attempts.
- Man-in-the-Middle (MitM) Attacks: Use SSH host key verification to ensure the authenticity of the server before establishing a connection.
- Buffer Overflow Attacks: Ensure that SSH software is up to date and patched to address buffer overflow vulnerabilities.
- SSH Key Compromise: Regularly rotate SSH keys and revoke compromised keys to prevent unauthorized access.
- Phishing Attacks: Educate users about phishing scams and encourage them to be cautious of unsolicited emails or messages requesting sensitive information.
SSH Troubleshooting
Troubleshooting SSH UDP and TCP issues involves identifying and resolving common errors that may arise during SSH sessions. These issues can range from connection problems to authentication failures.
Connection Issues
*
-*Unable to establish a connection
Verify that the SSH server is running on the remote host and that the correct port is specified. Check firewall settings to ensure that SSH traffic is allowed.
-
- -*Connection timeout Increase the connection timeout value in the SSH client configuration to allow more time for the connection to be established.
-*Port forwarding issues
Ensure that port forwarding is enabled on both the SSH client and server, and that the correct ports are specified.
Authentication Issues
*
-*Incorrect credentials
Verify that the username and password or SSH key being used are correct.
-
- -*Permission denied Ensure that the user attempting to connect has the necessary permissions to access the SSH server.
-*Public key authentication failure
Check that the public key used for authentication is valid and has been added to the authorized_keys file on the SSH server.
Other Issues
*
-*Slow performance
Optimize network settings, such as increasing the TCP window size or enabling compression, to improve performance.
-
- -*Buffer overflow Adjust the buffer size in the SSH client configuration to prevent buffer overflow errors.
-*Packet loss
Check network connectivity and consider using a VPN or SSH tunnel to improve stability.
SSH Use Cases
SSH is a powerful tool that can be used for a variety of purposes. Some of the most common use cases include:
Remote System Administration
SSH is a secure way to remotely administer systems. This is especially useful for managing servers that are located in a different location or that are not easily accessible physically. With SSH, you can perform all the same tasks that you would be able to do if you were sitting at the console of the remote system.
File Transfer
SSH can also be used to transfer files between systems. This is a secure way to transfer sensitive files, such as financial data or customer information. SSH uses encryption to protect the data from being intercepted and read by unauthorized users.
Secure Shell Access
SSH can be used to provide secure shell access to a system. This allows you to log in to the system and run commands as if you were sitting at the console. SSH uses encryption to protect the login credentials and the data that is transferred between the client and the server.
Port Forwarding
SSH can be used to forward ports between systems. This allows you to access services on a remote system as if they were running on your local system. This is useful for accessing services that are not normally accessible from outside the network, such as internal web servers or databases.
Final Summary
Whether you opt for the speed and agility of UDP or the reliability and robustness of TCP, SSH remains a cornerstone of secure remote access. Its versatility, coupled with its robust encryption and authentication mechanisms, makes it an indispensable tool for system administrators, network engineers, and anyone seeking to securely manage remote systems.