SSH.SSHSlowdns.com – Secure Shell (SSH) is a powerful tool for managing remote systems and transferring data securely. With its robust configuration options, SSH can be tailored to meet specific needs, including creating custom accounts, enabling UDP port forwarding, and implementing advanced security measures.
This guide delves into the intricacies of SSH configuration, providing a comprehensive overview of its capabilities and practical examples to enhance your remote management experience.
From understanding the fundamentals of SSH to exploring advanced topics such as cloud integration and network security, this guide empowers you to leverage the full potential of SSH for efficient and secure remote system administration.
SSH Configuration
SSH (Secure Shell) is a cryptographic network protocol that provides a secure channel for remote login and command execution over an insecure network. It allows users to securely access and manage remote systems without compromising their credentials or data.SSH offers several key features:
-
- -*Encryption Encrypts all data transmitted between the client and server, ensuring the confidentiality and integrity of the connection.
-*Authentication
Supports multiple authentication methods, including password, public key, and two-factor authentication, to verify the identity of users.
-*Remote Access
Enables users to remotely access and manage systems, execute commands, and transfer files securely.
-*Port Forwarding
Allows users to securely tunnel traffic through SSH connections, enabling access to remote resources.
SSH configurations are typically managed through the SSH configuration file (/etc/ssh/sshd_config). Common configuration options include:
-
- -*Port The port number used for SSH connections (default: 22).
-*Protocol
The SSH protocol version to be used (default: 2).
-*Ciphers
The encryption algorithms used to protect data (default: AES-256-CBC).
-*MACs
The message authentication codes used to verify data integrity (default: HMAC-SHA2-512).
-*Key Exchange Algorithms
The algorithms used to establish a secure key exchange (default: Diffie-Hellman Group 14).
-*Authentication Methods
The methods allowed for user authentication (default: password and public key).
For example, to disable password authentication and enforce public key authentication only, the following configuration can be added to the SSH configuration file:“`PasswordAuthentication noPubkeyAuthentication yes“`
UDP Port Forwarding
UDP port forwarding allows you to redirect UDP traffic from one port on your local machine to a different port on a remote machine. This can be useful for applications that use UDP, such as games or voice chat programs.To
configure UDP port forwarding in SSH, you need to use the
-L option. The syntax is as follows
“`
-L [bind_address
]bind_port:[remote_address:]remote_port“`For example, the following command will forward UDP traffic from port 5000 on your local machine to port 2000 on the remote machine:“`ssh
-L 5000
remote_address:2000 user@remote_host“`You can also specify a bind address, which is the IP address of the local interface that the traffic will be forwarded from. For example, the following command will forward UDP traffic from port 5000 on the local interface with IP address 192.168.1.100 to port 2000 on the remote machine:“`ssh
-L 192.168.1.100
5000:remote_address:2000 user@remote_host“`
Custom Accounts
Custom accounts provide a secure and flexible way to manage SSH access to your system. By creating custom accounts, you can control the level of access that each user has, and you can also specify the commands that they are allowed to run.
To create a custom account, you will need to use the useradd command. The useradd command takes a number of options, which you can use to specify the username, password, home directory, and other settings for the new account.
For example, the following command will create a new user account called “john” with a password of “password”:
“`useradd
- m
- d /home/john
- s /bin/bash john
“`
Once you have created a custom account, you can use the passwd command to set the password for the account.
You can also use the visudo command to edit the /etc/sudoers file, which controls which users are allowed to run sudo commands.
By using custom accounts, you can improve the security of your system and you can also make it easier to manage user access.
SSH Authentication Methods
SSH supports various authentication methods to provide secure access to remote servers. Each method has its own advantages and drawbacks, and the choice depends on the security requirements and preferences of the user.
Password Authentication
- Simplest and most common method
- Requires a username and password to establish a connection
- Prone to brute-force attacks and eavesdropping
Public Key Authentication
- Uses a pair of cryptographic keys (public and private)
- Public key is stored on the server, while the private key is kept secret by the client
- More secure than password authentication as it eliminates the risk of eavesdropping and brute-force attacks
Keyboard-Interactive Authentication
- Prompts the user for additional information during the authentication process
- Can be used in combination with other authentication methods to enhance security
- Not as secure as public key authentication as it involves user input
Certificate-Based Authentication
- Uses digital certificates to authenticate the client
- Provides strong security and can be used for both user and machine authentication
- Requires a certificate authority to issue and manage certificates
GSSAPI Authentication
- Uses a third-party authentication mechanism, such as Kerberos
- Delegates authentication to a trusted third party
- Simplifies authentication and eliminates the need for manual password management
SSH Security Best Practices
SSH security is crucial for protecting remote access to servers and networks. It ensures data integrity, confidentiality, and system availability. Implementing best practices enhances SSH security and minimizes vulnerabilities.
Best Practices for Securing SSH
-
- -*Use Strong Passwords or SSH Keys Complex passwords or SSH keys prevent unauthorized access.
-*Enable Two-Factor Authentication (2FA)
2FA adds an extra layer of security by requiring an additional verification step.
-*Restrict Access
Limit SSH access to specific users and IP addresses to prevent unauthorized connections.
-*Disable Root Login
Disable direct root login via SSH to prevent attackers from gaining administrative privileges.
-*Use Port Knocking
Port knocking involves knocking on specific ports in a sequence to grant access, making it harder for attackers to guess the SSH port.
-*Monitor SSH Logs
Regularly review SSH logs for suspicious activities and failed login attempts.
-*Keep SSH Software Updated
Ensure the SSH software is up-to-date with the latest security patches.
-*Disable Unnecessary Services
Disable any SSH-related services that are not essential to minimize potential attack vectors.
-*Use SSH Tunneling
Create secure channels for data transfer over insecure networks.
SSH Troubleshooting
SSH, or Secure Shell, is a powerful tool for securely accessing remote servers. However, like any complex technology, it can sometimes encounter issues. In this section, we will explore some common SSH troubleshooting issues and discuss the steps involved in resolving them.
Identifying SSH Issues
The first step in troubleshooting SSH issues is to identify the problem. This can be done by examining the error messages or other symptoms that are present. Common SSH issues include:
- Connection refused
- Permission denied
- Host key mismatch
- Authentication failure
Troubleshooting Steps
Once the SSH issue has been identified, the next step is to troubleshoot and resolve it. The following steps can be helpful in this process:
- Check the basics: Verify that the SSH server is running on the remote host and that the correct port is being used. Also, ensure that the client and server are using compatible SSH versions.
- Examine error messages: Error messages can provide valuable clues about the cause of the issue. Carefully read the error messages and search for solutions online or in the SSH documentation.
- Verify SSH configuration: Check the SSH configuration files on both the client and server to ensure that they are correct. Look for any misconfigurations or missing settings.
- Test connectivity: Use tools like ping or traceroute to test the network connectivity between the client and server. This can help identify any network issues that may be causing the SSH problem.
- Disable SSH authentication methods: Temporarily disable SSH authentication methods like password authentication or public key authentication to isolate the issue. This can help determine if the problem lies with the authentication method or other SSH settings.
- Reset SSH keys: If the SSH issue is related to SSH keys, try resetting the keys and generating a new pair. This can resolve problems with corrupted or invalid SSH keys.
Example Troubleshooting Techniques
Here are some specific examples of SSH troubleshooting techniques:
- Connection refused: Check if the SSH server is running on the remote host. If not, start the server and try connecting again.
- Permission denied: Verify that the user has the necessary permissions to access the remote server. Check the file permissions and user groups on the server.
- Host key mismatch: This error occurs when the SSH client cannot verify the host key of the remote server. Check if the host key has changed or if there is a man-in-the-middle attack.
- Authentication failure: Ensure that the username and password or SSH key are correct. Also, check if the SSH server has any authentication restrictions, such as IP address filtering.
SSH in Cloud Environments
SSH provides secure access to remote cloud servers, offering several benefits in cloud environments:
-
- -*Centralized Management SSH allows administrators to manage multiple cloud servers from a single location, simplifying administration and reducing errors.
-*Secure Access
SSH encrypts all communication, ensuring data security and preventing unauthorized access.
-*Automation
SSH can be automated using scripts and tools, enabling efficient and consistent server management tasks.
However, SSH in cloud environments also poses challenges:
-
- -*Ephemeral Instances Cloud instances can be created and terminated frequently, requiring dynamic SSH configuration management.
-*Shared Environments
Multiple users may access cloud servers, necessitating secure and granular access controls.
-*Security Vulnerabilities
SSH configurations must be carefully managed to prevent vulnerabilities and unauthorized access.
SSH Configurations for Cloud Environments:To optimize SSH in cloud environments, consider the following configurations:
-
- -*Key-based Authentication Use SSH keys instead of passwords for strong authentication and reduced security risks.
-*Port Forwarding
Enable port forwarding to securely access applications and services running on the remote server.
-*Firewall Rules
Configure firewalls to restrict SSH access to specific IP addresses or networks.
-*Bastion Hosts
Implement a bastion host as an intermediary server for secure SSH access, reducing the attack surface of the target servers.
SSH Tools and Utilities
SSH provides various tools and utilities to enhance its functionality and usability.
These tools assist in managing SSH keys, debugging connections, and automating tasks.
To use SSH tools and utilities, they can be invoked from the command line. The specific syntax and options for each tool vary depending on the tool being used.
SSH Key Management Tools
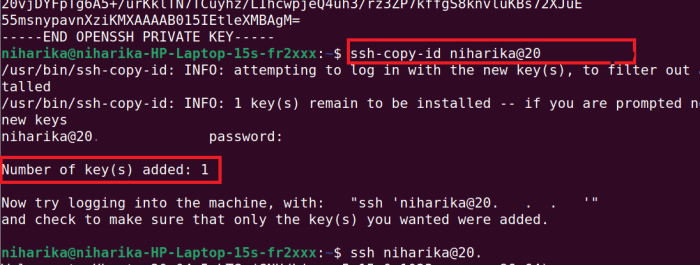
- ssh-keygen: Generates, manages, and converts SSH keys.
- ssh-copy-id: Copies SSH public keys to remote hosts.
- ssh-add: Adds SSH private keys to the SSH agent.
- ssh-agent: Manages SSH keys and provides authentication.
SSH Debugging Tools
- ssh
-v: Enables verbose mode for SSH, providing detailed information about the connection process. - ssh
-vvv: Enables extra verbose mode, providing even more detailed information. - sshd
-d: Enables debug mode for the SSH daemon, providing detailed information about SSH server operations.
SSH Automation Tools
- sshpass: Allows for automating SSH login by providing the password via the command line.
- expect: A scripting language used for automating interactive SSH sessions.
- paramiko: A Python library for automating SSH connections.
SSH and Network Security
SSH plays a crucial role in enhancing network security by providing secure remote access, data encryption, and authentication mechanisms. It secures communication channels, prevents unauthorized access, and safeguards sensitive data in transit.
SSH can be utilized in various ways to bolster network security:
Secure Remote Access
SSH allows administrators to securely access and manage remote systems over unsecured networks. It establishes an encrypted tunnel, preventing eavesdropping and man-in-the-middle attacks.
Data Encryption
SSH encrypts all data transmitted between the client and server, ensuring confidentiality and preventing unauthorized access to sensitive information.
Authentication
SSH supports multiple authentication methods, including password-based, key-based, and multi-factor authentication. This helps prevent unauthorized access and strengthens overall network security.
Example SSH Configurations for Network Security
Here are some sample SSH configurations for enhancing network security:
- Disable Password Authentication: Disabling password authentication prevents brute-force attacks and strengthens security. Use key-based authentication instead.
- Limit Root Access: Restrict root access to only authorized users and create separate user accounts with limited privileges.
- Enable Two-Factor Authentication: Implement two-factor authentication (2FA) for an additional layer of security.
- Use Strong Ciphers: Configure SSH to use strong encryption algorithms like AES-256-CBC or ChaCha20-Poly1305.
- Restrict Access to Specific Hosts: Limit SSH access to specific hosts or IP addresses to prevent unauthorized connections.
SSH and System Administration
SSH plays a crucial role in system administration, providing secure and efficient remote access to manage and maintain systems. It enables administrators to perform various tasks from remote locations, including:
Remote Configuration and Management
SSH allows administrators to remotely access and configure servers, routers, switches, and other network devices. They can modify system settings, install software, update configurations, and perform troubleshooting tasks without the need for physical presence.
File Transfer and Synchronization
SSH supports secure file transfer protocols such as SCP and SFTP. This enables administrators to transfer files between remote systems, perform backups, and synchronize data across different locations.
Remote Script Execution
Administrators can use SSH to execute scripts and commands on remote systems. This allows them to automate repetitive tasks, perform batch operations, and manage multiple systems efficiently.
System Monitoring and Troubleshooting
SSH provides a secure channel for system monitoring tools to collect data from remote systems. Administrators can use SSH to access log files, check system status, and diagnose issues remotely.